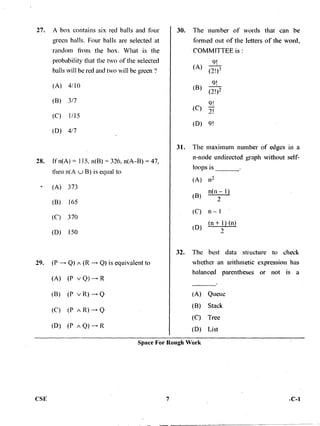
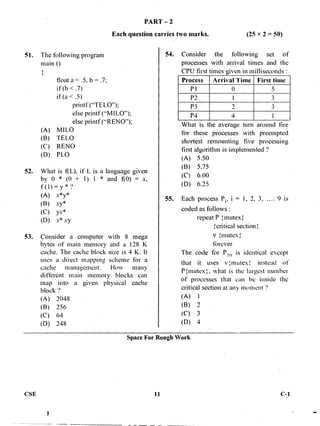
The document provides instructions for a post graduate common entrance test for computer science engineering. It specifies the date, time, duration, and format of the test. Candidates are instructed to fill in personal details like registration number, question booklet code and serial number on the answer sheet. They are also provided instructions on how to answer questions within the given time limit, as well as guidelines for proper marking of responses. The test contains 2 parts - part 1 has 50 one-mark questions and part 2 has 25 two-mark questions.