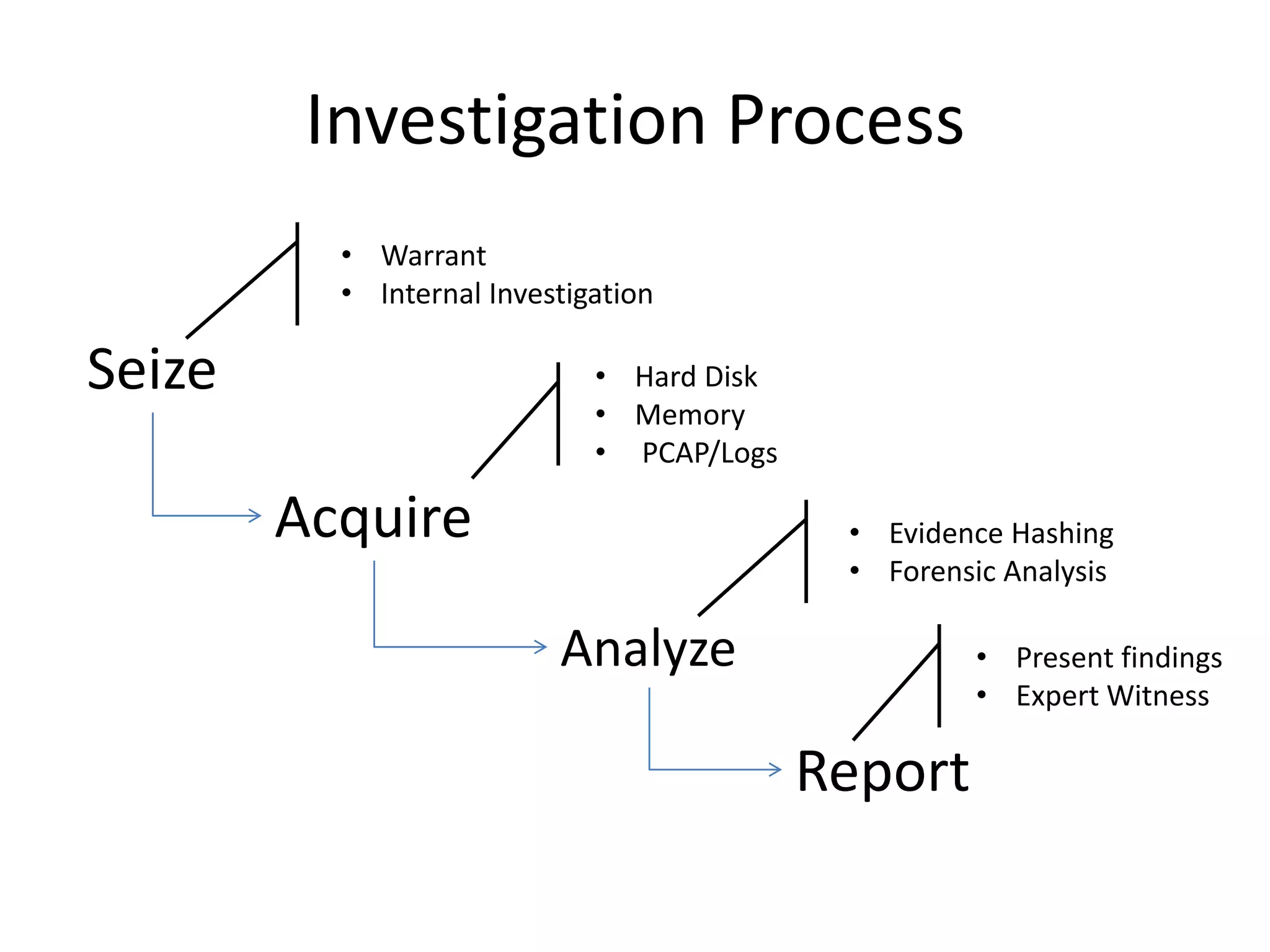
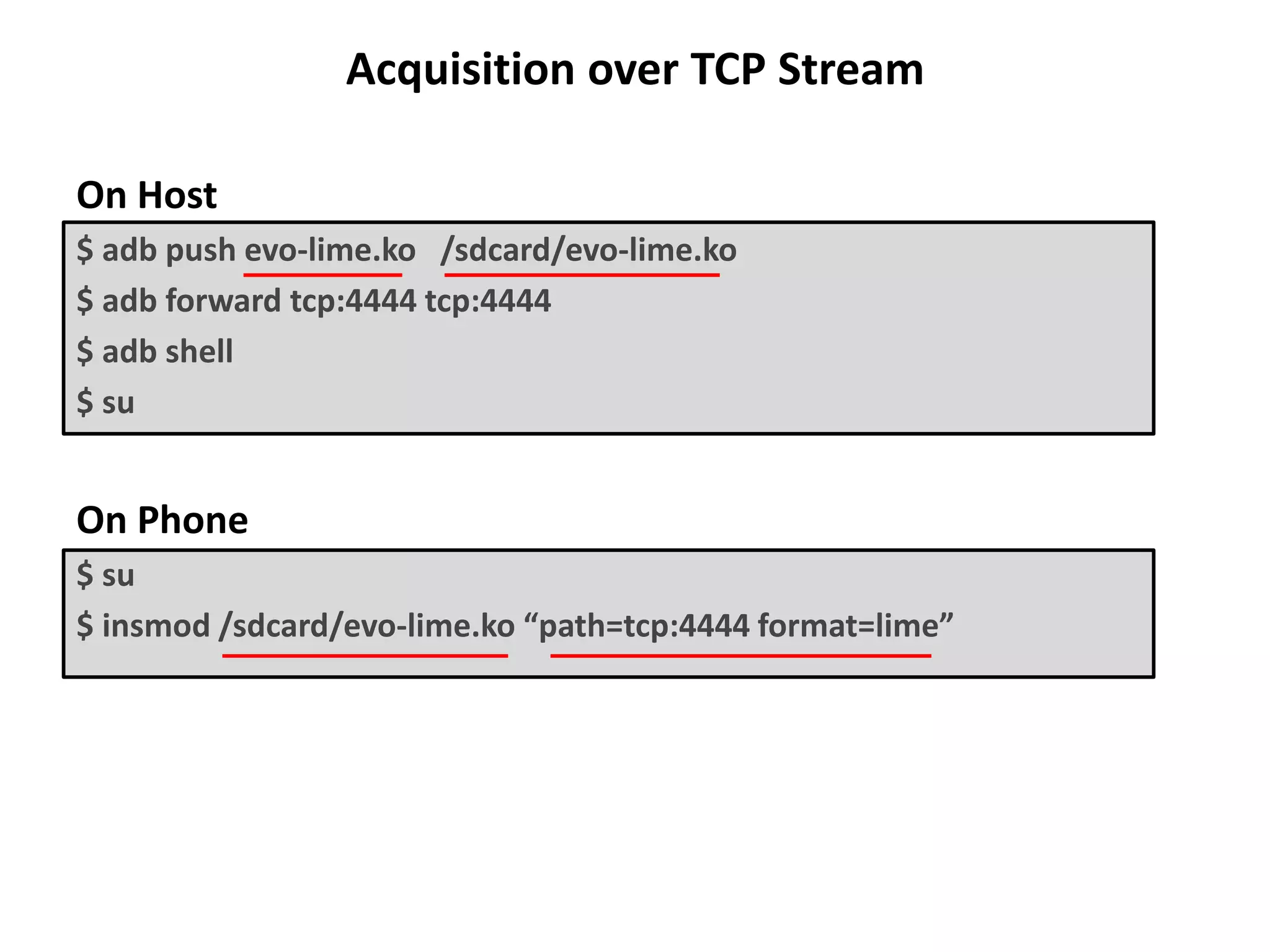
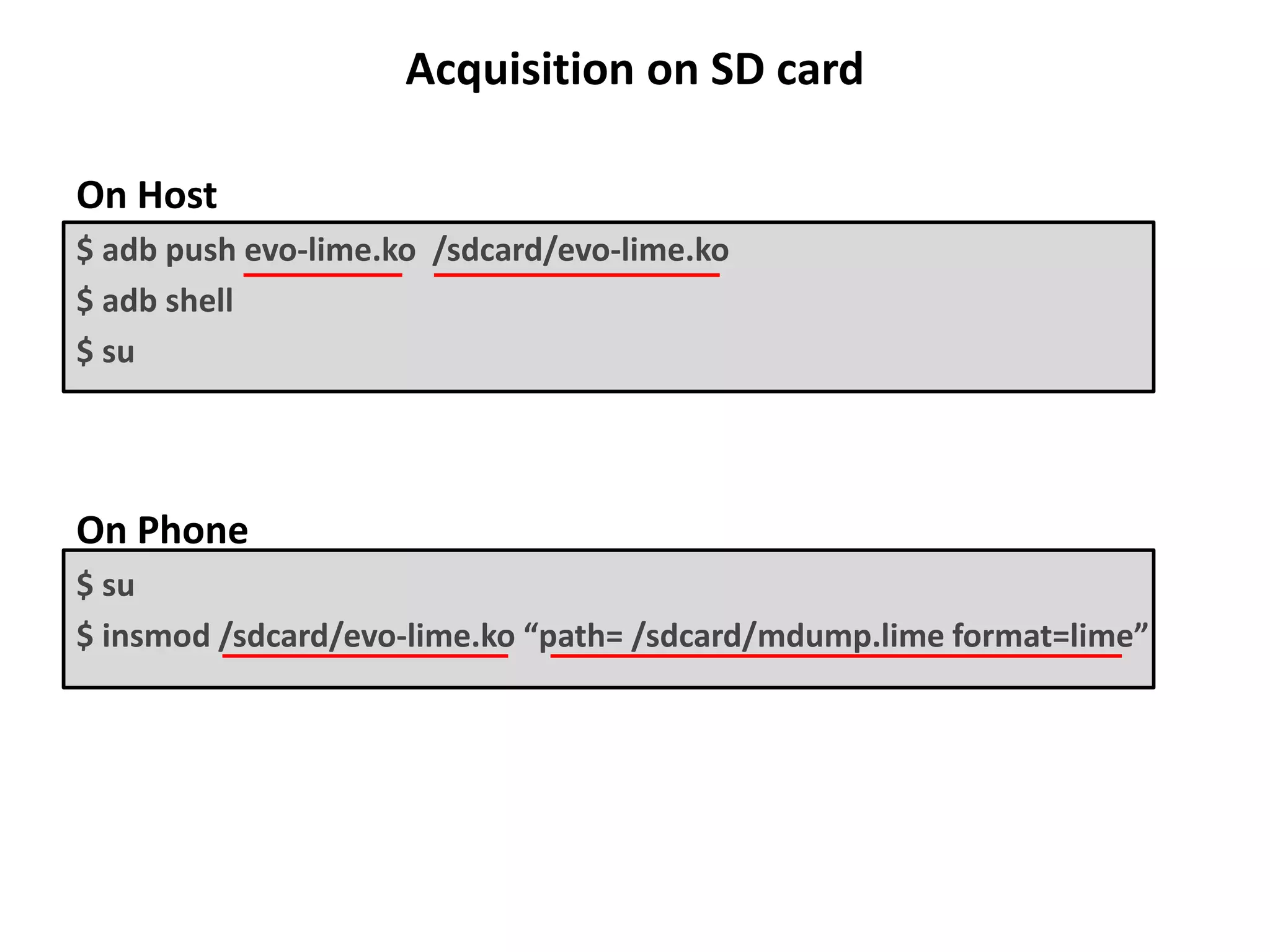
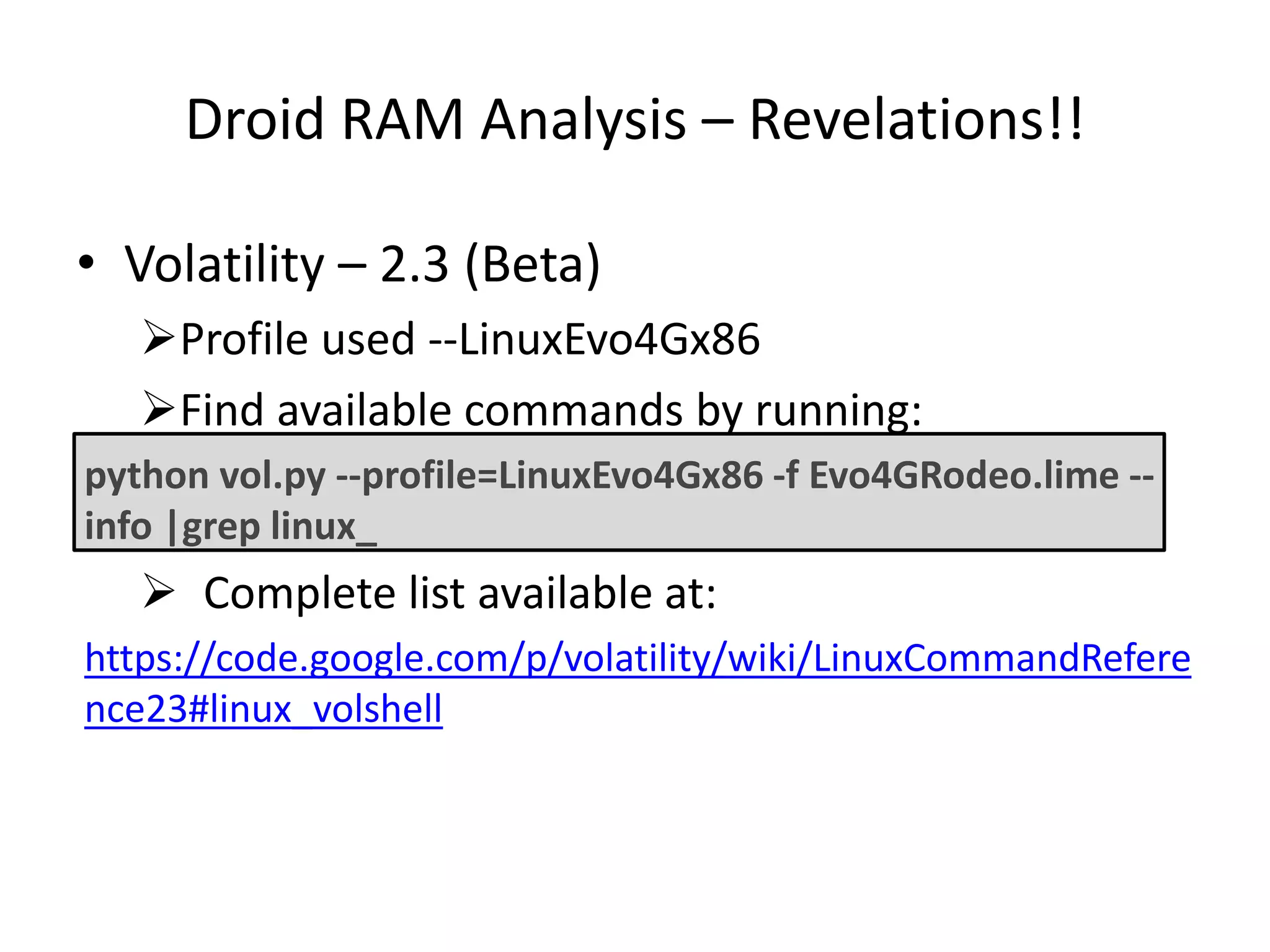
