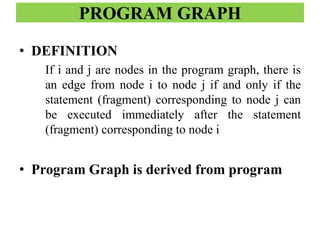
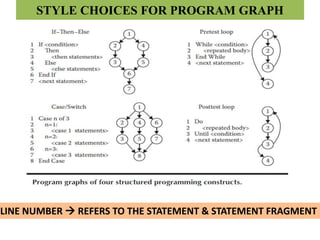
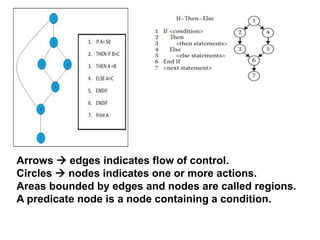
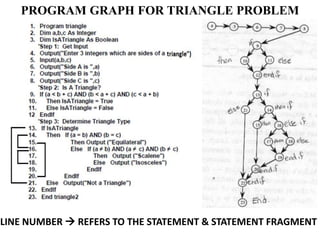
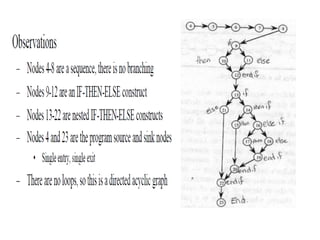
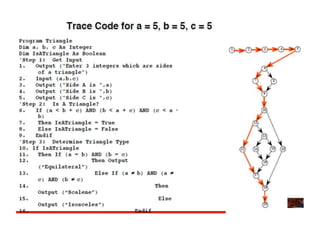
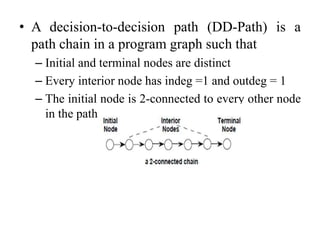
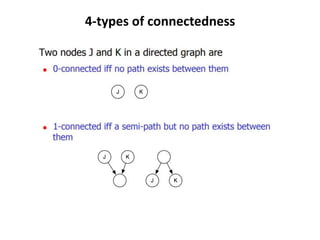
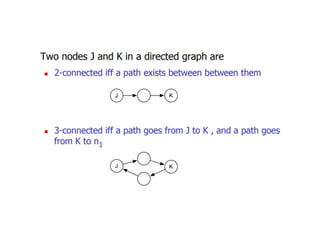
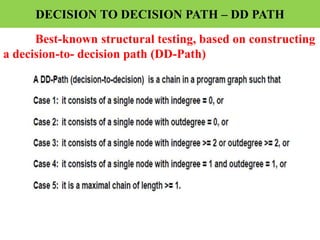
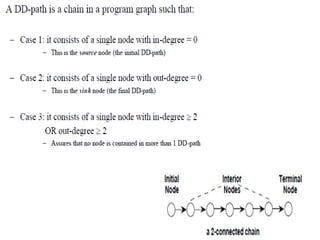
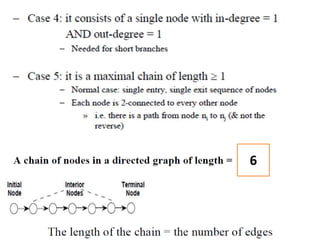
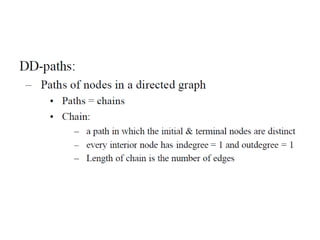
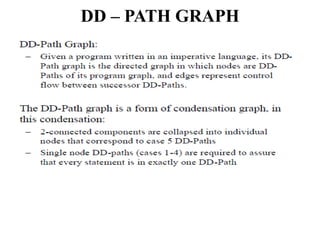
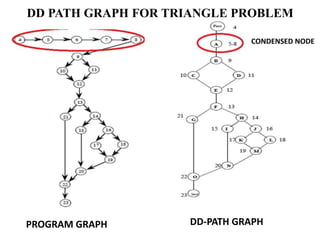
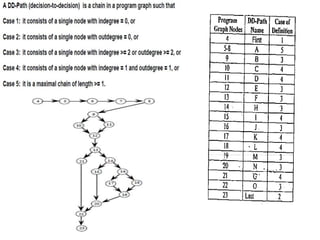
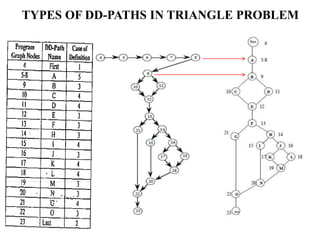
