Embed presentation
Downloaded 11 times

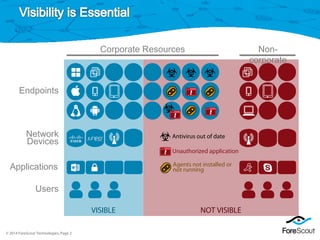
![© 2014 ForeScout Technologies, Page 3
Control Access
Based on Compliance
Incident Response
Compliance Dashboard
Complete
Visibility
Enforcement Remediation
Information
Sharing
Endpoint
Interrogation &
Authentication
Device Discovery, Profiling
[HW/SW USER LOC ...]
Multi-factor, Complete,
Clientless, Access Control
Continuous
Monitoring
Challenge
• Asset visibility
• Access and threat dynamics
• Endpoint and infrastructure diversity
• Network authentication and control
• Dynamic threats and remediation costs
Solution
• Pre-admission user/device
authentication and authorization
• Continuous endpoint diagnostics,
posture assessment and mitigation
• Port-based control and broad device
policy enforcement
• Infrastructure agnostic, interoperable,
scalable, works with enterprise tool sets Natively or Using Existing
Enterprise Tools](https://image.slidesharecdn.com/openanalyticscdm4-141009081815-conversion-gate02/85/CDM-Where-do-you-start-OA-Cyber-Summit-3-320.jpg)
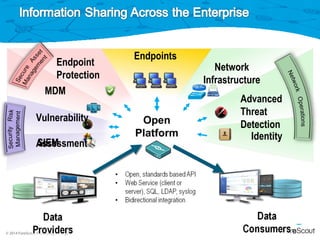
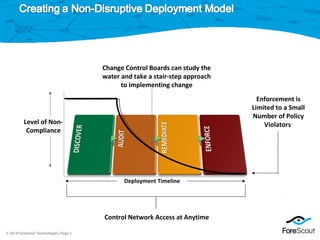



The document discusses ForeScout's network access control solution. It provides visibility into networked devices and endpoints, including those that are and aren't corporate assets. It can control access based on compliance levels, perform continuous monitoring, and share information. The solution offers user and device authentication, posture assessment, policy-based enforcement across networks and infrastructure, and integration with existing enterprise tools through an open platform. It allows network access control to be implemented gradually over time through a staged approach.


![© 2014 ForeScout Technologies, Page 3
Control Access
Based on Compliance
Incident Response
Compliance Dashboard
Complete
Visibility
Enforcement Remediation
Information
Sharing
Endpoint
Interrogation &
Authentication
Device Discovery, Profiling
[HW/SW USER LOC ...]
Multi-factor, Complete,
Clientless, Access Control
Continuous
Monitoring
Challenge
• Asset visibility
• Access and threat dynamics
• Endpoint and infrastructure diversity
• Network authentication and control
• Dynamic threats and remediation costs
Solution
• Pre-admission user/device
authentication and authorization
• Continuous endpoint diagnostics,
posture assessment and mitigation
• Port-based control and broad device
policy enforcement
• Infrastructure agnostic, interoperable,
scalable, works with enterprise tool sets Natively or Using Existing
Enterprise Tools](https://image.slidesharecdn.com/openanalyticscdm4-141009081815-conversion-gate02/85/CDM-Where-do-you-start-OA-Cyber-Summit-3-320.jpg)



