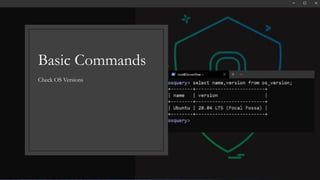
This document provides an introduction to OS Query, an open source tool for querying information about operating systems. It outlines lessons that will cover OS Query basics, deploying OS Query, and running basic commands. Examples of queries are provided to find running processes, network connections, kernel modules, and more. Use cases are described for how OS Query can be used to detect new listening processes, outbound network activity, deleted process binaries, and loaded kernel modules.