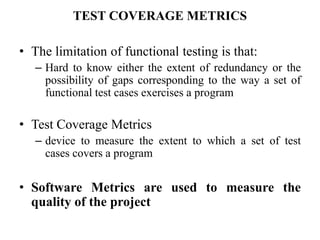
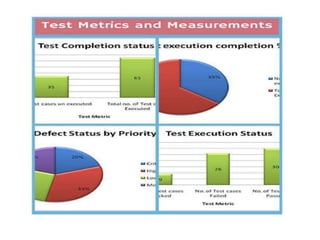
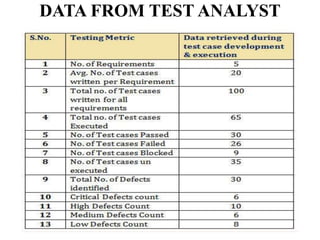
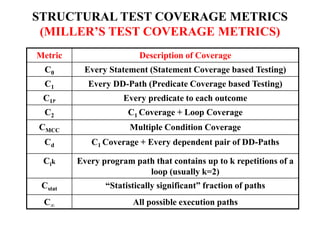
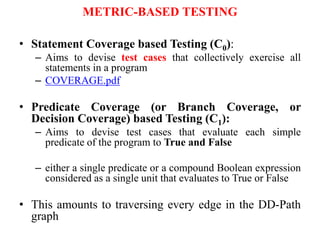
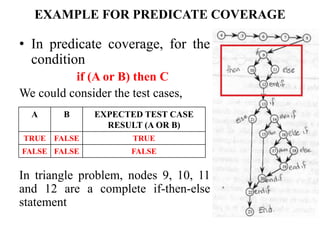
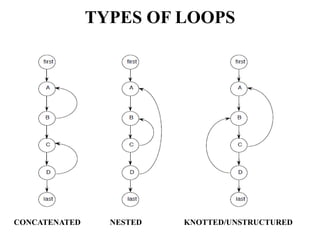
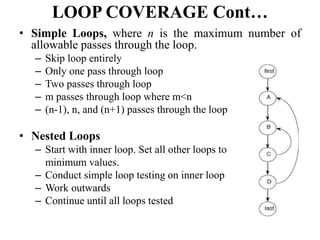
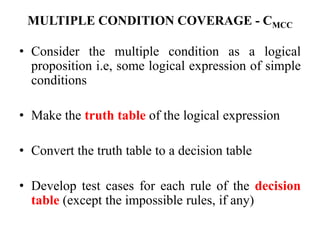
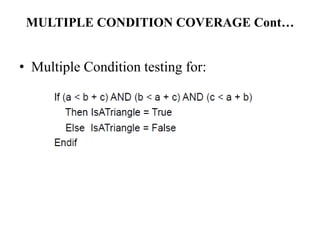
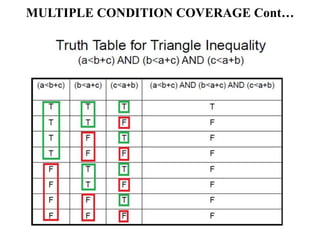
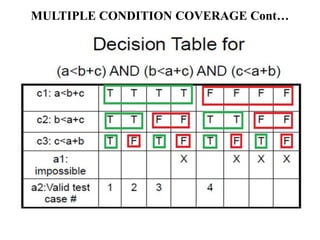
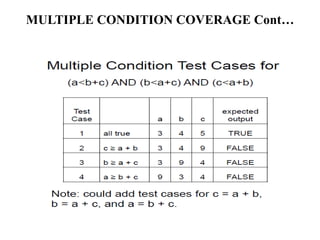
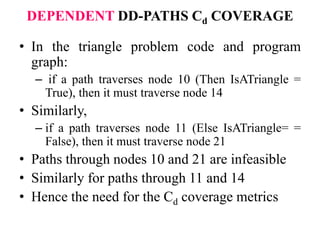
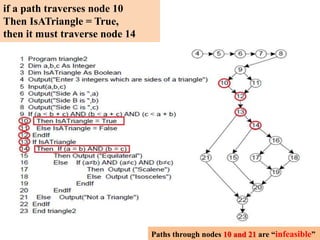
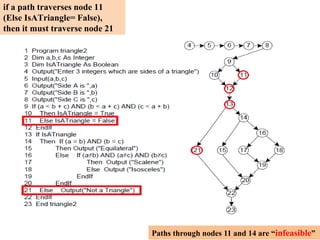
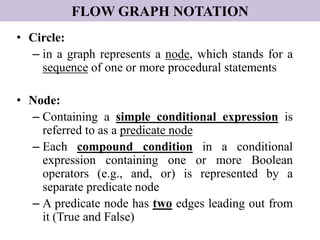
