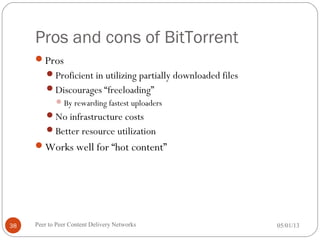
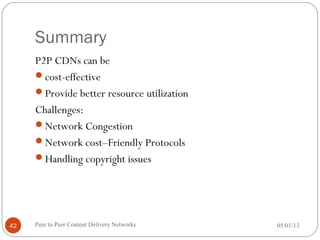
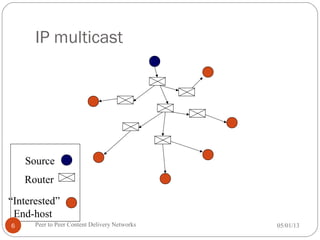
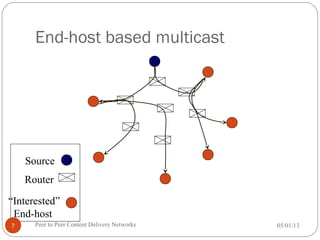
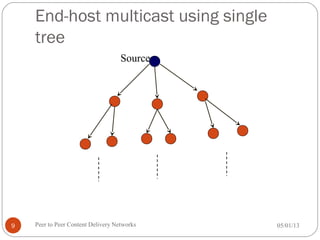
The seminar discusses peer-to-peer (P2P) content delivery networks, highlighting their importance in efficiently distributing large files among users without a centralized source. Different types of P2P systems such as centralized (like Napster) and decentralized (like Gnutella and BitTorrent) are explored, along with their advantages, challenges, and underlying technologies. Key concepts like swarming, piece selection strategies, and the implications of network congestion and legal issues are also addressed.



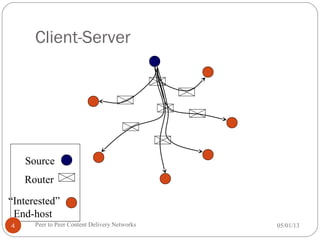
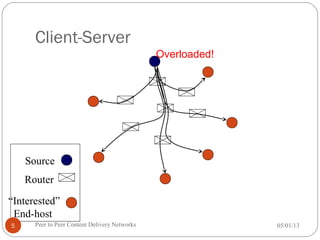




![Data types
All the data used in Bit-torrent communication is Bencoded.
Integer: 2011 Bencoded: i2011e
String: “Something” Bencoded: 9: Something
List: List[0]=1337 List[1]=“DEF” List[2]=“CON” Bencoded:
li1337e:3DEF:3CONe
Dictionary:Dictionary[“uname”]=“hpcbabu”
Dictionary[“password”]=“default” Benocded form
d5:uname7:hpcbabu8:password7:defaulte
05/01/13Peer to Peer Content Delivery Networks22](https://image.slidesharecdn.com/p2pcdn-130501065800-phpapp01/85/P2p-cdn-22-320.jpg)