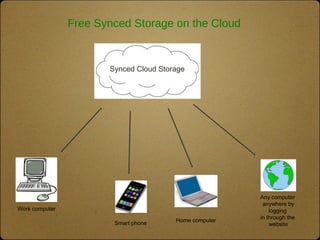
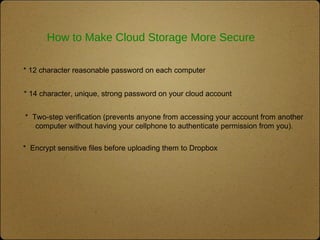
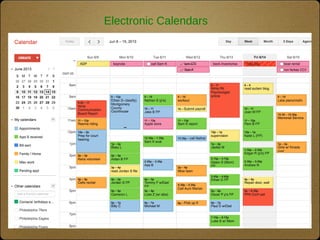
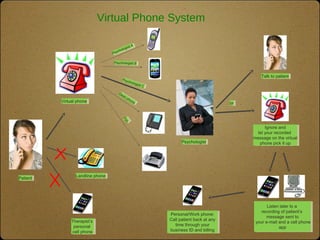
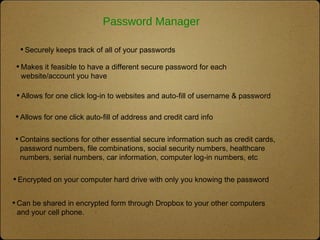
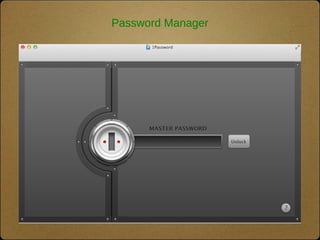
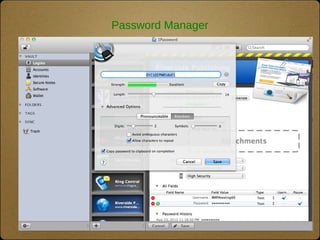
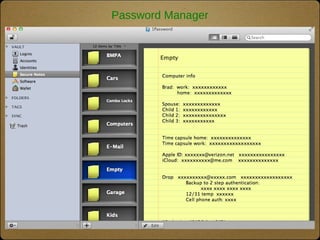
The document outlines the top 10 technologies for psychologists, focusing on tools such as synced cloud storage, electronic calendars, virtual phone systems, and password managers. It emphasizes the importance of security and offers practical steps for ensuring the safety of online information, including password management and data backup strategies. Commonly used services and recommendations for enhancing security practices are also included.