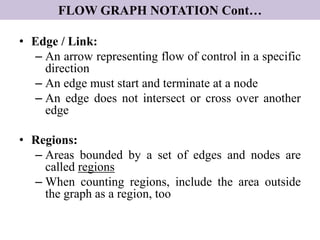
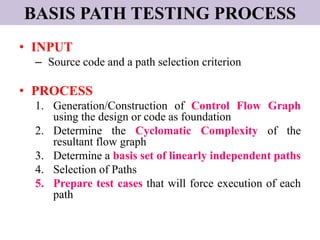
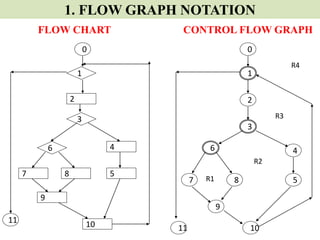
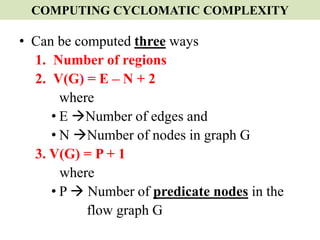
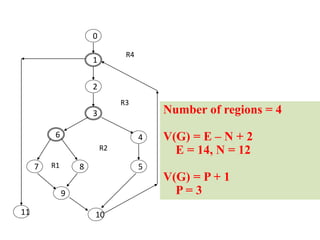
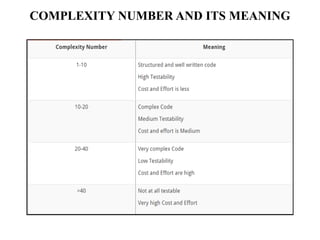
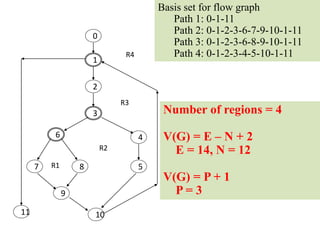
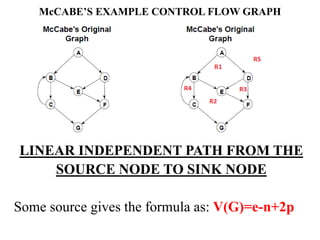
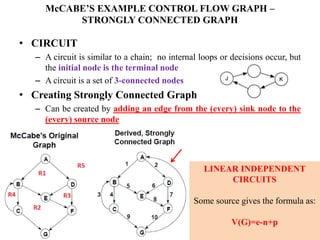
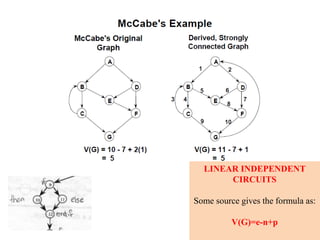
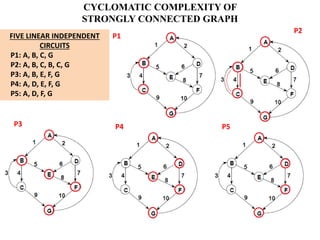
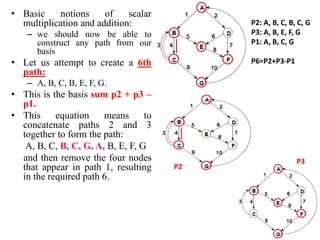
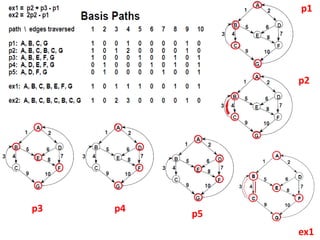
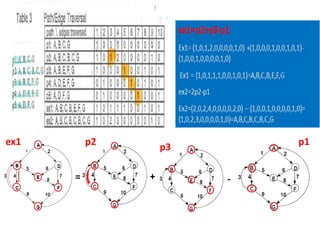
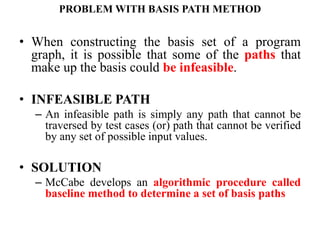
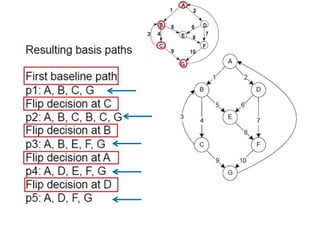
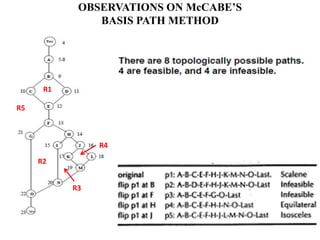
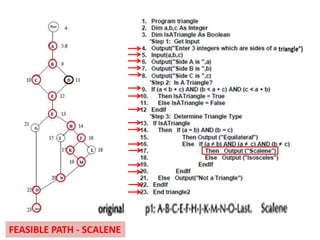
