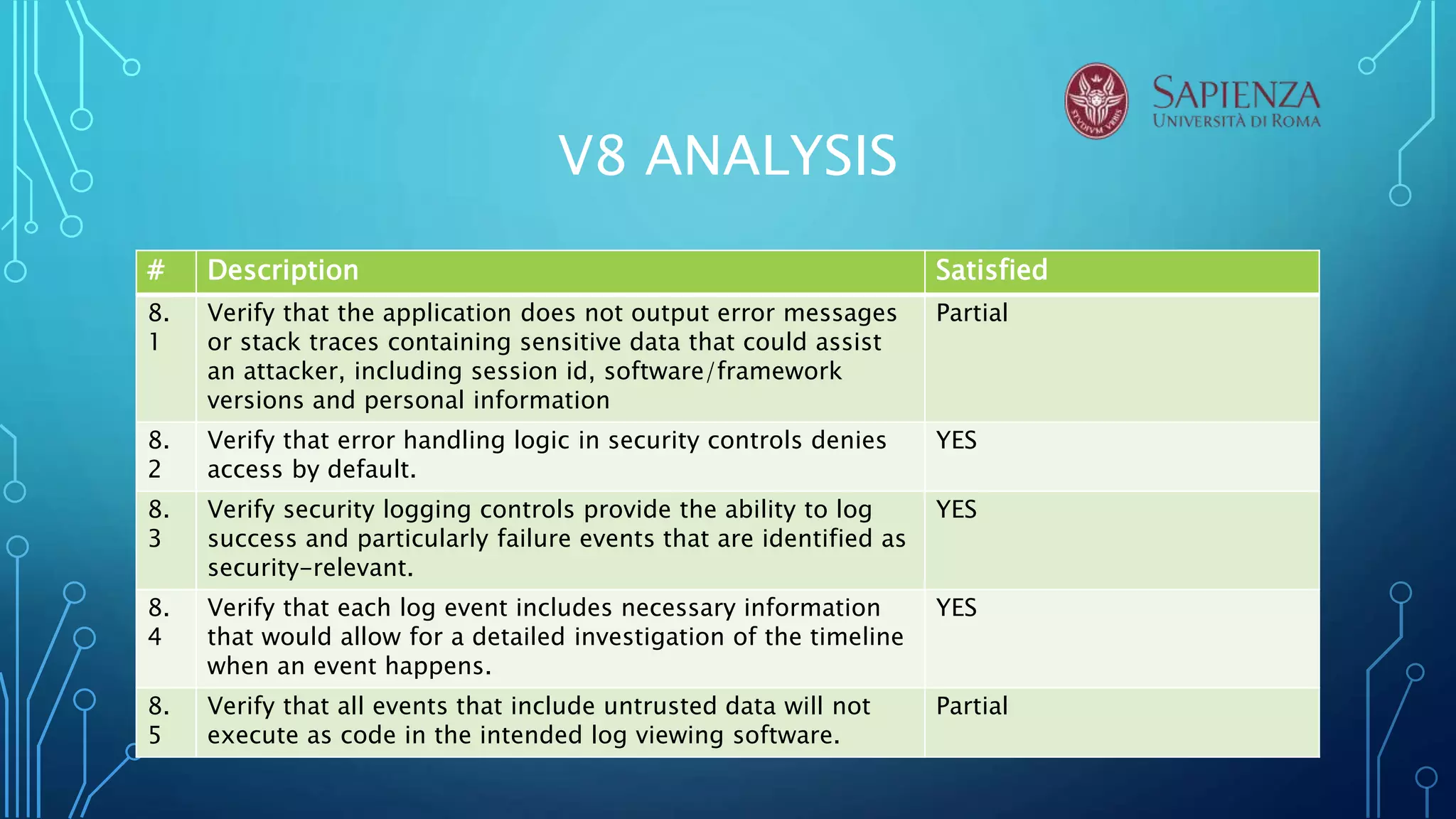
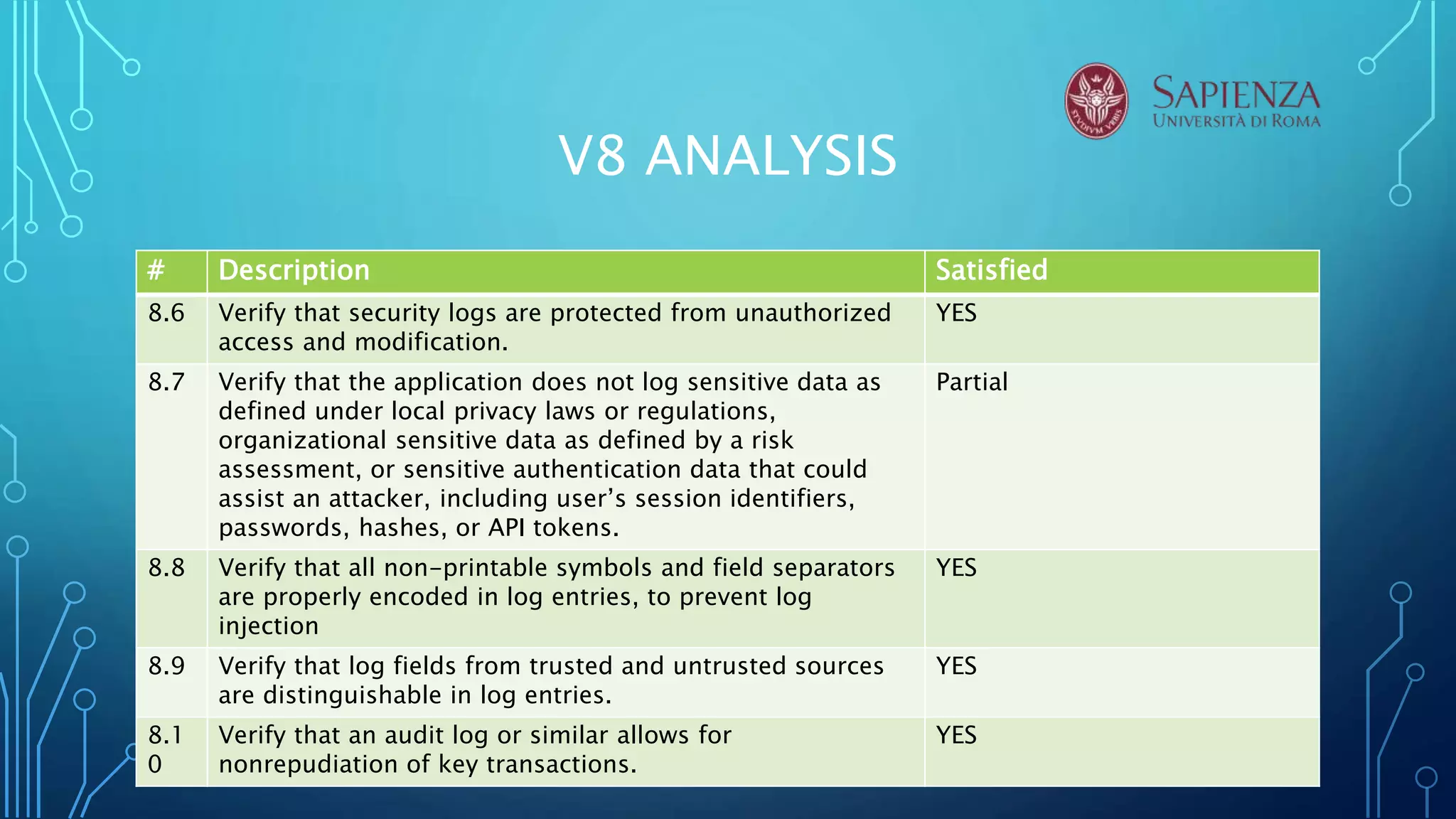
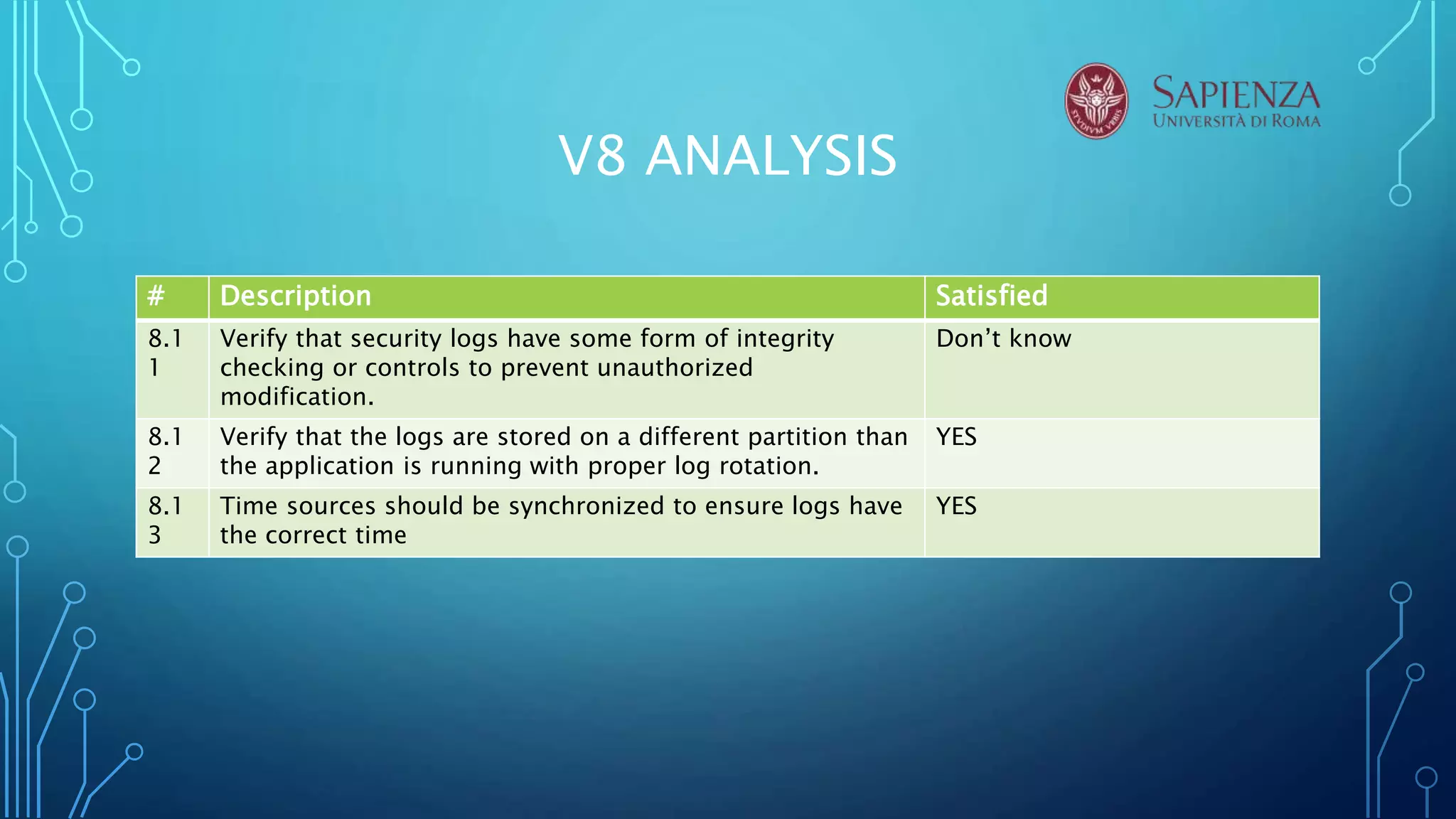
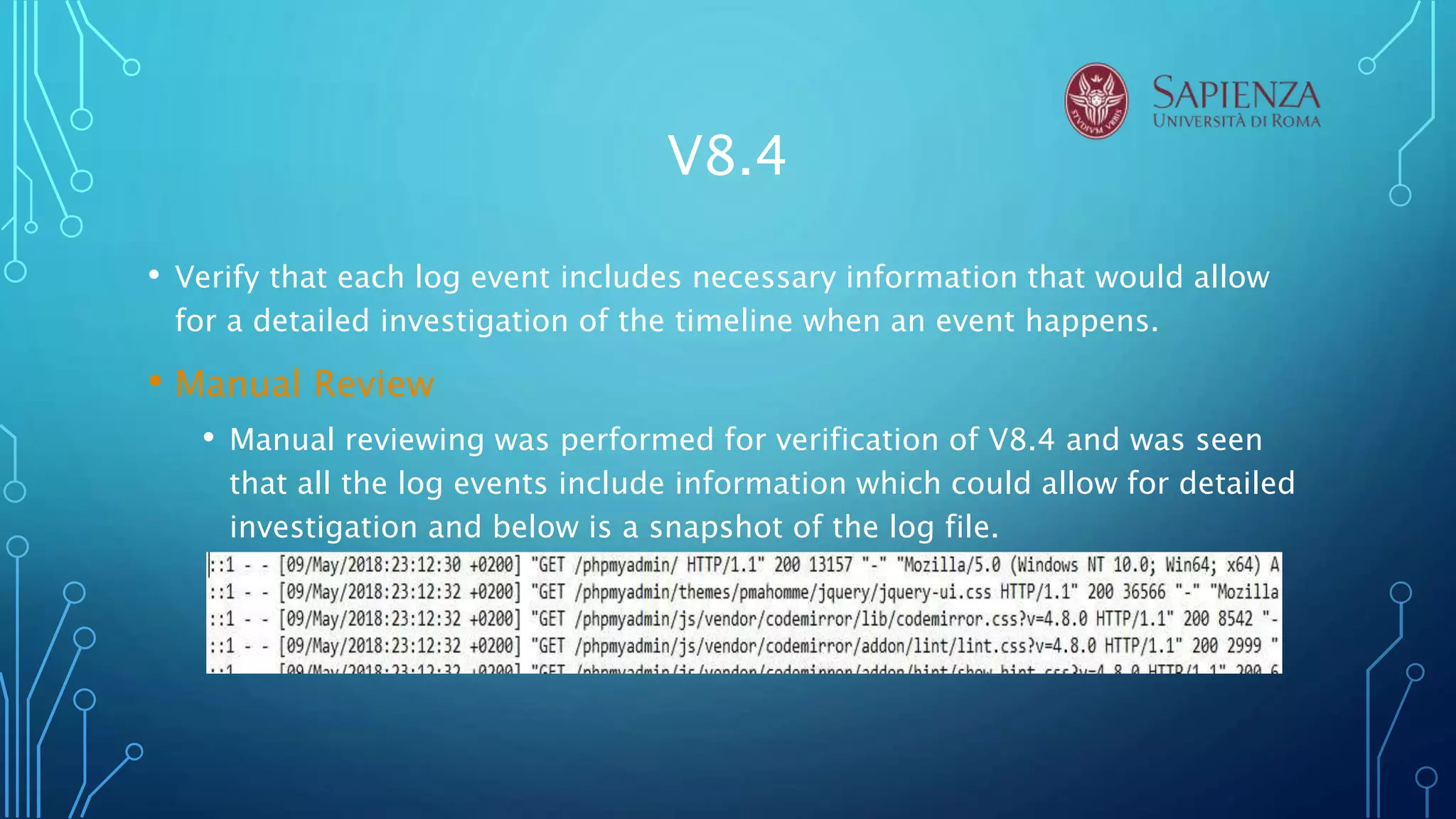