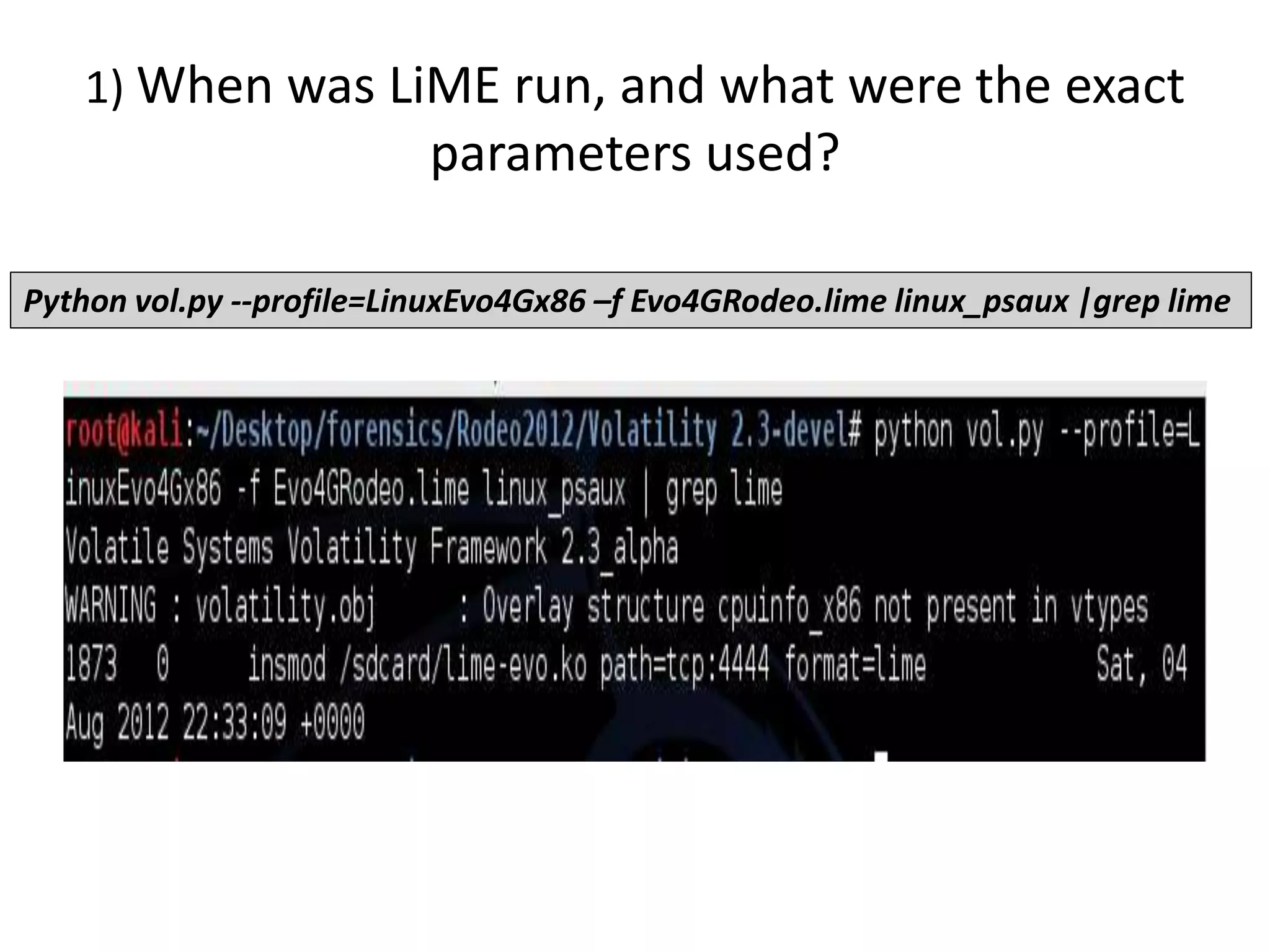
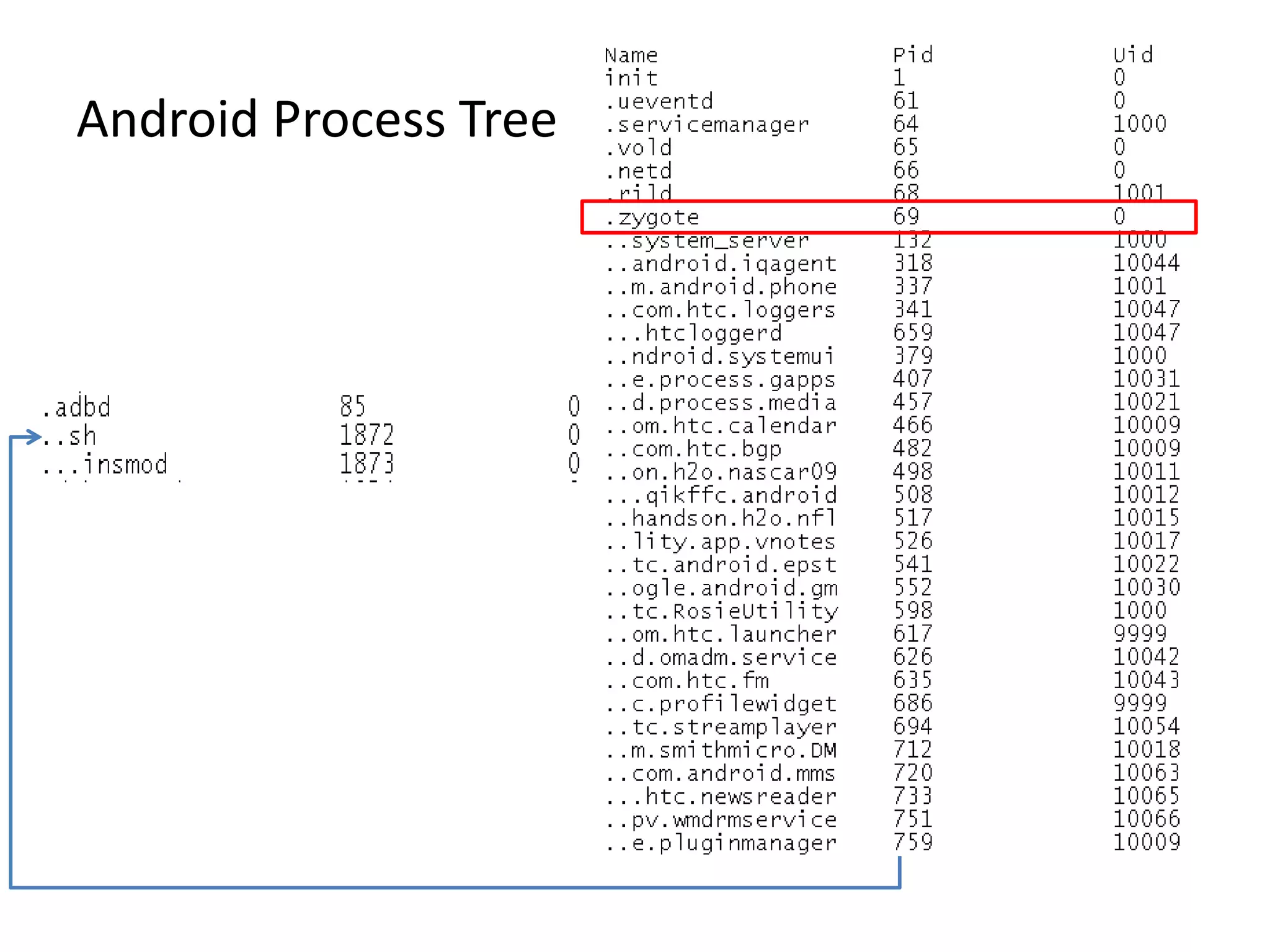
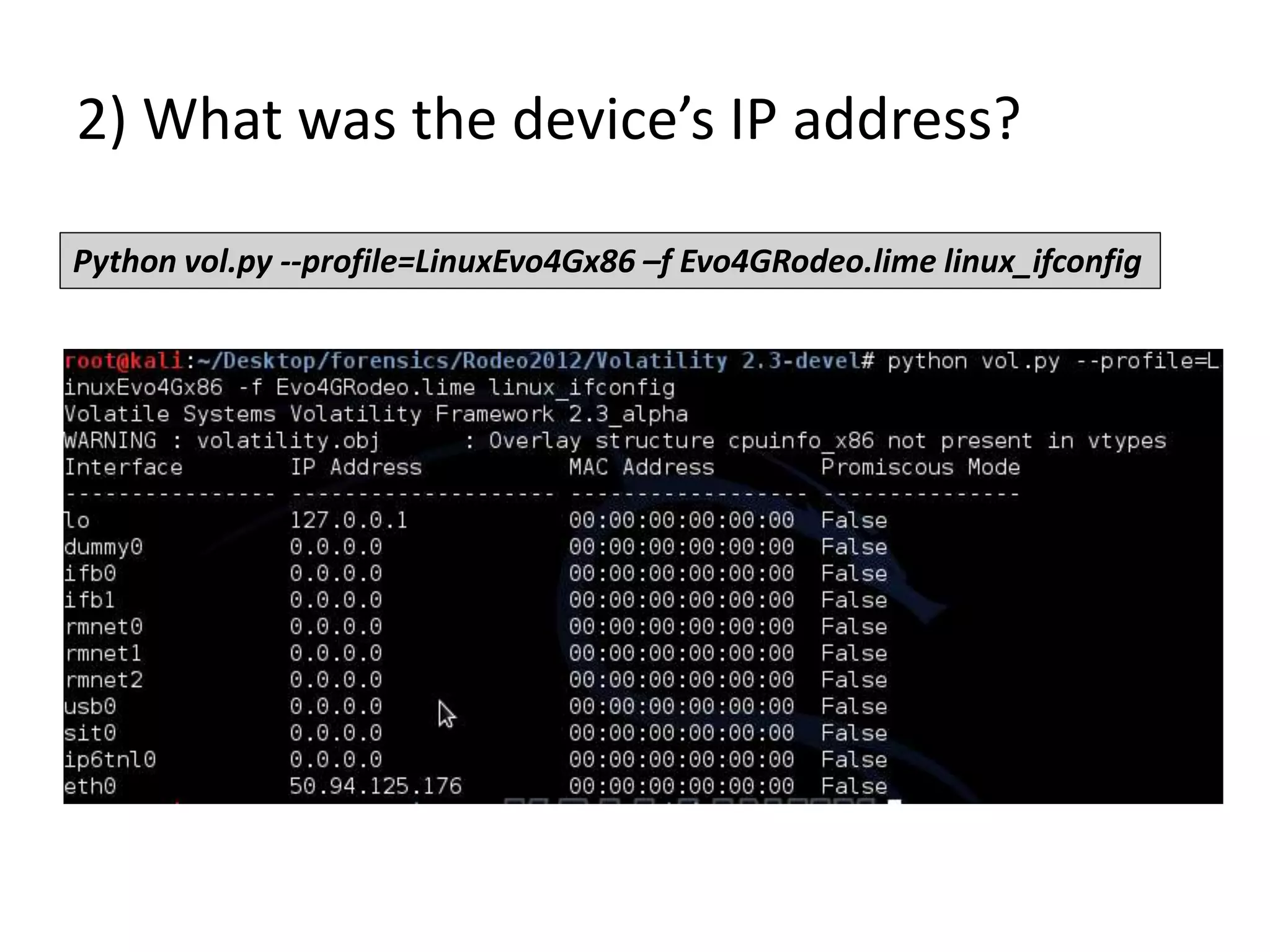