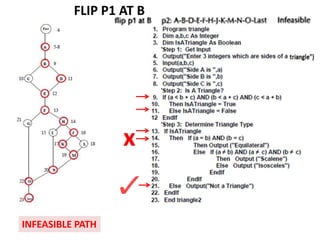
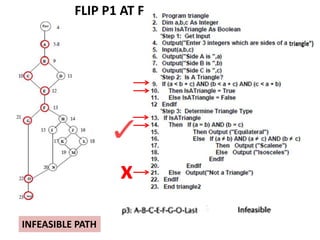
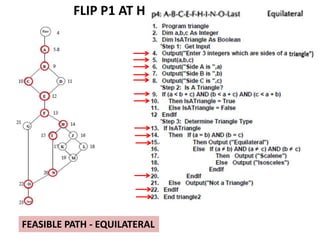
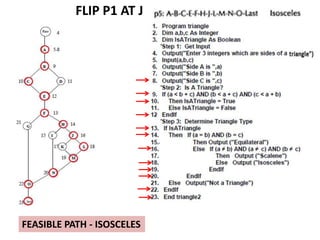
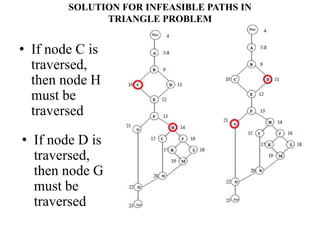
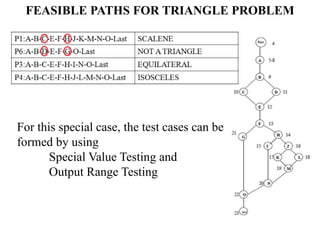
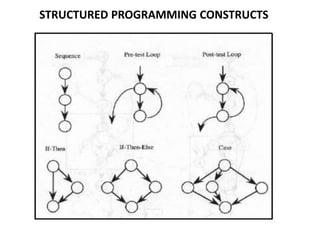
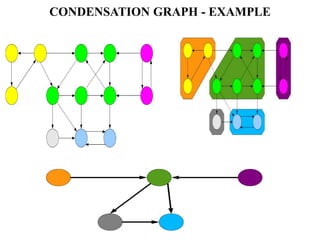
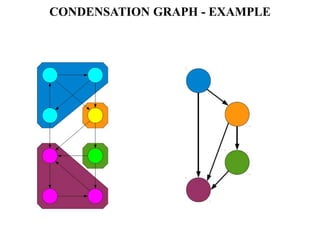
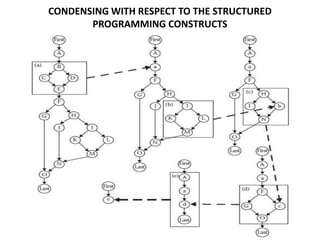
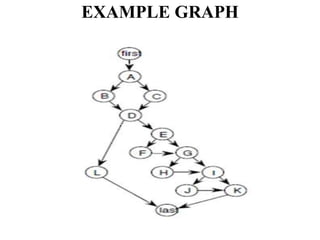
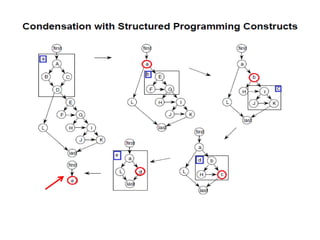
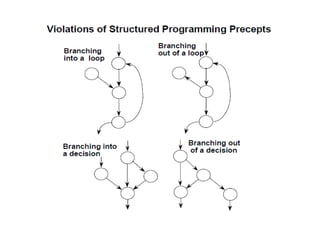
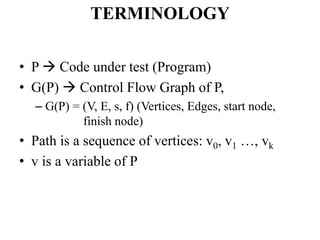
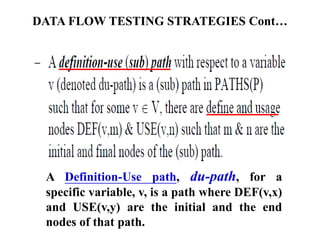
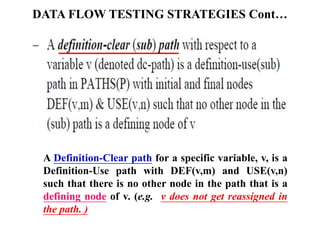
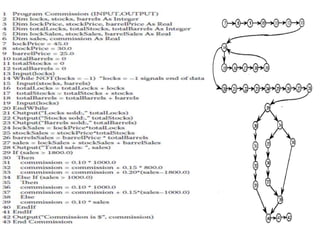
