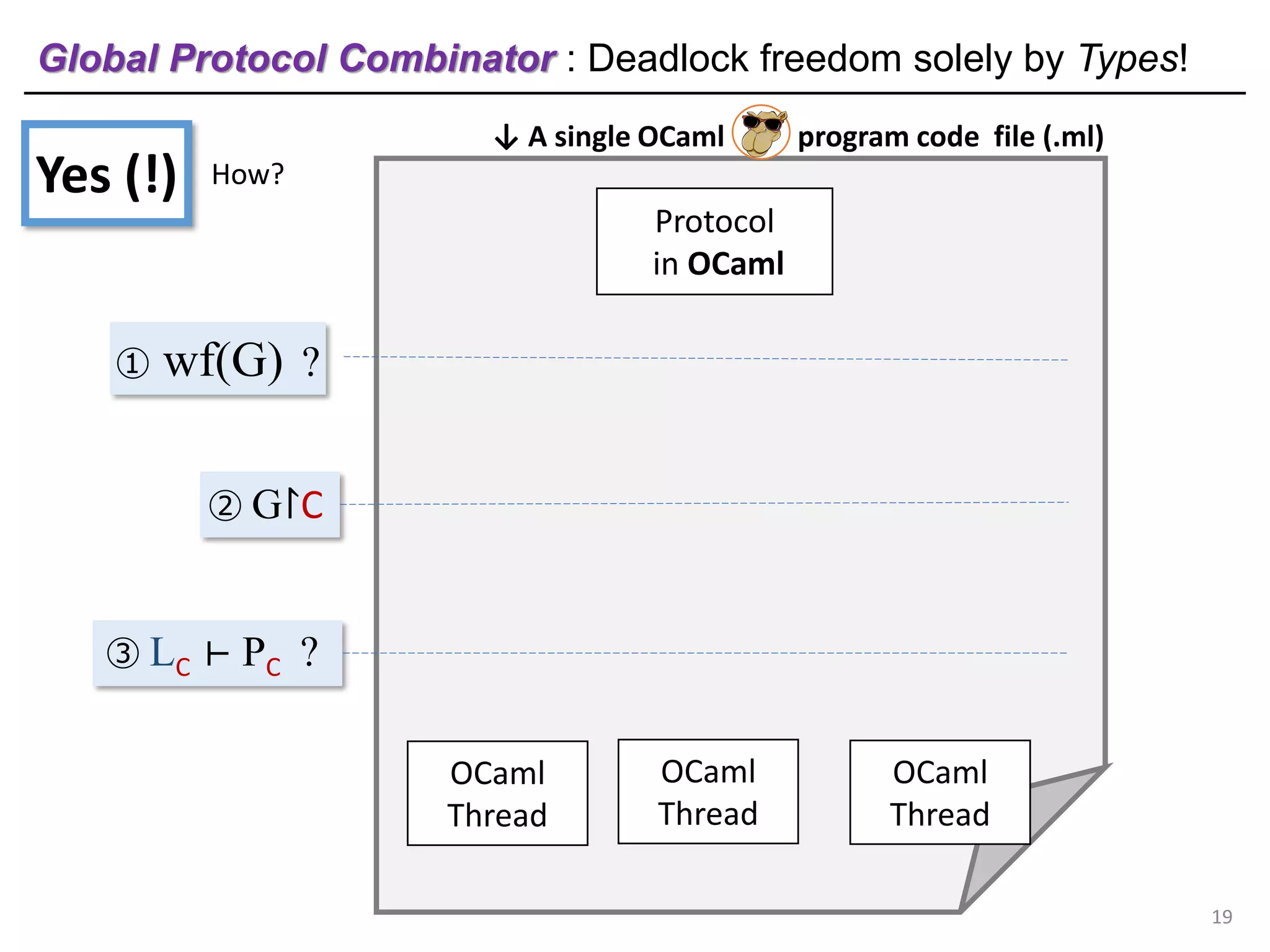
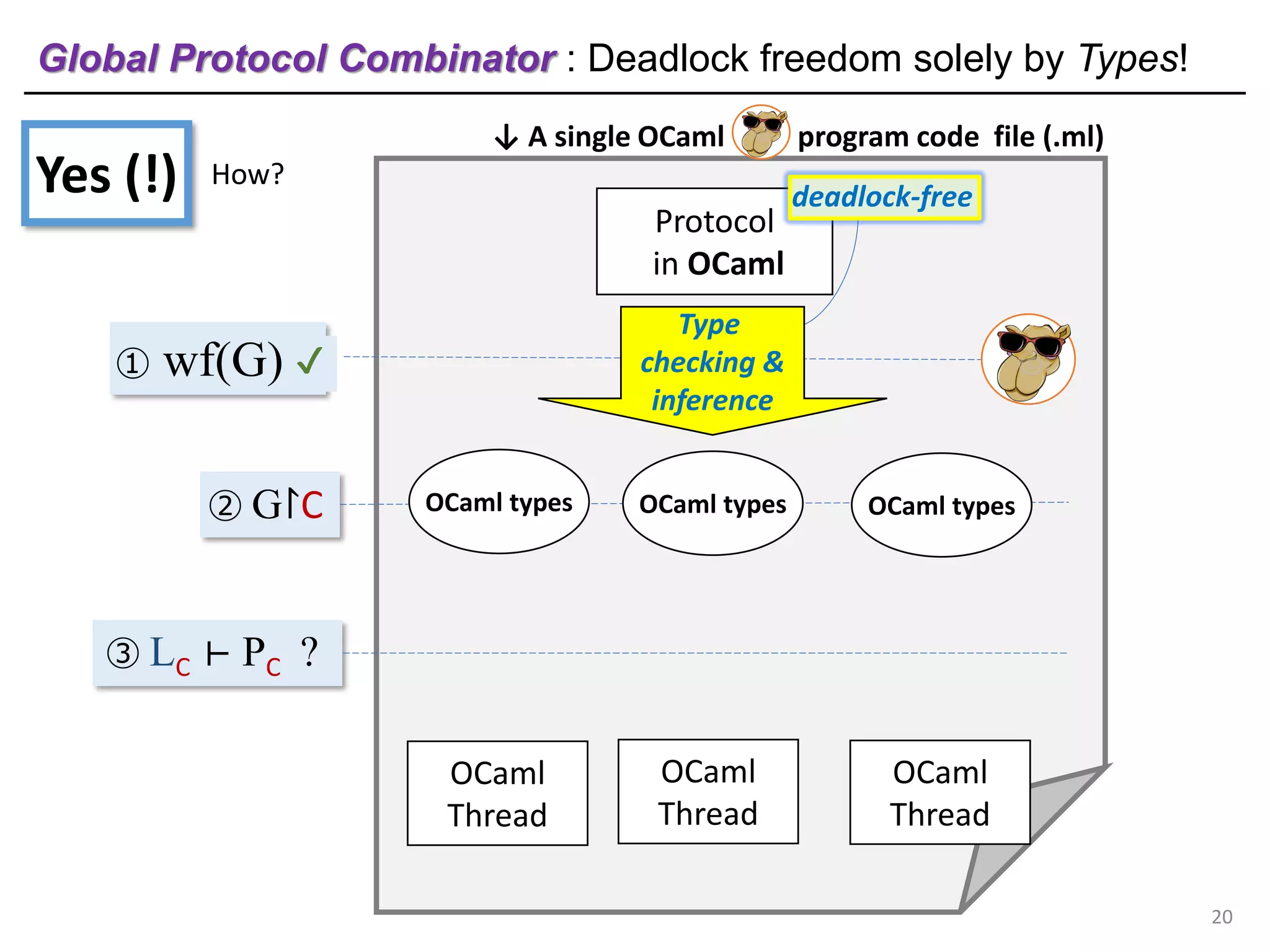
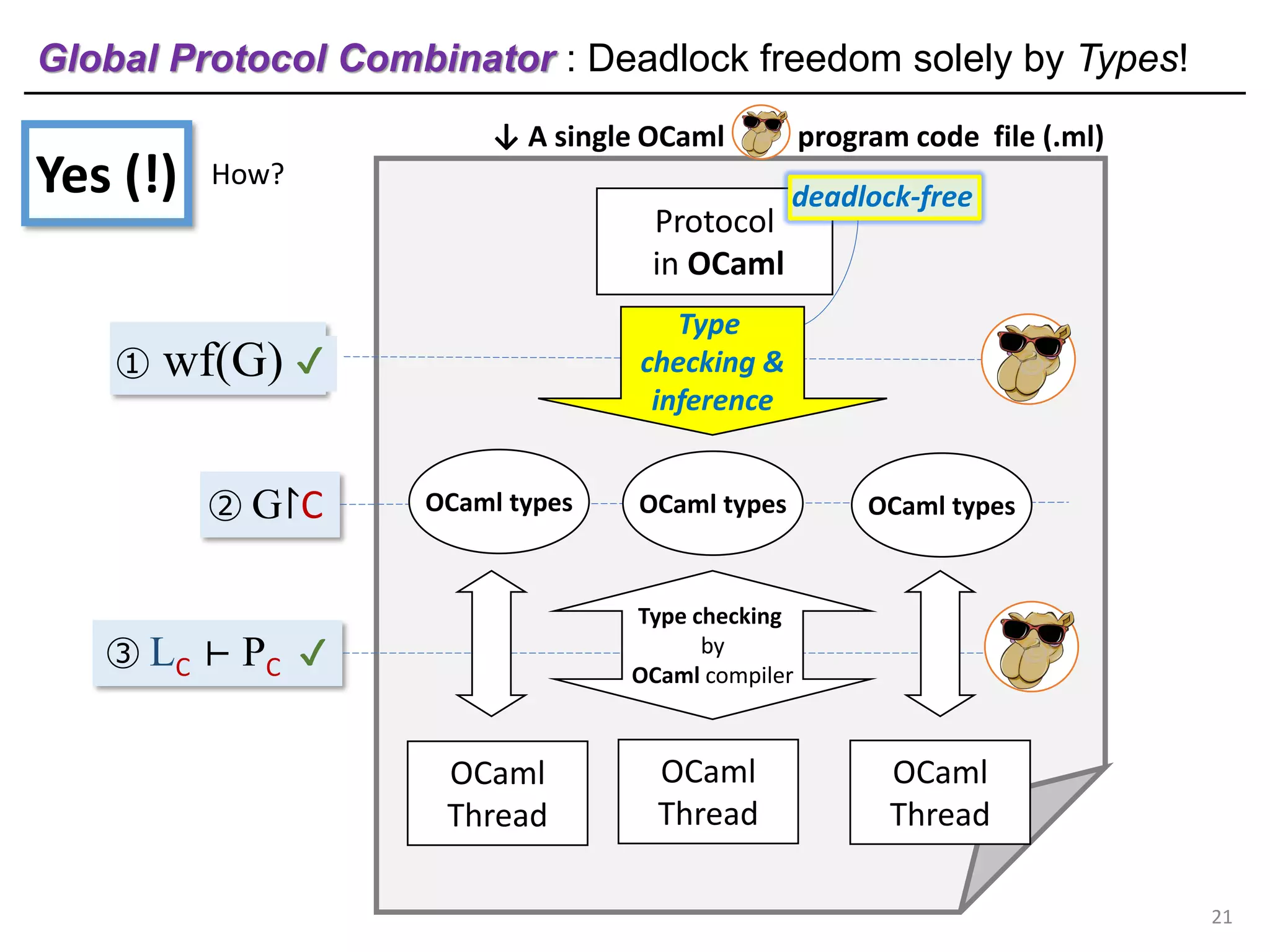
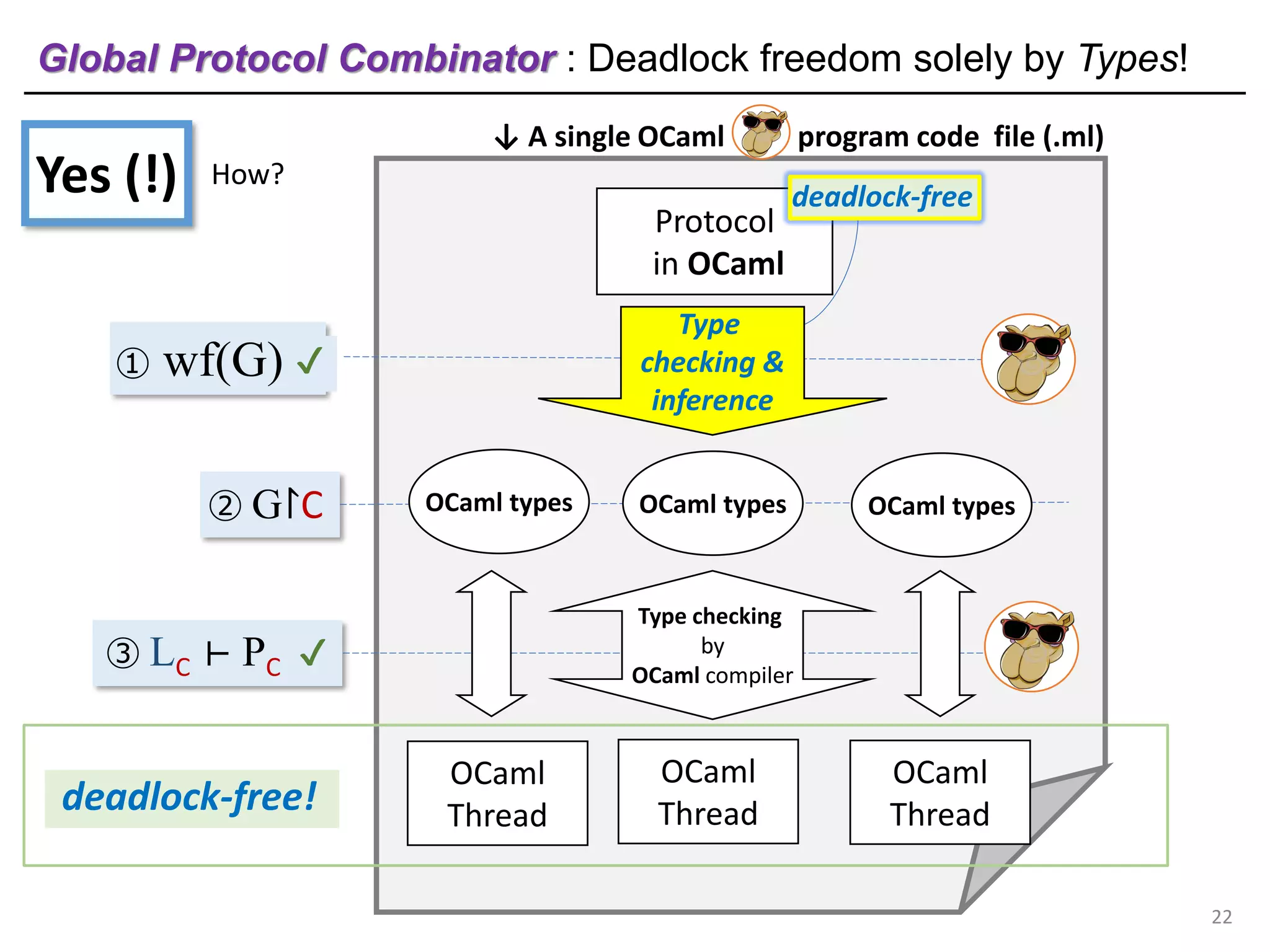
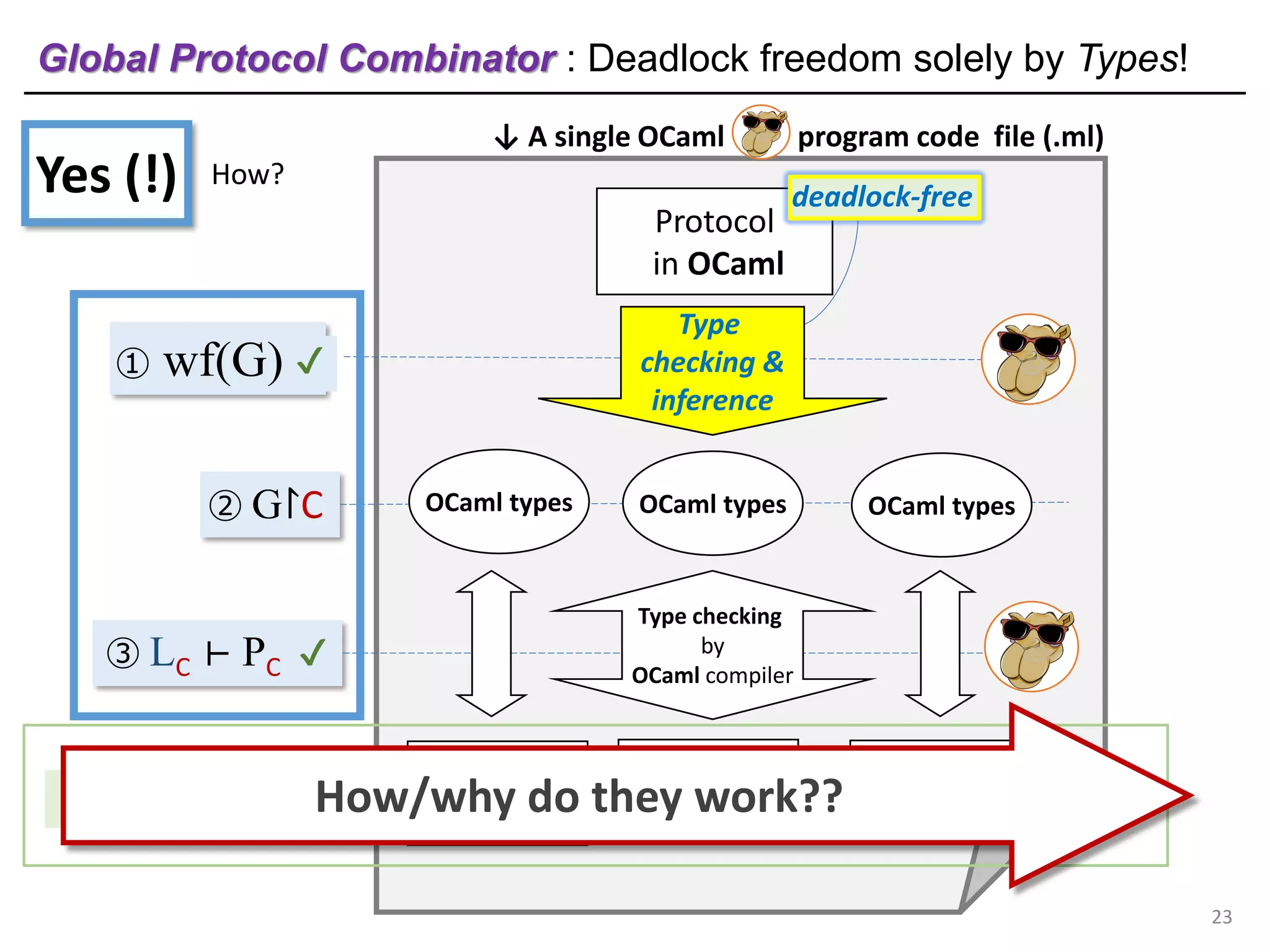
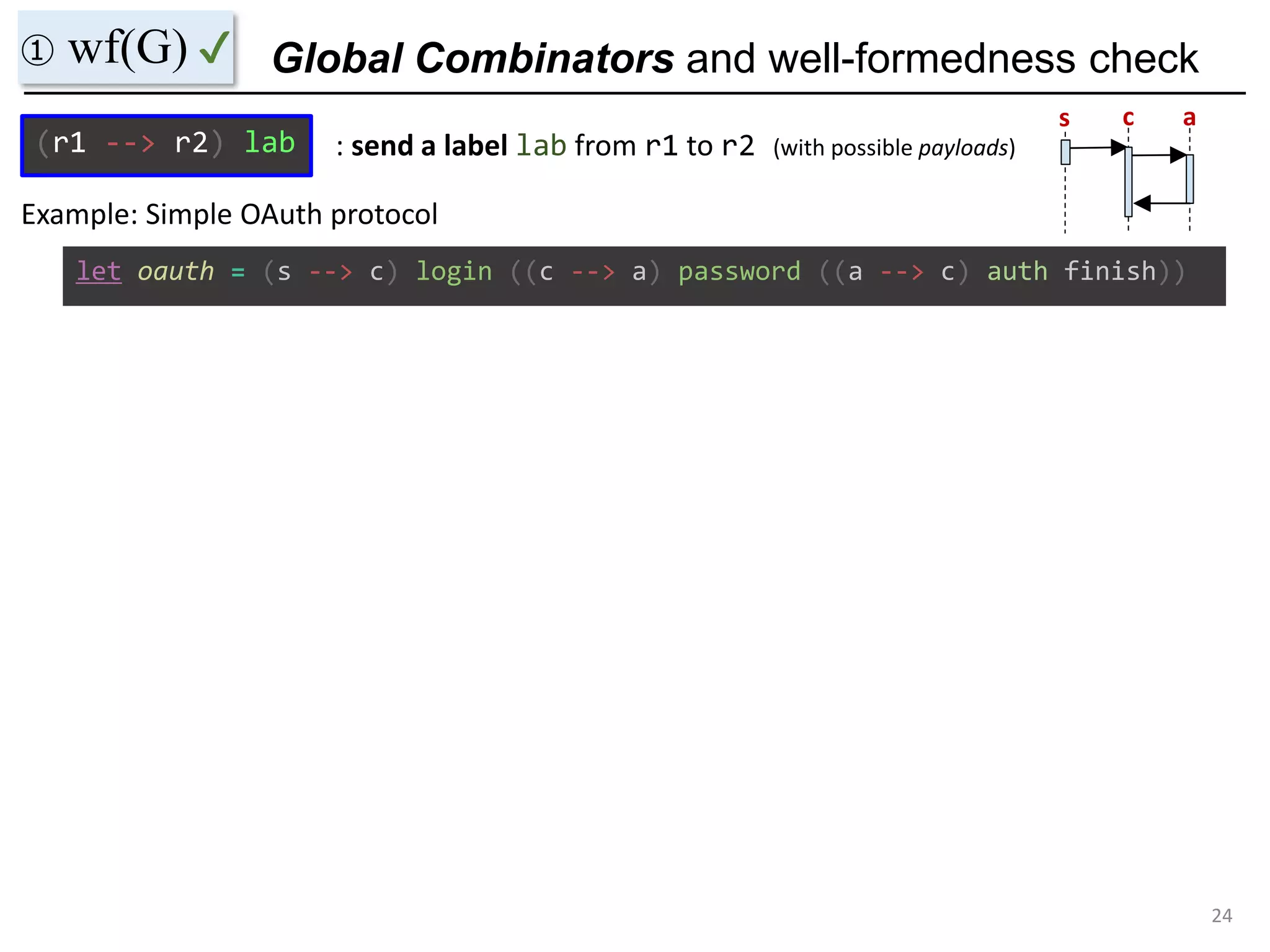
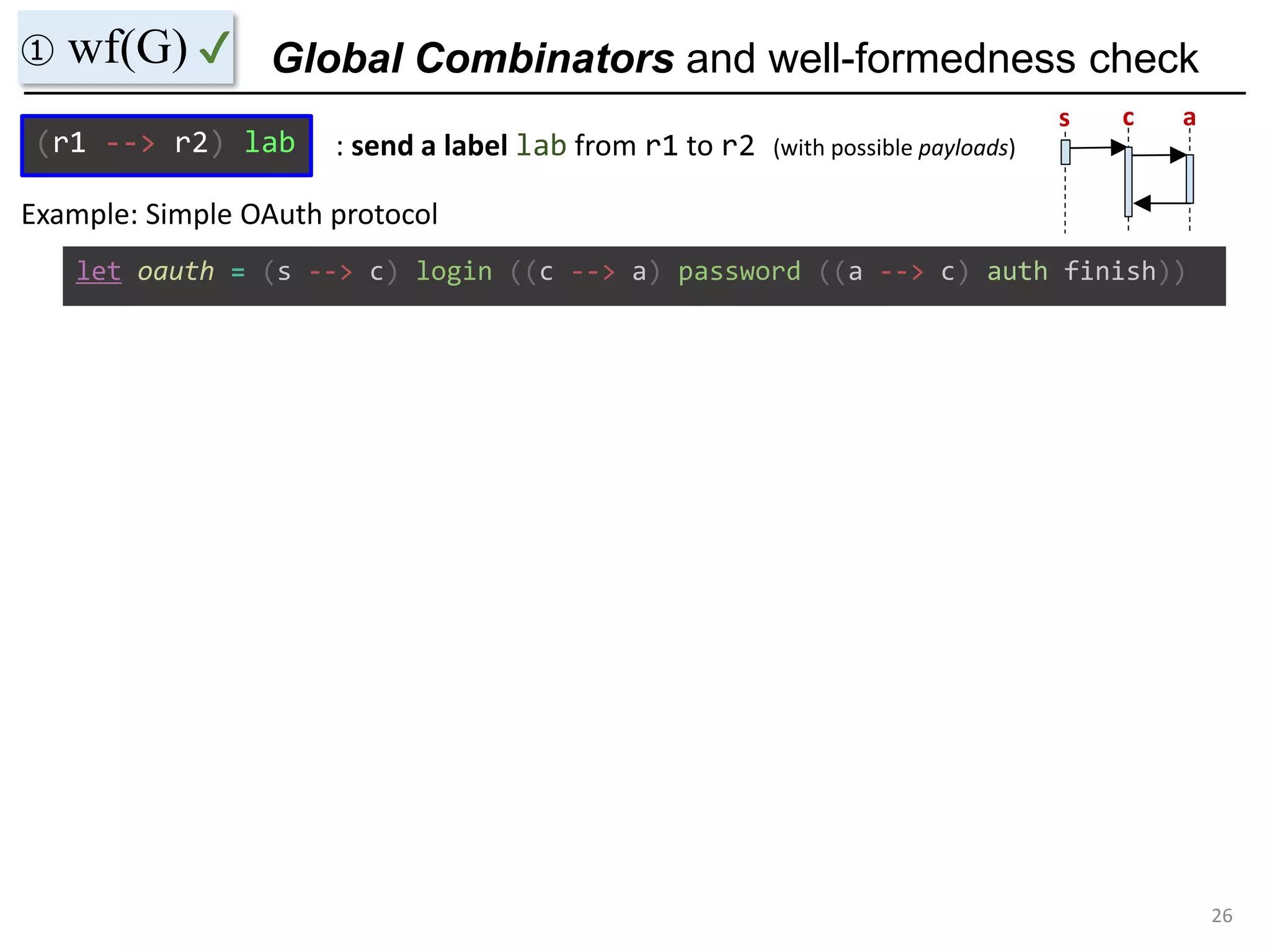
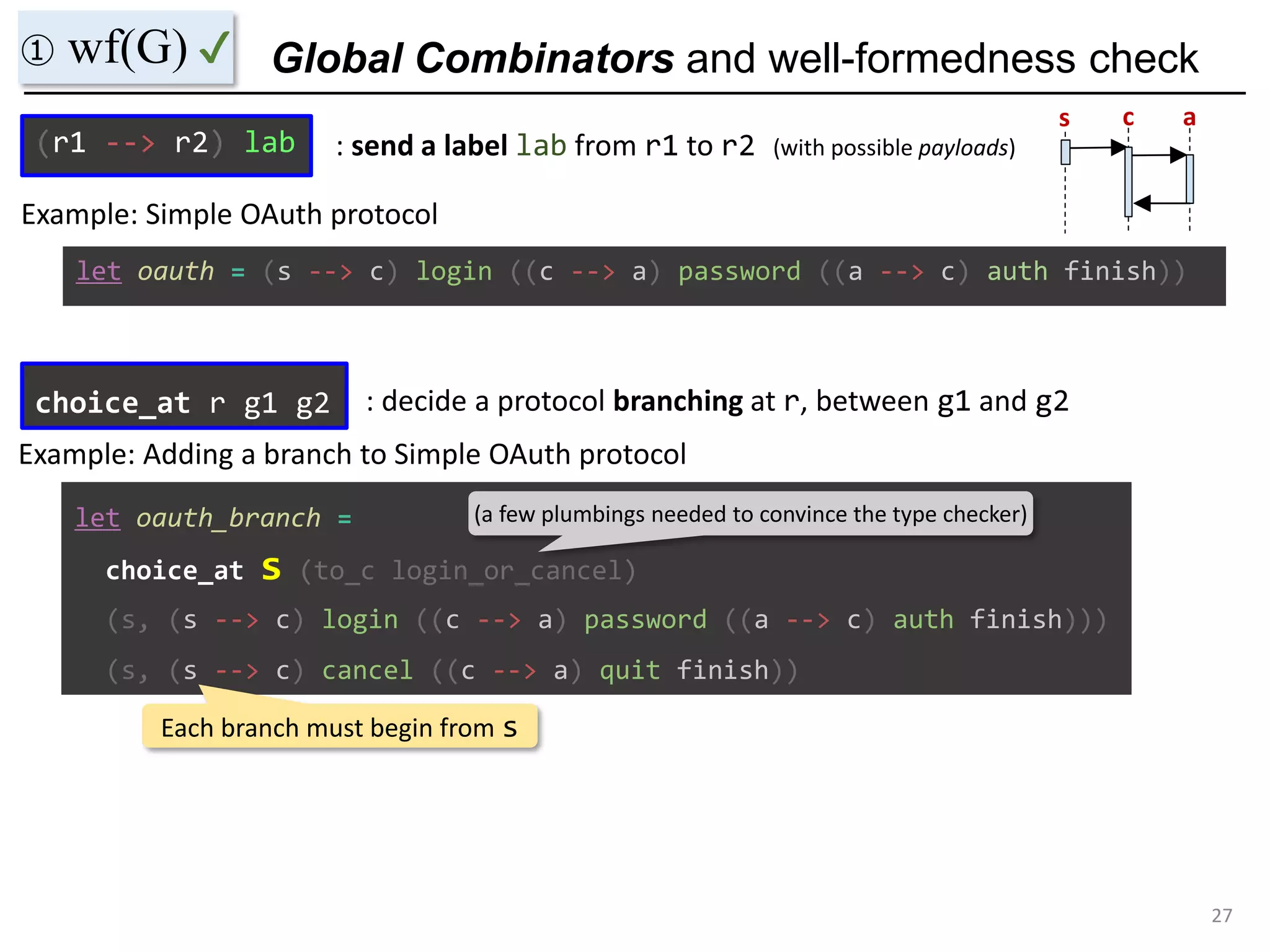
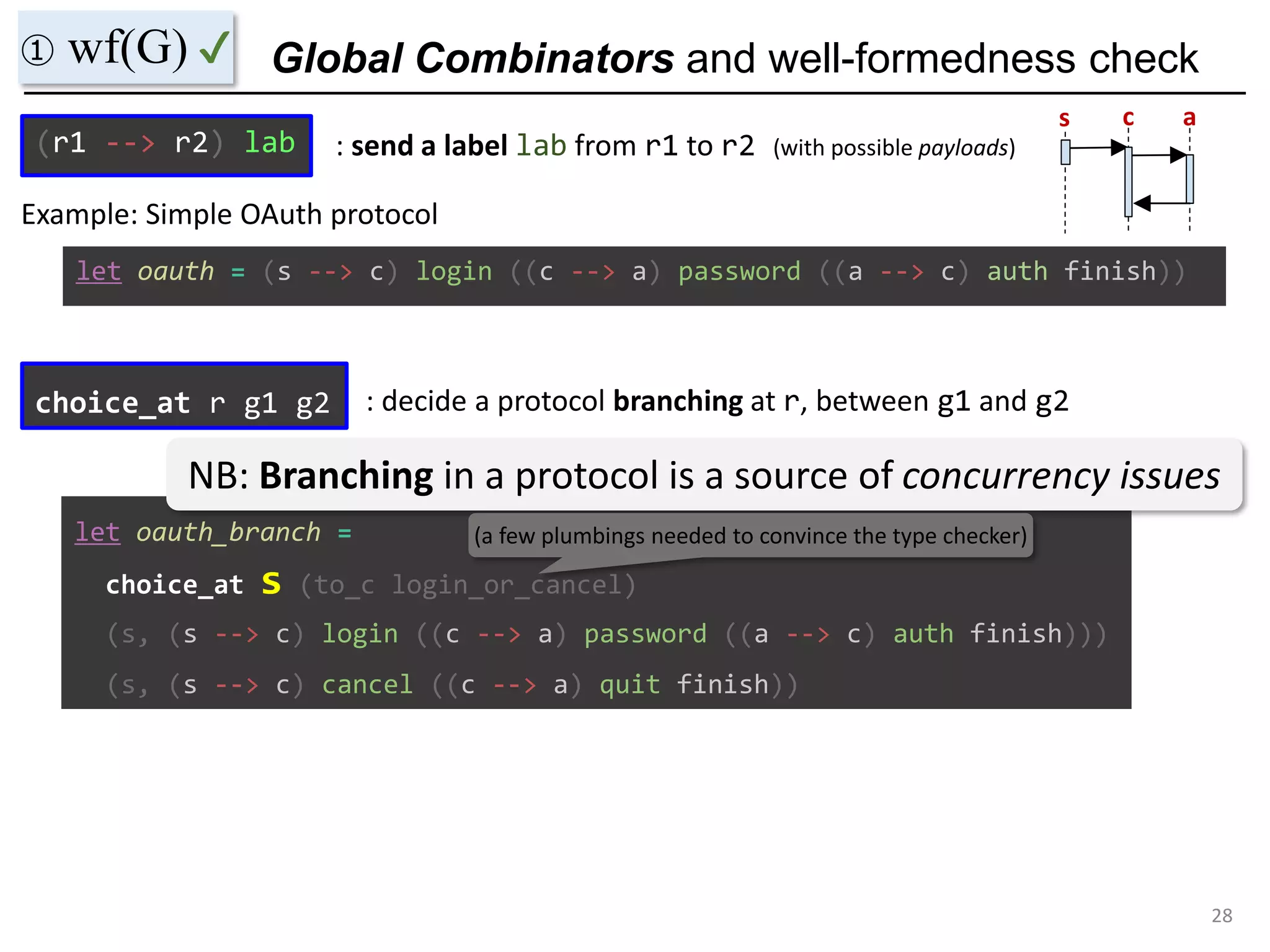
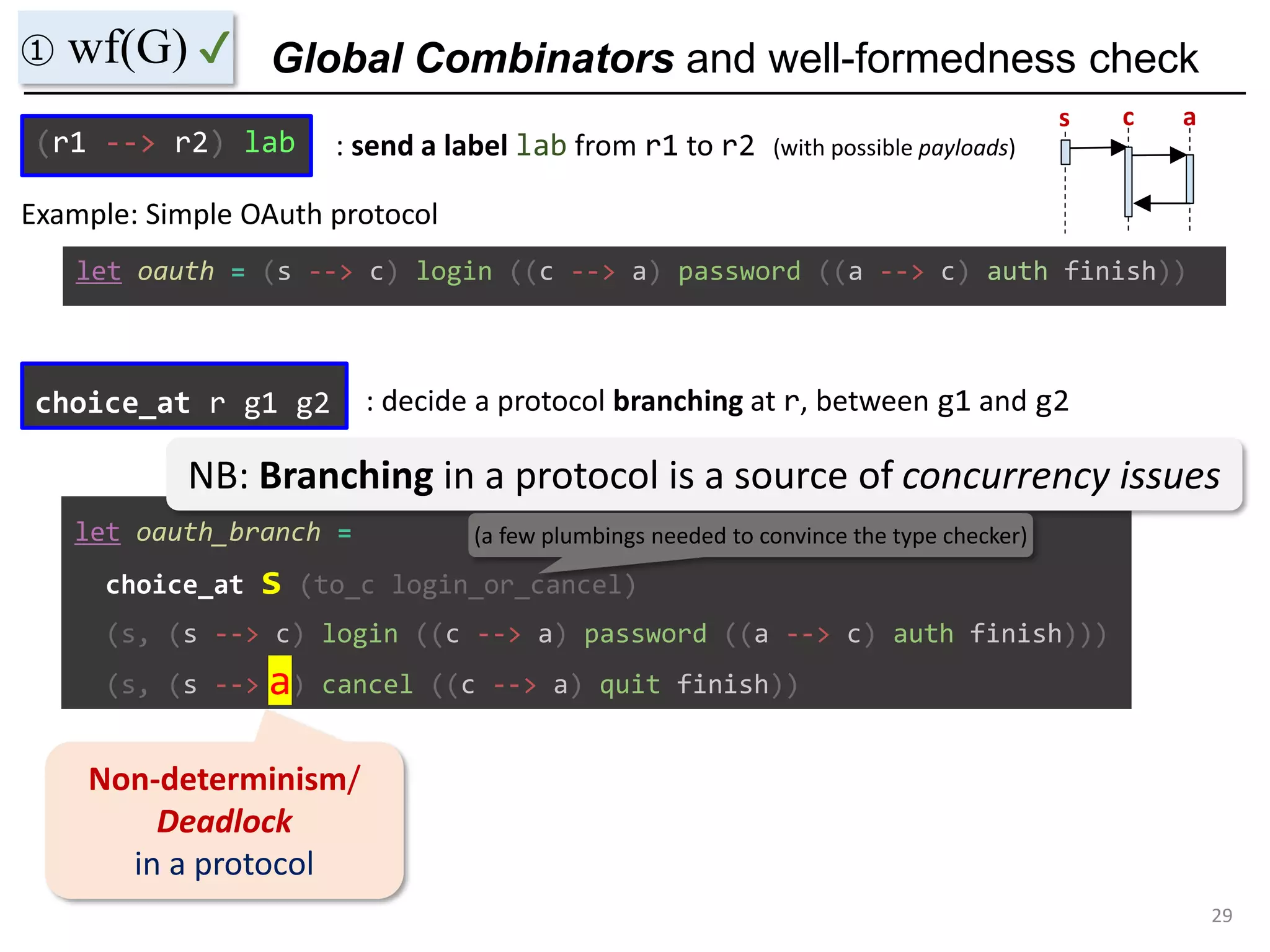
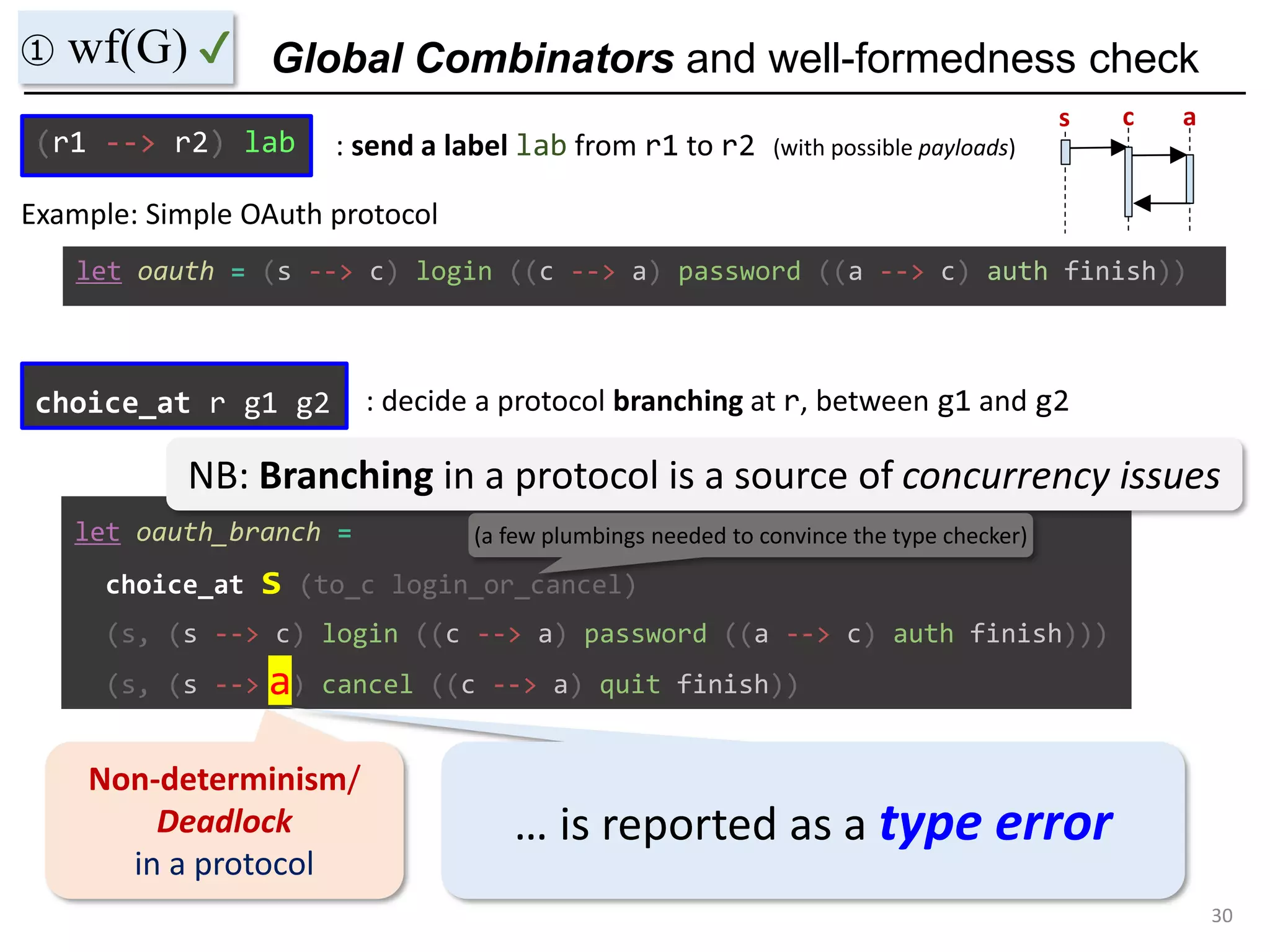
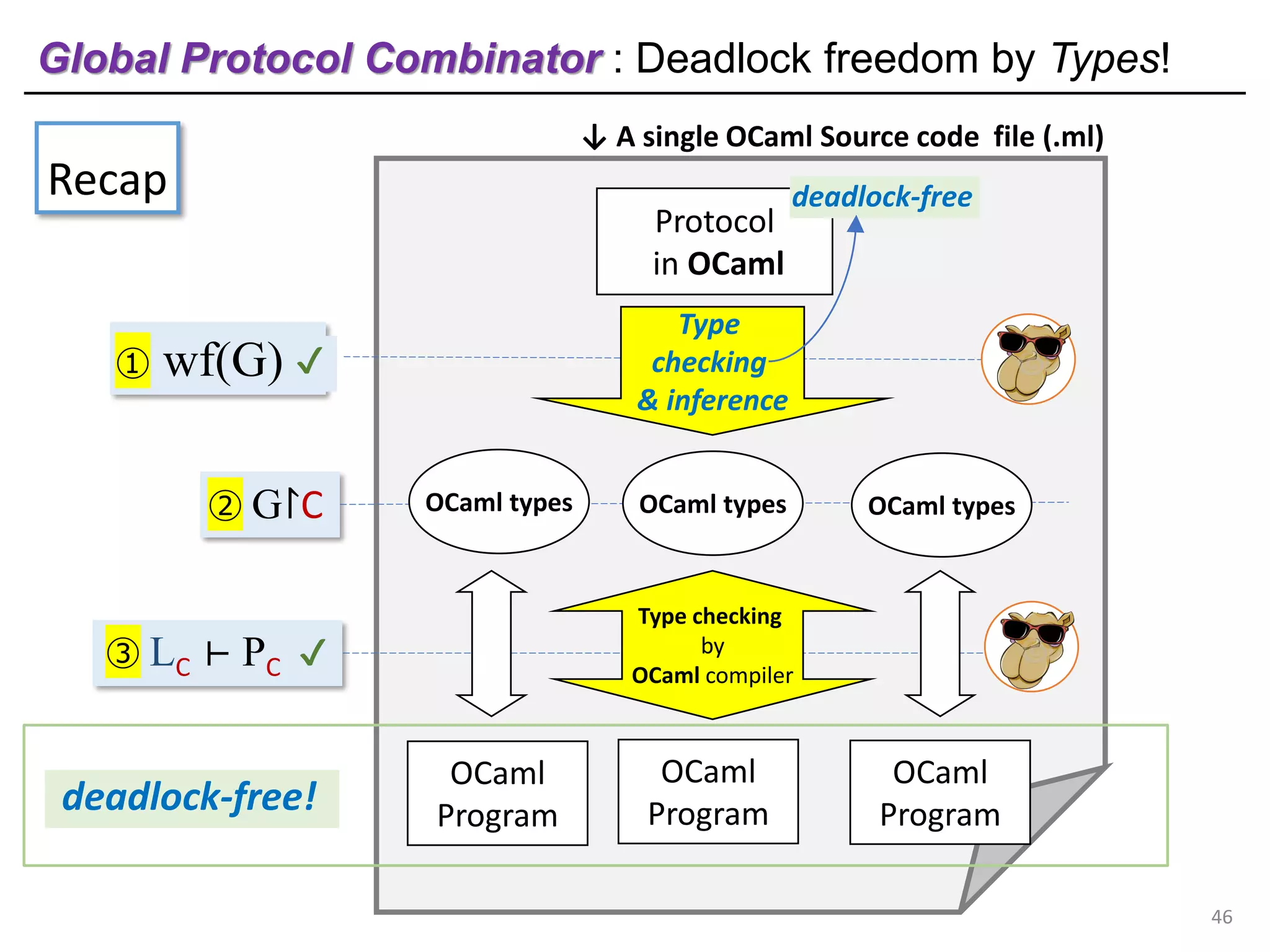
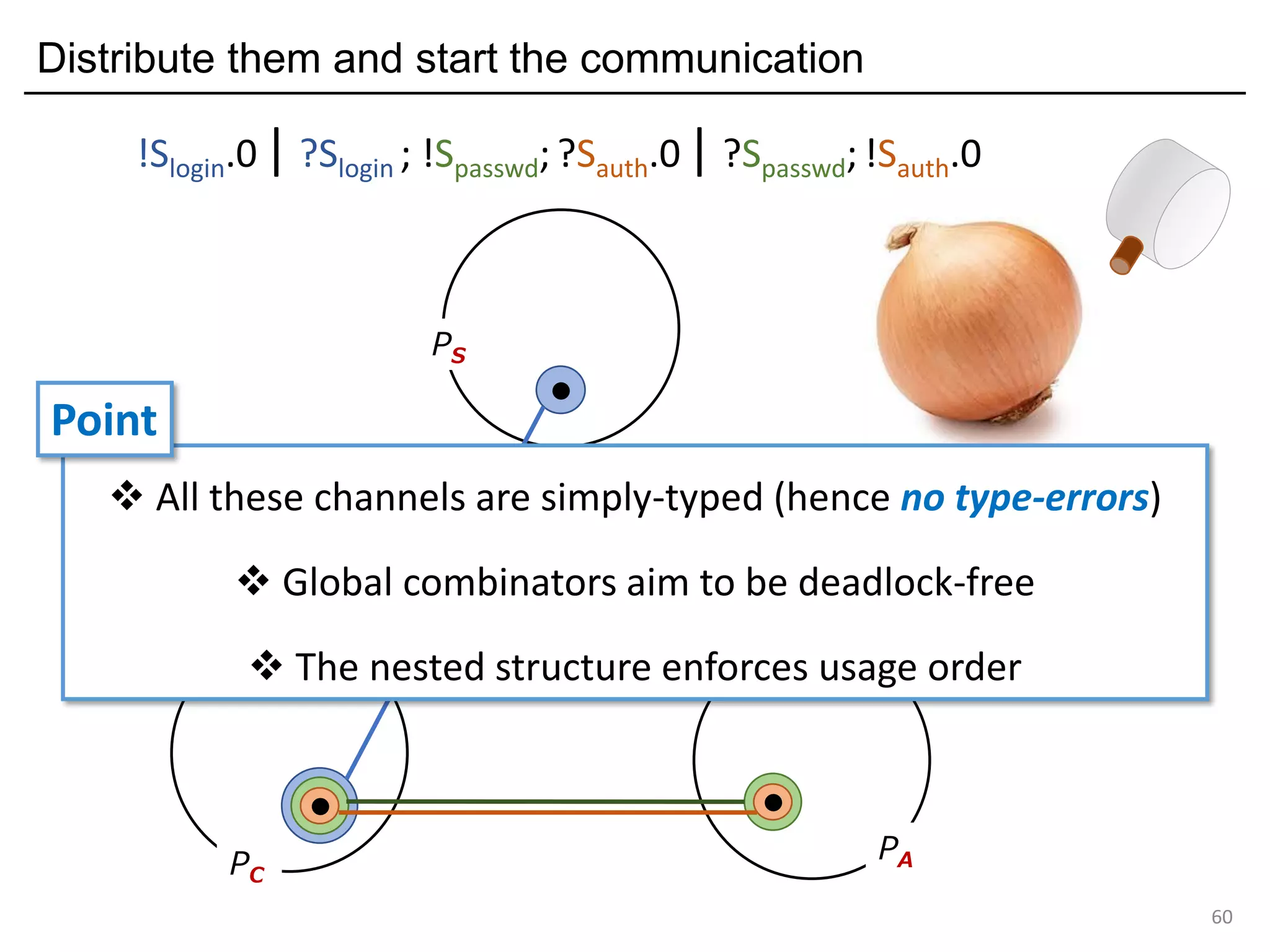
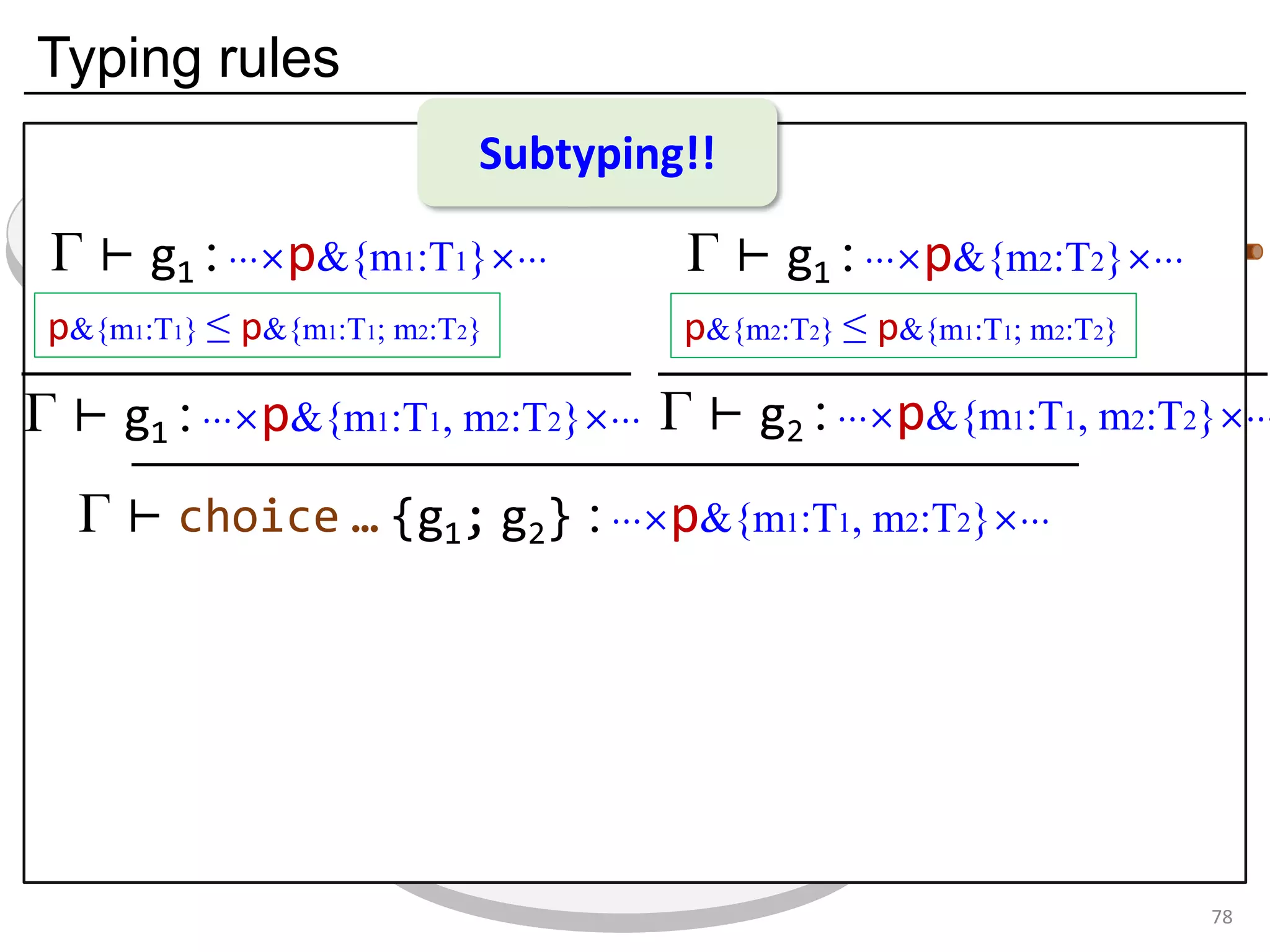
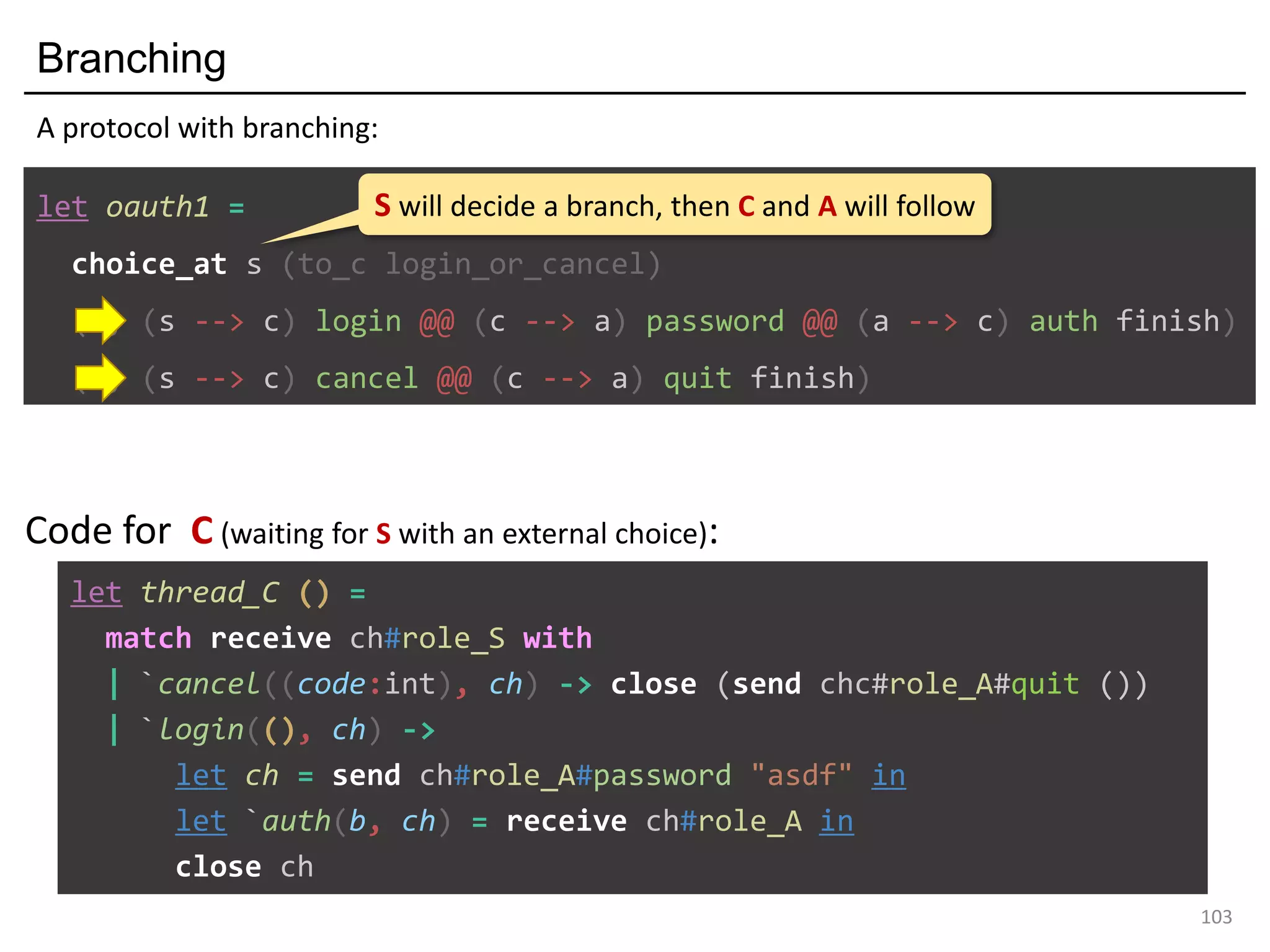