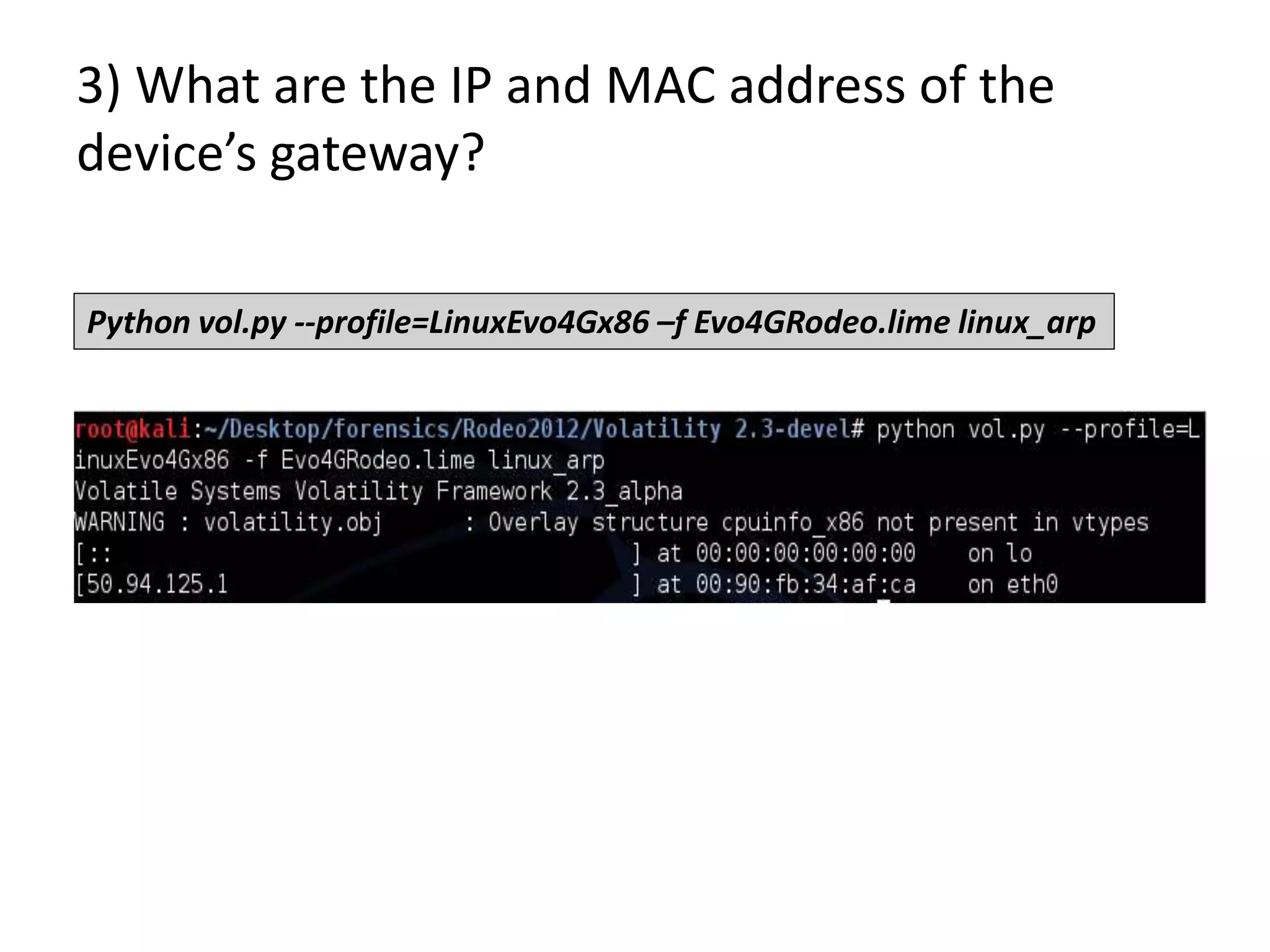
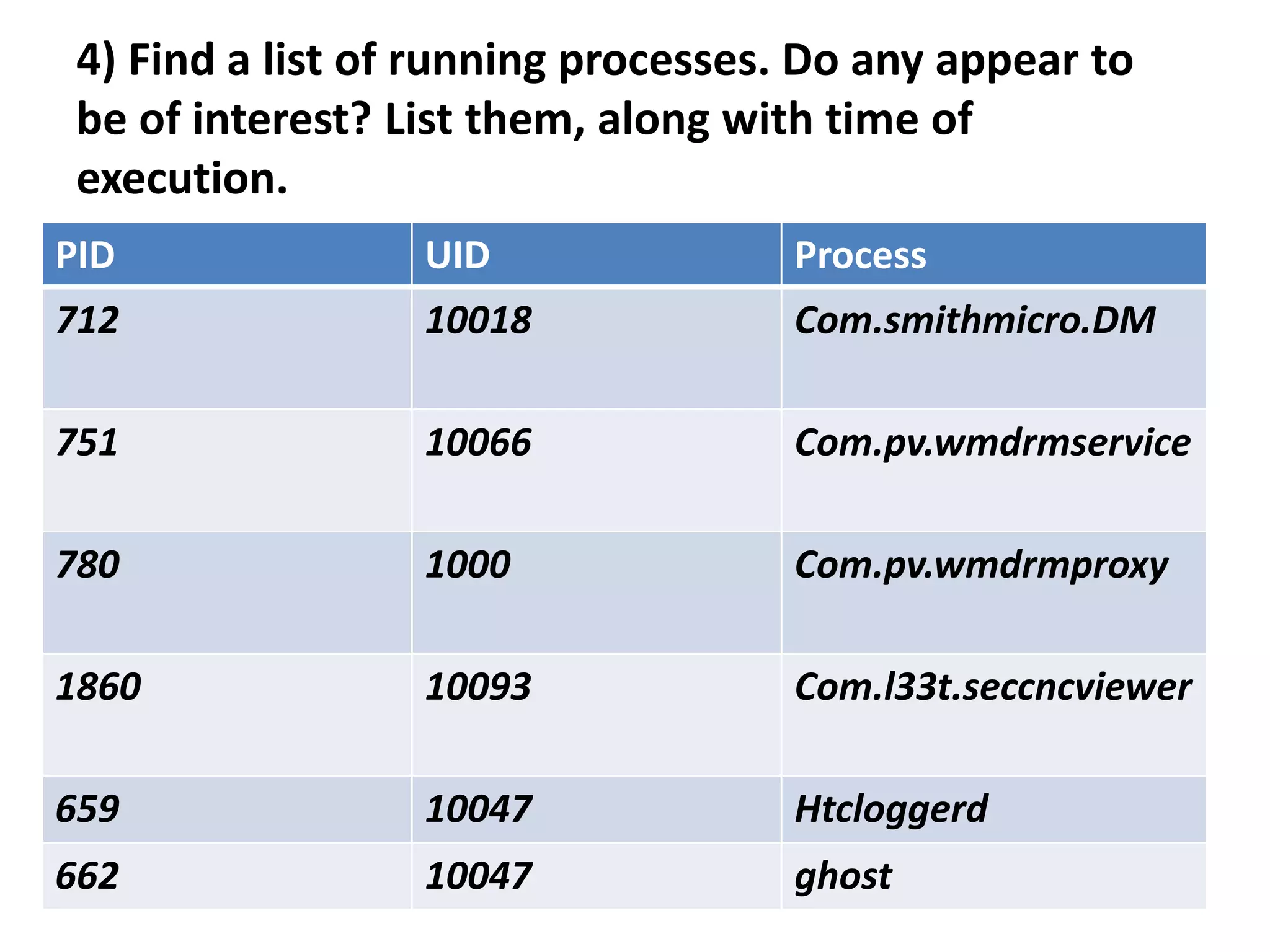
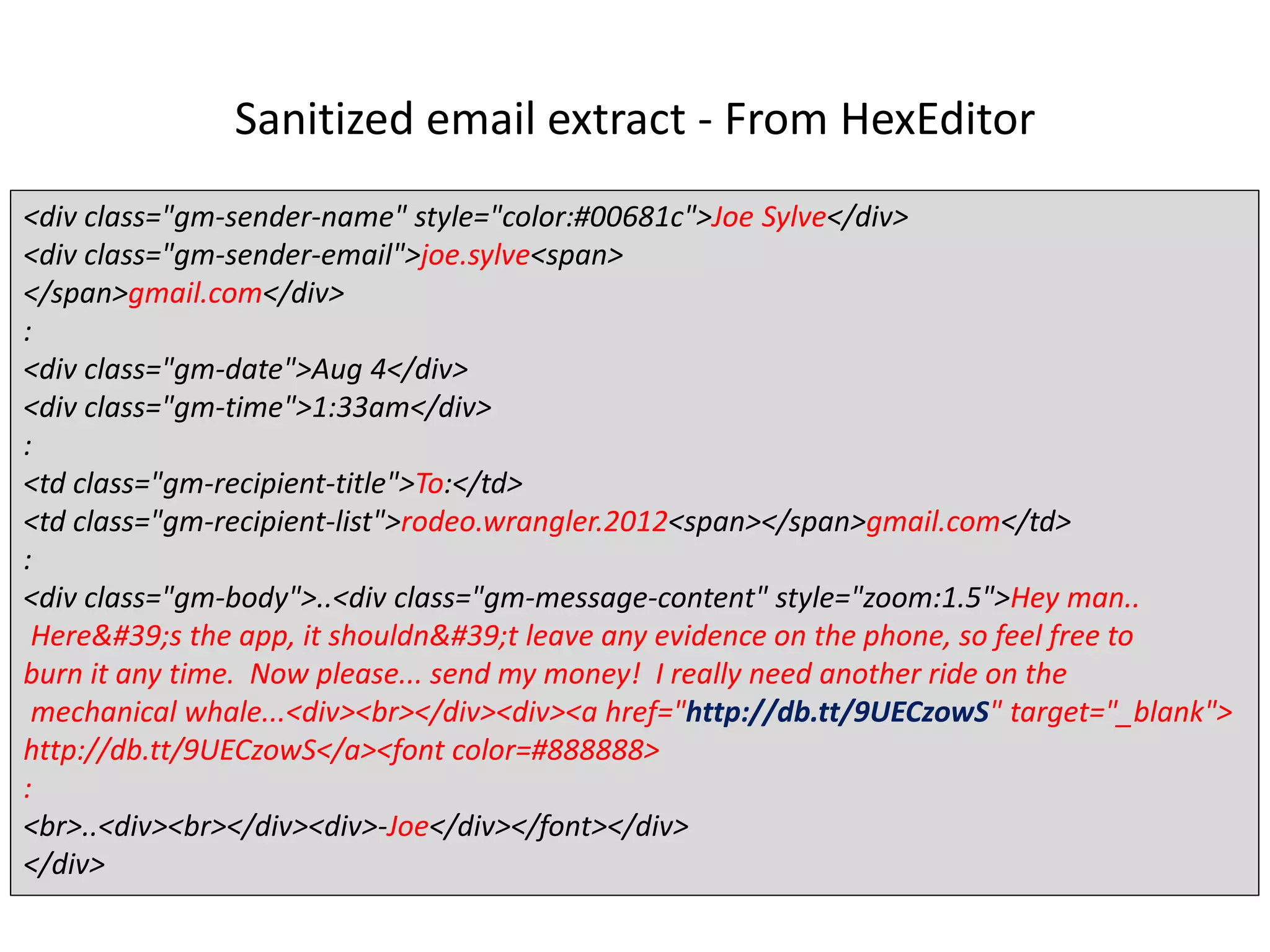
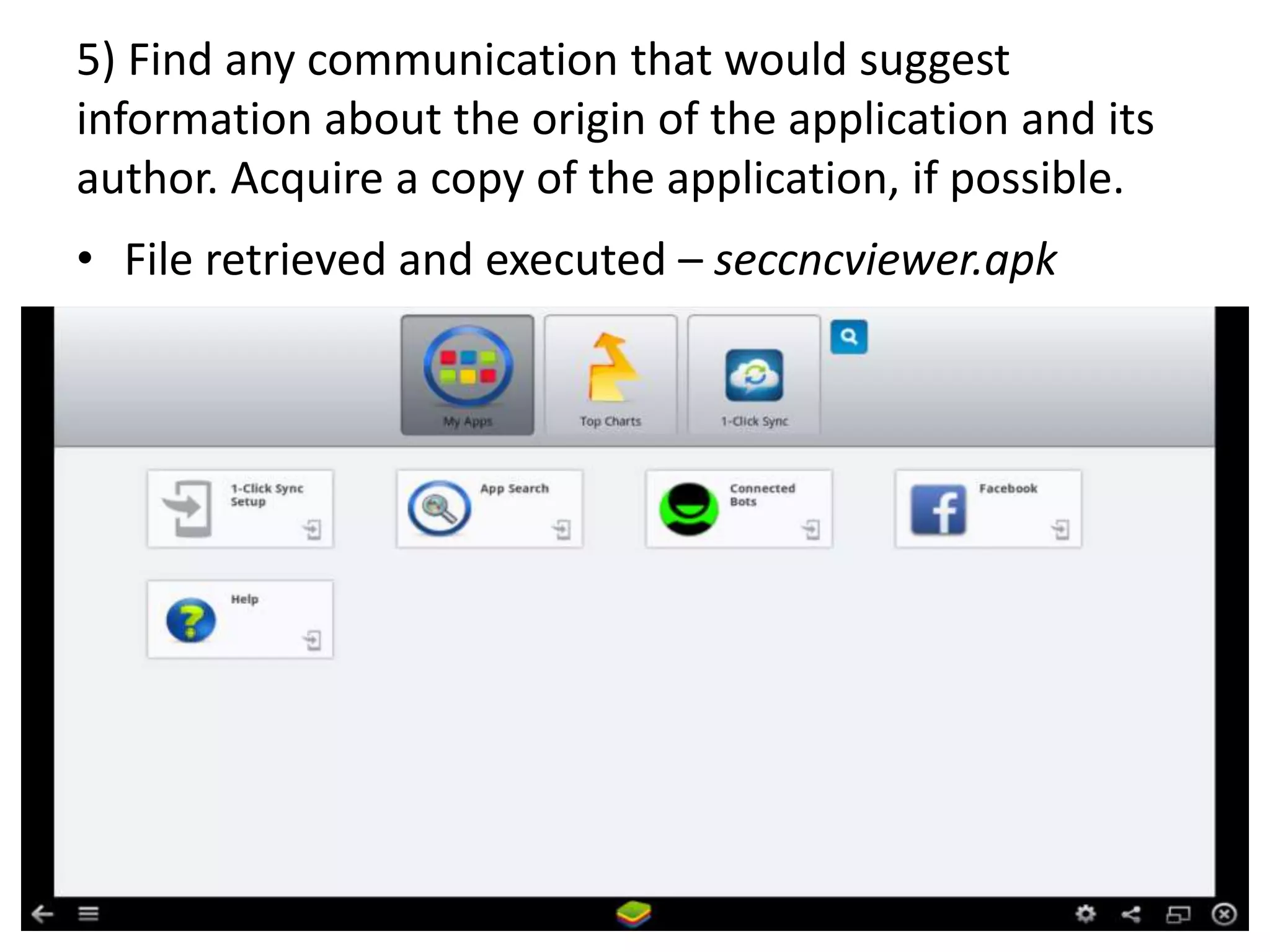
