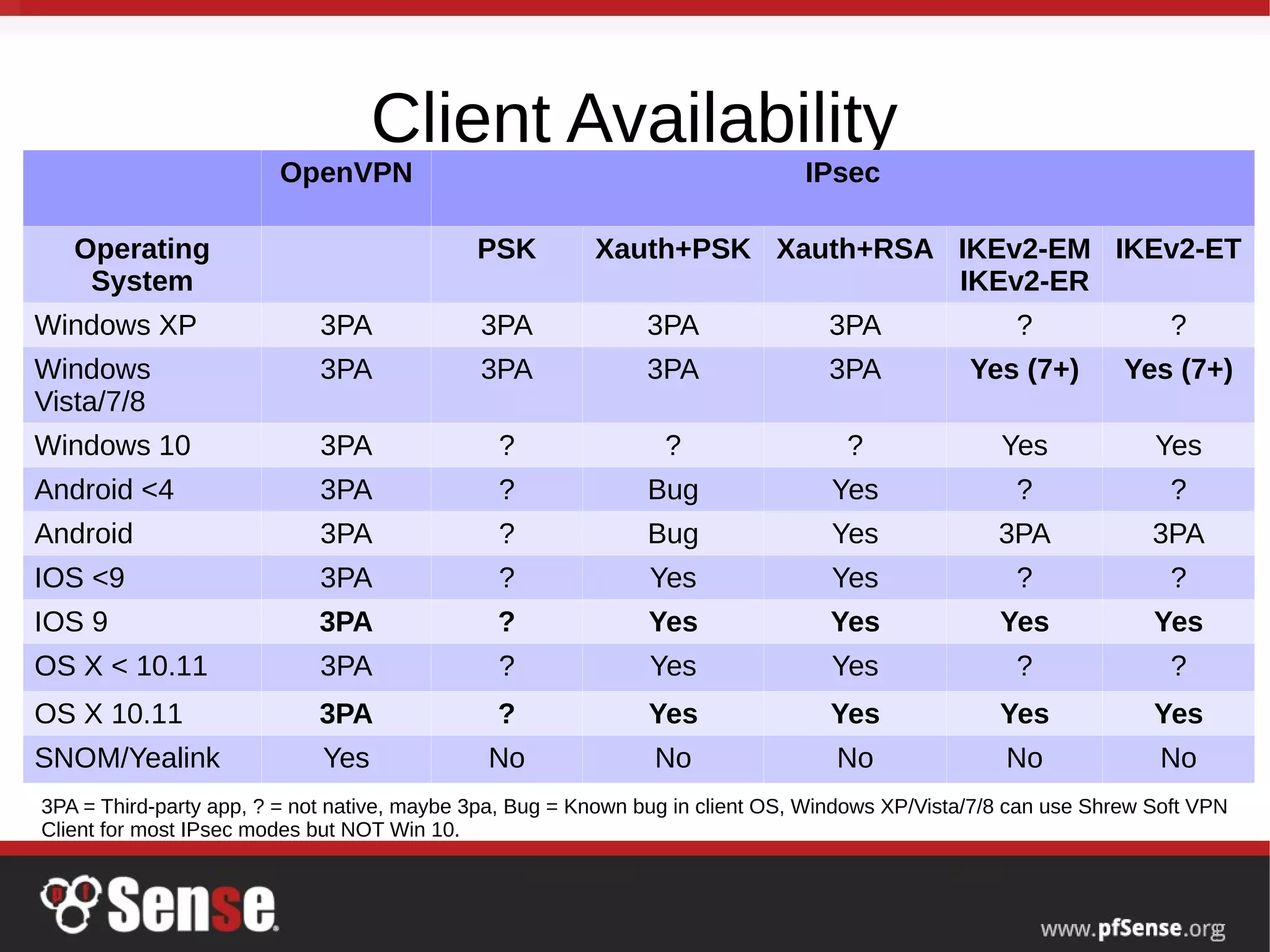
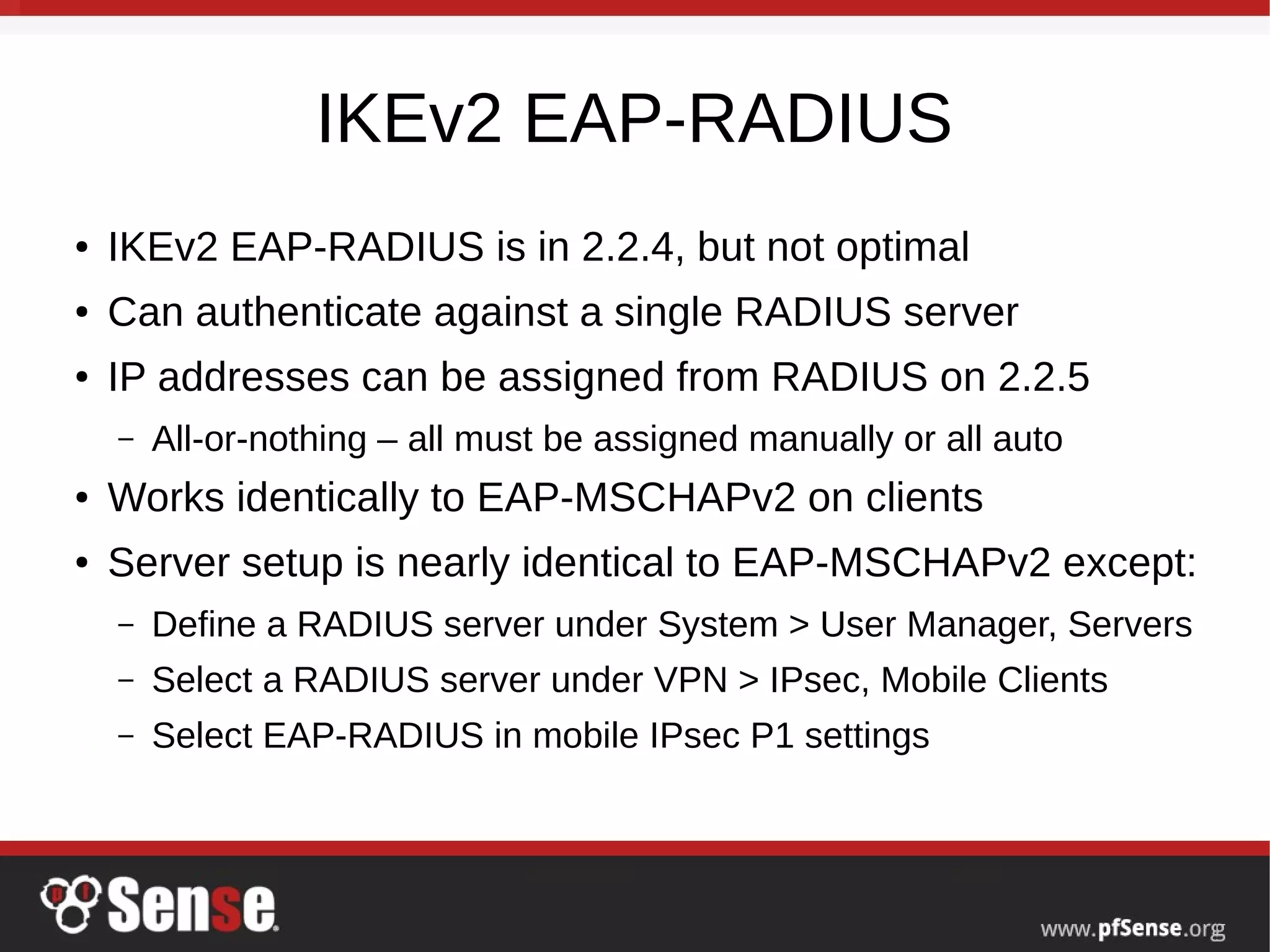