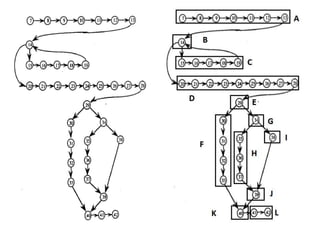
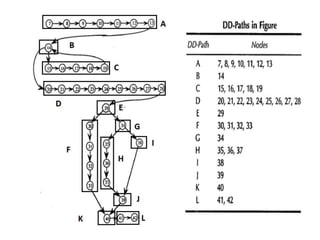
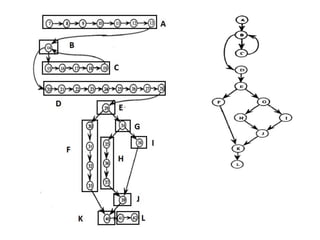
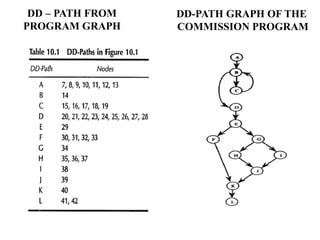
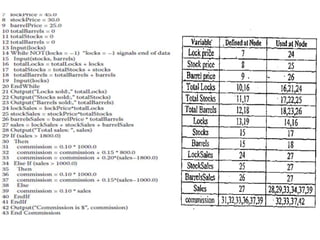
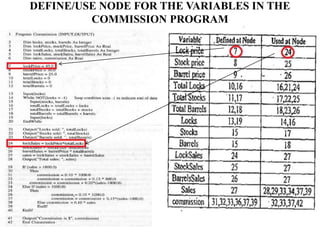
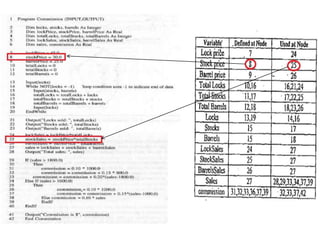
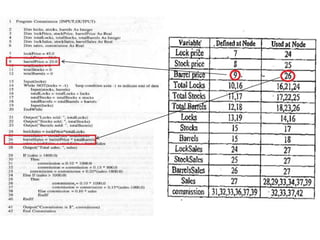
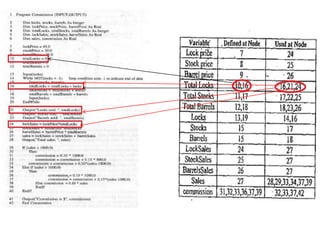
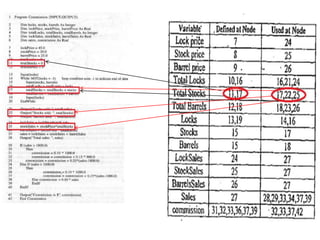
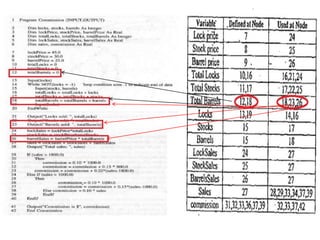
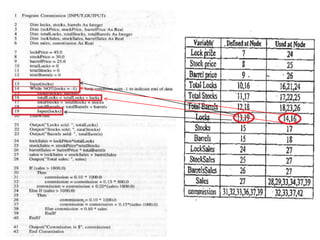
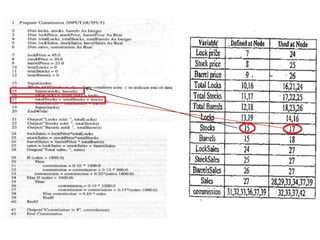
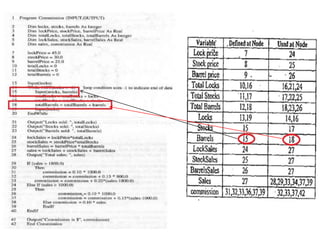
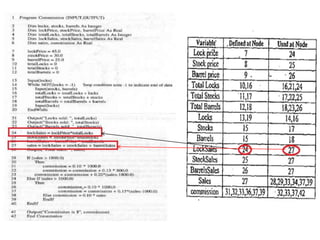
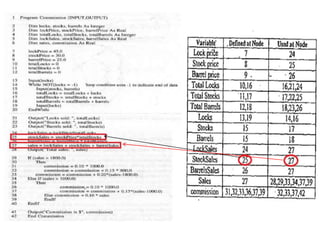
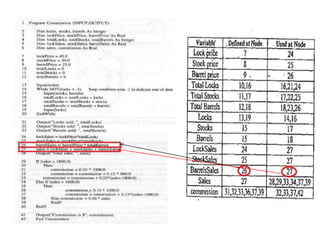