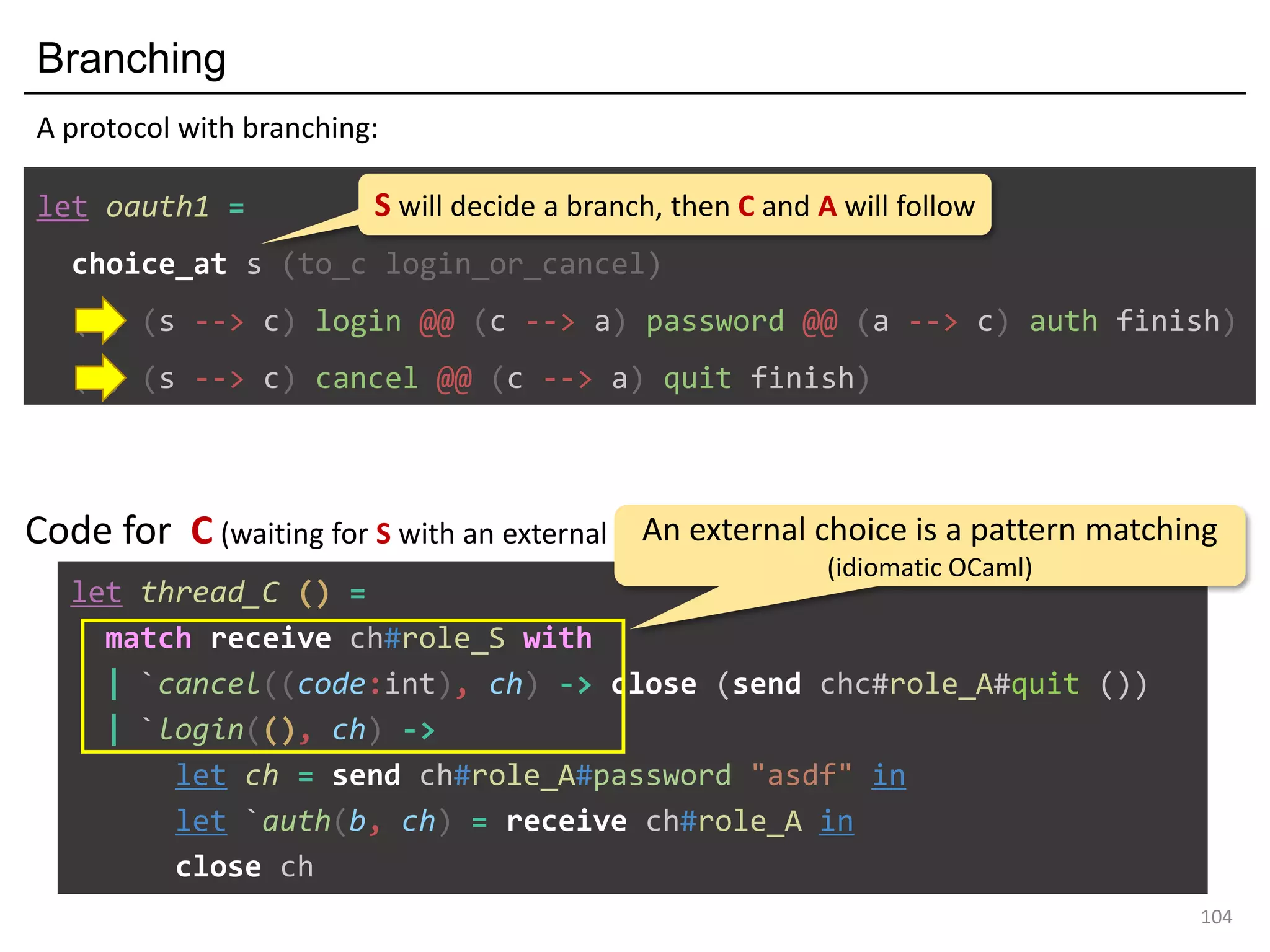
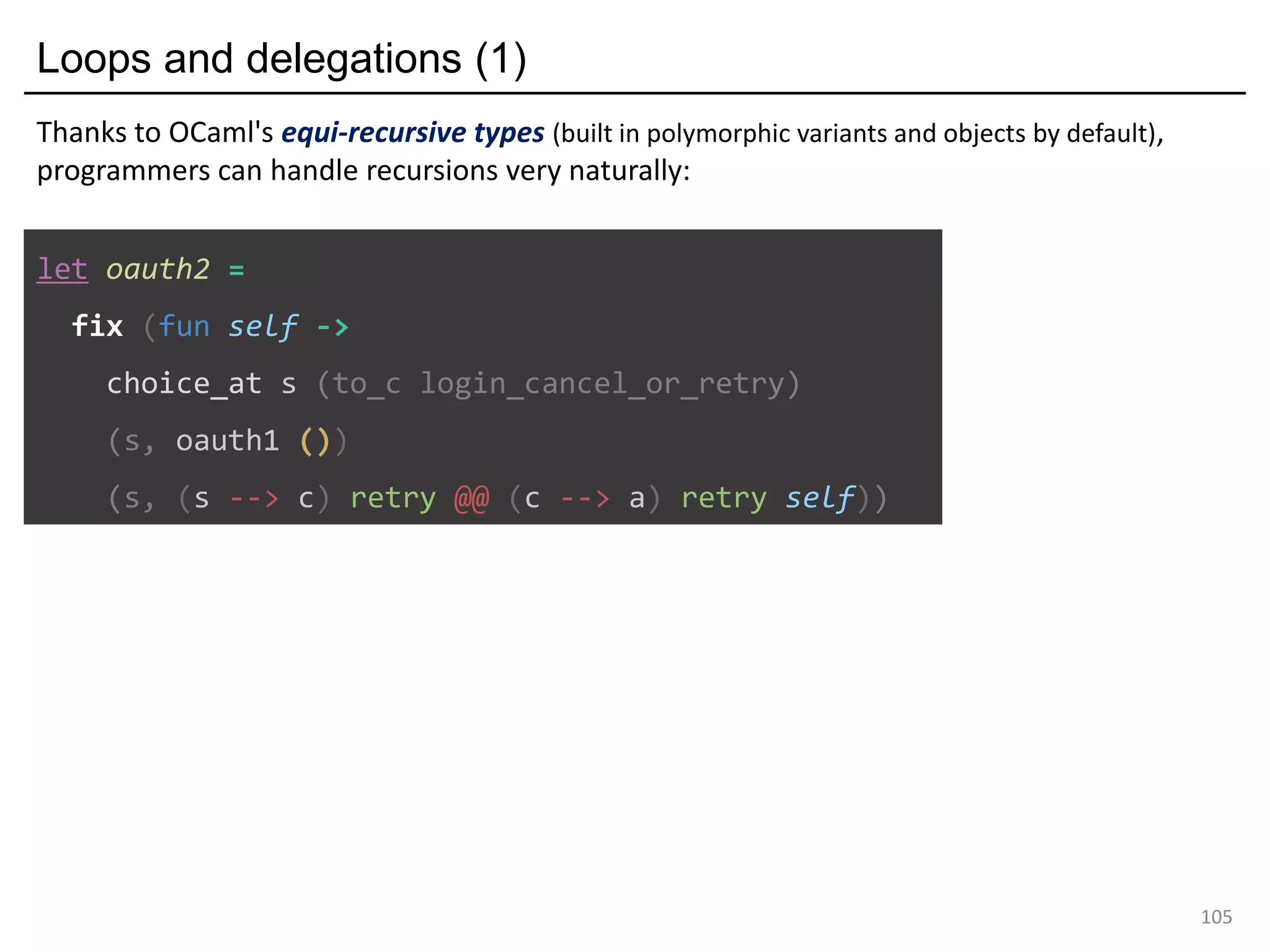
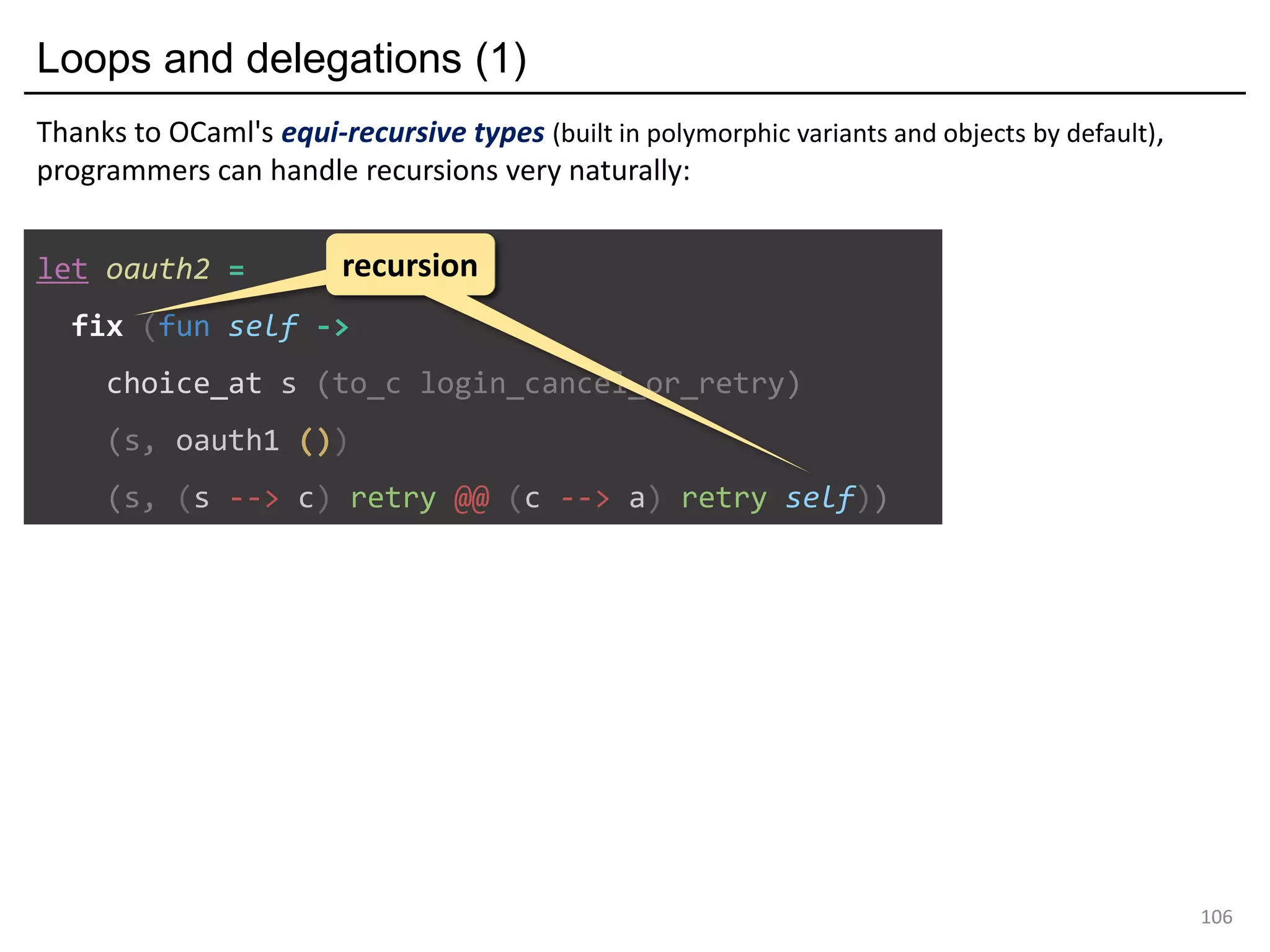
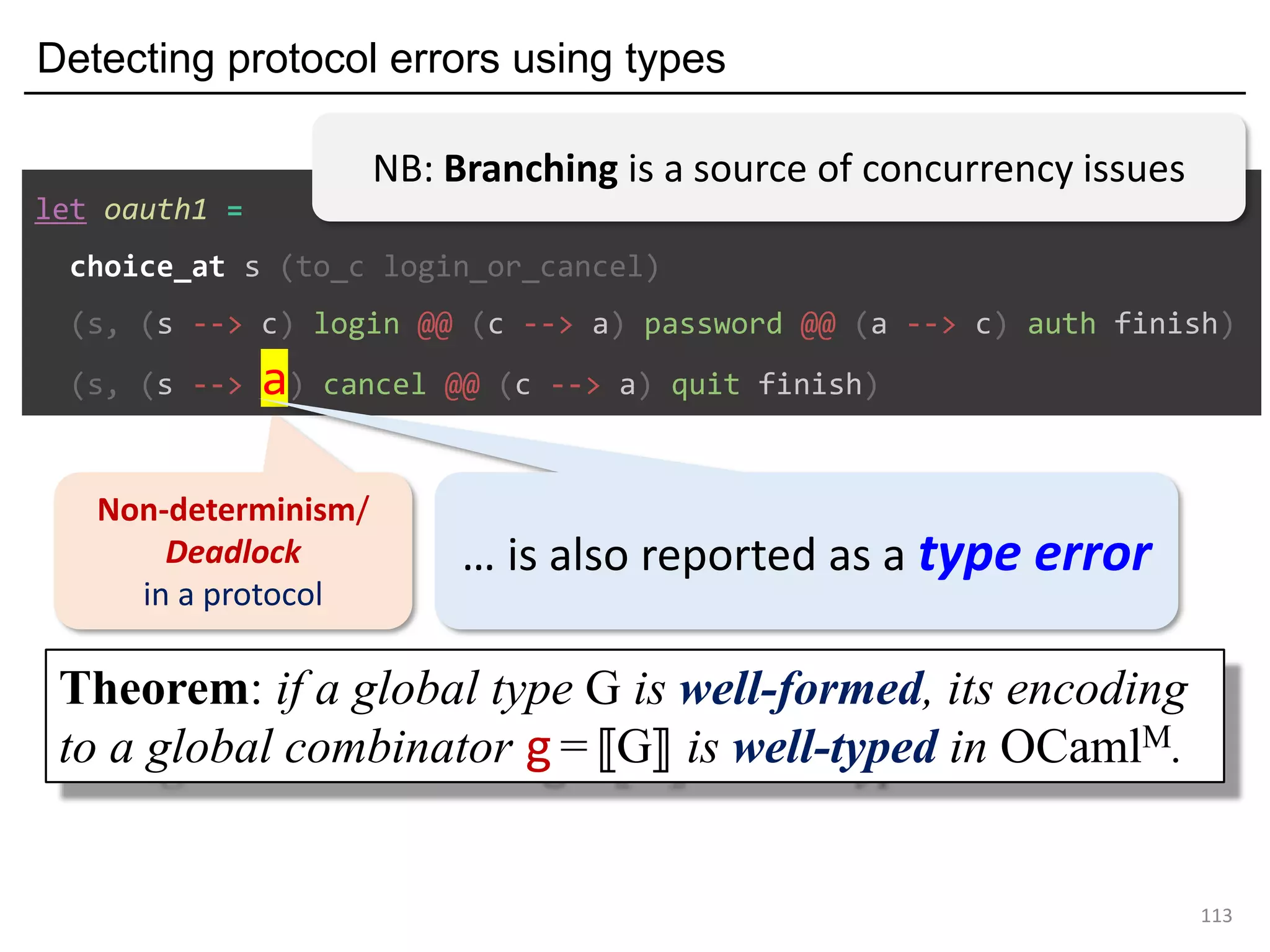
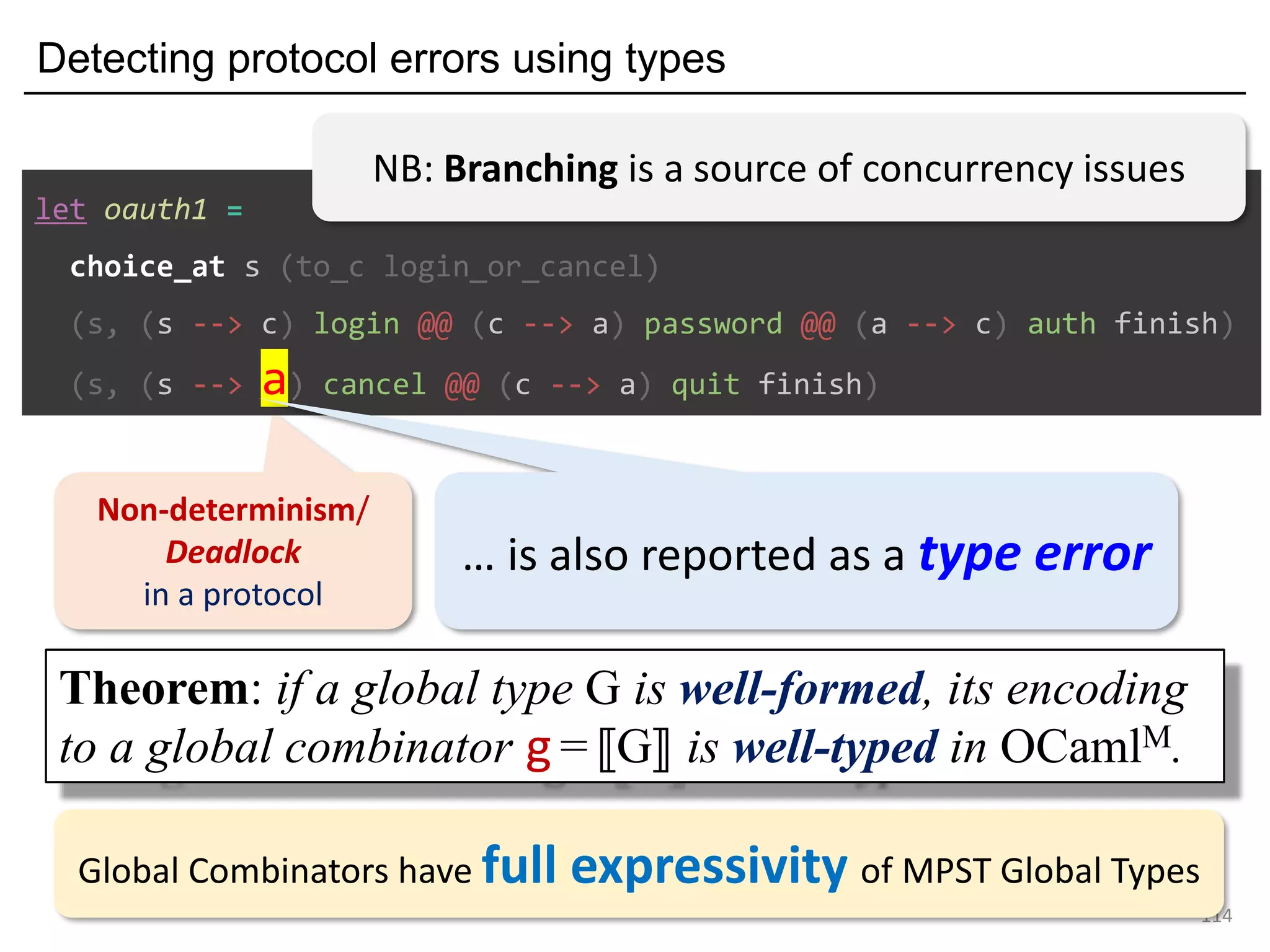
- The document discusses global protocol combinators for specifying multiparty session types in OCaml.
- It presents an approach to ensure deadlock-freedom solely through type checking in OCaml, without code generation. Local types are inferred from the global protocol specification.
- Well-formedness of the global protocol and type checking of the OCaml program ensure deadlock-freedom. Branching and non-determinism in protocols can be detected as type errors.