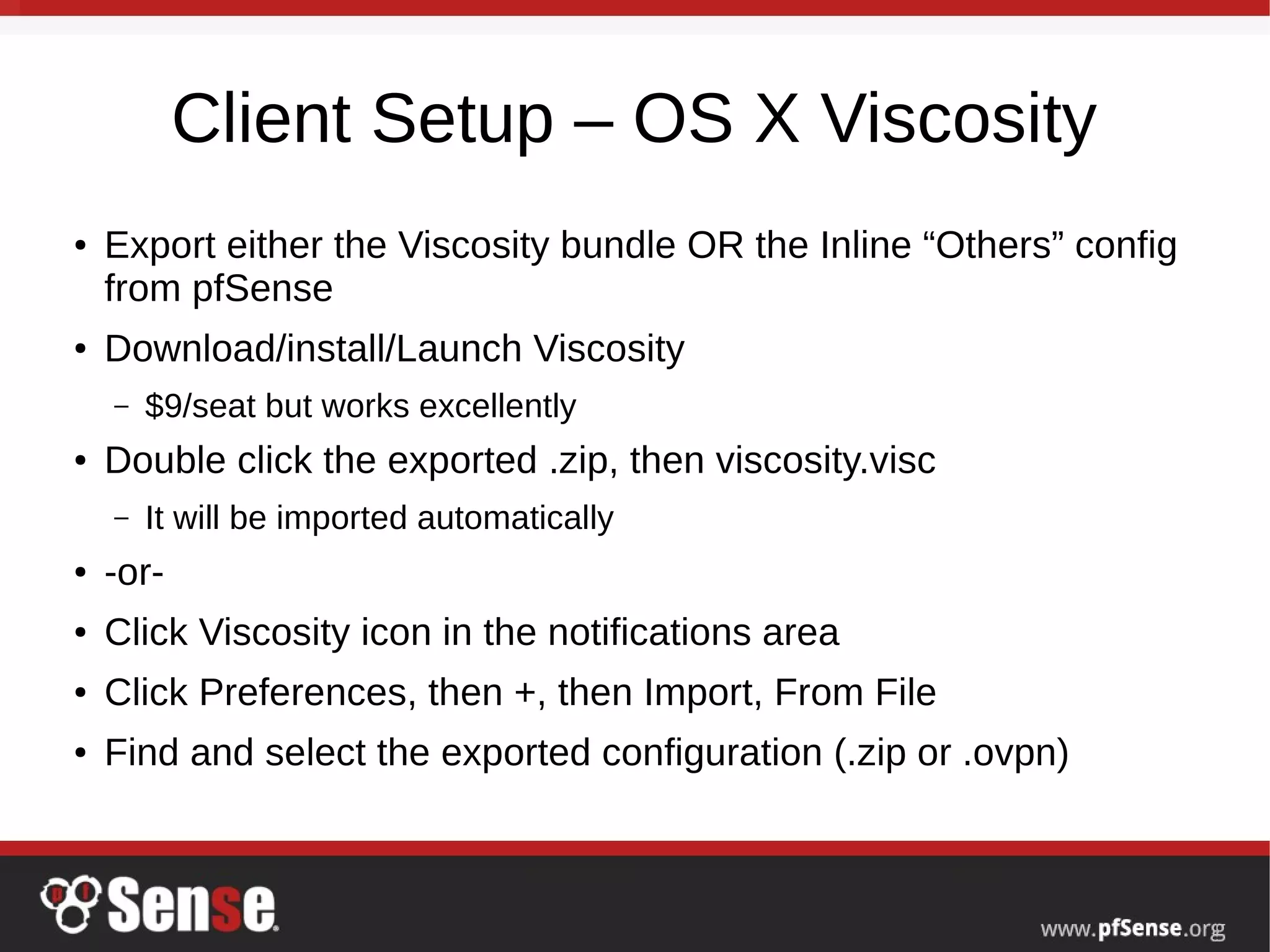
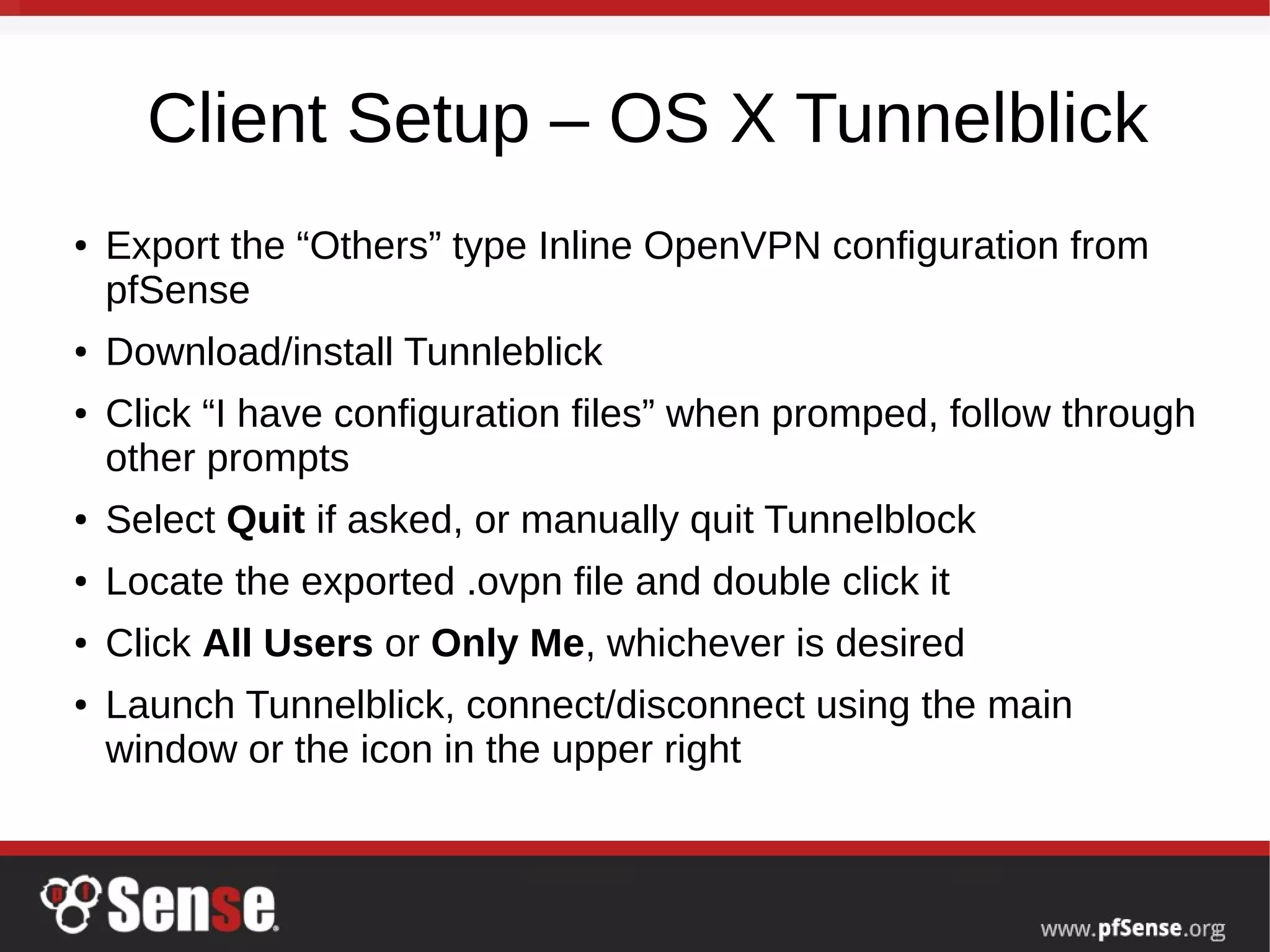
