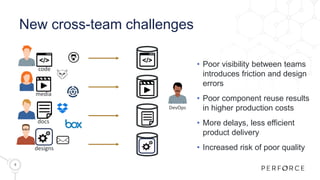
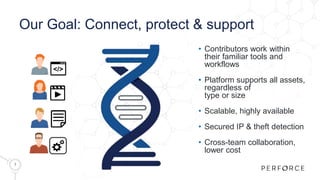
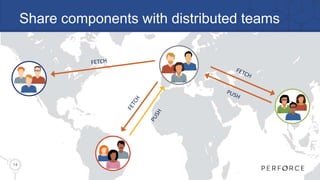
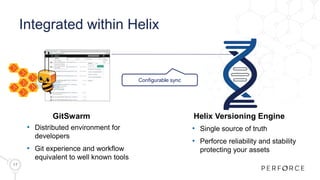
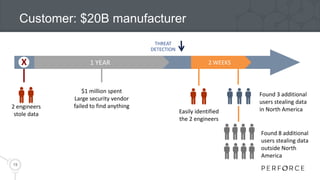
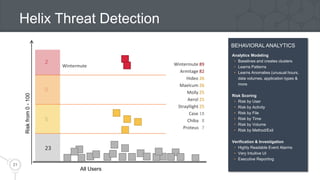
The document introduces Perforce Helix, addressing challenges in modern product development and the need for better cross-team collaboration. It emphasizes the importance of security against IP theft and presents Helix's features, including a new git ecosystem, advanced threat detection, and flexible deployment options. Perforce Helix aims to enhance productivity, support diverse workflows, and protect intellectual property in an increasingly complex development environment.