![deadlock-free?
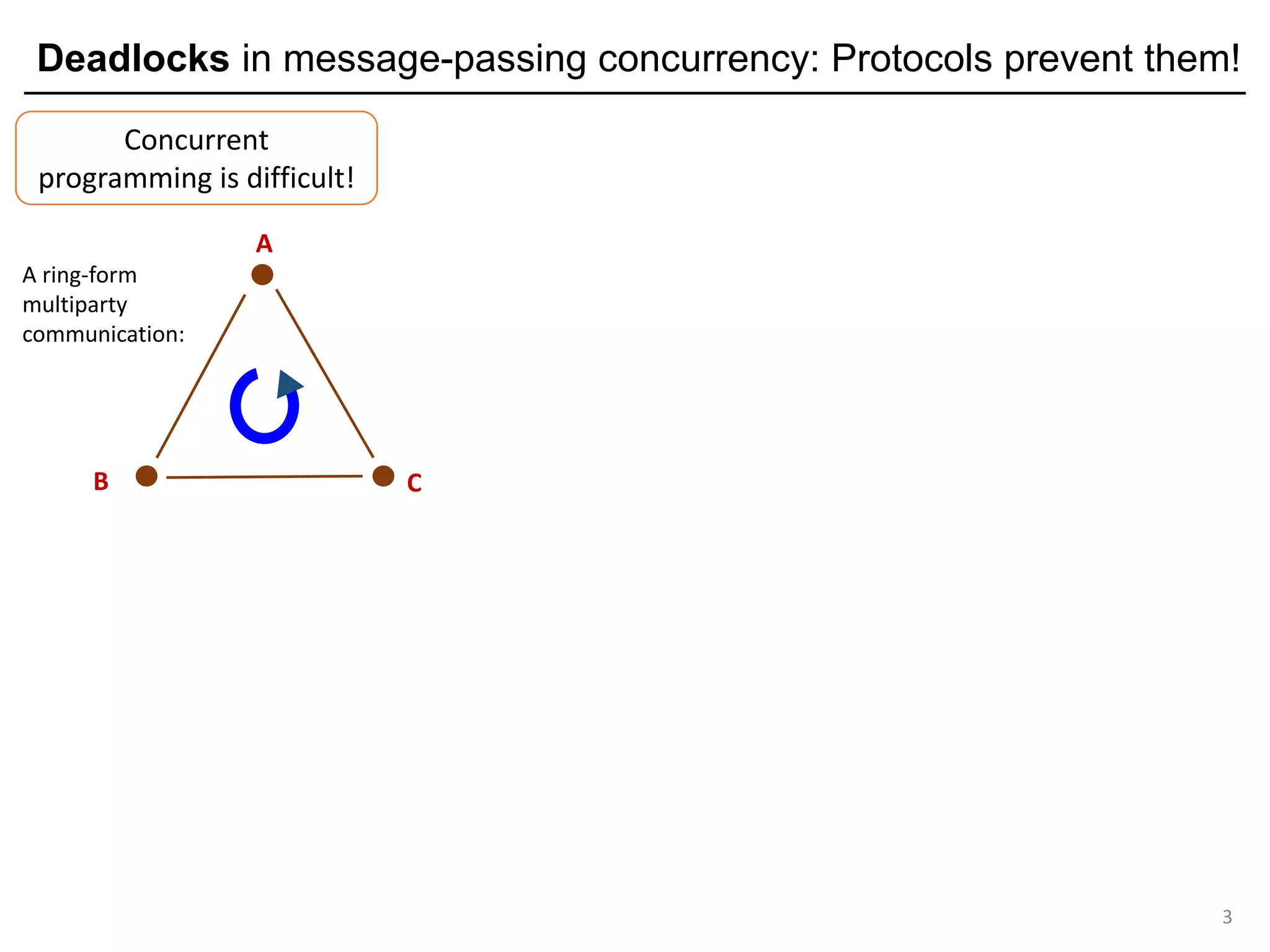
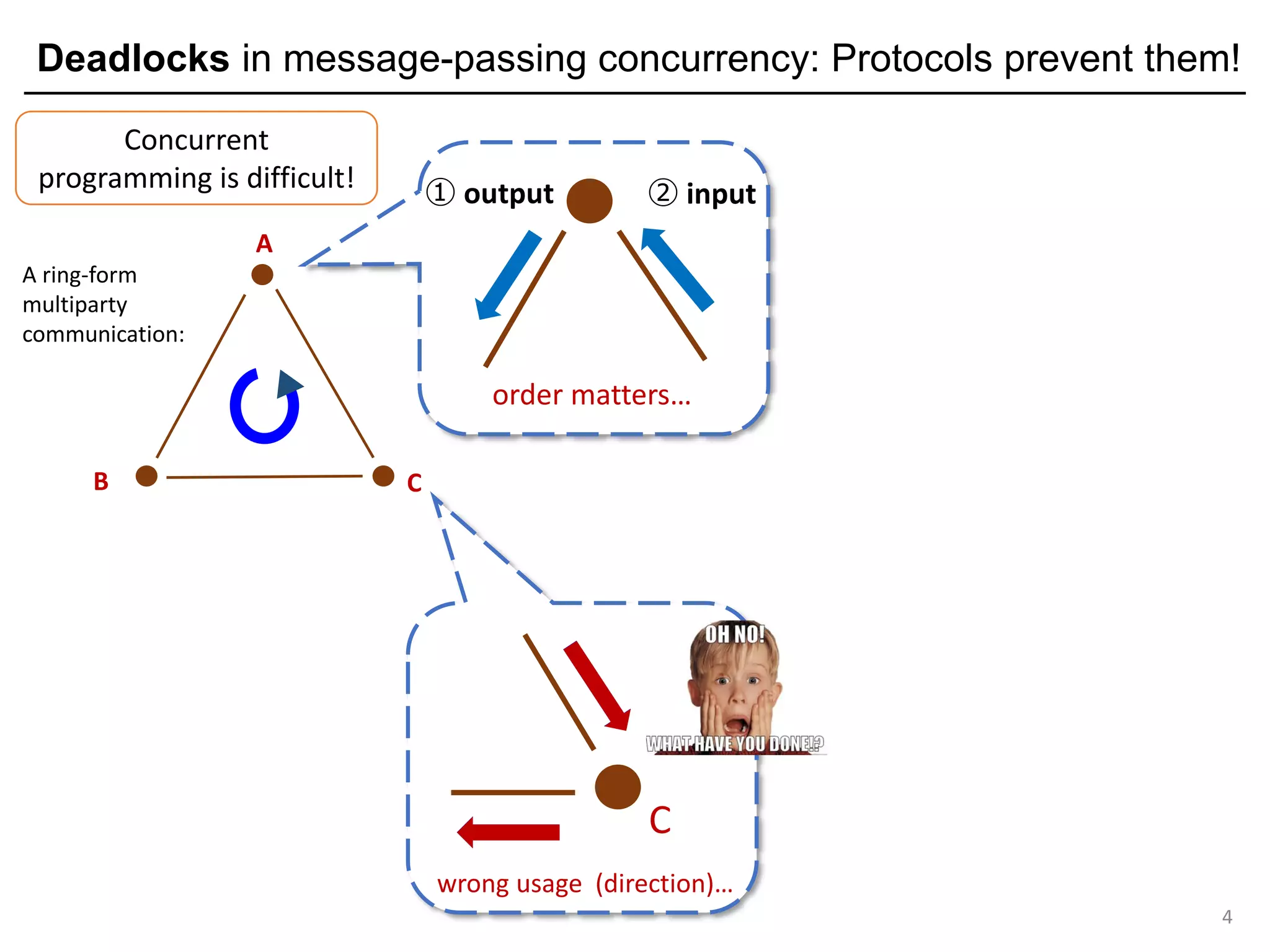
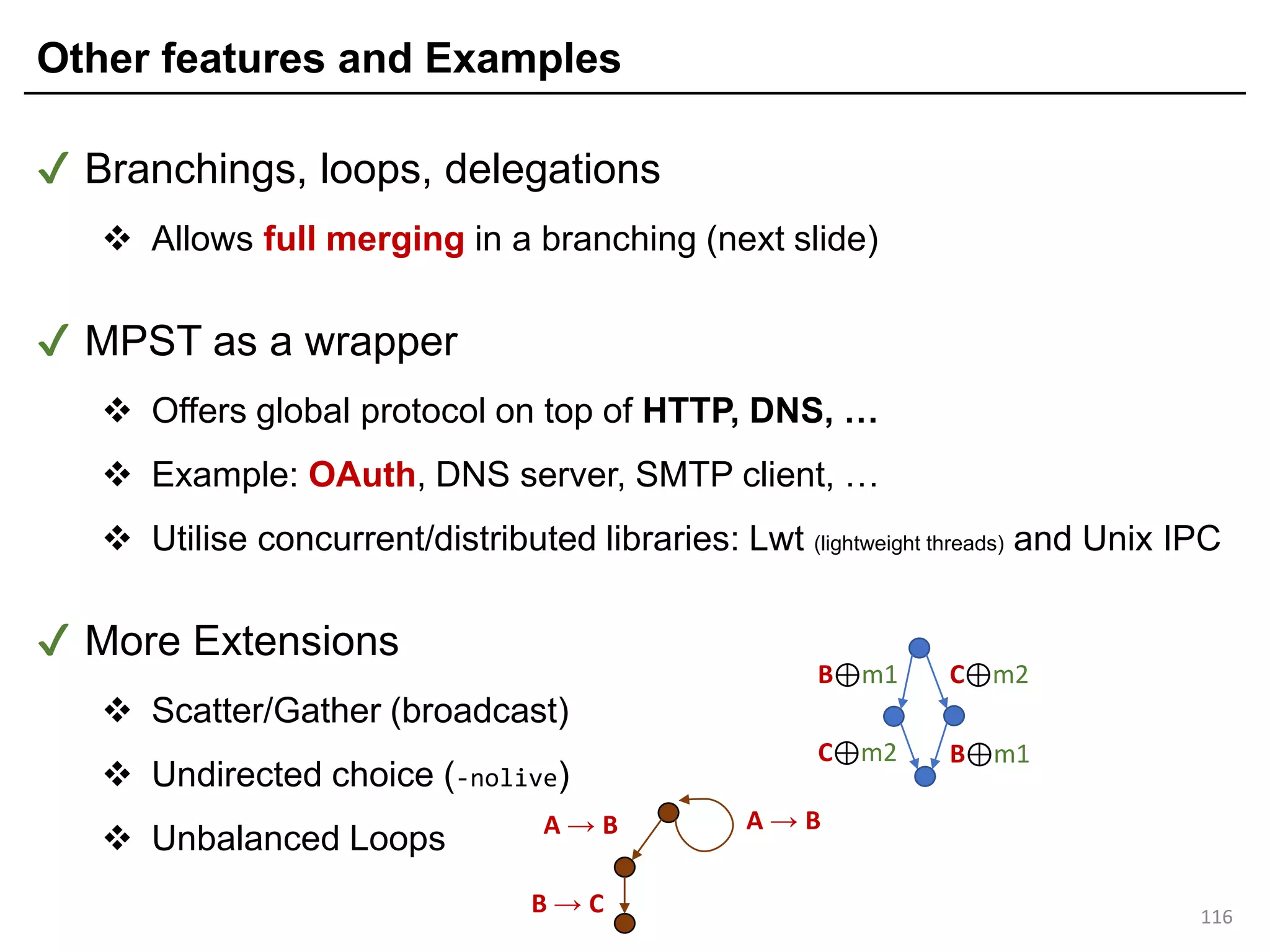
Multiparty Session Types (MPSTs): Protocol-based deadlock freedom
7
C S
a "ping" protocol
③ Give concurrent processes (programs) and check their types
① Write a Global Type and check it
② Derive Local Types by End Point Projection (↾)
PC | PS
The system PC | PS is
[Honda et al., 2008]](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-7-2048.jpg)
![deadlock-free?