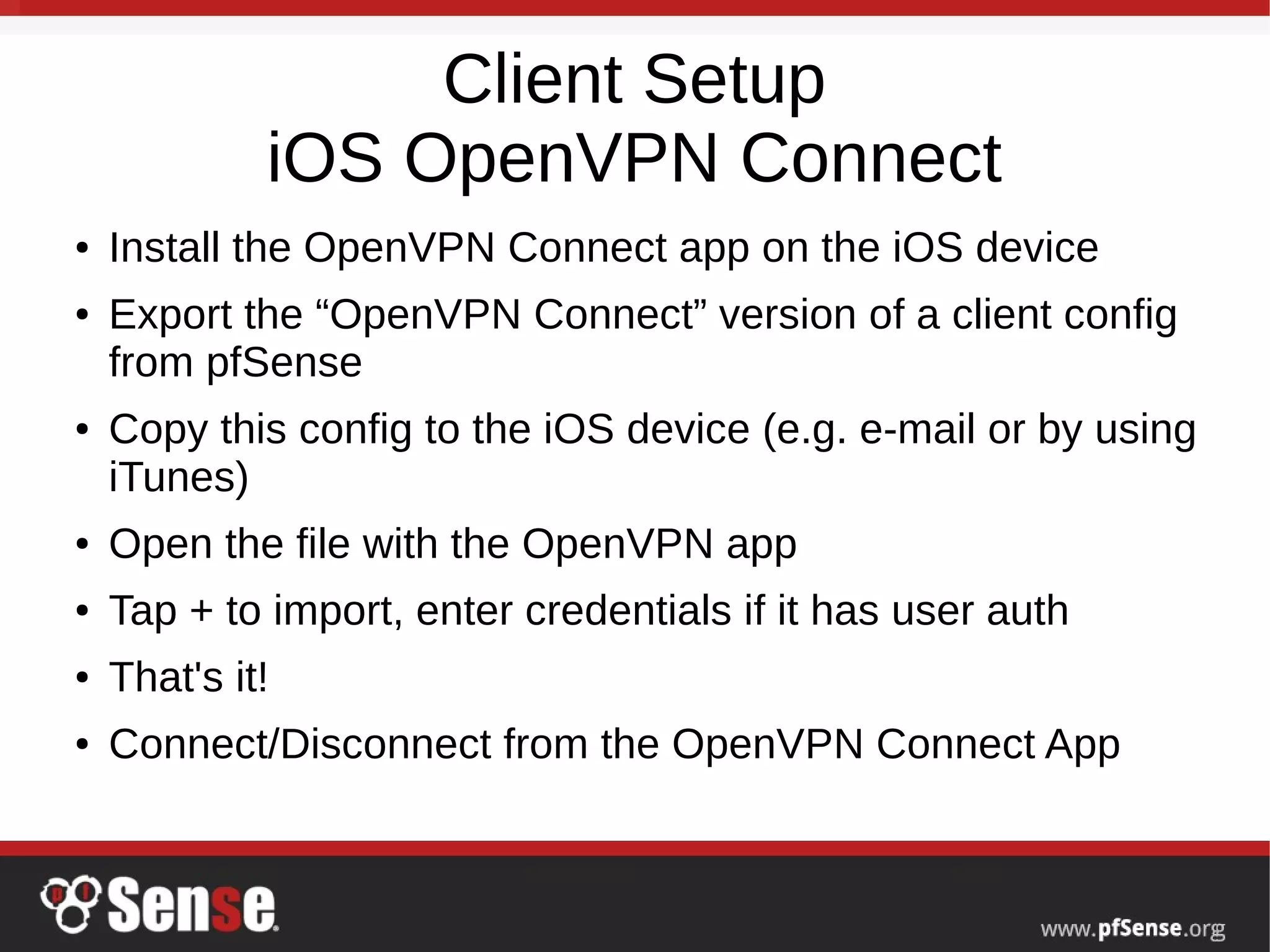
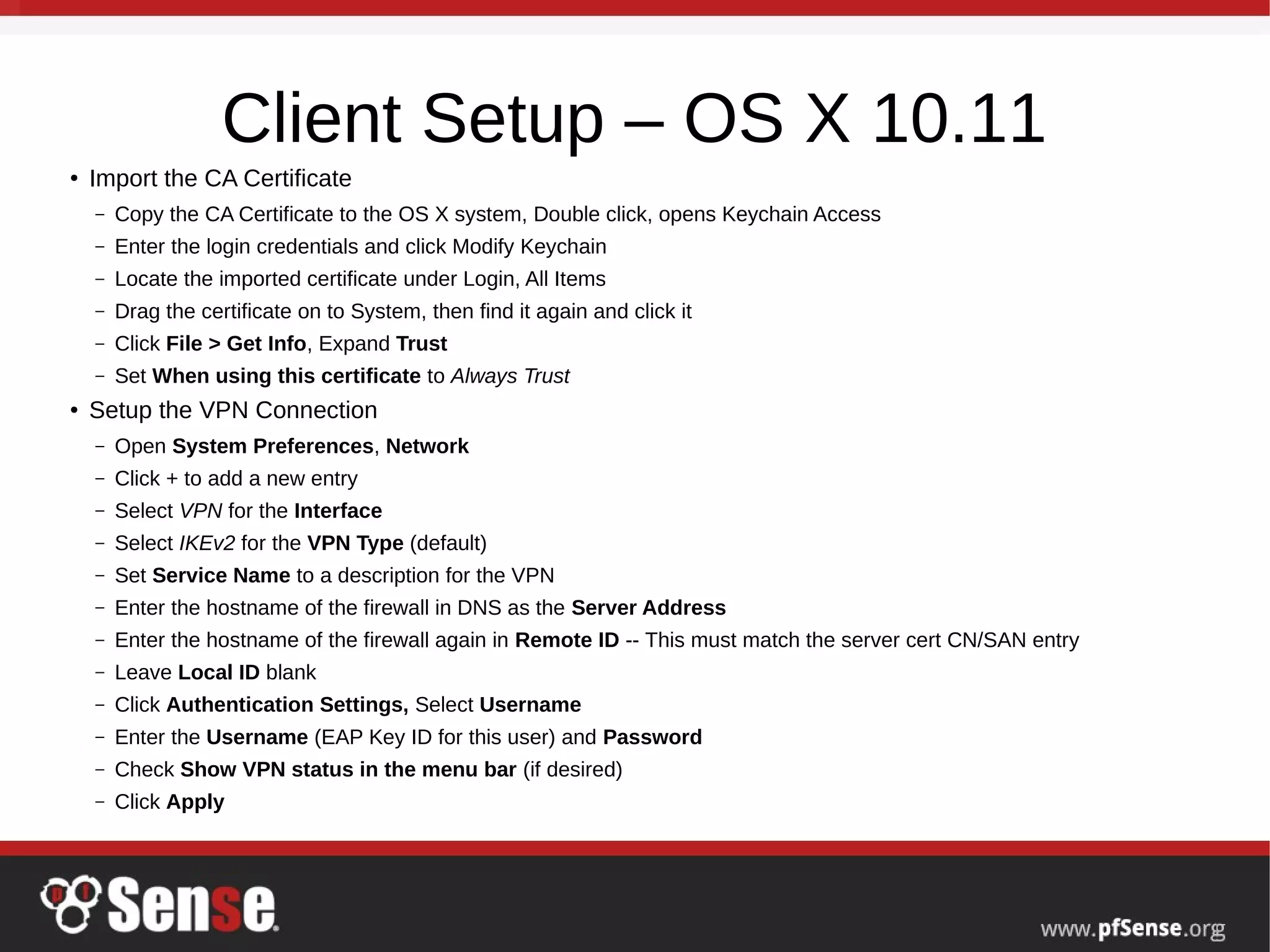
