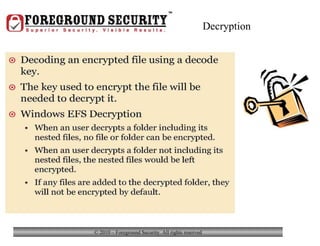
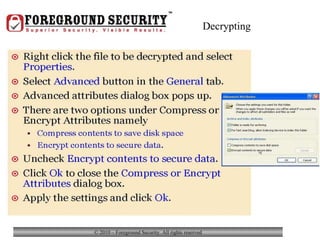
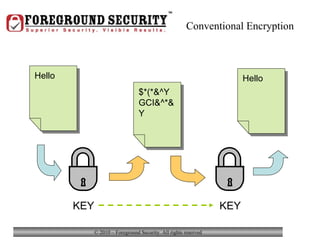
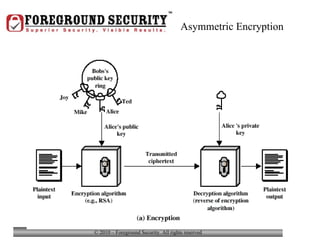
- Laptop theft is common, with a laptop stolen every 53 seconds. Keeping valuable personal or business information on a laptop increases the consequences if it is stolen.
- Practical ways to protect laptops from theft include keeping your eyes on your laptop at all times, using passwords and encryption, installing tracking software, making backups, and using locks, insurance, and remote data deletion options.
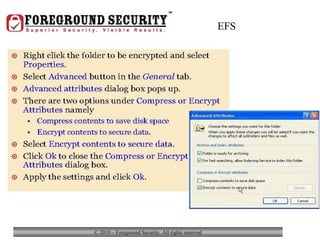
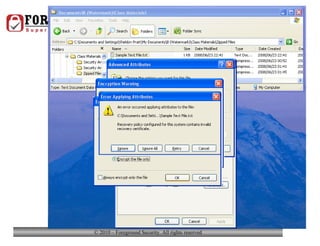
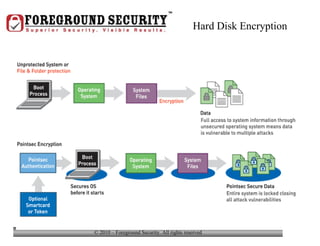
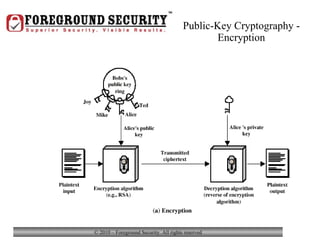
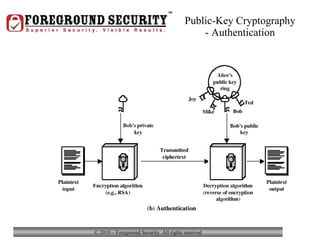
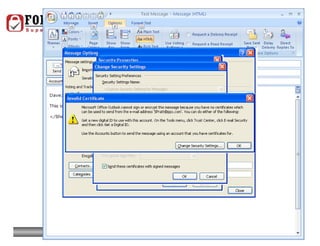
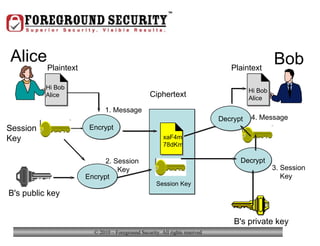
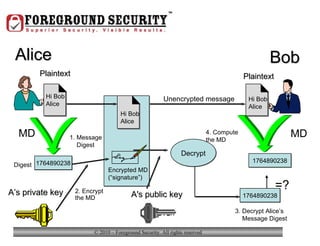
- In addition to general desktop security practices, laptop security requires physical security like using locking cables when the laptop is left unattended, as well as data security practices like using whole-disk encryption and privacy screens.