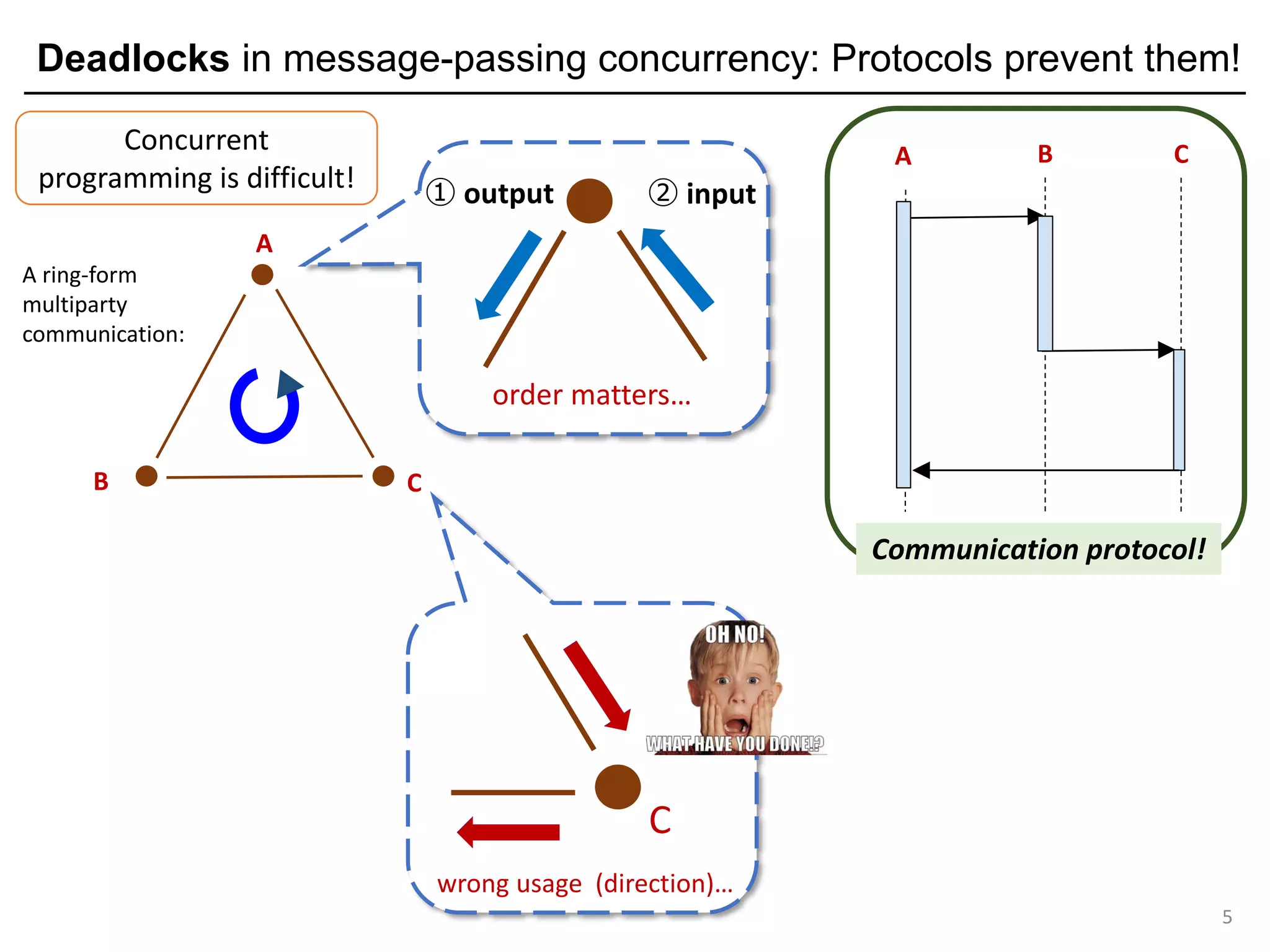
Multiparty Session Types (MPSTs): Protocol-based deadlock freedom
8
C S
a "ping" protocol
③ Give concurrent processes (programs) and check their types
① Write a Global Type and check it
② Derive Local Types by End Point Projection (↾)
PC | PS
The system PC | PS is
"well-formed": protocol G iswf(G) ✔
G = C → S. S → C.end
deadlock-free
[Honda et al., 2008]](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-8-2048.jpg)
![deadlock-free?
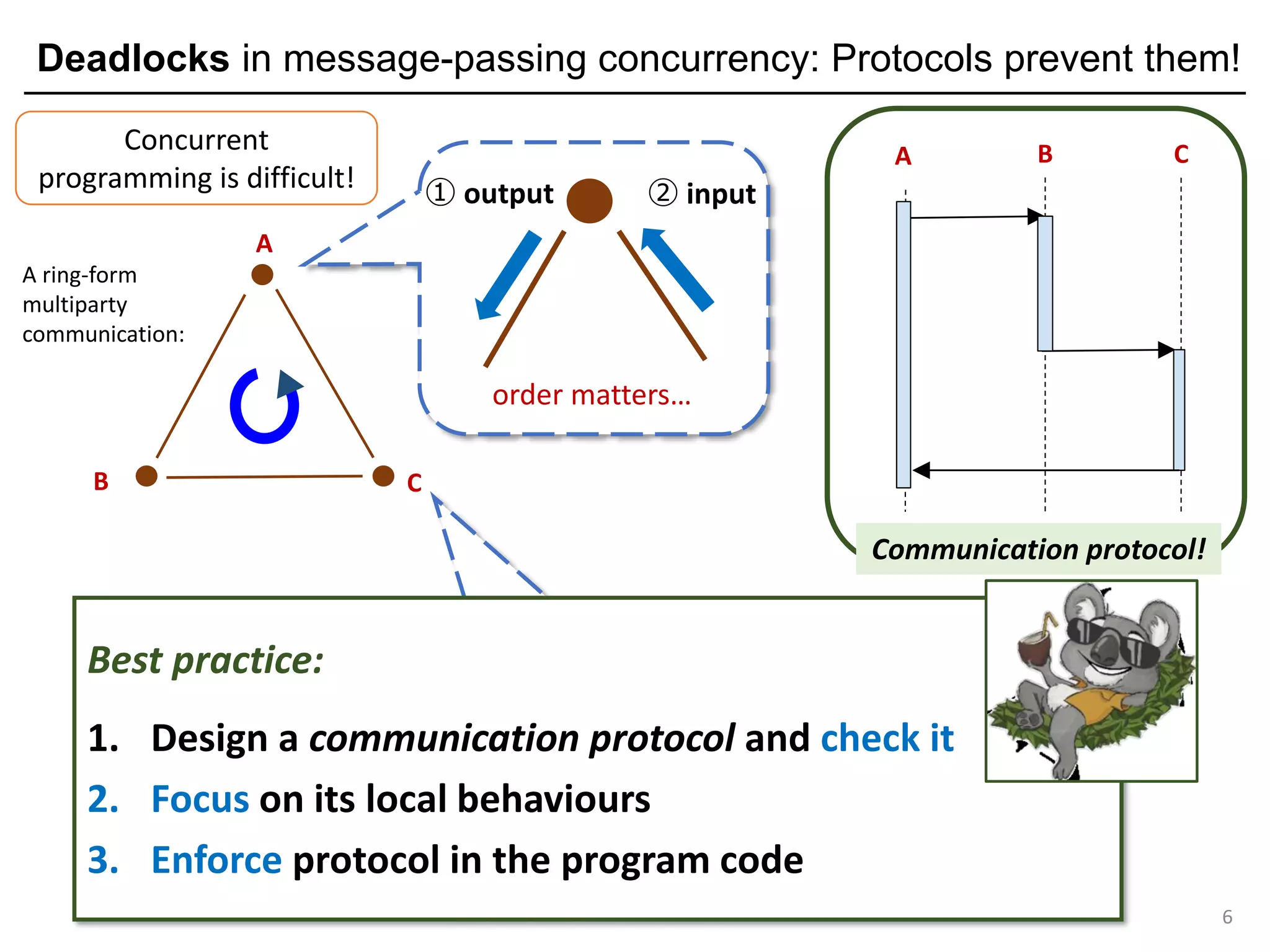
Multiparty Session Types (MPSTs): Protocol-based deadlock freedom
9
C S
a "ping" protocol
③ Give concurrent processes (programs) and check their types
① Write a Global Type and check it
② Derive Local Types by End Point Projection (↾)
PC | PS
The system PC | PS is
"well-formed": protocol G iswf(G) ✔
G = C → S. S → C.end
deadlock-free
G↾C = LC = LSG↾S
S! S?
C? C!
LC =
LS =
: "views" of the protocol
[Honda et al., 2008]](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-9-2048.jpg)
![deadlock-free?
Multiparty Session Types (MPSTs): Protocol-based deadlock freedom
10
C S
a "ping" protocol
③ Give concurrent processes (programs) and check their types
① Write a Global Type and check it
② Derive Local Types by End Point Projection (↾)
PC | PS
The system PC | PS is
✔✔ : "these processes respect the protocol"PSPC LS ⊢LC ⊢
"well-formed": protocol G iswf(G) ✔
G = C → S. S → C.end
deadlock-free
G↾C = LC = LSG↾S
S! S?
C? C!
LC =
LS =
: "views" of the protocol
[Honda et al., 2008]](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-10-2048.jpg)
![deadlock-free?
Multiparty Session Types (MPSTs): Protocol-based deadlock freedom
11
C S
a "ping" protocol
③ Give concurrent processes (programs) and check their types
① Write a Global Type and check it
② Derive Local Types by End Point Projection (↾)
PC | PS
The system PC | PS is
✔✔ : "these processes respect the protocol"PSPC LS ⊢LC ⊢
"well-formed": protocol G iswf(G) ✔
G = C → S. S → C.end
deadlock-free
G↾C = LC = LSG↾S
S! S?
C? C!
LC =
LS =
: "views" of the protocol
deadlock-free!
[Honda et al., 2008]](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-11-2048.jpg)
![deadlock-free?
Multiparty Session Types (MPSTs): Protocol-based deadlock freedom
12
C S
a "ping" protocol
③ Give concurrent processes (programs) and check their types
① Write a Global Type and check it
② Derive Local Types by End Point Projection (↾)
PC | PS
The system PC | PS is
✔✔ : "these processes respect the protocol"PSPC LS ⊢LC ⊢
"well-formed": protocol G iswf(G) ✔
G = C → S. S → C.end
deadlock-free
G↾C = LC = LSG↾S
S! S?
C? C!
LC =
LS =
: "views" of the protocol
deadlock-free!
[Honda et al., 2008]
How to implement MPSTs
in a programming language?
Question](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-12-2048.jpg)
![③ LC ⊢ PC ?
Go
Thread
State of the art: Deadlock freedom via code generation
13
① wf(G) ?
② G↾C
Global
Protocol File
Go
Thread
Go
Thread
In a MPST toolchain for programming language Go [D. Castro et al., POPL 2019]:](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-13-2048.jpg)
![③ LC ⊢ PC ?
Go
Thread
State of the art: Deadlock freedom via code generation
14
① wf(G) ?
② G↾C
Global
Protocol File
Go
Thread
Go
Thread
In a MPST toolchain for programming language Go [D. Castro et al., POPL 2019]:
deadlock-free
(Well-formedness checking
and End Point Projection)
Go type
(Generated
code)
Go type
(Generated
code)
Go type
(Generated
code)
Code
generation
✔](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-14-2048.jpg)
![③ LC ⊢ PC ?
Type checking
by
Go compiler
✔ (type checking to check
protocol conformance)
Go
Thread
State of the art: Deadlock freedom via code generation
15
① wf(G) ?
② G↾C
Global
Protocol File
Go
Thread
Go
Thread
In a MPST toolchain for programming language Go [D. Castro et al., POPL 2019]:
deadlock-free
(Well-formedness checking
and End Point Projection)
Go type
(Generated
code)
Go type
(Generated
code)
Go type
(Generated
code)
Code
generation
✔](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-15-2048.jpg)
![③ LC ⊢ PC ?
Type checking
by
Go compiler
✔ (type checking to check
protocol conformance)
Go
Thread
State of the art: Deadlock freedom via code generation
16
① wf(G) ?
② G↾C
Global
Protocol File
Go
Thread
Go
Thread
In a MPST toolchain for programming language Go [D. Castro et al., POPL 2019]:
