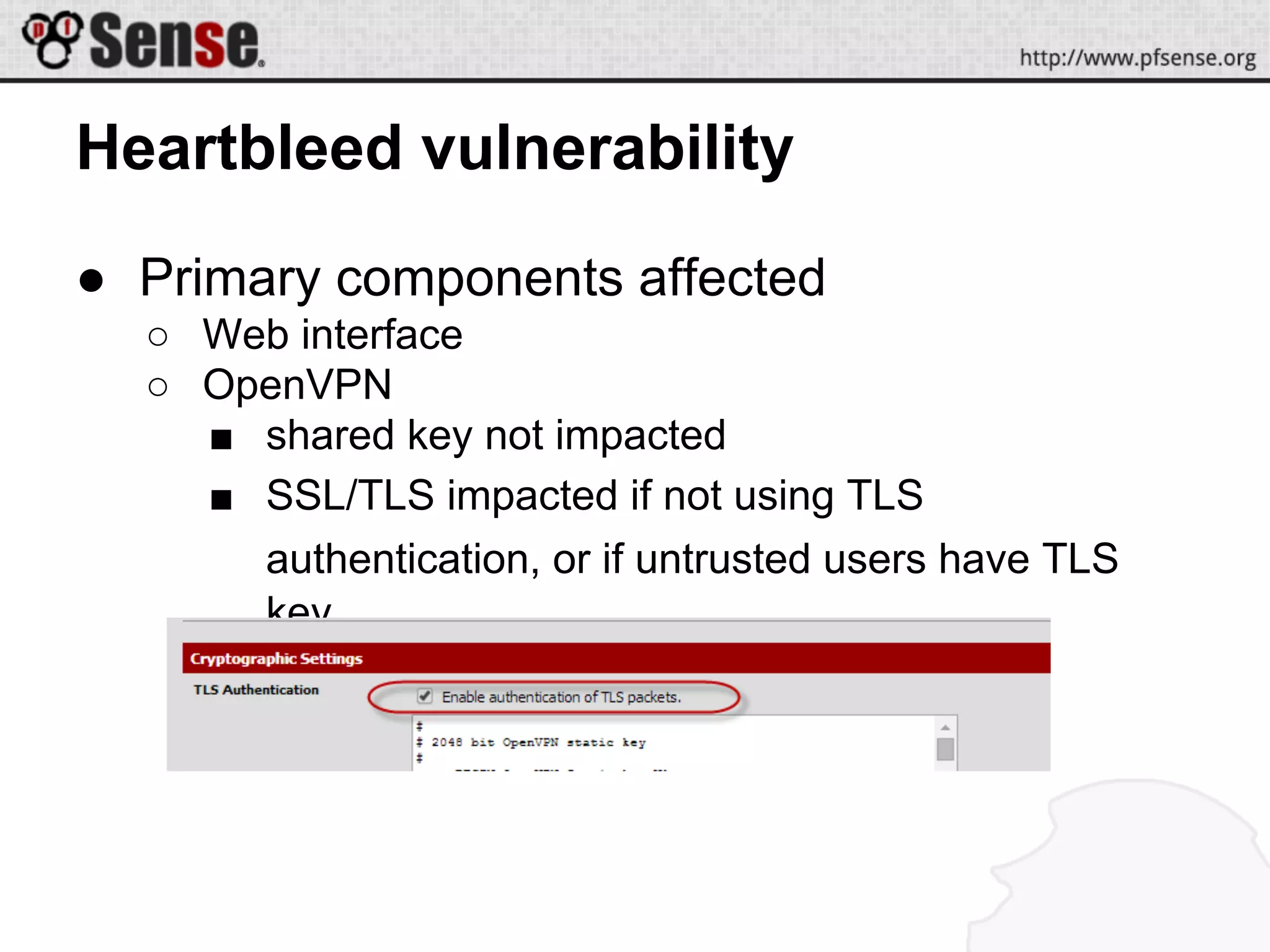
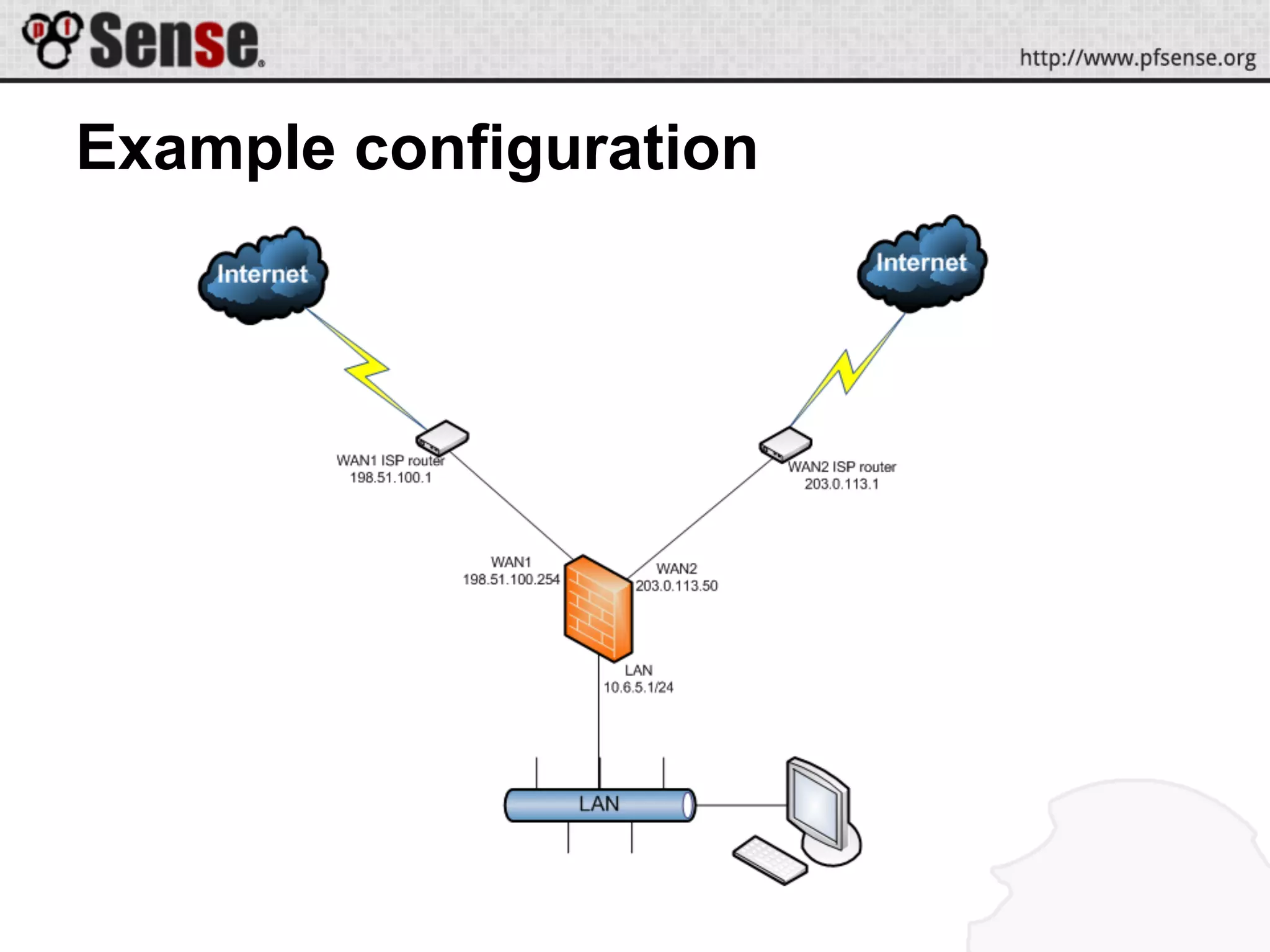
This document summarizes a pfSense hangout about multi-WAN configurations. It announces two new hardware platforms for pfSense and discusses the Heartbleed vulnerability in OpenSSL and its impact on pfSense. It then covers the goals and strategies for multi-WAN configurations, including redundancy, bandwidth aggregation, and service segregation. Various multi-WAN configuration examples and demos are provided. Troubleshooting tips are also included.