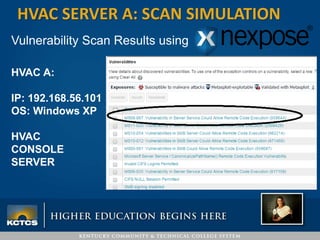
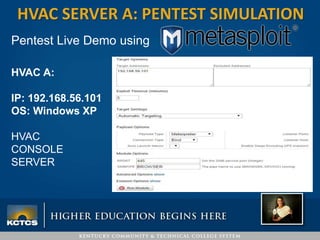
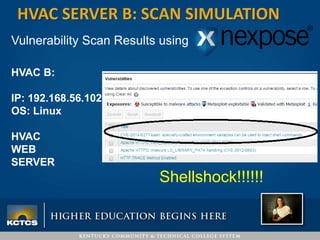
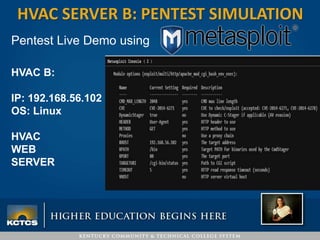
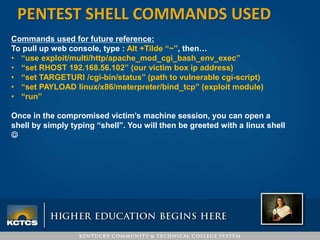
Robbie Corley presents on conducting pentests to find vulnerabilities in networks. A pentest involves simulated attacks against systems to validate vulnerabilities found in scans. Rapid7 is recommended for its pre-compiled exploits and free community tools. Corley demonstrates pentests against example HVAC systems, exploiting vulnerabilities on Windows and Linux servers like Shellshock. He also discusses using social engineering phishing modules like the open-source SPTOOLKIT to test user awareness through simulated phishing emails.