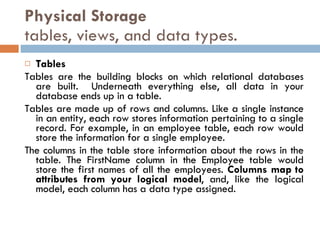
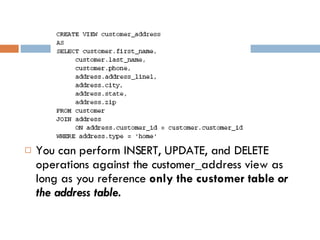
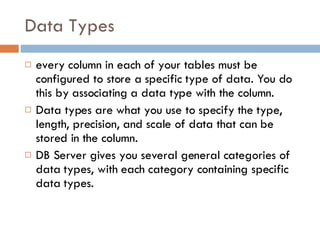
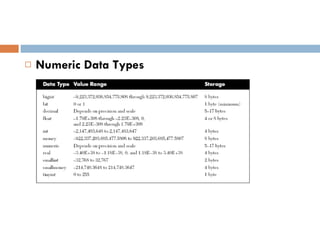
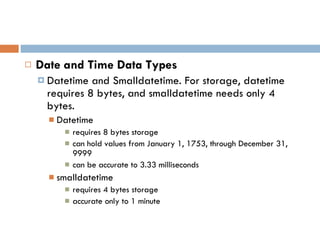
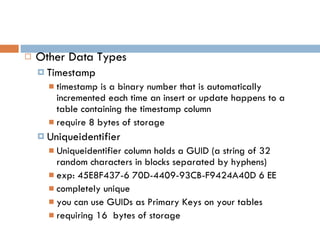
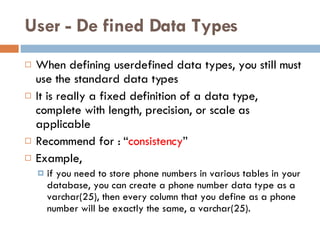
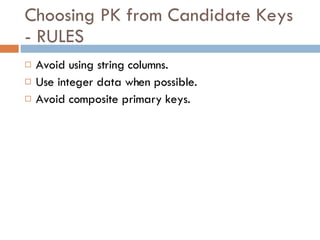
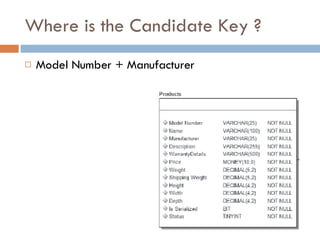
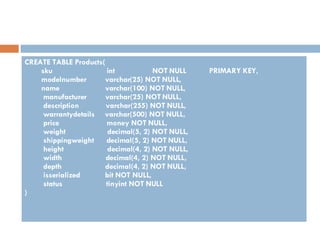
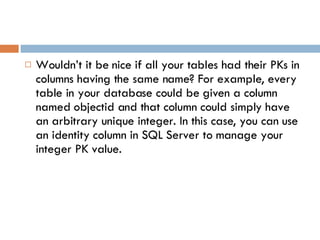
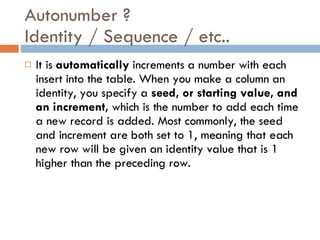
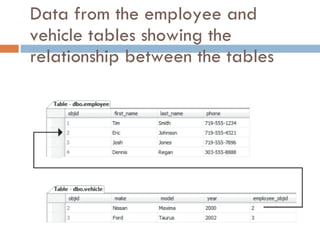
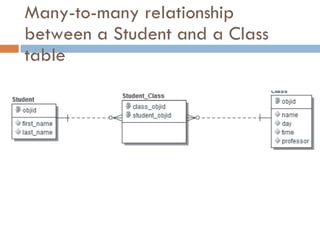
Physical storage in databases involves tables, views, and data types. Tables store data in rows and columns and are made up of columns with assigned data types. Views allow you to display data from tables in different ways. Common data types include numeric, string, date/time, and binary types that determine what values a column can store.