deadlock-free
(Well-formedness checking
and End Point Projection)
Go type
(Generated
code)
Go type
(Generated
code)
Go type
(Generated
code)
Code
generation
✔
deadlock-free](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-16-2048.jpg)
![③ LC ⊢ PC ?
Type checking
by
Go compiler
✔ (type checking to check
protocol conformance)
Go
Thread
State of the art: Deadlock freedom via code generation
17
① wf(G) ?
② G↾C
Global
Protocol File
Go
Thread
Go
Thread
In a MPST toolchain for programming language Go [D. Castro et al., POPL 2019]:
deadlock-free
(Well-formedness checking
and End Point Projection)
Go type
(Generated
code)
Go type
(Generated
code)
Go type
(Generated
code)
Code
generation
✔
deadlock-free
Is it possible to implement MPSTs
without code generation?
Question](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-17-2048.jpg)
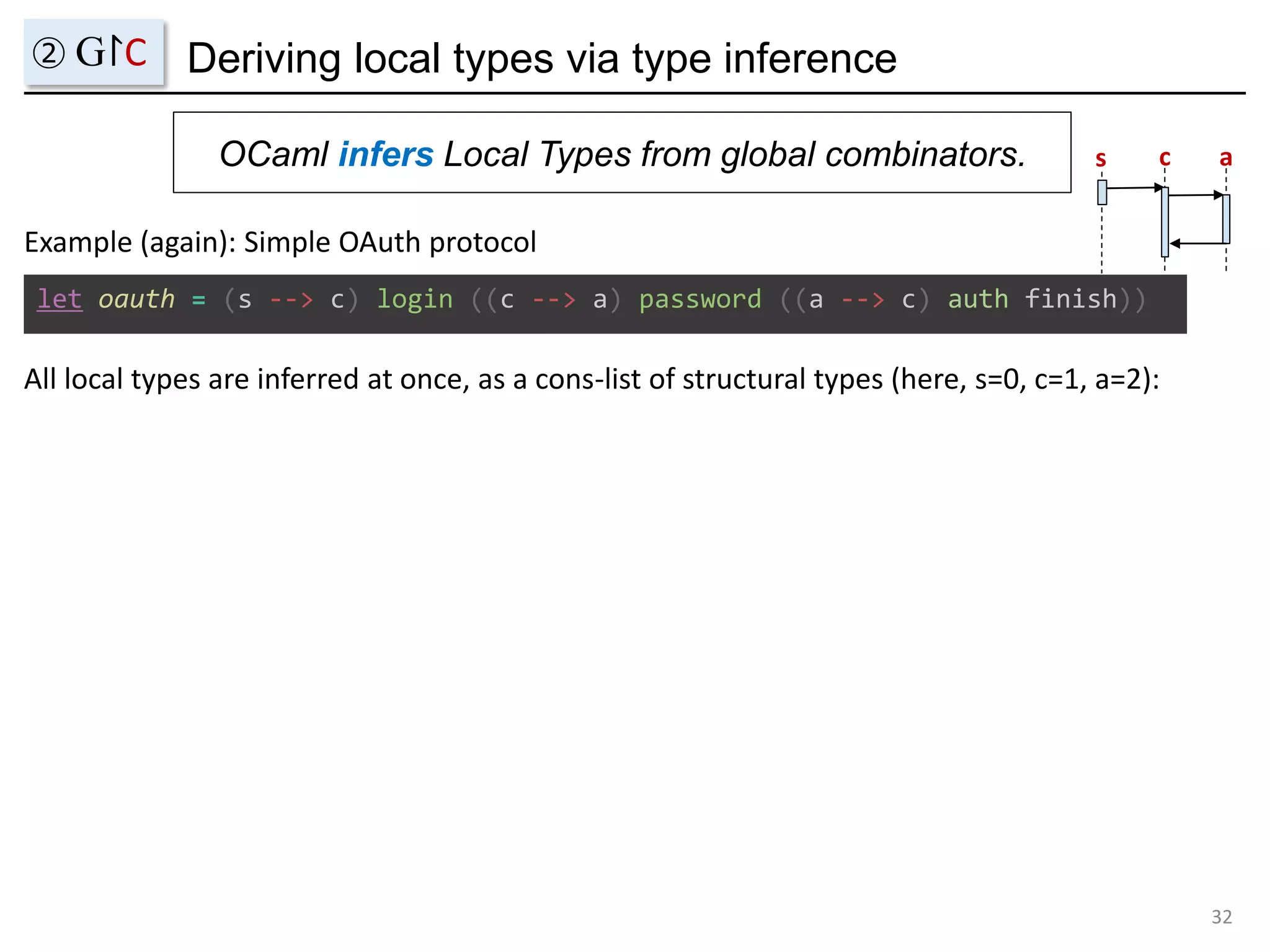
![Deriving local types via type inference
OCaml infers Local Types from global combinators.
33
② G↾C
let oauth = (s --> c) login ((c --> a) password ((a --> c) auth finish))
Example (again): Simple OAuth protocol
s c a
All local types are inferred at once, as a cons-list of structural types (here, s=0, c=1, a=2):
val oauth :
[ `cons of
< role_C : < login : ('a * close) out lin > > *
[ `cons of
< role_S : [> `login of 'a *
< role_A : < password : ('b *
< role_A : [> `auth of 'c *
close ] inp lin >) out lin > > ] inp lin > *
[ `cons of
< role_C : [> `password of 'b *
< role_C : < auth : ('c *
close) out lin > > ] inp lin > *
([ `cons of close * 'x ] as 'x) ] ] ] Seq.t
c!login
s?login a!pass a?auth
s!pass s?auth
s
c
a](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-33-2048.jpg)
![Deriving local types via type inference
OCaml infers Local Types from global combinators.
34
② G↾C
let oauth = (s --> c) login ((c --> a) password ((a --> c) auth finish))
Example (again): Simple OAuth protocol
s c a
All local types are inferred at once, as a cons-list of structural types (here, s=0, c=1, a=2):
val oauth :
[ `cons of
< role_C : < login : ('a * close) out lin > > *
[ `cons of
< role_S : [> `login of 'a *
< role_A : < password : ('b *
< role_A : [> `auth of 'c *
close ] inp lin >) out lin > > ] inp lin > *
[ `cons of
< role_C : [> `password of 'b *
< role_C : < auth : ('c *
close) out lin > > ] inp lin > *
([ `cons of close * 'x ] as 'x) ] ] ] Seq.t
c!login
s?login a!pass a?auth
s!pass s?auth
s
c
a
Destination role's names are a method of an object
< role_S
< role_A
< role_A](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-34-2048.jpg)
![Deriving local types via type inference
OCaml infers Local Types from global combinators.
35
② G↾C
let oauth = (s --> c) login ((c --> a) password ((a --> c) auth finish))
Example (again): Simple OAuth protocol
s c a
All local types are inferred at once, as a cons-list of structural types (here, s=0, c=1, a=2):
val oauth :
[ `cons of
< role_C : < login : ('a * close) out lin > > *
[ `cons of
< role_S : [> `login of 'a *
< role_A : < password : ('b *
< role_A : [> `auth of 'c *
close ] inp lin >) out lin > > ] inp lin > *
[ `cons of
< role_C : [> `password of 'b *
< role_C : < auth : ('c *
close) out lin > > ] inp lin > *
([ `cons of close * 'x ] as 'x) ] ] ] Seq.t
c!login
s?login a!pass a?auth
s!pass s?auth
s
c
a
Output labels are methods in an object
< password
Destination role's names are a method of an object
< role_S
< role_A
< role_A](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-35-2048.jpg)
![Deriving local types via type inference
OCaml infers Local Types from global combinators.
36
② G↾C
let oauth = (s --> c) login ((c --> a) password ((a --> c) auth finish))
Example (again): Simple OAuth protocol
s c a
All local types are inferred at once, as a cons-list of structural types (here, s=0, c=1, a=2):
val oauth :
[ `cons of
< role_C : < login : ('a * close) out lin > > *
[ `cons of
< role_S : [> `login of 'a *
< role_A : < password : ('b *
< role_A : [> `auth of 'c *
close ] inp lin >) out lin > > ] inp lin > *
[ `cons of
< role_C : [> `password of 'b *
< role_C : < auth : ('c *
close) out lin > > ] inp lin > *
([ `cons of close * 'x ] as 'x) ] ] ] Seq.t
c!login
s?login a!pass a?auth
s!pass s?auth
s
c
a
Input labels are (polymorphic) variant type tags
[ `login
[ `auth
Output labels are methods in an object