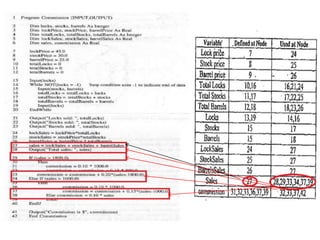
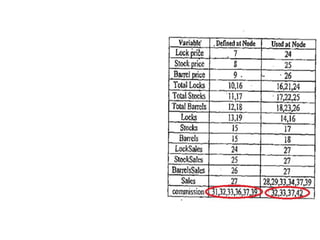
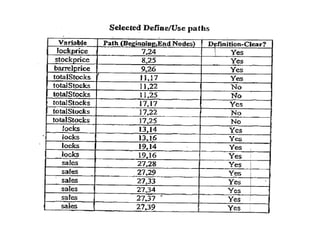
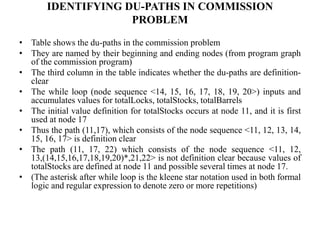
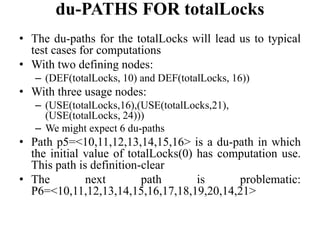
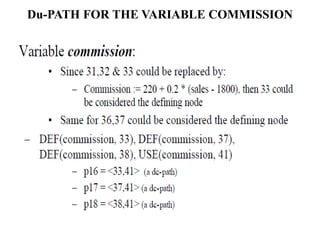
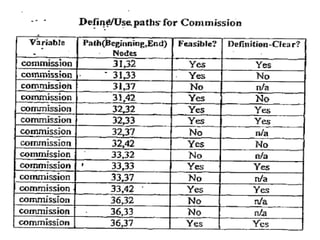
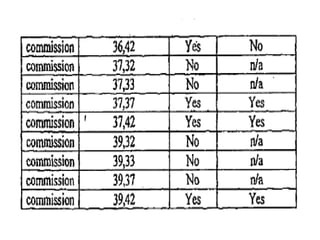
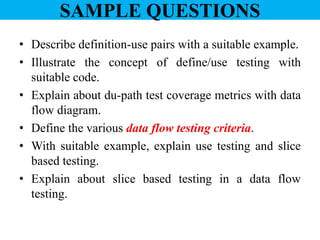
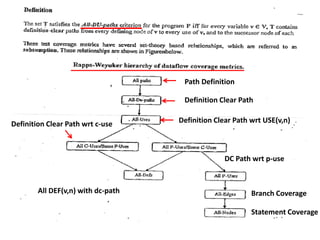
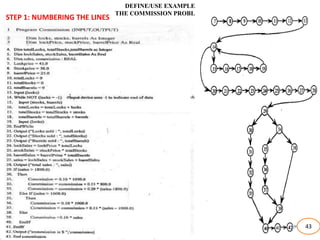
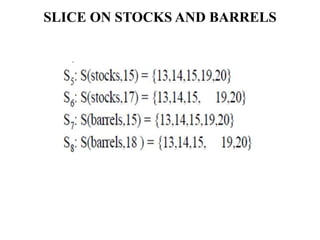
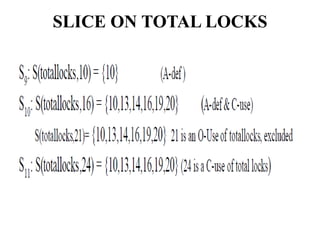
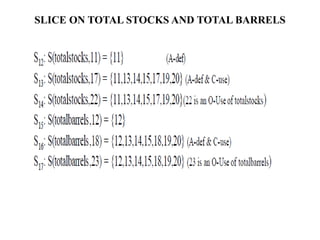
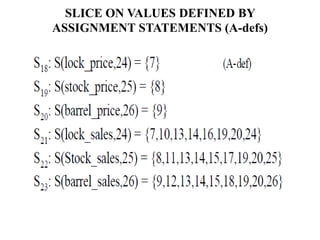
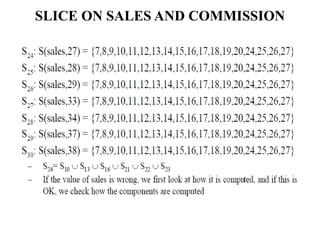
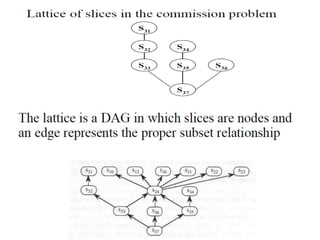