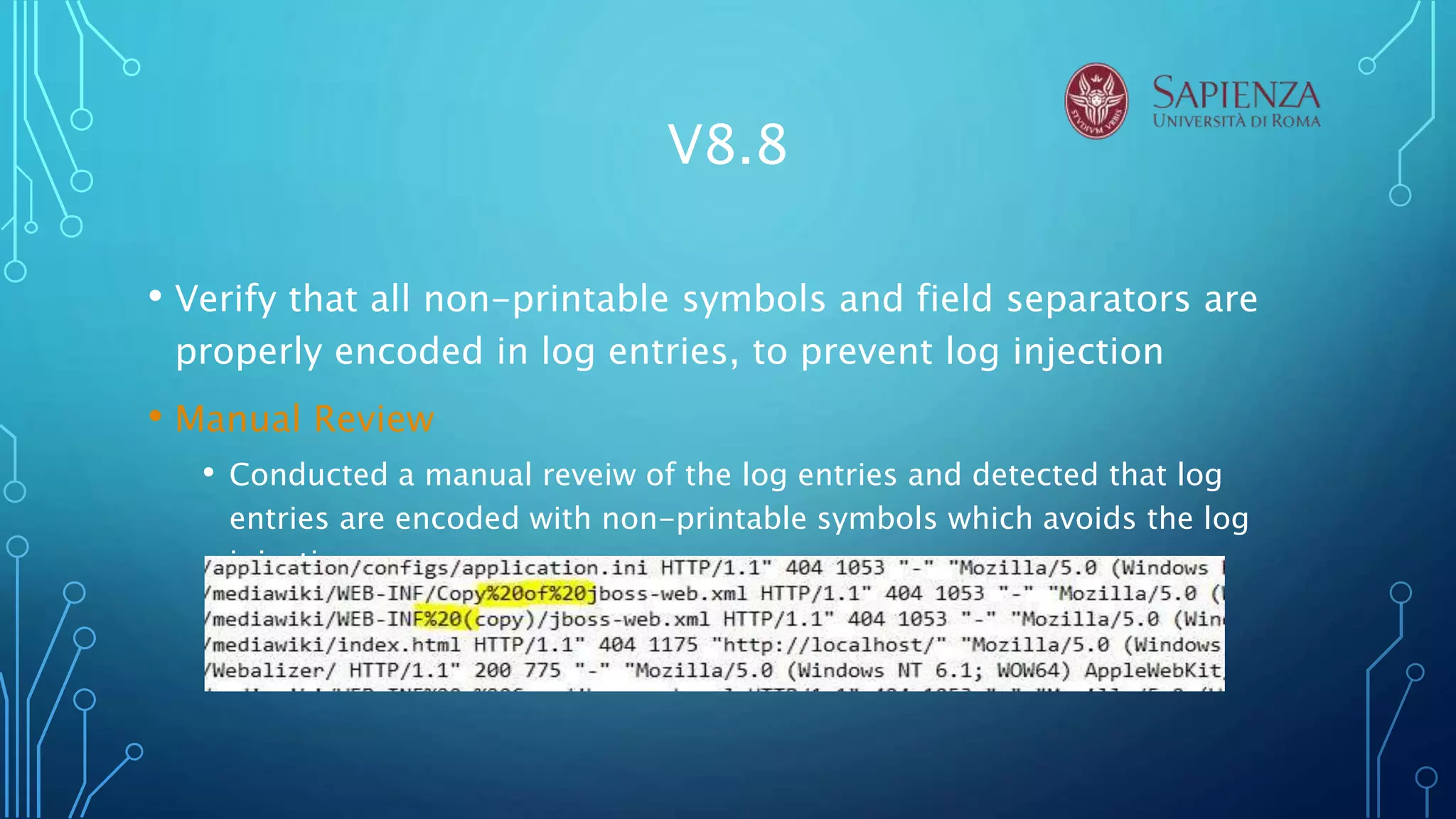
The document analyzes the error handling and logging verification requirements for MediaWiki version 8. Several tools were used to analyze MediaWiki including RIPS, VCG, VEGA, Acunetix. The analysis found that MediaWiki partially satisfies requirements around not outputting sensitive error messages, logs, and data. It was also found that logs should be better protected and distinguish trusted and untrusted data. The conclusion recommends discussing security design choices with developers and notes that RIPS, VCG, and Acunetix were most effective for source code analysis.