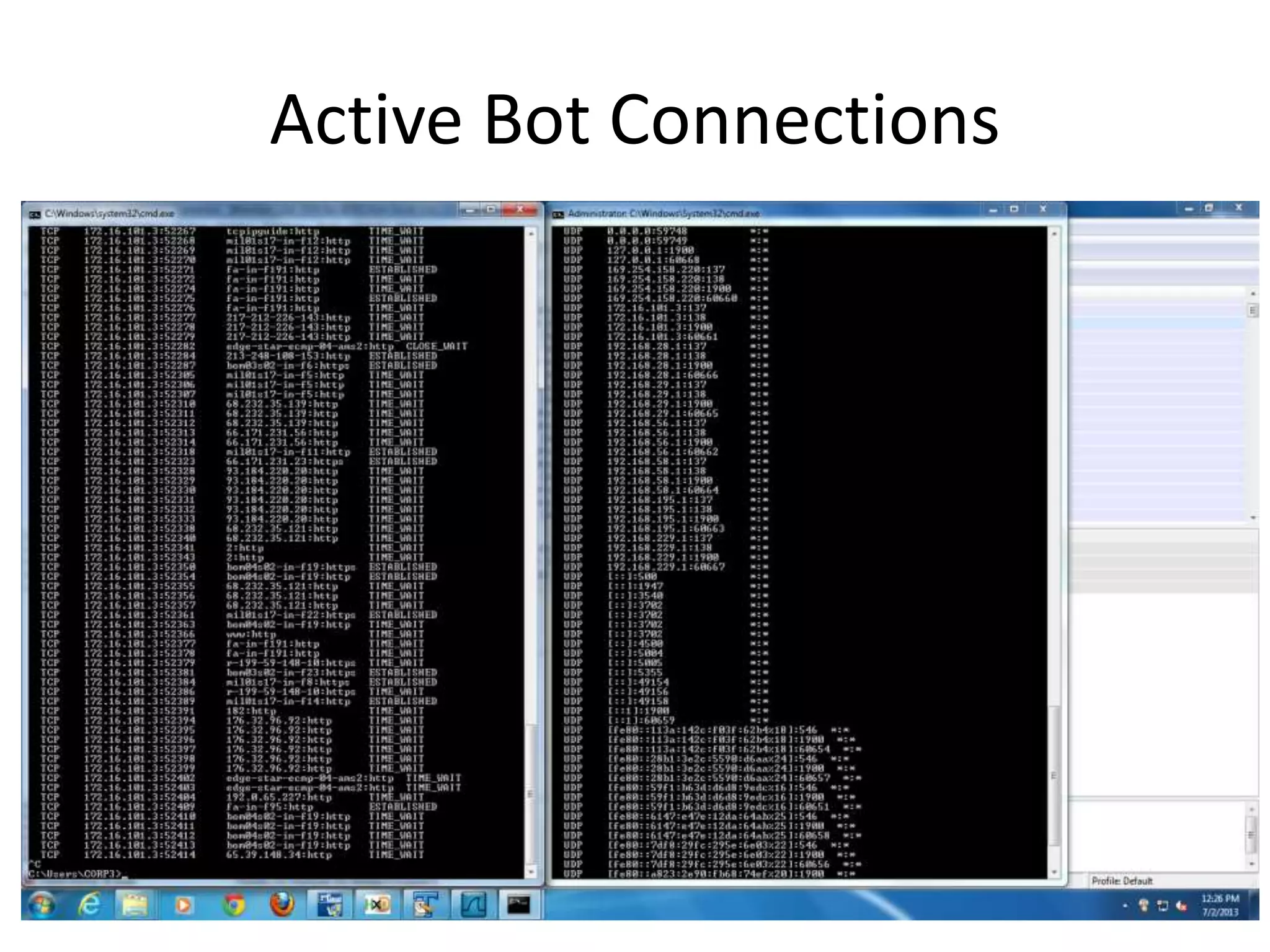
This document discusses investigating a case involving a botnet commander using a custom Android application. The investigation process involved acquiring a memory dump from the suspect's Android device using LIME and analyzing it using Volatility. Key findings included identifying running processes of interest, extracting communication suggesting the origin and author of the application, and retrieving a copy of the malicious application. Challenges included limitations in Volatility's support for Android memory forensics and not having enough time to fully analyze the memory dump and application to identify such things as the command and control server IP address and details about the bots.