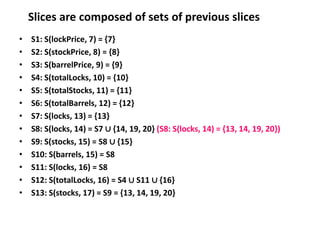
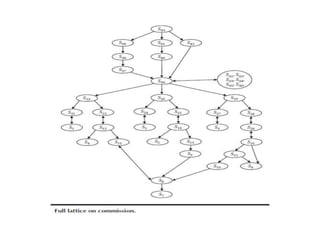
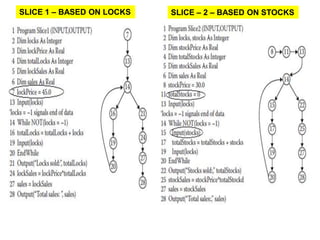
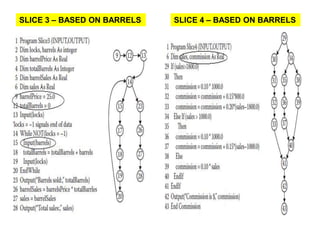
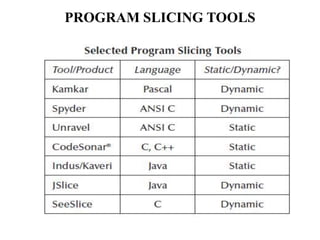
The document discusses white-box testing techniques focusing on path testing and data flow testing within software engineering. It outlines the concepts of control flow graphs, decision-to-decision paths, and various path selection criteria to enhance test coverage and identify faults in code. Additionally, it presents metrics for evaluating test coverage, such as statement, branch, and predicate coverage, as well as an analysis of cyclomatic complexity to guide the development of effective test cases.