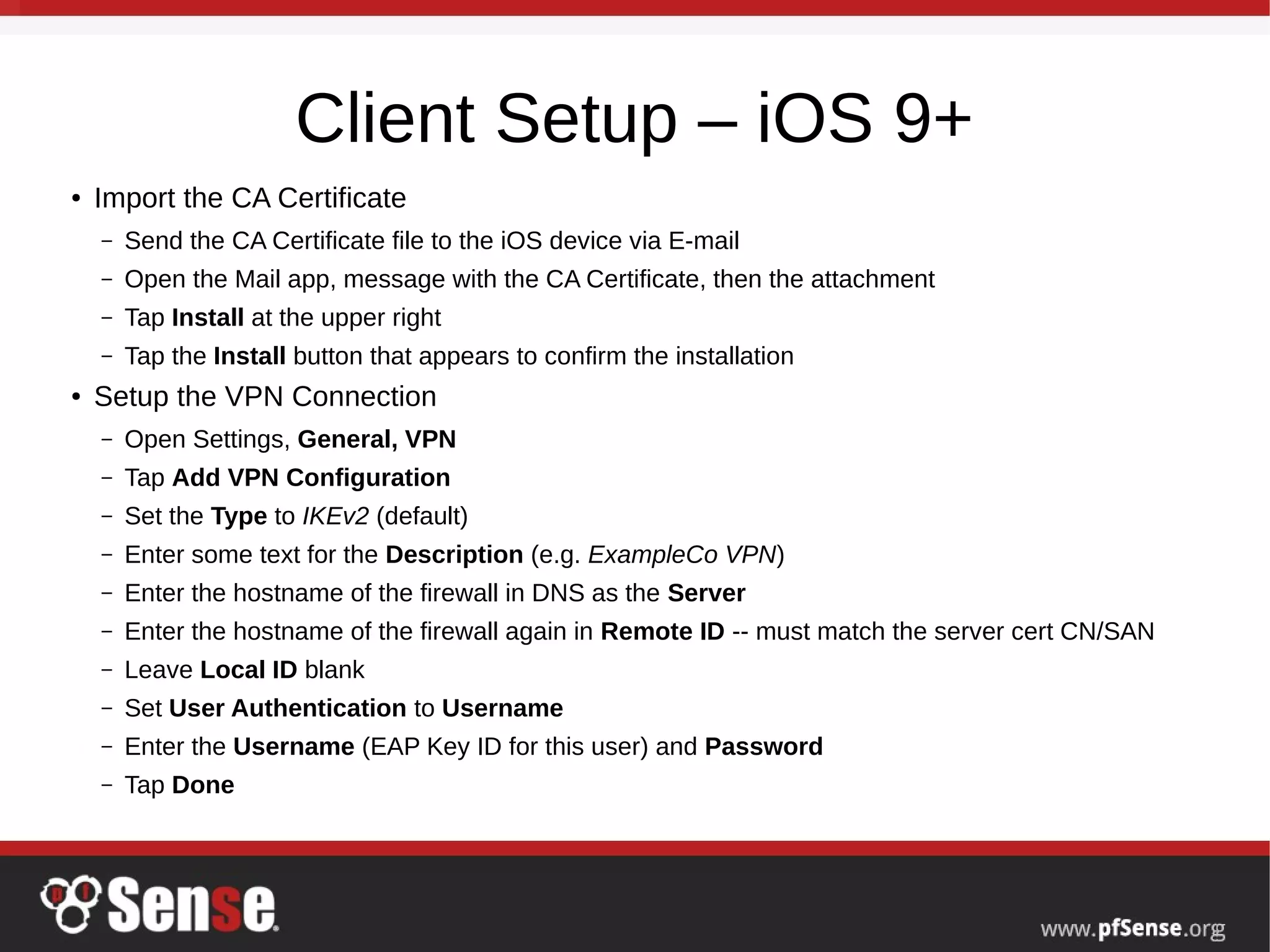
This document summarizes a hangout about remote access VPNs on pfSense. It provides information on recent and upcoming releases of pfSense and improvements to IPsec and IKEv2 functionality. It also includes step-by-step guides for configuring and connecting OpenVPN and IKEv2 clients on Mac OS X and iOS devices.