Embed presentation
Downloaded 13 times

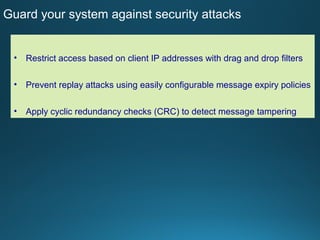





Anypoint Enterprise Security provides tools to block unauthorized access, prevent security attacks, and maintain data integrity and confidentiality. It allows users to restrict access by IP address, prevent replay attacks with message expiry policies, and detect tampering with CRC checks. The software also enables encryption of payloads, secure credential storage, and digital signatures to preserve integrity. Additionally, it leverages standards like SAML, OAuth, and WS-Security for authentication and uses LDAP stores for authorization when accessing APIs and SOA endpoints.









