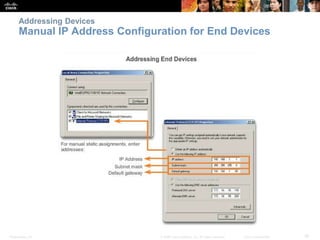
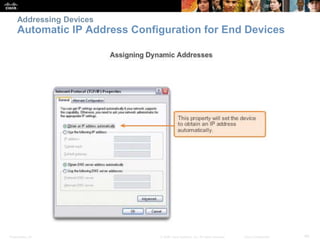
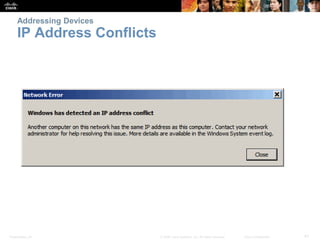
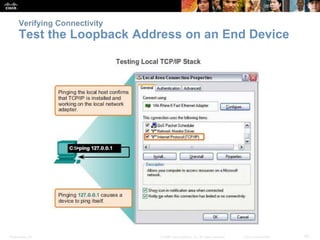
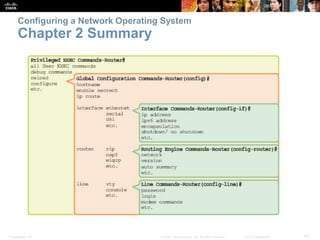
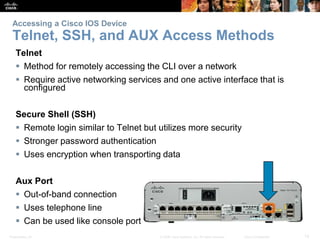
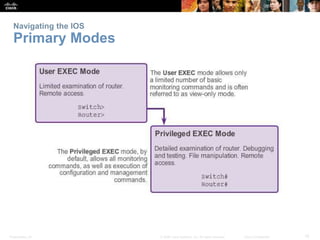
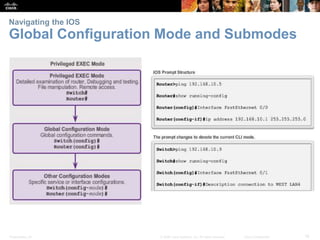
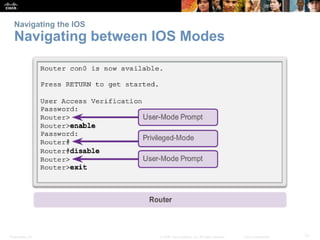
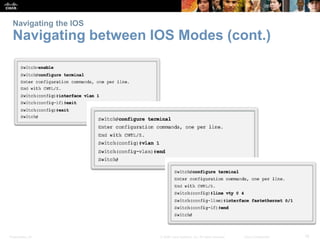
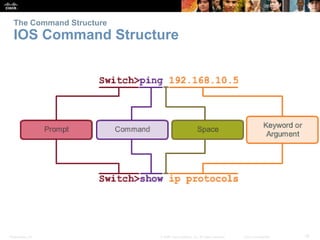
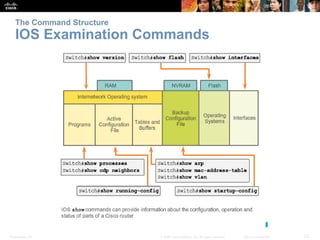
The document discusses configuring and navigating the Cisco IOS operating system. It covers accessing IOS using the console port or Telnet, navigating the command-line interface modes, setting hostnames and passwords to secure devices, assigning IP addresses, and verifying basic network connectivity. The objectives are to understand how to initially configure and secure a Cisco switch, assign IP addresses to devices, and test communication across a small network.















![Presentation_ID 35
© 2008 Cisco Systems, Inc. All rights reserved. Cisco Confidential
Saving Configurations
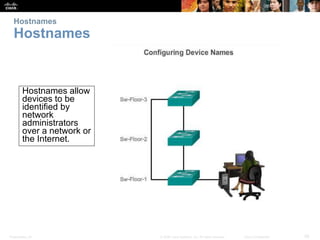
Configuration Files
Switch# reload
System configuration has
been modified. Save?
[yes/no]: n
Proceed with reload?
[confirm]
Startup configuration is
removed by using
the erase startup-config
Switch# erase startup-config
On a switch you must
also issue the delete
vlan.dat
Switch# delete vlan.dat
Delete filename [vlan.dat]?
Delete flash:vlan.dat?
[confirm]](https://image.slidesharecdn.com/itninstructorpptchapter2-230214085018-af97e462/85/ITN_instructorPPT_Chapter2-pptx-35-320.jpg)