< password
Destination role's names are a method of an object
< role_S
< role_A
< role_A](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-36-2048.jpg)
![let ch = get_ch c oauth (* get a MPST channel for s *)
val ch :
< role_S : [> `login of 'a *
< role_A : < password : ('b *
< role_A : [> `auth of 'c *
close ] inp lin >) out lin > > ] inp lin >
OCaml>
let oauth = (s --> c) login ((c --> a) password ((a --> c) auth finish))
let thread_C () =
match receive ch#role_S with
| `login((u:string), ch)->
let ch = send ch#role_A#password "asdf" in
match receive ch#role_A with
| `auth((b:bool), ch) ->
close ch
Protocol conformance via OCaml's type checking
37
③ LC ⊢ PC ✔](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-37-2048.jpg)
![let ch = get_ch c oauth (* get a MPST channel for s *)
val ch :
< role_S : [> `login of 'a *
< role_A : < password : ('b *
< role_A : [> `auth of 'c *
close ] inp lin >) out lin > > ] inp lin >
OCaml>
let oauth = (s --> c) login ((c --> a) password ((a --> c) auth finish))
let thread_C () =
match receive ch#role_S with
| `login((u:string), ch)->
let ch = send ch#role_A#password "asdf" in
match receive ch#role_A with
| `auth((b:bool), ch) ->
close ch
Protocol conformance via OCaml's type checking
38
< role_S
Select destination role via method invocation (#)
role_S
③ LC ⊢ PC ✔](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-38-2048.jpg)
![let ch = get_ch c oauth (* get a MPST channel for s *)
val ch :
< role_S : [> `login of 'a *
< role_A : < password : ('b *
< role_A : [> `auth of 'c *
close ] inp lin >) out lin > > ] inp lin >
OCaml>
let oauth = (s --> c) login ((c --> a) password ((a --> c) auth finish))
let thread_C () =
match receive ch#role_S with
| `login((u:string), ch)->
let ch = send ch#role_A#password "asdf" in
match receive ch#role_A with
| `auth((b:bool), ch) ->
close ch
Protocol conformance via OCaml's type checking
39
< role_S
Select destination role via method invocation (#)
role_S
③ LC ⊢ PC ✔
[ `login
`login
… and receive on it, then pattern-match the value against variant tags (labels)
received payload](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-39-2048.jpg)
![let ch = get_ch c oauth (* get a MPST channel for s *)
val ch :
< role_S : [> `login of 'a *
< role_A : < password : ('b *
< role_A : [> `auth of 'c *
close ] inp lin >) out lin > > ] inp lin >
OCaml>
let oauth = (s --> c) login ((c --> a) password ((a --> c) auth finish))
let thread_C () =
match receive ch#role_S with
| `login((u:string), ch)->
let ch = send ch#role_A#password "asdf" in
match receive ch#role_A with
| `auth((b:bool), ch) ->
close ch
Protocol conformance via OCaml's type checking
40
< role_S
Select destination role via method invocation (#)
role_S
③ LC ⊢ PC ✔
[ `login
`login
… and receive on it, then pattern-match the value against variant tags (labels)
received payload
"Next" channel is supplied as a part of the returned value](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-40-2048.jpg)
![let ch = get_ch c oauth (* get a MPST channel for s *)
val ch :
< role_S : [> `login of 'a *
< role_A : < password : ('b *
< role_A : [> `auth of 'c *
close ] inp lin >) out lin > > ] inp lin >
OCaml>
let oauth = (s --> c) login ((c --> a) password ((a --> c) auth finish))
let thread_C () =
match receive ch#role_S with
| `login((u:string), ch)->
let ch = send ch#role_A#password "asdf" in
match receive ch#role_A with
| `auth((b:bool), ch) ->
close ch
Protocol conformance via OCaml's type checking
41
< role_S
Select destination role via method invocation (#)
role_S
< role_A
role_A
③ LC ⊢ PC ✔
[ `login
`login
… and receive on it, then pattern-match the value against variant tags (labels)
received payload
"Next" channel is supplied as a part of the returned value](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-41-2048.jpg)
![let ch = get_ch c oauth (* get a MPST channel for s *)
val ch :
< role_S : [> `login of 'a *
< role_A : < password : ('b *
< role_A : [> `auth of 'c *
close ] inp lin >) out lin > > ] inp lin >
OCaml>
let oauth = (s --> c) login ((c --> a) password ((a --> c) auth finish))
let thread_C () =
match receive ch#role_S with
| `login((u:string), ch)->
let ch = send ch#role_A#password "asdf" in
match receive ch#role_A with
| `auth((b:bool), ch) ->
close ch
