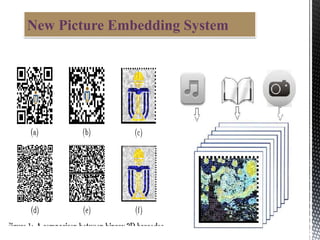
This document presents a new picture-embedding 2D barcode called PiCode. PiCode aims to mitigate limitations of conventional 2D barcodes by embedding a picturesque image within the barcode. It is designed to consider both the perceptual quality of the embedded image and decoding robustness. Comparisons show PiCode achieves one of the best image qualities while maintaining a good balance between quality and robustness under various conditions. The document describes the encoding and decoding algorithms used in PiCode. It concludes that PiCode provides an improved perceptual quality picture embedding compared to existing beautified QR codes while still allowing robust decoding.