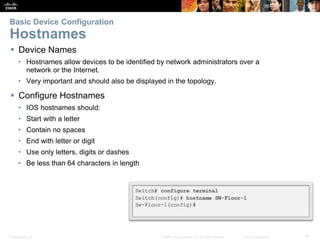
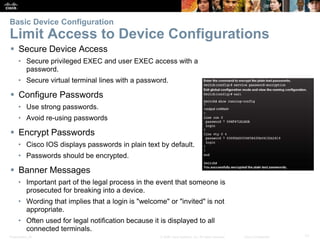
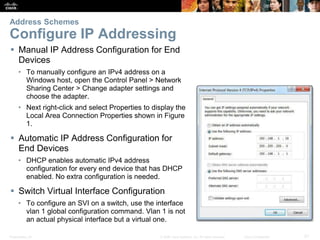
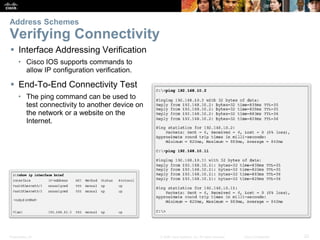
This document provides instructions on configuring network devices using Cisco IOS software. It covers topics such as navigating the Cisco IOS command line interface, setting hostnames and passwords, saving configurations, assigning IP addresses, and testing connectivity. The document is divided into several sections that explain how to initially access Cisco devices, secure device access, configure basic settings like IP addressing, and verify connectivity between devices on the network.