Protocol conformance via OCaml's type checking
42
< role_S
Select destination role via method invocation (#)
role_S
< role_A
role_A
③ LC ⊢ PC ✔
[ `login
`login
… and receive on it, then pattern-match the value against variant tags (labels)
received payload
"Next" channel is supplied as a part of the returned value
< password
#password
Select an output label via method invocation (#), then
send it with a payload](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-42-2048.jpg)
![let ch = get_ch c oauth (* get a MPST channel for s *)
val ch :
< role_S : [> `login of 'a *
< role_A : < password : ('b *
< role_A : [> `auth of 'c *
close ] inp lin >) out lin > > ] inp lin >
OCaml>
let oauth = (s --> c) login ((c --> a) password ((a --> c) auth finish))
let thread_C () =
match receive ch#role_S with
| `login((u:string), ch)->
let ch = send ch#role_A#password "asdf" in
match receive ch#role_A with
| `auth((b:bool), ch) ->
close ch
Protocol conformance via OCaml's type checking
43
< role_S
Select destination role via method invocation (#)
role_S
< role_A
role_A
role_A
< role_A
③ LC ⊢ PC ✔
[ `login
`login
… and receive on it, then pattern-match the value against variant tags (labels)
received payload
"Next" channel is supplied as a part of the returned value
< password
#password
Select an output label via method invocation (#), then
send it with a payload](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-43-2048.jpg)
![let ch = get_ch c oauth (* get a MPST channel for s *)
val ch :
< role_S : [> `login of 'a *
< role_A : < password : ('b *
< role_A : [> `auth of 'c *
close ] inp lin >) out lin > > ] inp lin >
OCaml>
let oauth = (s --> c) login ((c --> a) password ((a --> c) auth finish))
let thread_C () =
match receive ch#role_S with
| `login((u:string), ch)->
let ch = send ch#role_A#password "asdf" in
match receive ch#role_A with
| `auth((b:bool), ch) ->
close ch
Protocol conformance via OCaml's type checking
44
< role_S
Select destination role via method invocation (#)
role_S
< role_A
role_A
`auth
[ `auth
role_A
< role_A
③ LC ⊢ PC ✔
[ `login
`login
… and receive on it, then pattern-match the value against variant tags (labels)
received payload
"Next" channel is supplied as a part of the returned value
< password
#password
Select an output label via method invocation (#), then
send it with a payload](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-44-2048.jpg)
![let ch = get_ch s oauth (* get a MPST channel for s *)
val ch :
< role_S : [> `login of 'a *
< role_A : < password : ('b *
< role_A : [> `auth of 'c *
close ] inp lin >) out lin > > ] inp lin >
OCaml>
let oauth = (s --> c) login ((c --> a) password ((a --> c) auth finish))
let thread_C () =
match receive ch#role_S with
| `login((u:string), ch)->
let ch = send ch#role_A#password "asdf" in
match receive ch#role_A with
| `auth((b:bool), ch) ->
close ch
45
Protocol conformance via OCaml's type checking③ LC ⊢ PC ✔
ro
If there is a
typo …
OCaml reports a type error at this point](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-45-2048.jpg)
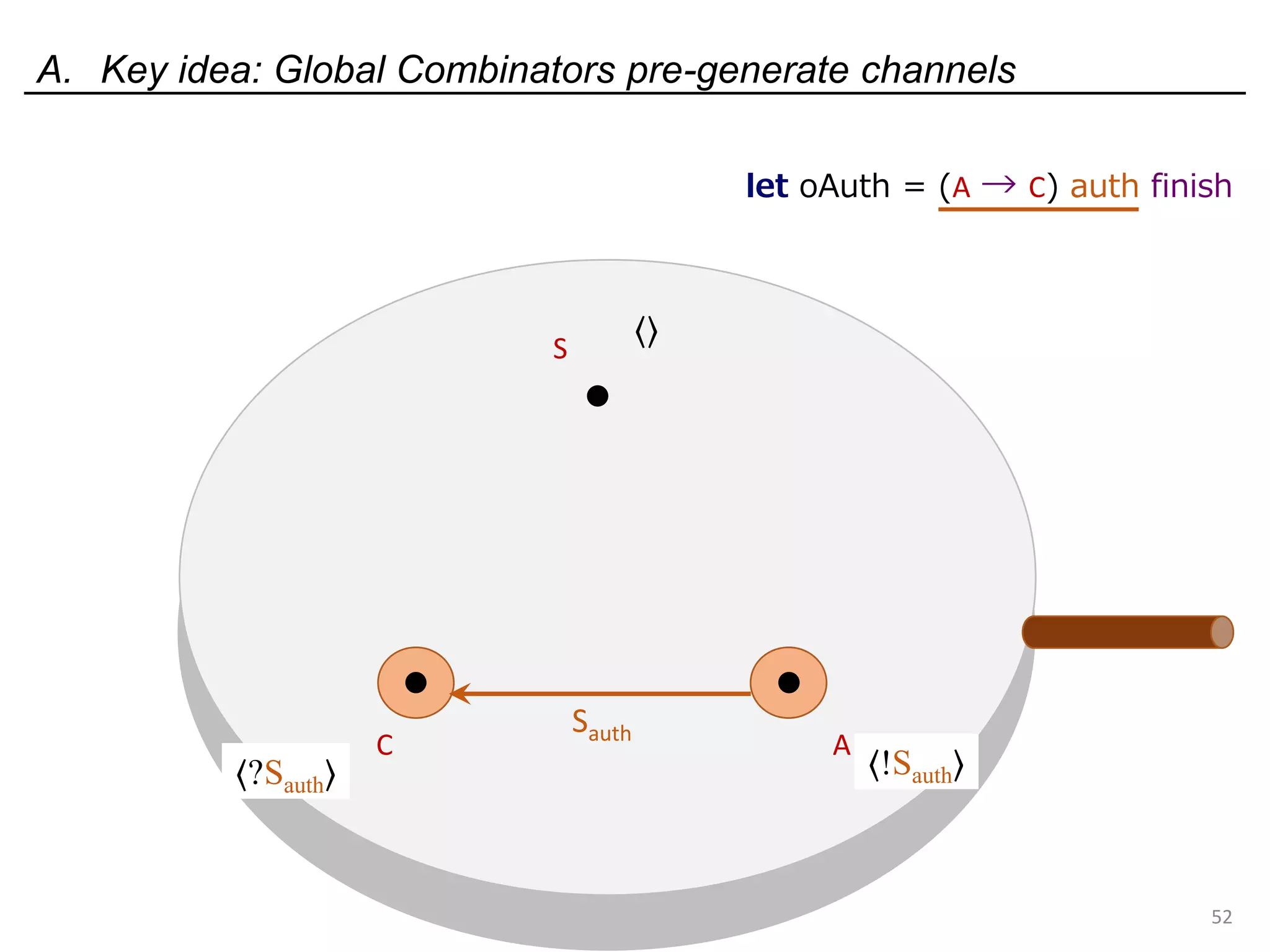
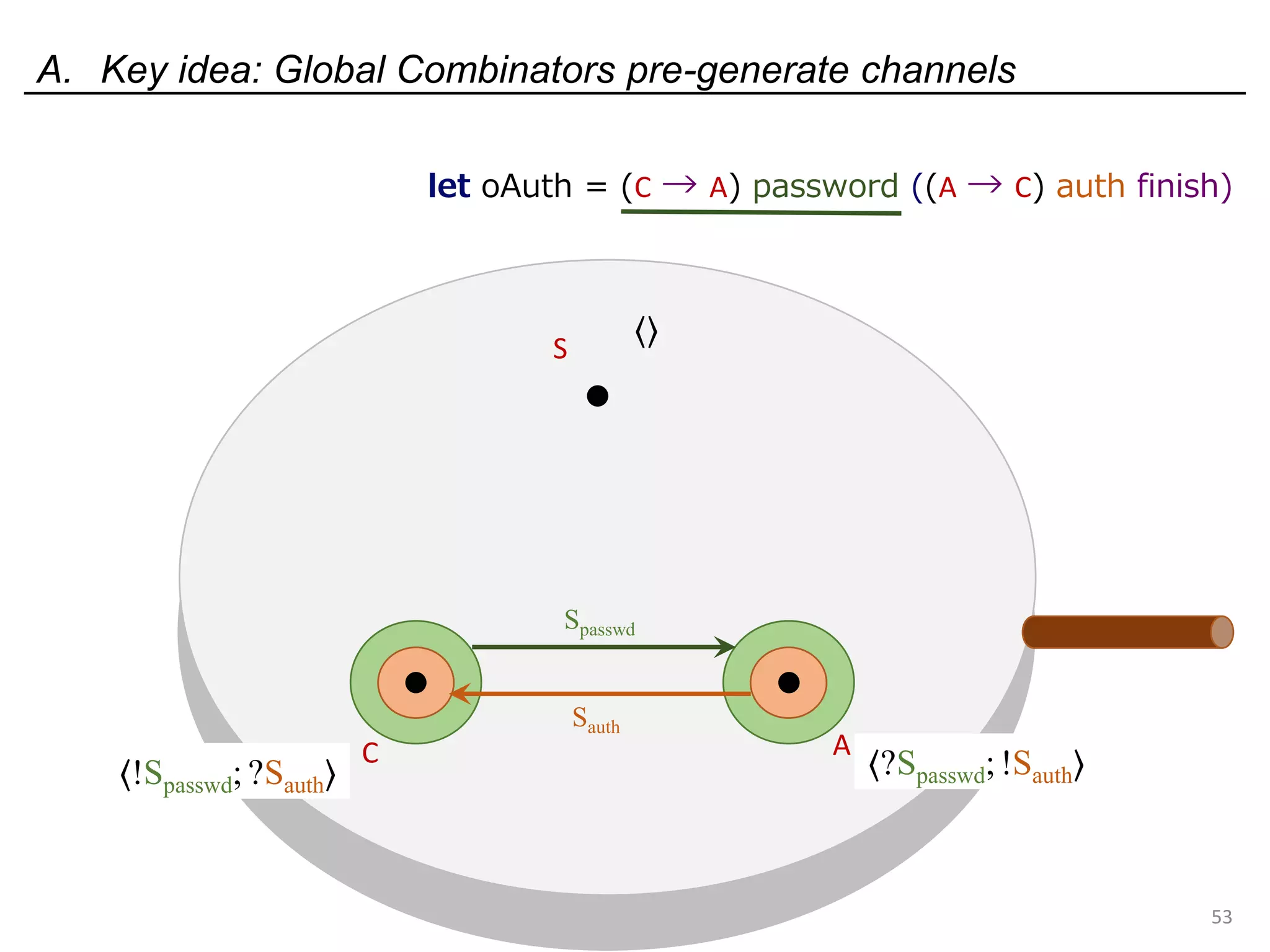
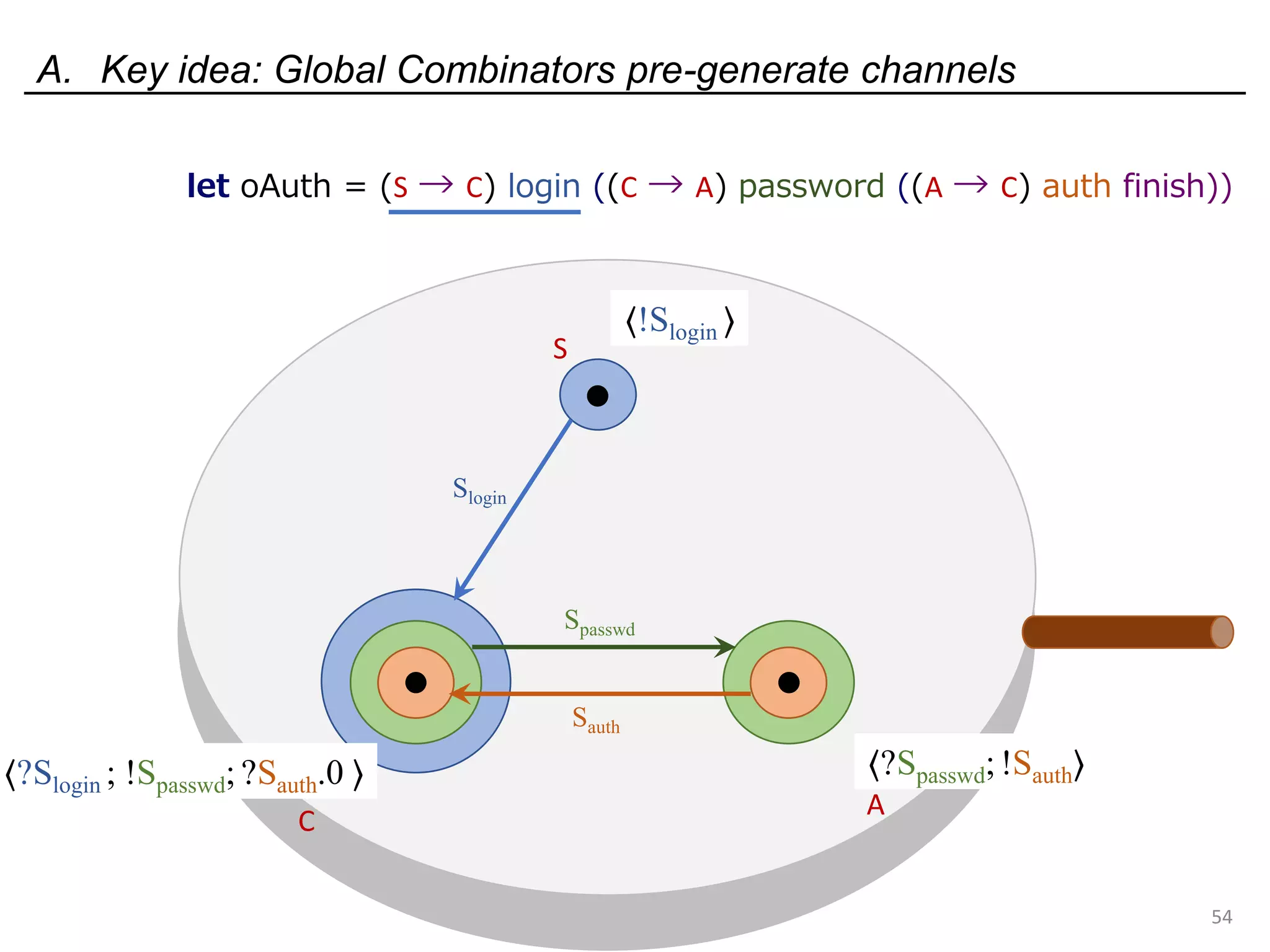
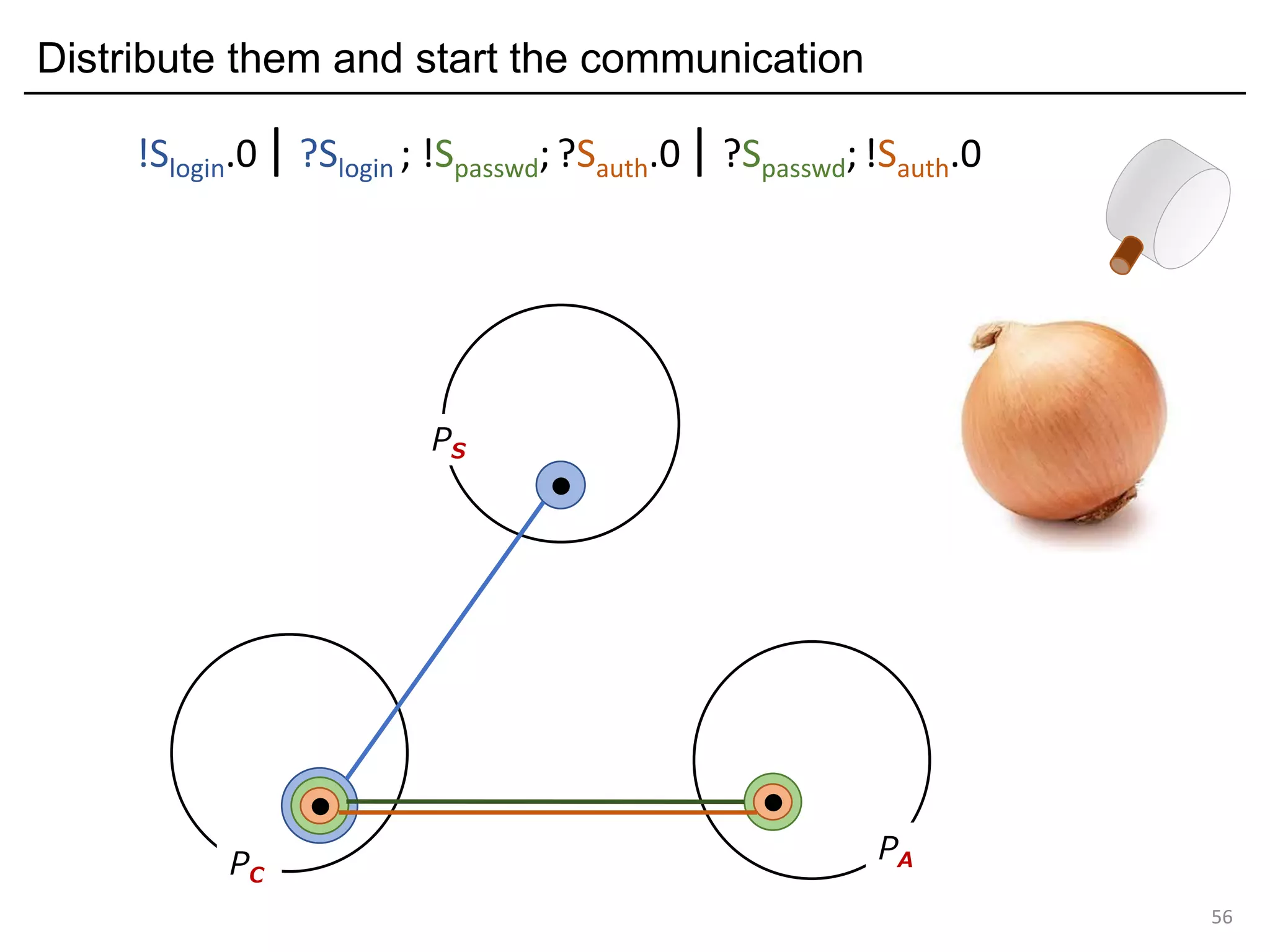
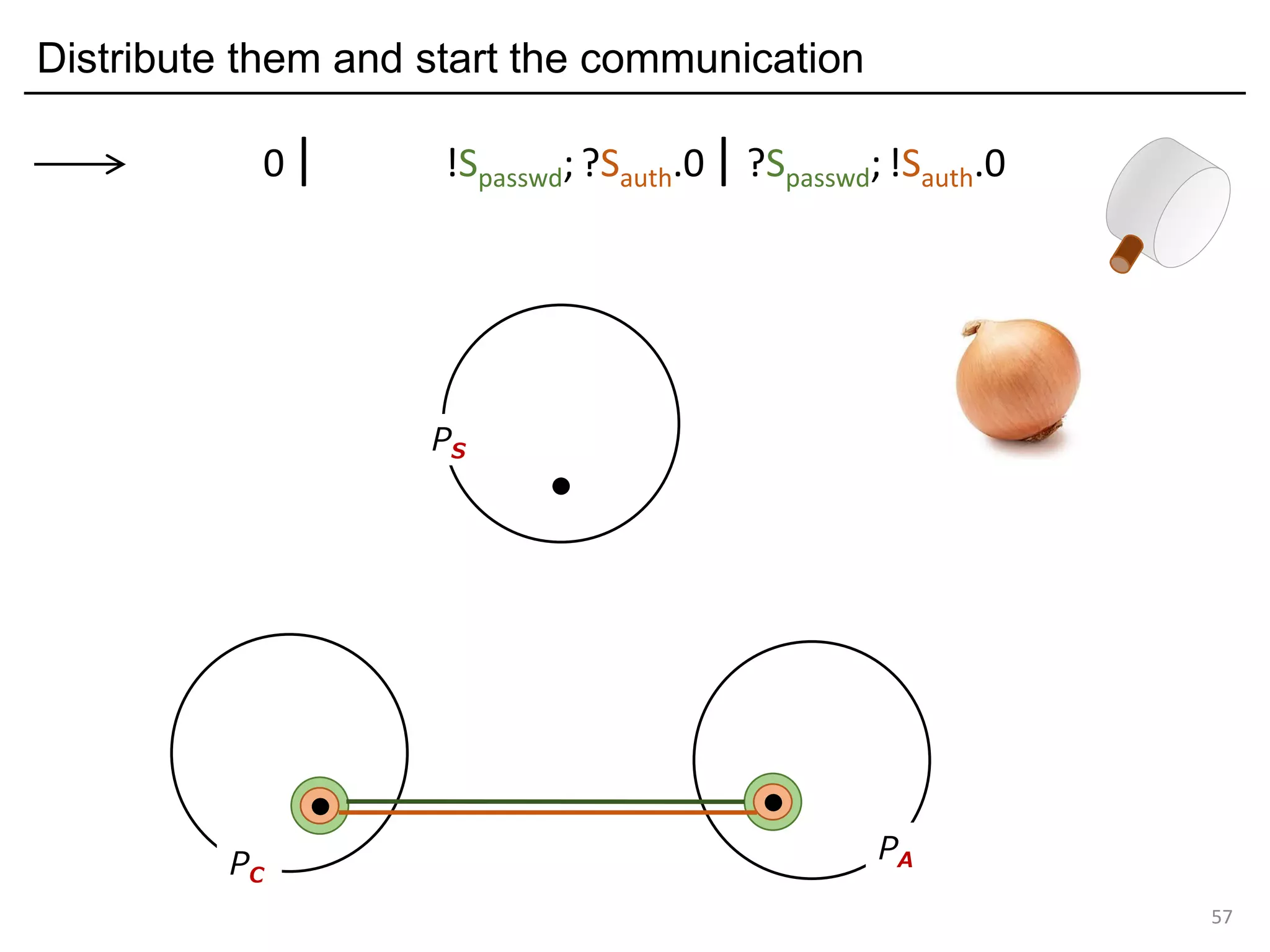
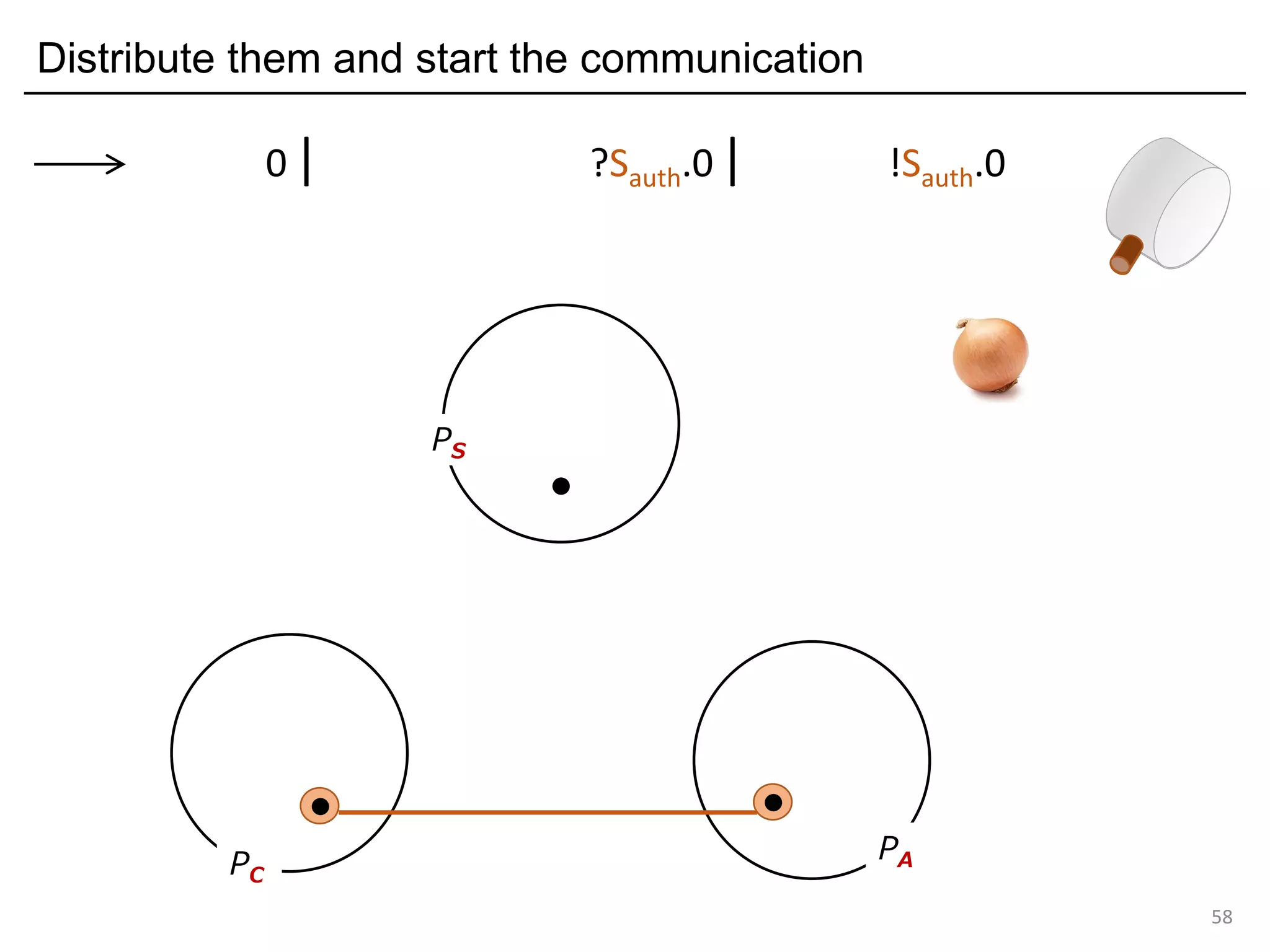
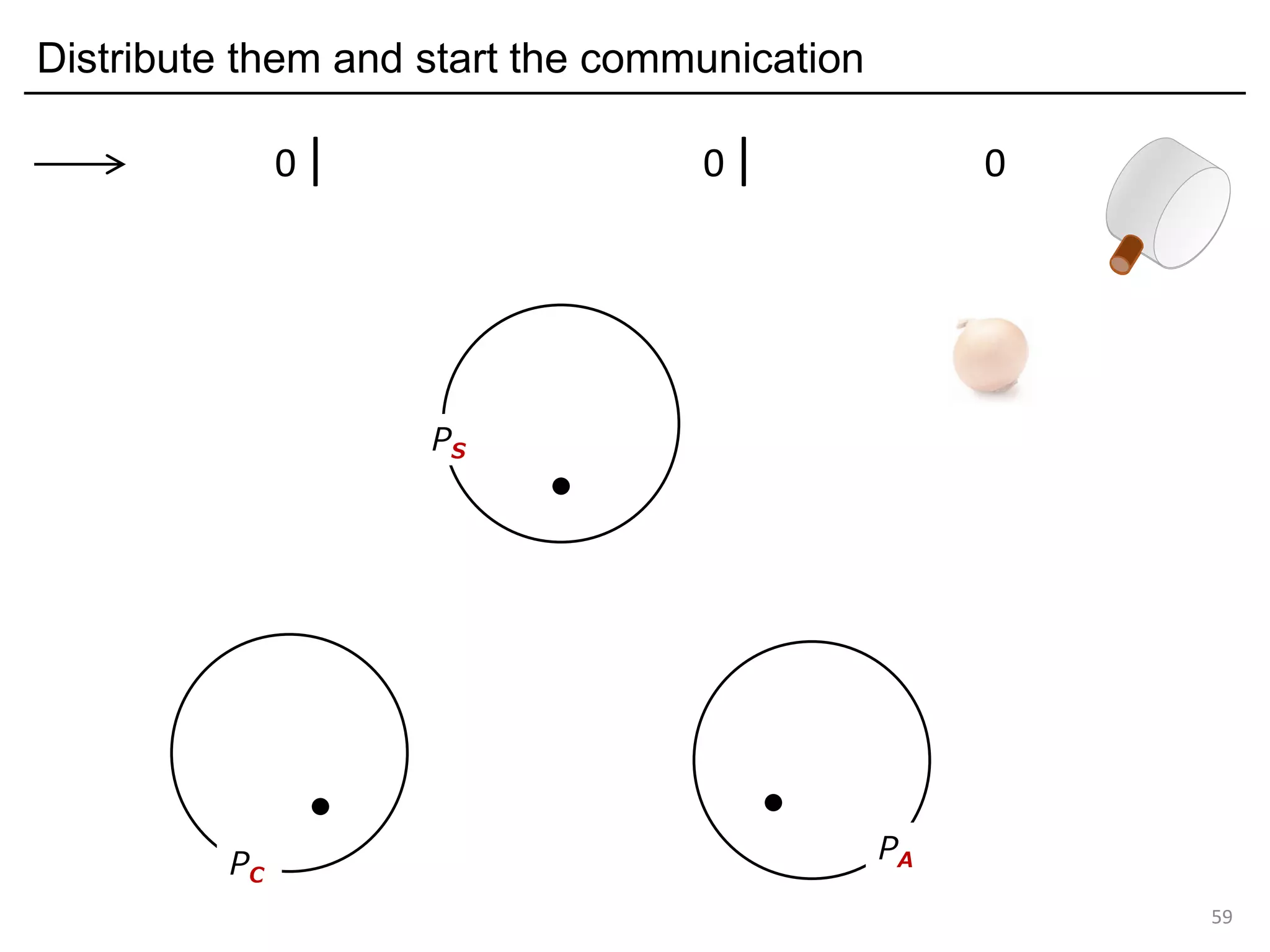

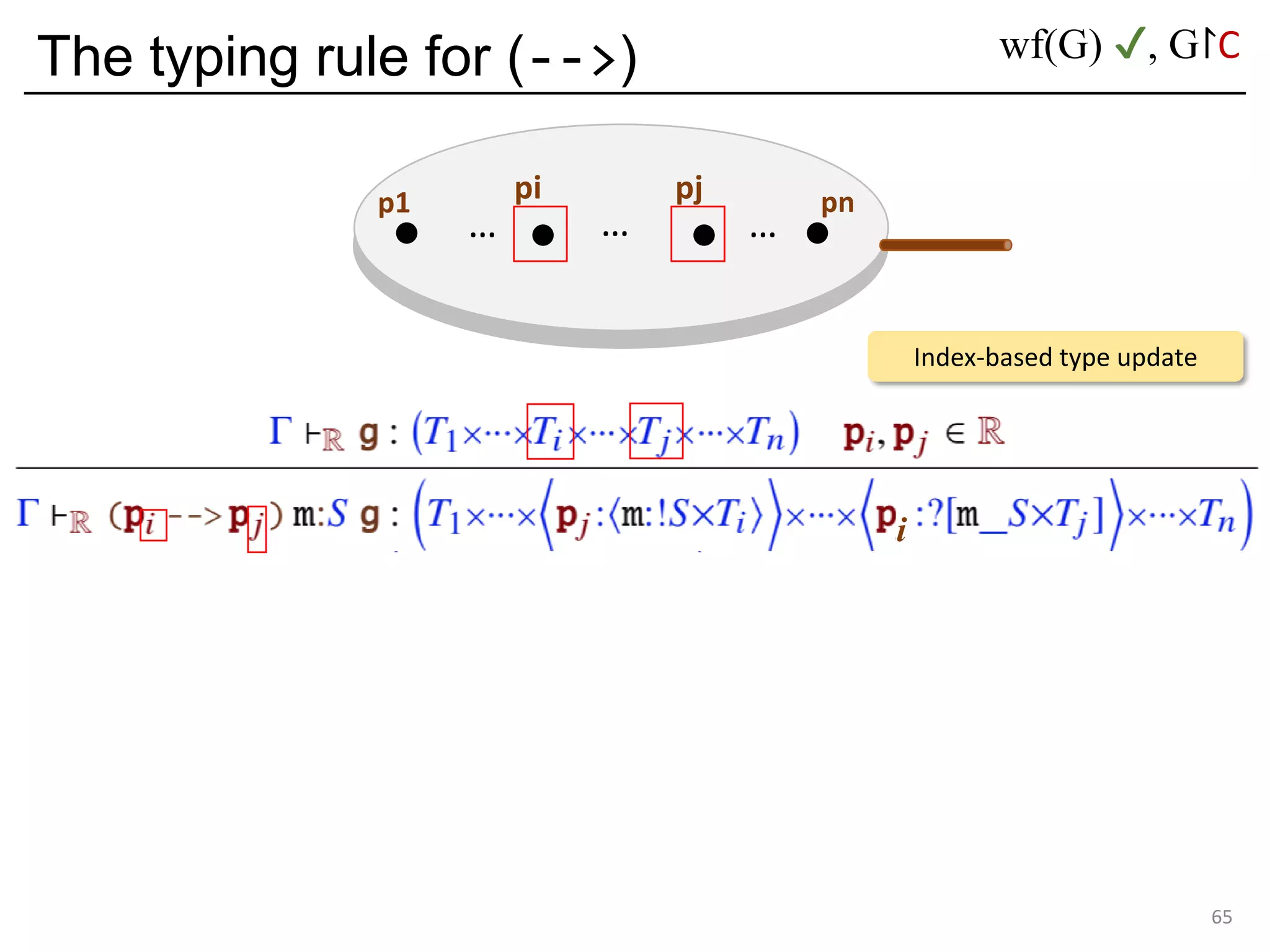
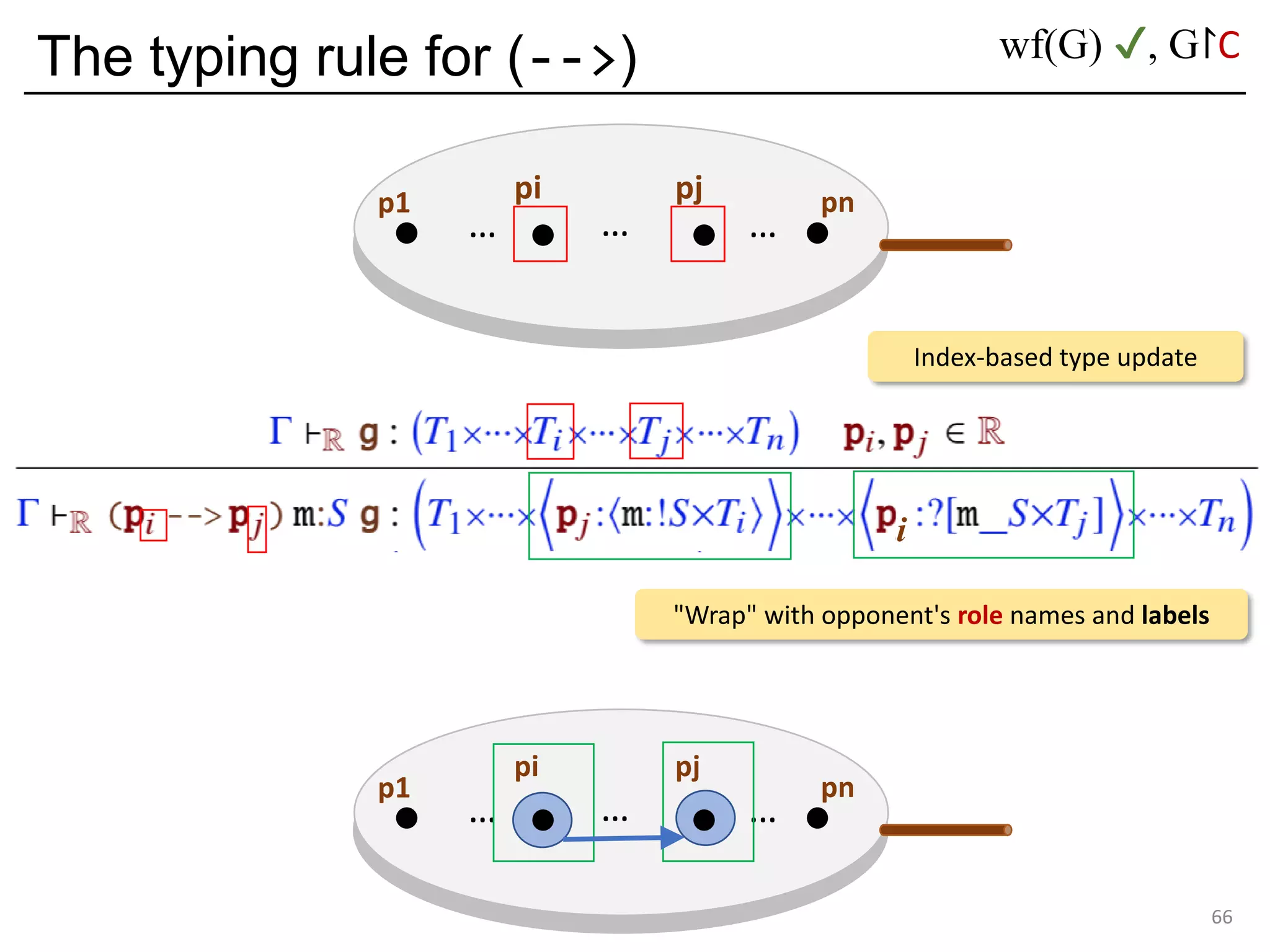
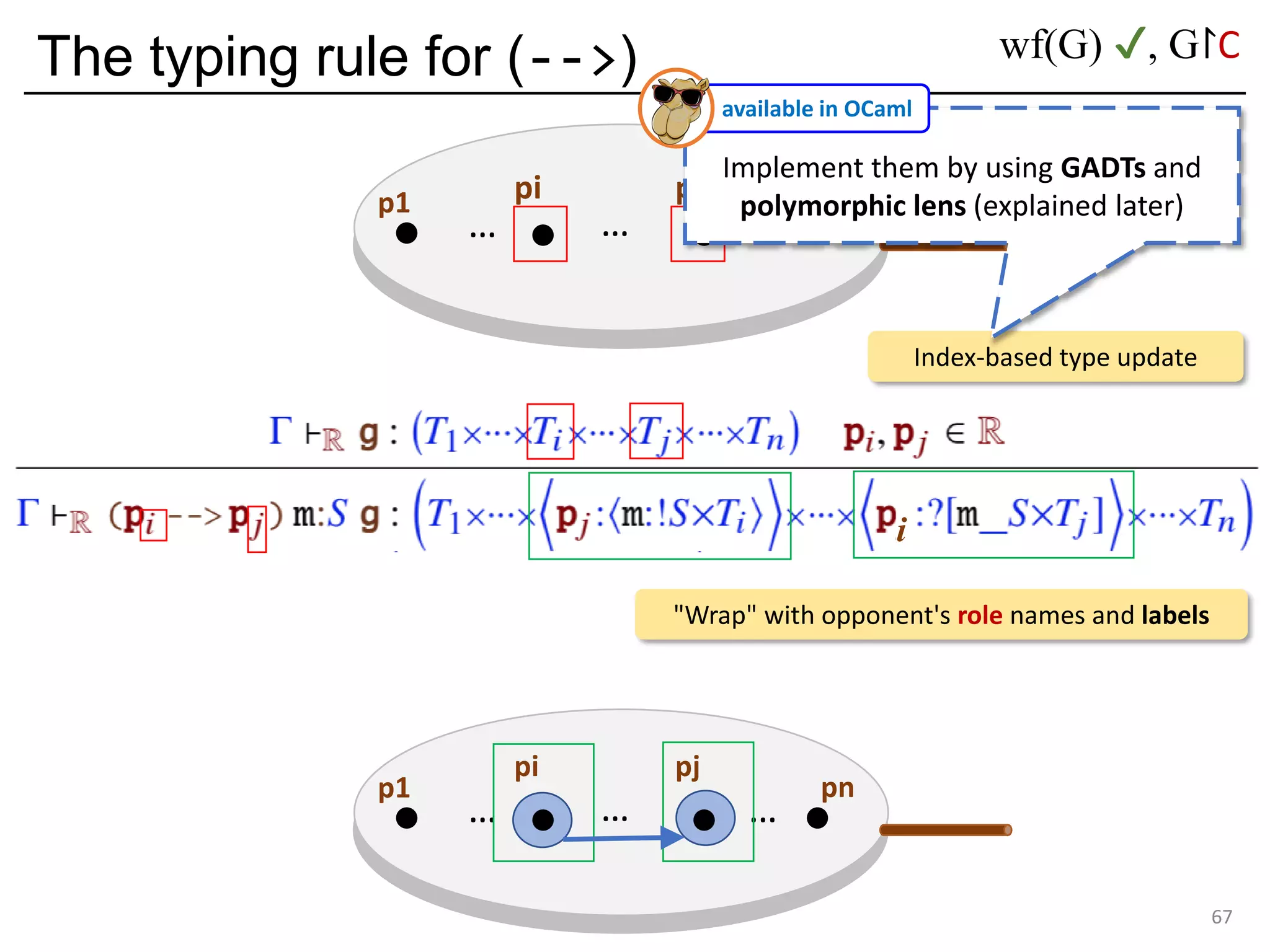
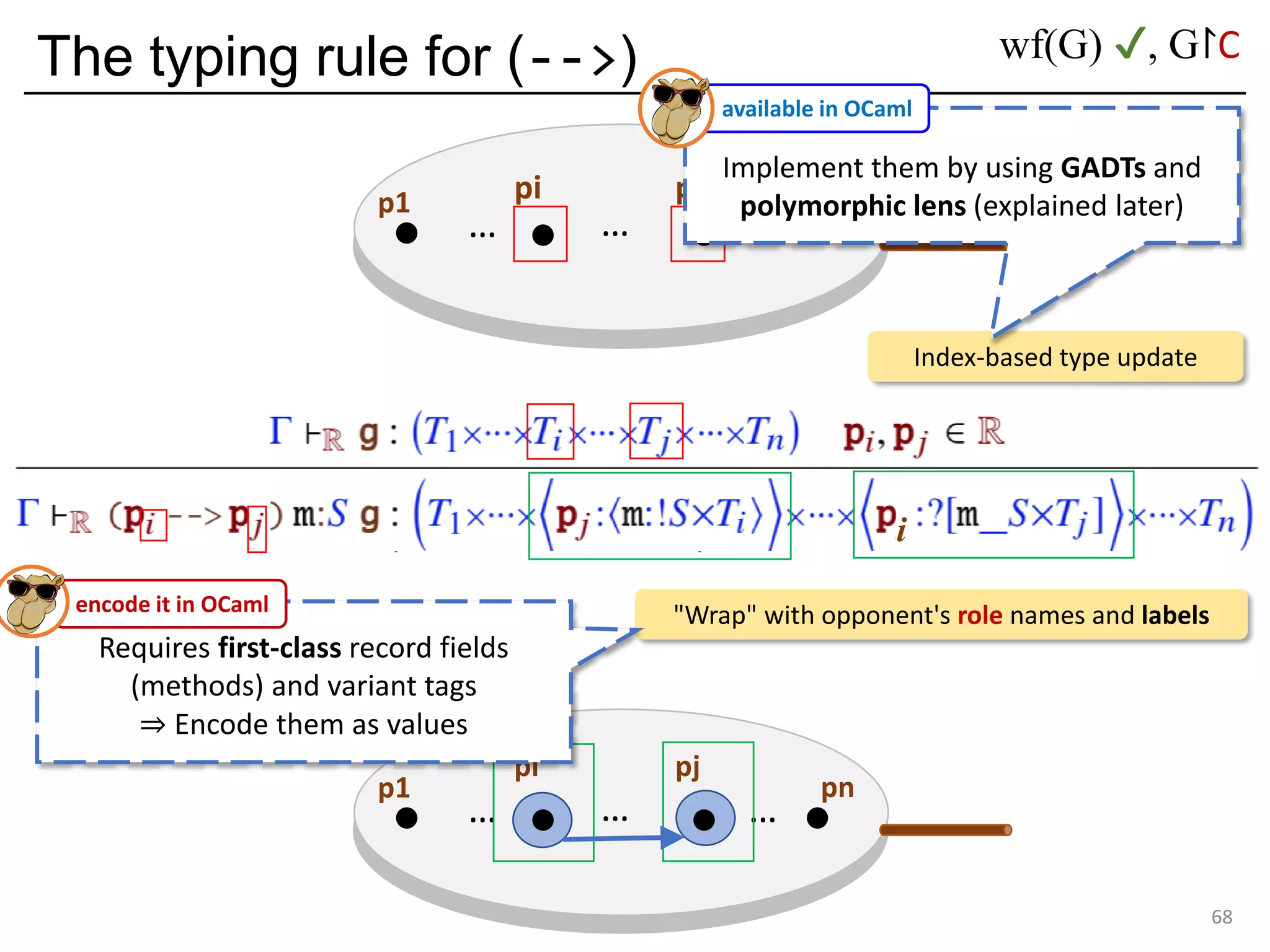

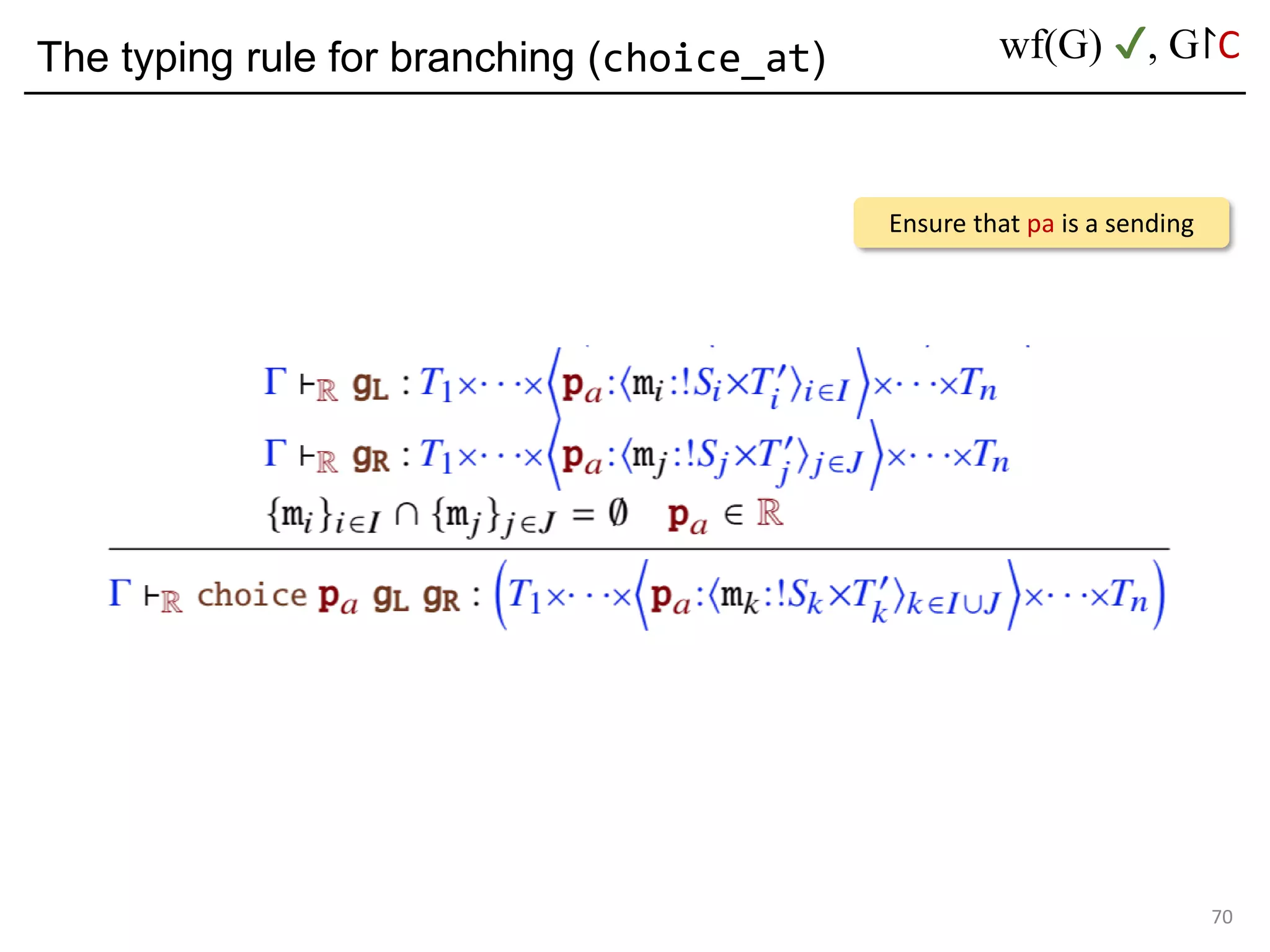
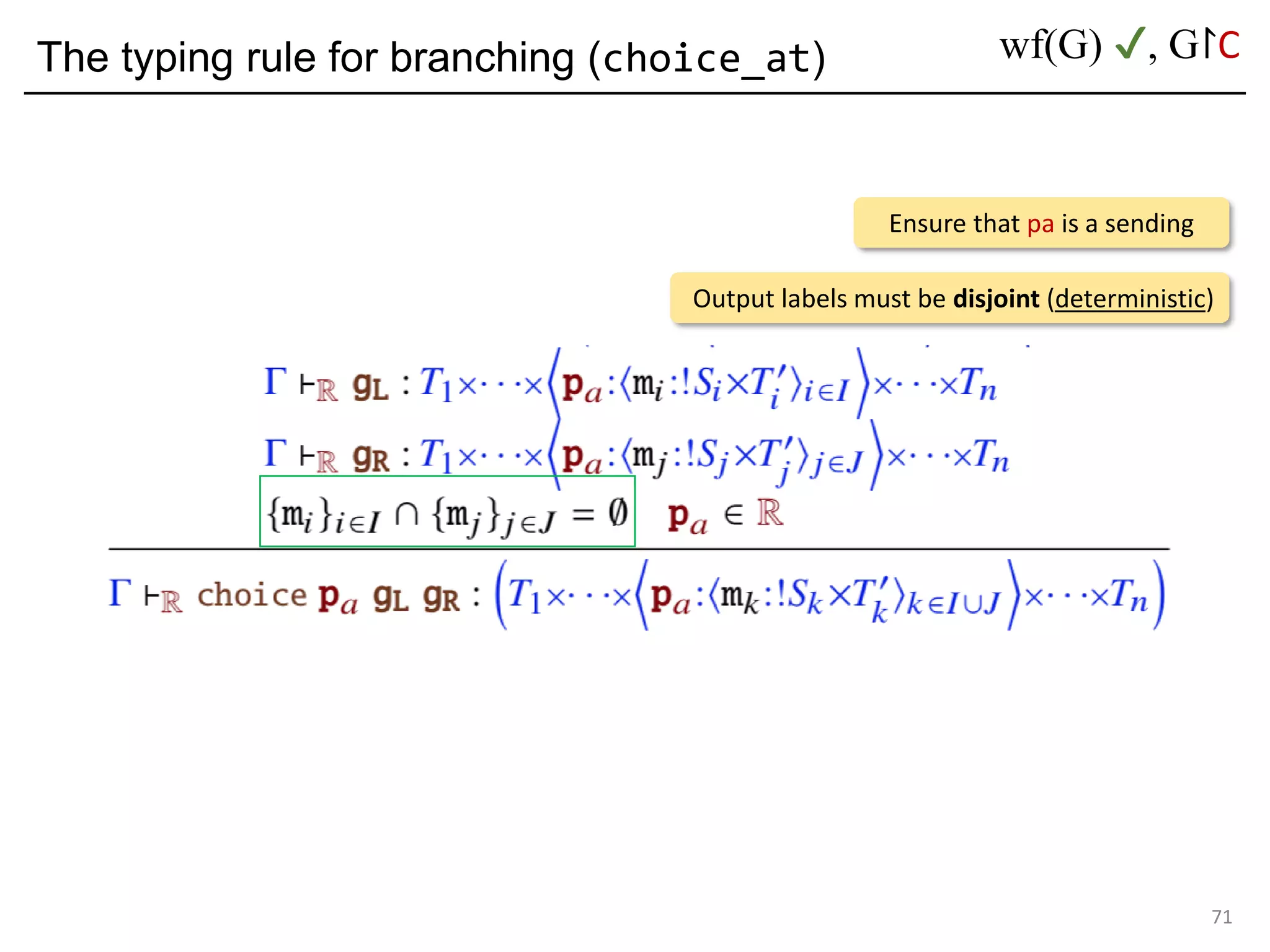
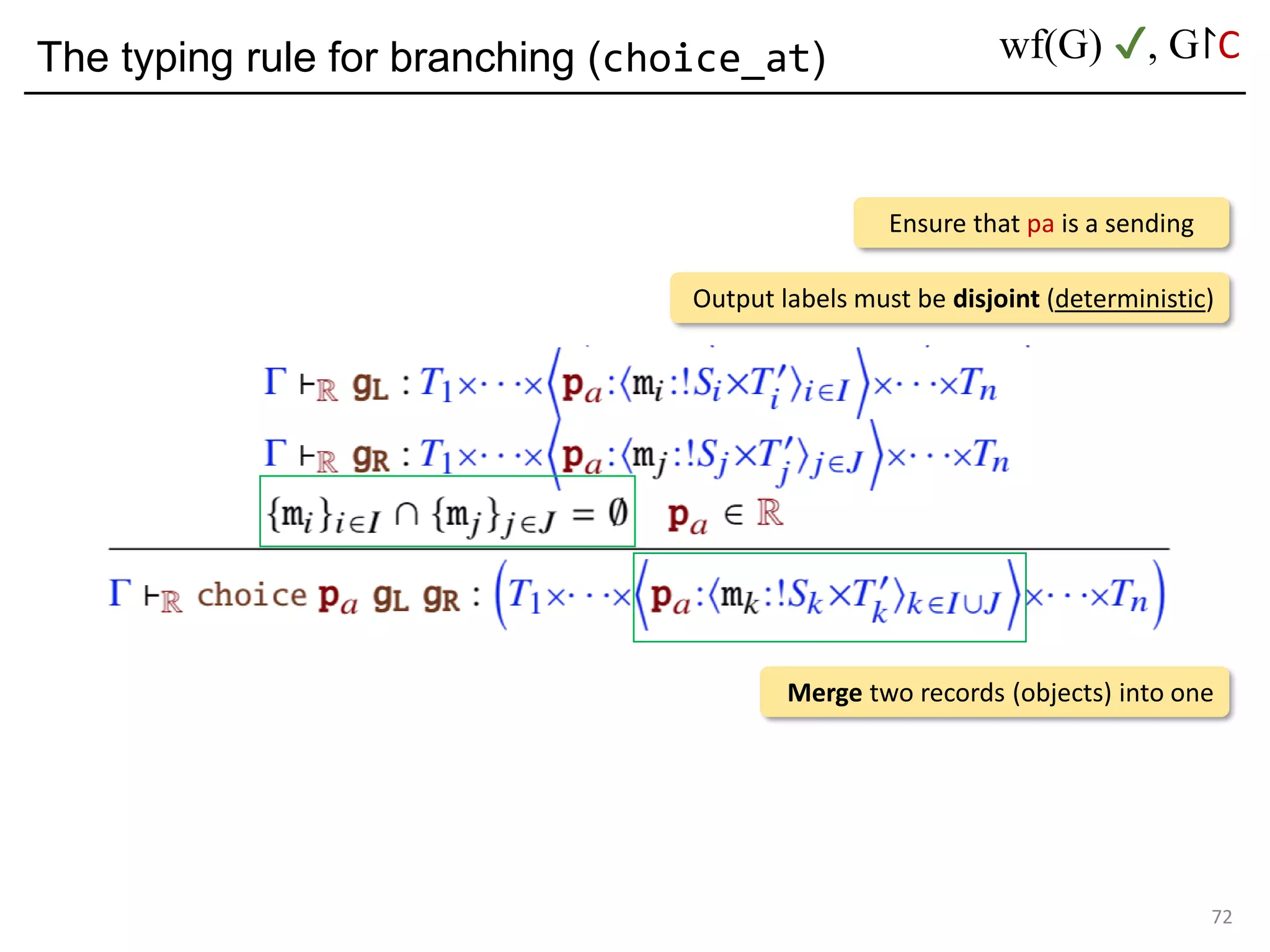
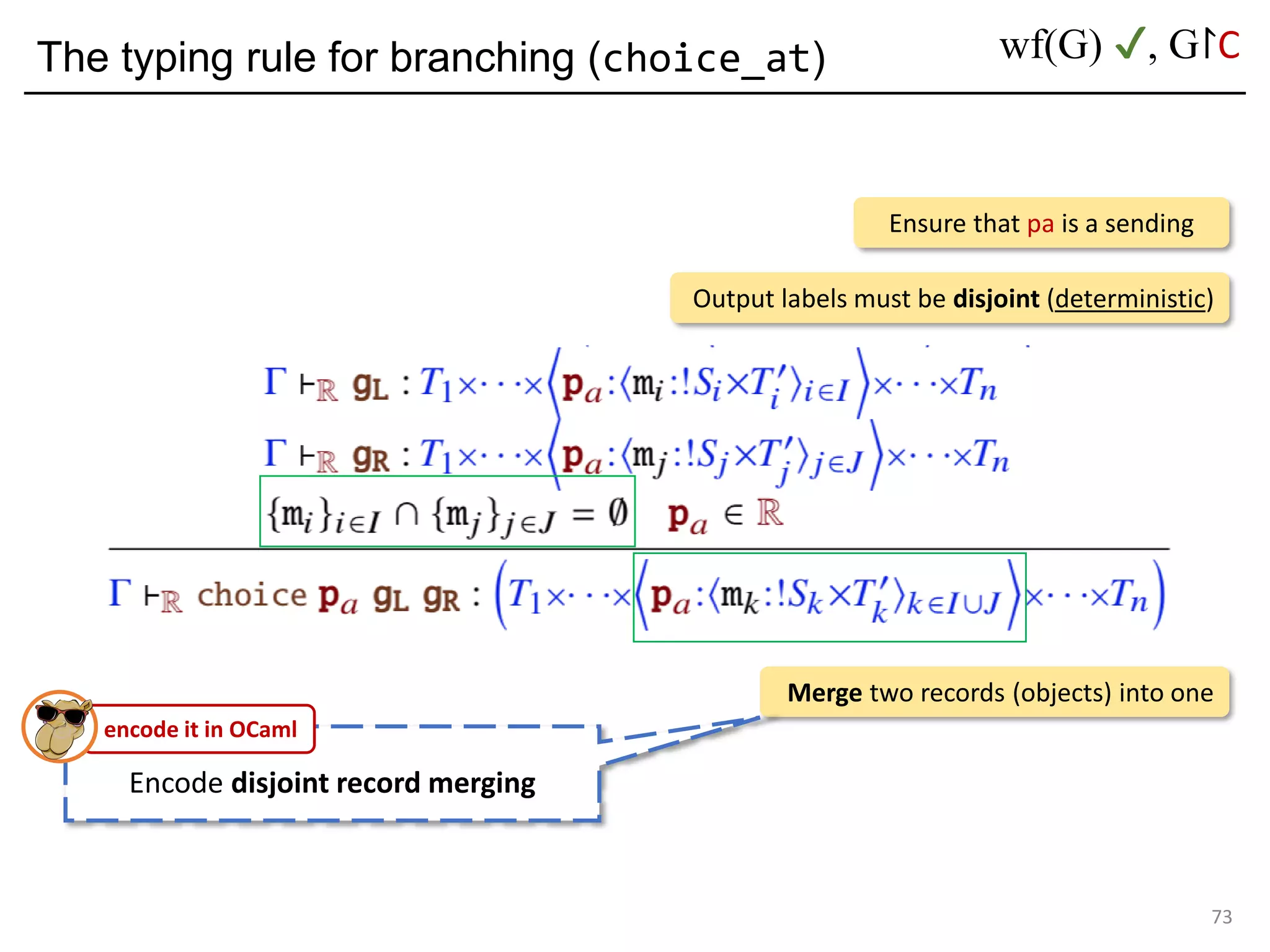
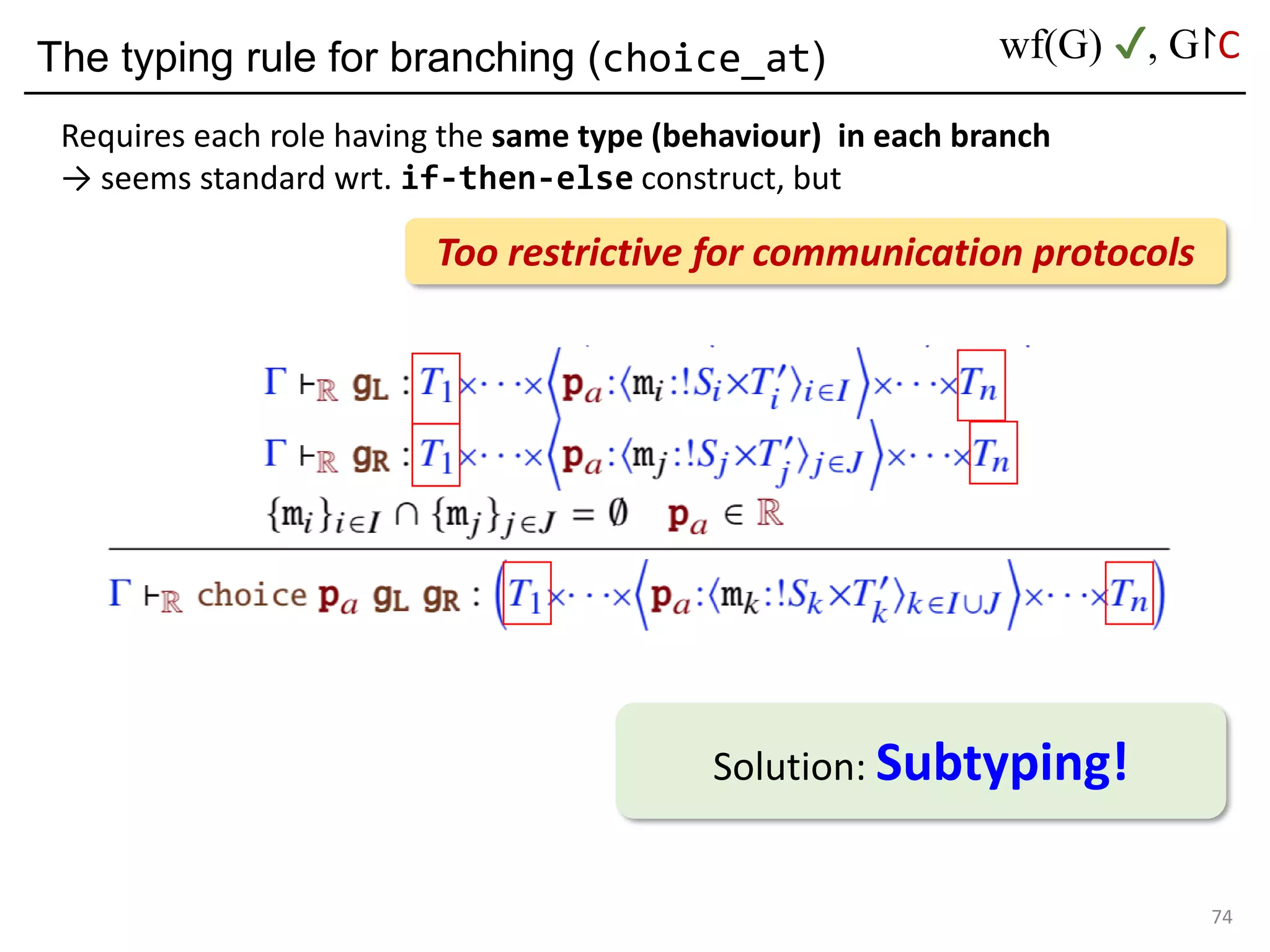
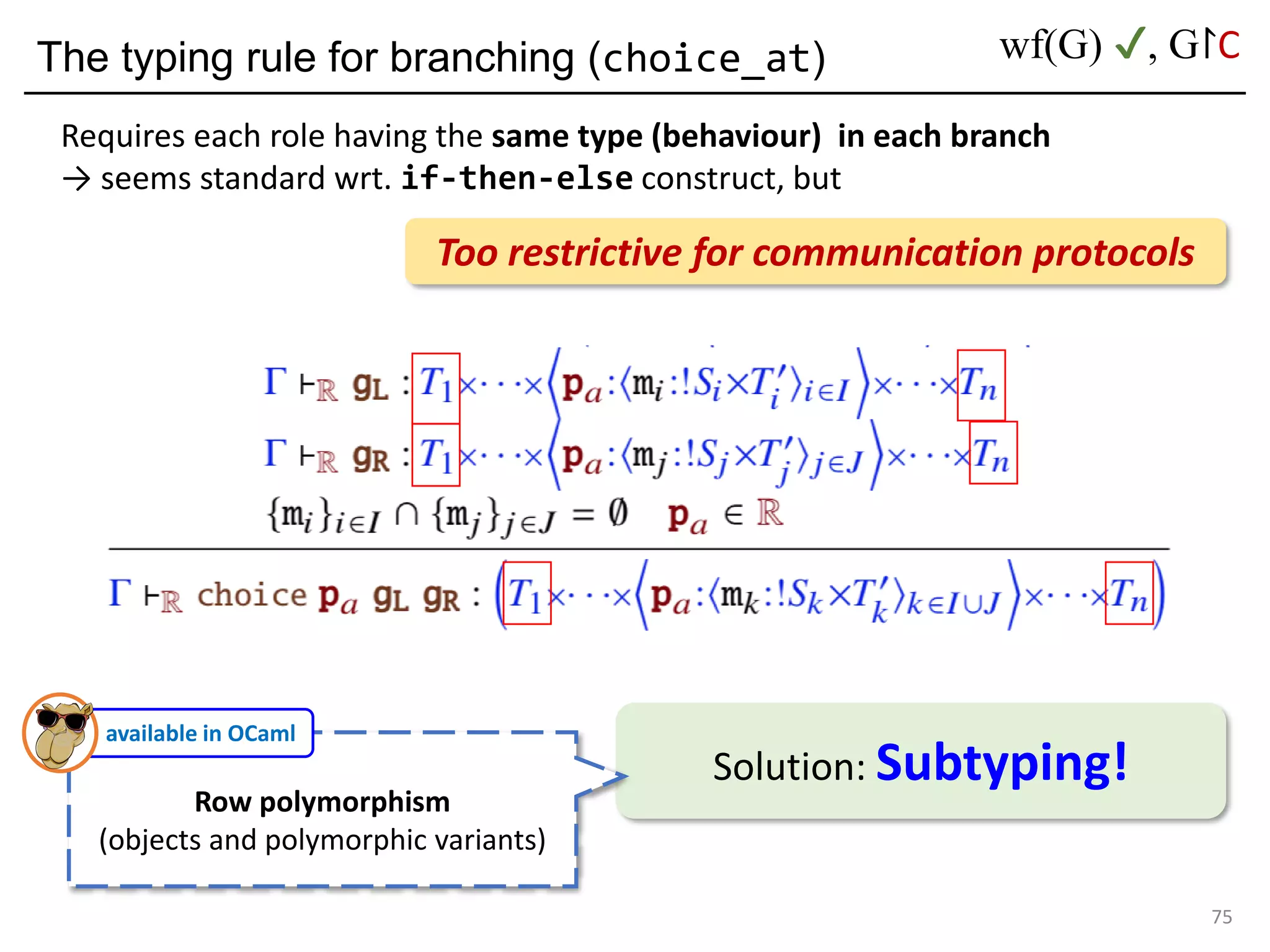
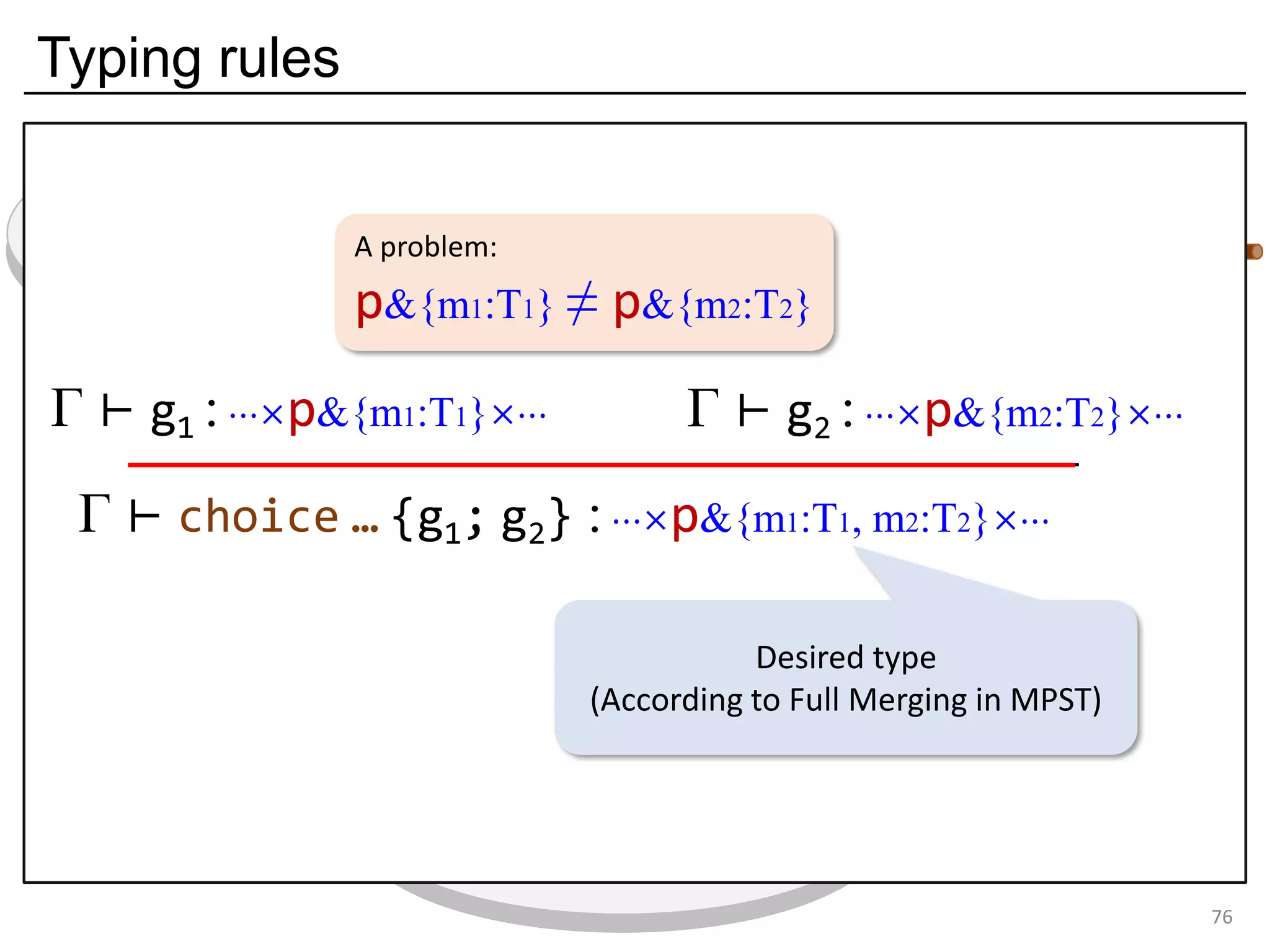
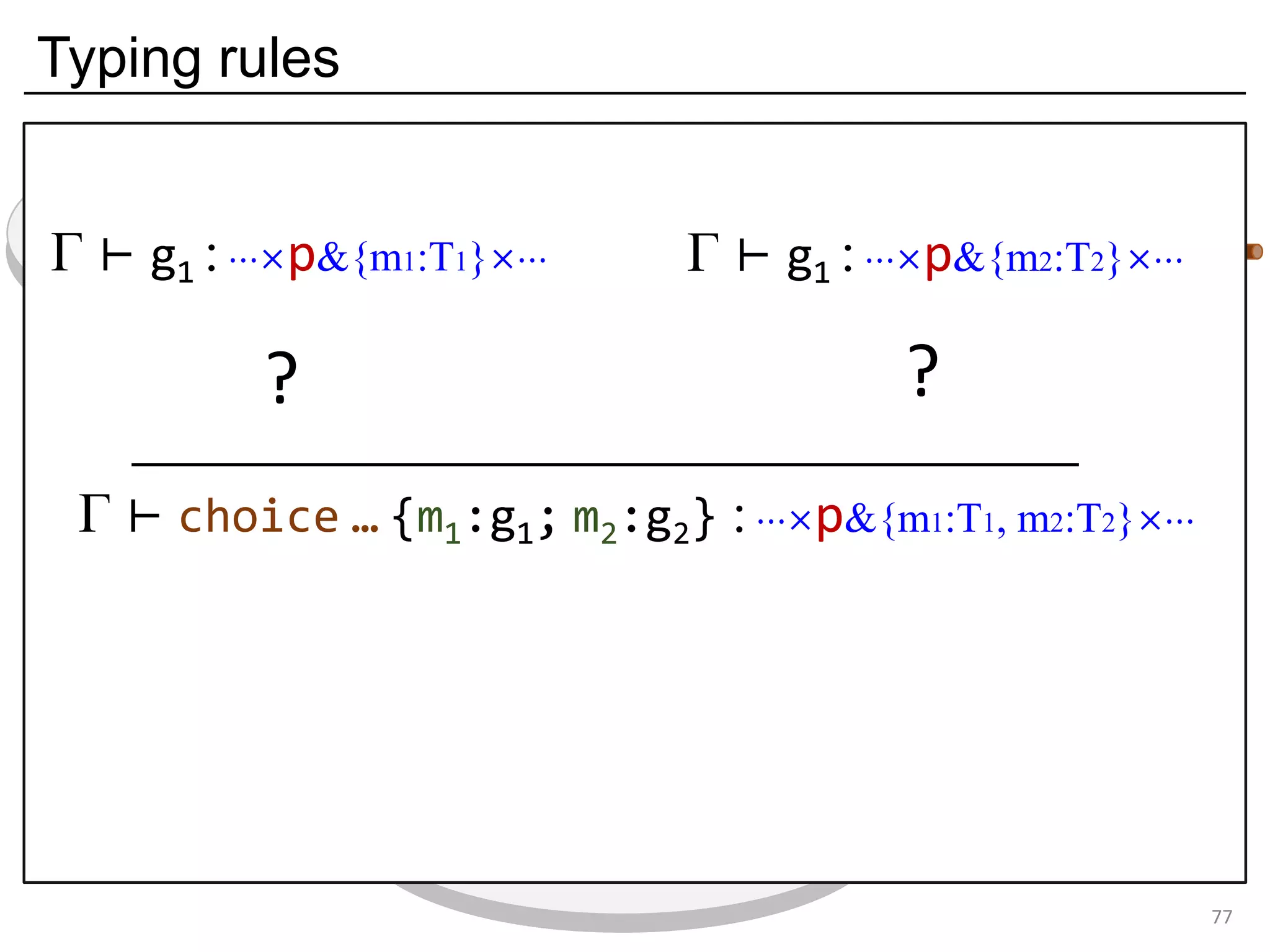
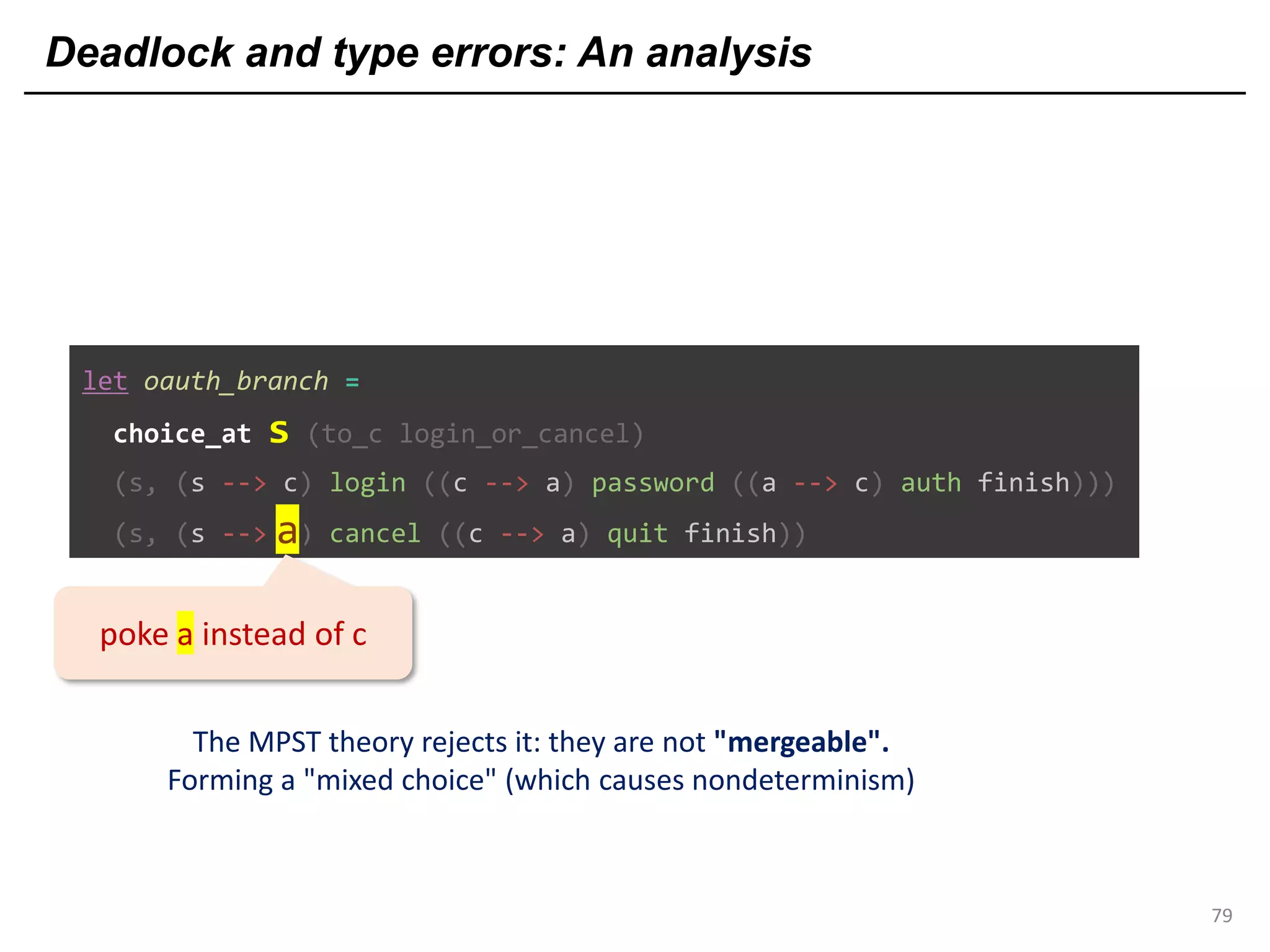
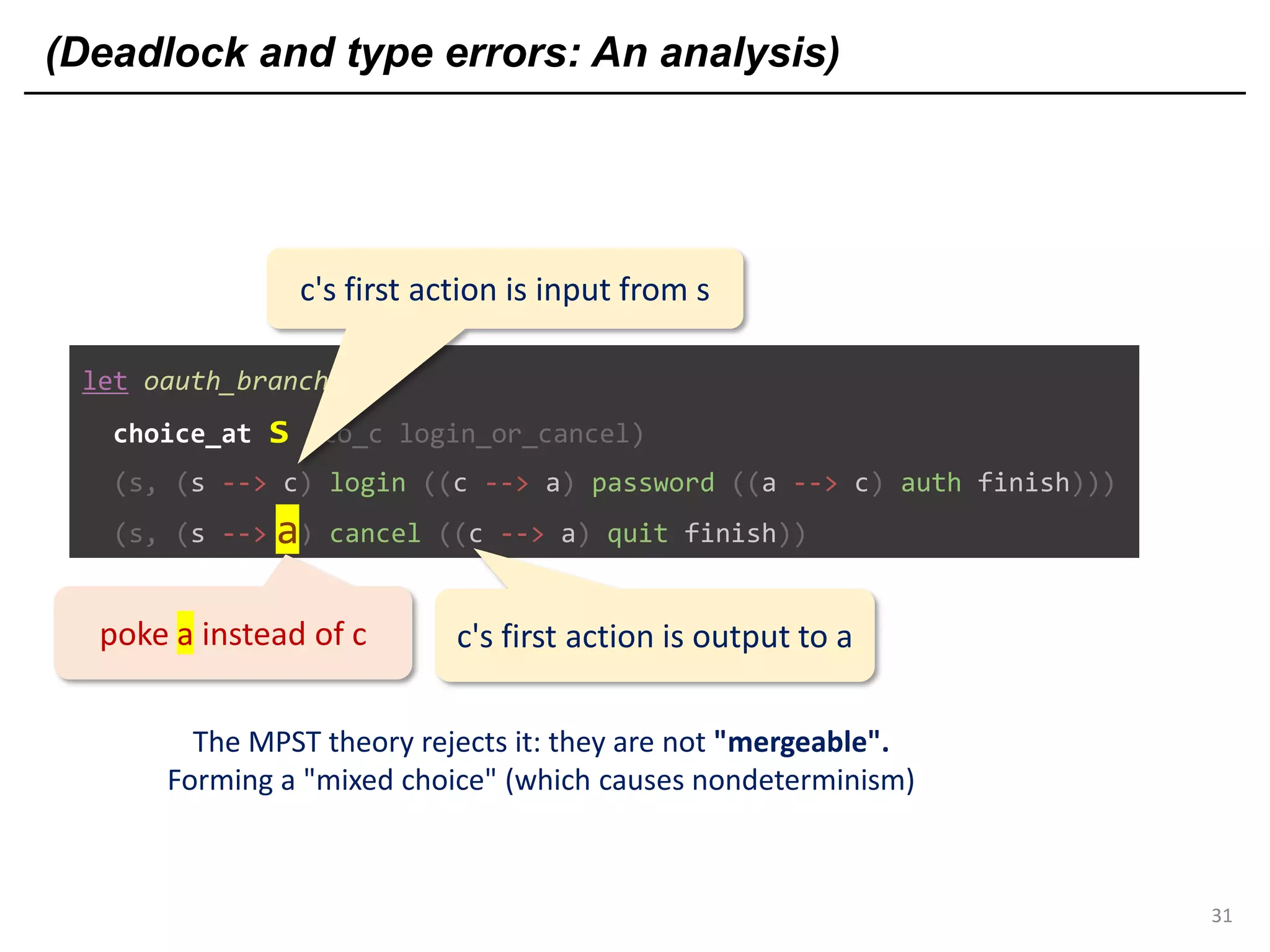
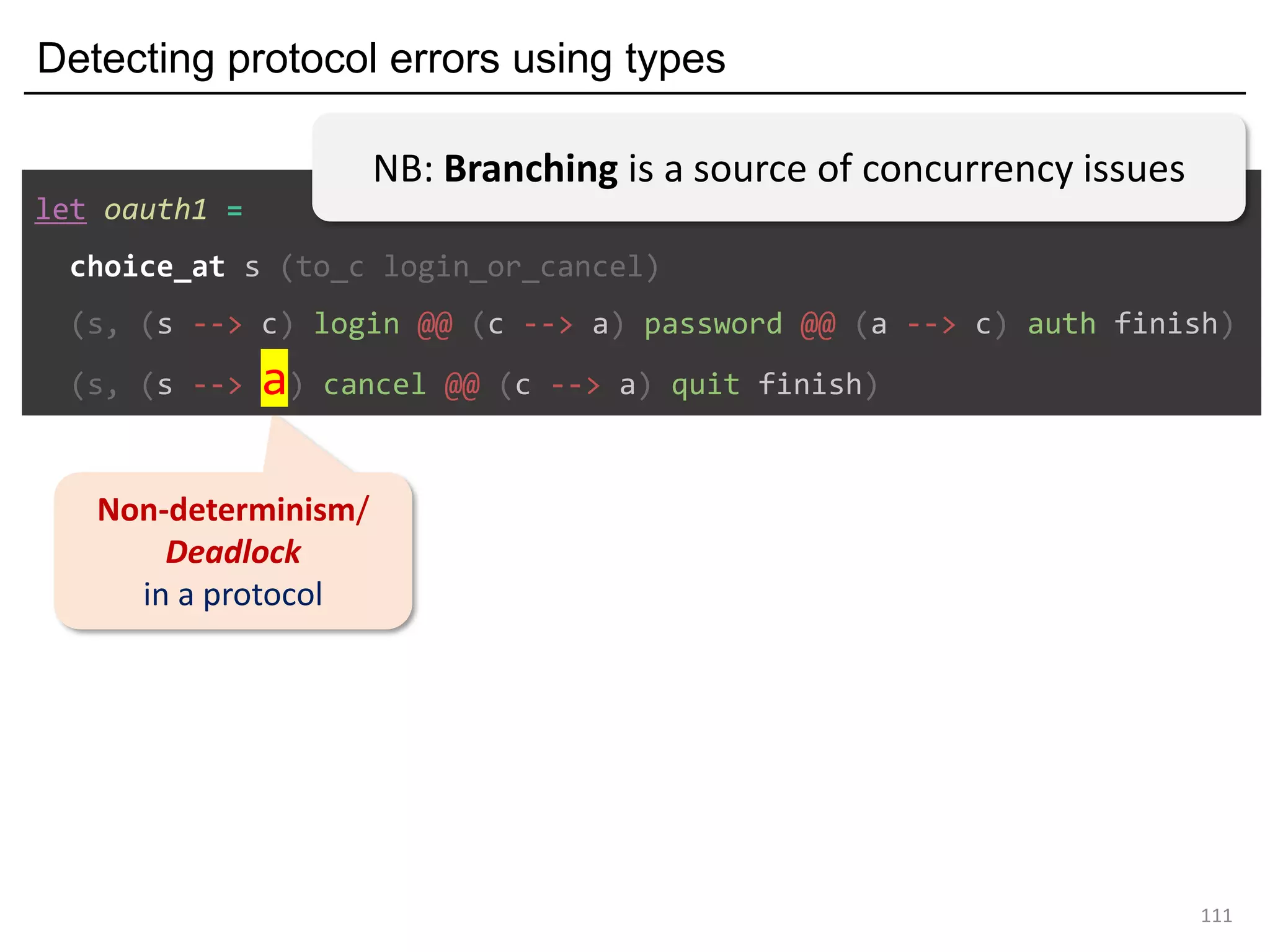
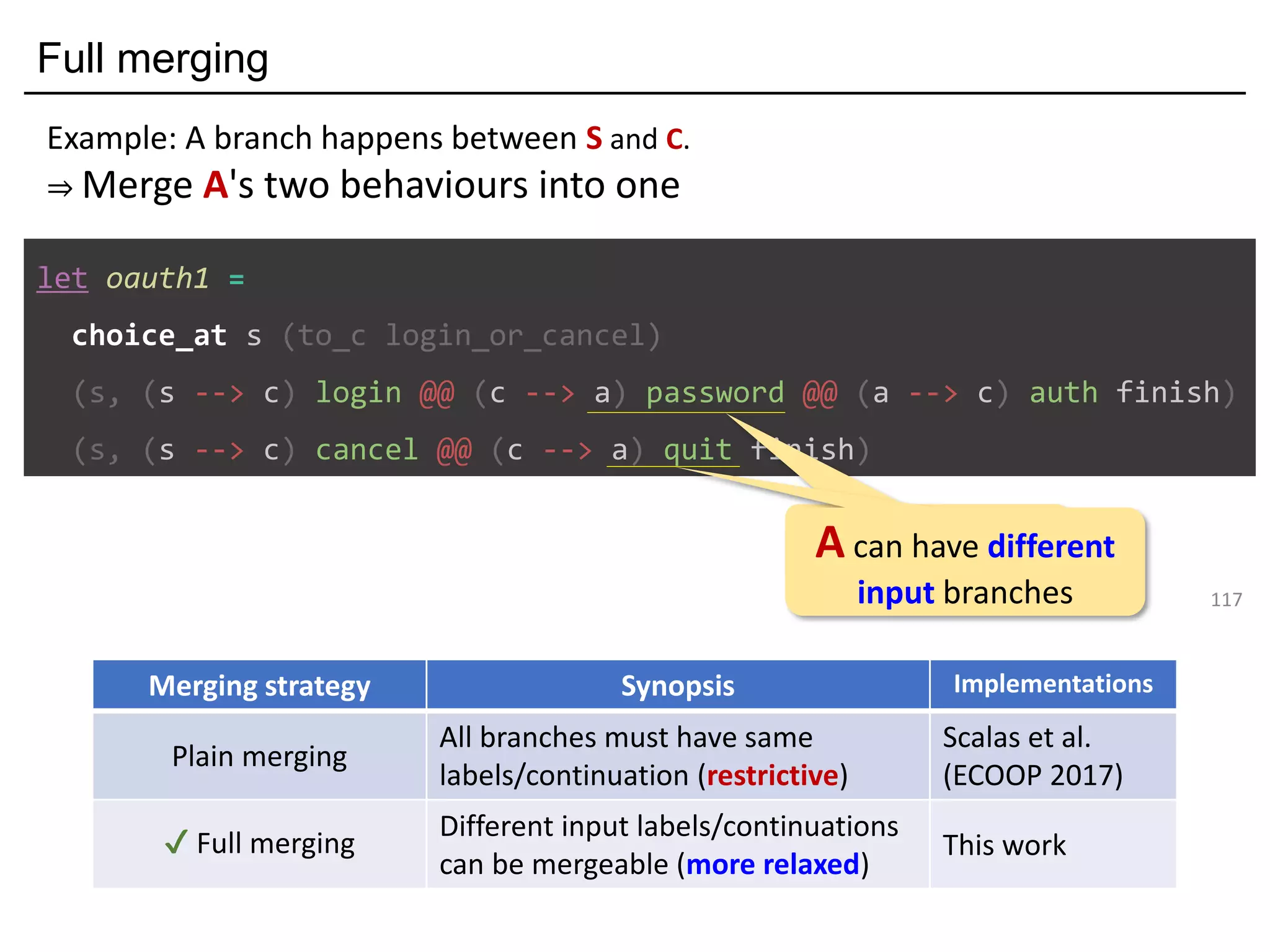
![Deadlock and type errors: An analysis
81
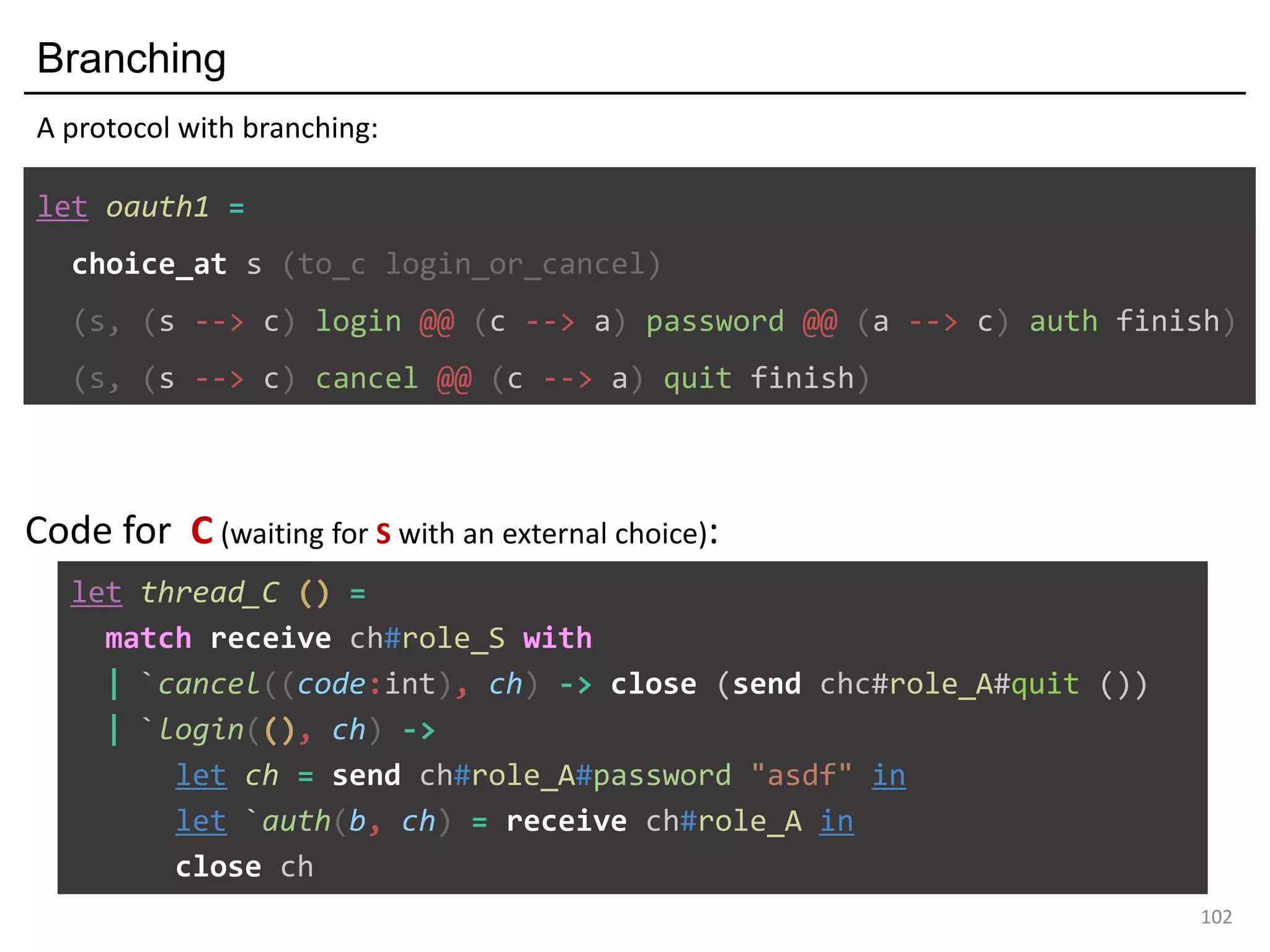
let oauth_branch =
choice_at s (to_c login_or_cancel)
(s, (s --> c) login ((c --> a) password ((a --> c) auth finish)))
(s, (s --> c) cancel ((c --> a) quit finish))a
poke a instead of c
The MPST theory rejects it: they are not "mergeable".
Forming a "mixed choice" (which causes nondeterminism)
c's first action is input from s <s: ?[login_str*cont1]>
c's first action is output to a <a: <quit: !bool*cont2>>](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-81-2048.jpg)
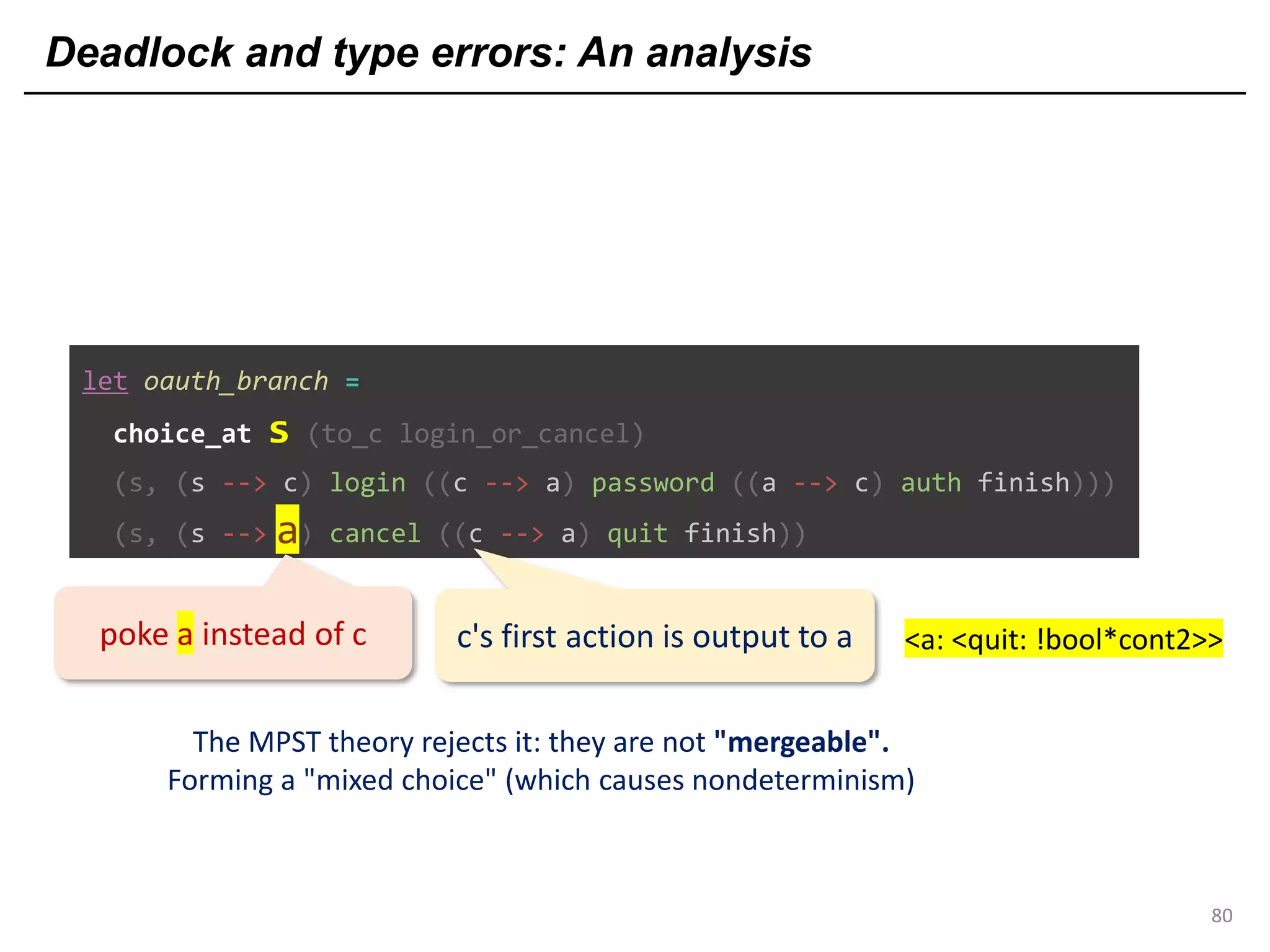
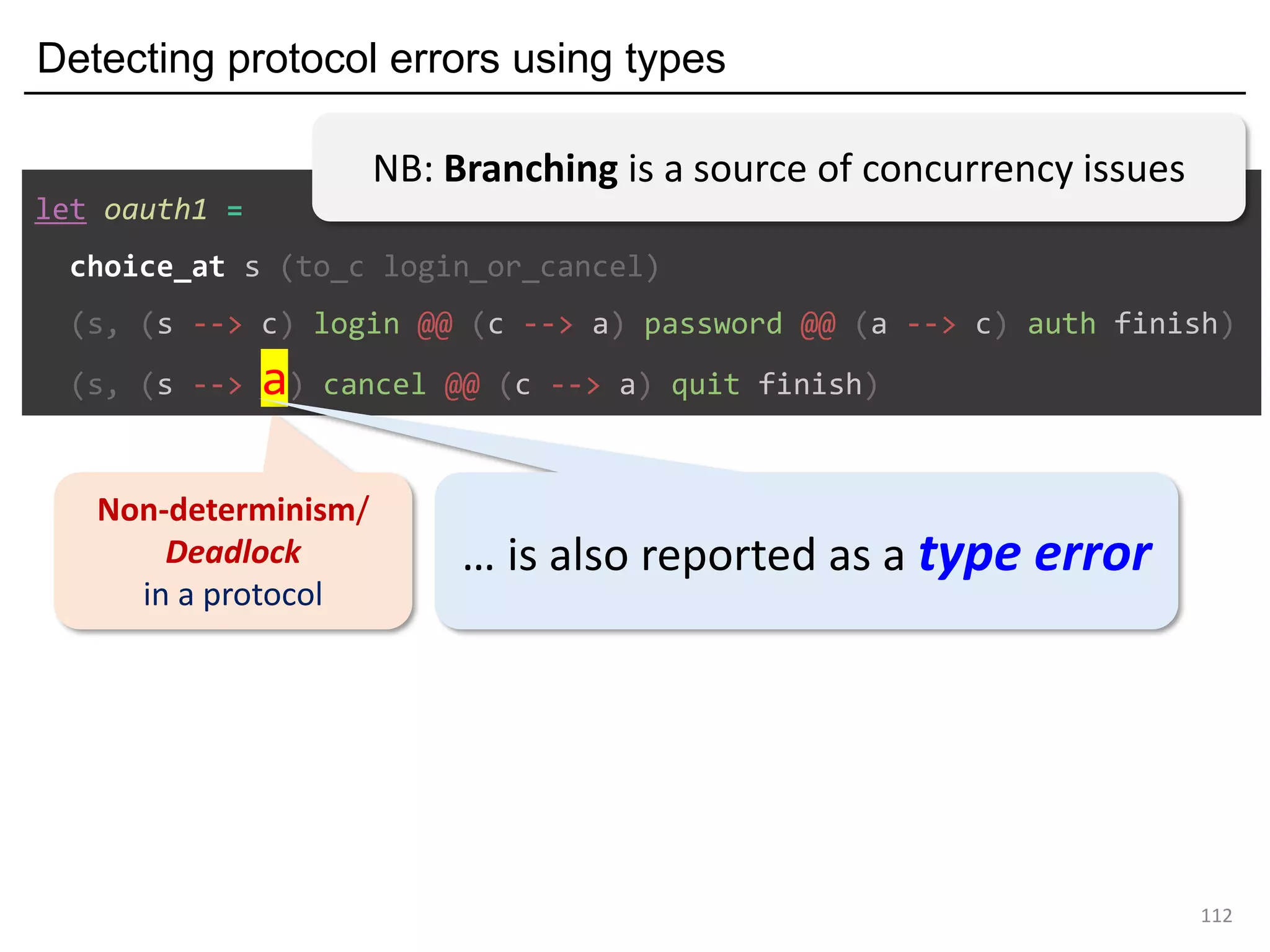
![Deadlock and type errors: An analysis
82
let oauth_branch =
choice_at s (to_c login_or_cancel)
(s, (s --> c) login ((c --> a) password ((a --> c) auth finish)))
(s, (s --> c) cancel ((c --> a) quit finish))a
poke a instead of c
The MPST theory rejects it: they are not "mergeable".
Forming a "mixed choice" (which causes nondeterminism)
c's first action is input from s <s: ?[login_str*cont1]>
c's first action is output to a <a: <quit: !bool*cont2>>
No least upper bound (common supertype)
⇒ type error
No least upper bound (common supertype)
⇒ type error](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-82-2048.jpg)
![A note on typing
83
<r: ?[lab: T1*T2]>
<r: <lab: !T1*T2>>
Input and output session types are not symmetric with each other. Why?
sok : ?bool, scancel : ?int
: ?[ok_(boolו); cancel_(int× …)] (← wanted)
Making a multiplexed channel from
simply-typed channels](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-83-2048.jpg)
![A note on typing
84
<r: ?[lab: T1*T2]>
<r: <lab: !T1*T2>>
Input and output session types are not symmetric with each other. Why?
sok : ?bool, scancel : ?int
: ?[ok_(boolו); cancel_(int× …)] (← wanted)
choose : List[?T] -> ?T
makes a (multiplexed) channel (external choice)
wrap : (α -> β) -> ?α -> ?β
makes a wrapped channel
Concurrent ML (Reppy, 1993)
Types are slightly modified, they uses "events" in reality
Making a multiplexed channel from
simply-typed channels](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-84-2048.jpg)
![A note on typing
85
<r: ?[lab: T1*T2]>
<r: <lab: !T1*T2>>
Input and output session types are not symmetric with each other. Why?
sok : ?bool, scancel : ?int
wrap (λx.[ok=(x,•)]) sok
: ?[ok_(boolו)]
wrap (λx.[cancel=(x,…)]) scancel
: ?[cancel_(int×…)]
: ?[ok_(boolו); cancel_(int× …)] (← wanted)
choose : List[?T] -> ?T
makes a (multiplexed) channel (external choice)
wrap : (α -> β) -> ?α -> ?β
makes a wrapped channel
Concurrent ML (Reppy, 1993)
Types are slightly modified, they uses "events" in reality
Making a multiplexed channel from
simply-typed channels](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-85-2048.jpg)
![A note on typing
86
<r: ?[lab: T1*T2]>
<r: <lab: !T1*T2>>
Input and output session types are not symmetric with each other. Why?
sok : ?bool, scancel : ?int
wrap (λx.[ok=(x,•)]) sok
: ?[ok_(boolו)]
wrap (λx.[cancel=(x,…)]) scancel
: ?[cancel_(int×…)]
List(wrap (λx.[ok=(x,•)]) sok; wrap (λx.[cancel=(x,…)]) scancel)
: List[ ?[ok_(boolו), cancel_(intׅ)] ]
: ?[ok_(boolו); cancel_(int× …)] (← wanted)
choose : List[?T] -> ?T
makes a (multiplexed) channel (external choice)
wrap : (α -> β) -> ?α -> ?β
makes a wrapped channel
Concurrent ML (Reppy, 1993)
Types are slightly modified, they uses "events" in reality
Making a multiplexed channel from
simply-typed channels](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-86-2048.jpg)
![A note on typing
87
<r: ?[lab: T1*T2]>
<r: <lab: !T1*T2>>
Input and output session types are not symmetric with each other. Why?
sok : ?bool, scancel : ?int
wrap (λx.[ok=(x,•)]) sok
: ?[ok_(boolו)]
wrap (λx.[cancel=(x,…)]) scancel
: ?[cancel_(int×…)]
List(wrap (λx.[ok=(x,•)]) sok; wrap (λx.[cancel=(x,…)]) scancel)
: List[ ?[ok_(boolו), cancel_(intׅ)] ]
choose (List(wrap (λx.[ok=(x,•)]) sok; wrap (λx.[cancel=(x,…)]) scancel))
: ?[ok_(boolו); cancel_(int× …)] (← wanted)
choose : List[?T] -> ?T
makes a (multiplexed) channel (external choice)
wrap : (α -> β) -> ?α -> ?β
makes a wrapped channel
Concurrent ML (Reppy, 1993)
Types are slightly modified, they uses "events" in reality
Making a multiplexed channel from
simply-typed channels](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-87-2048.jpg)



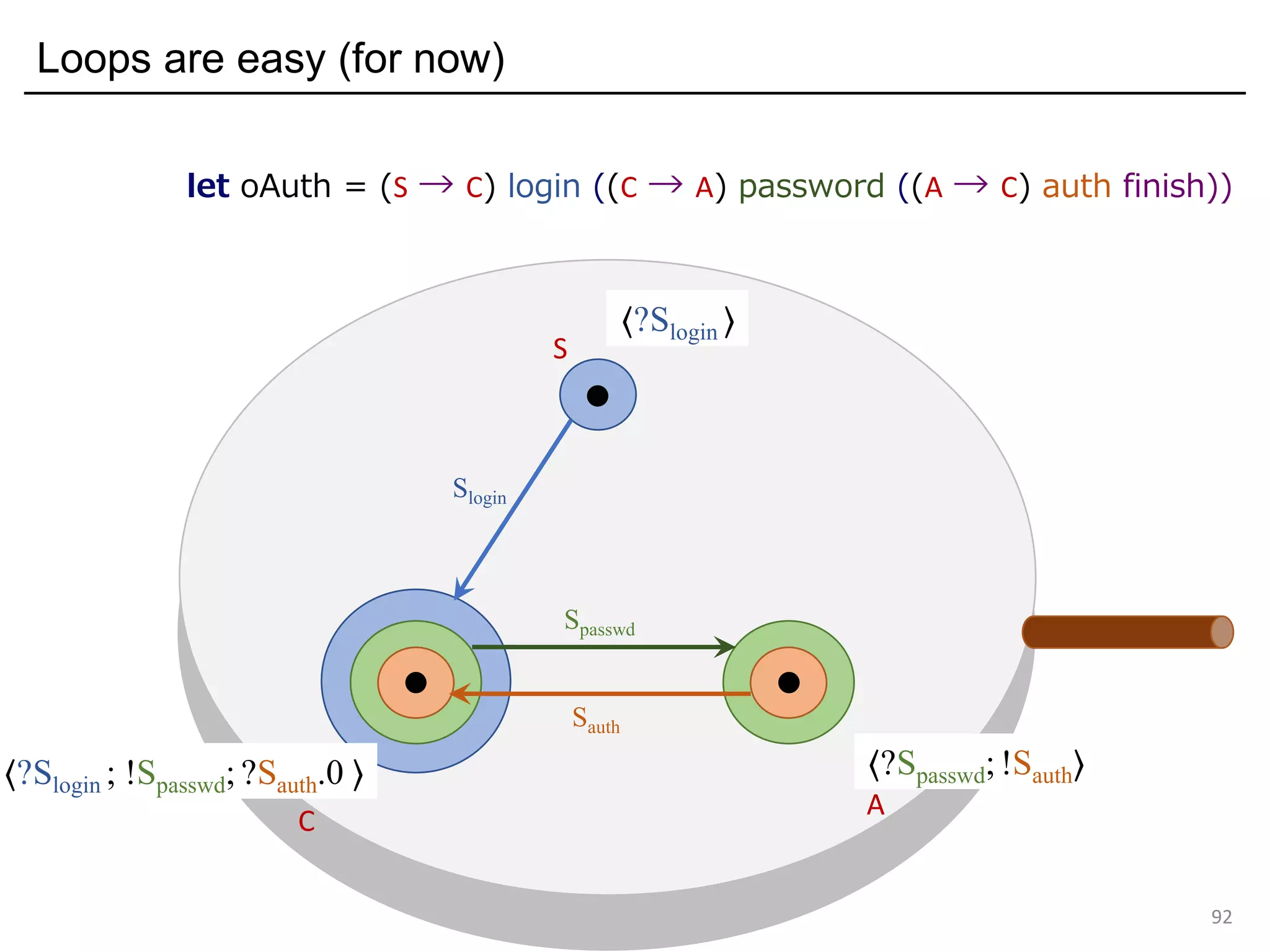
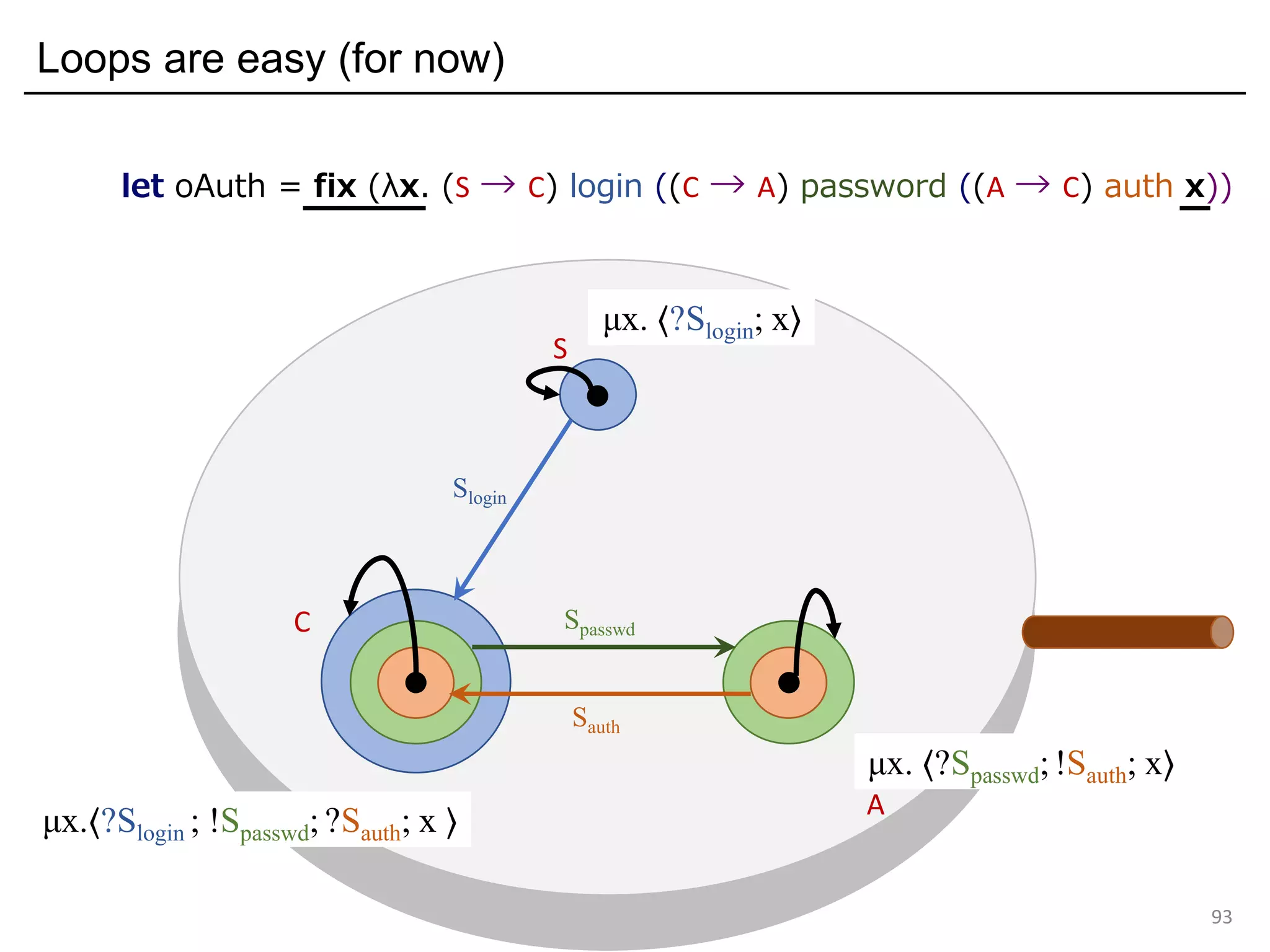
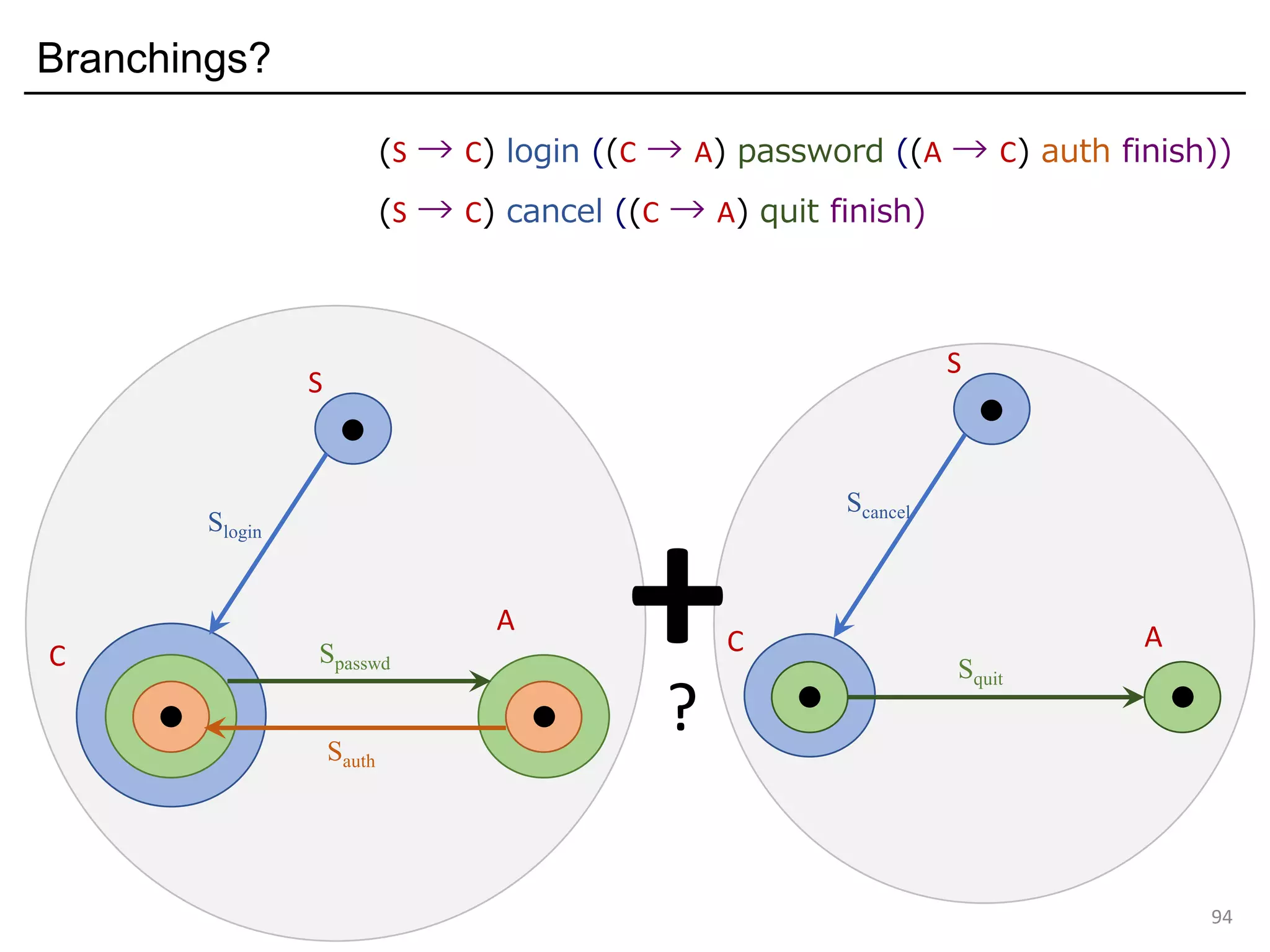
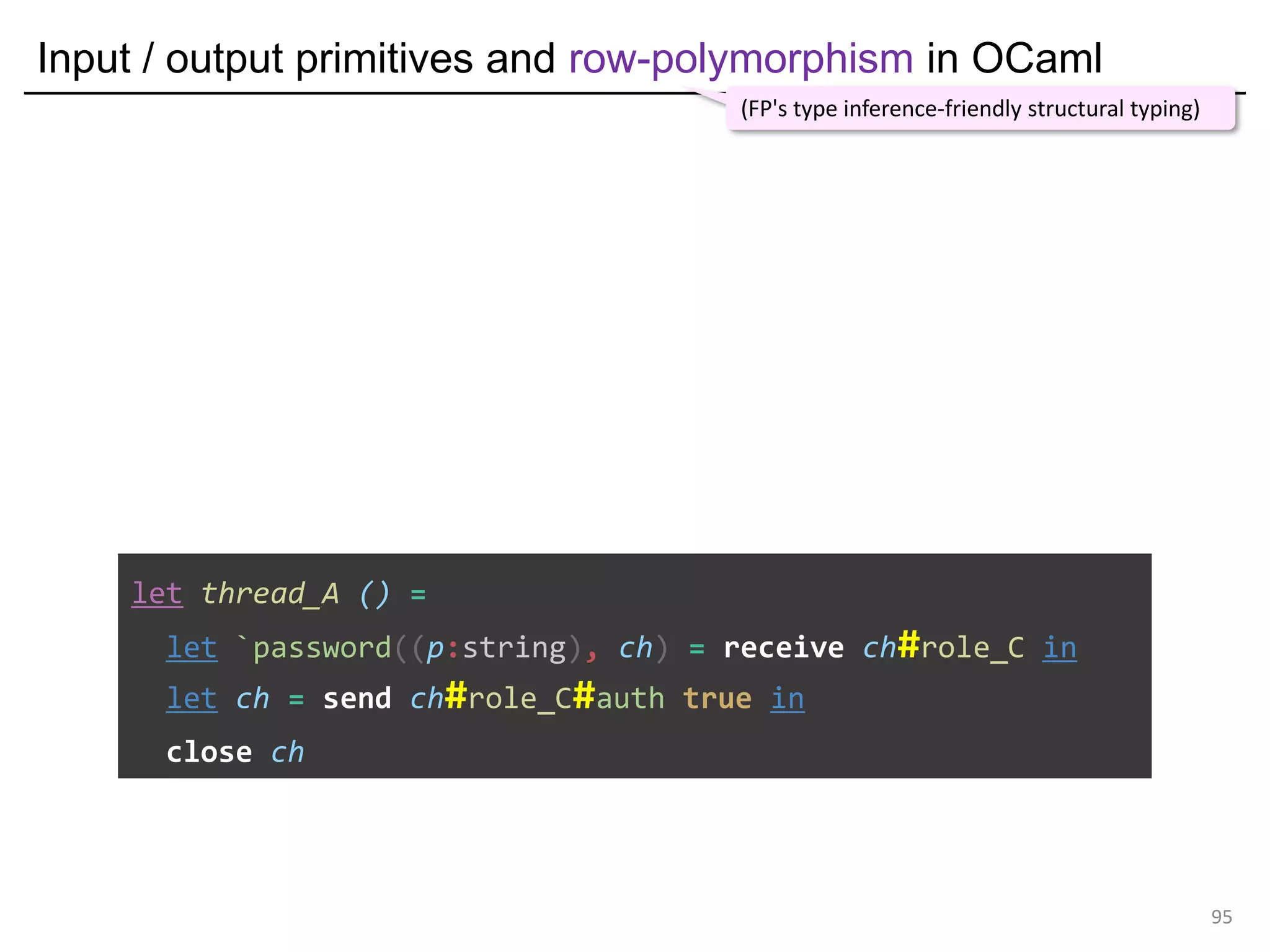
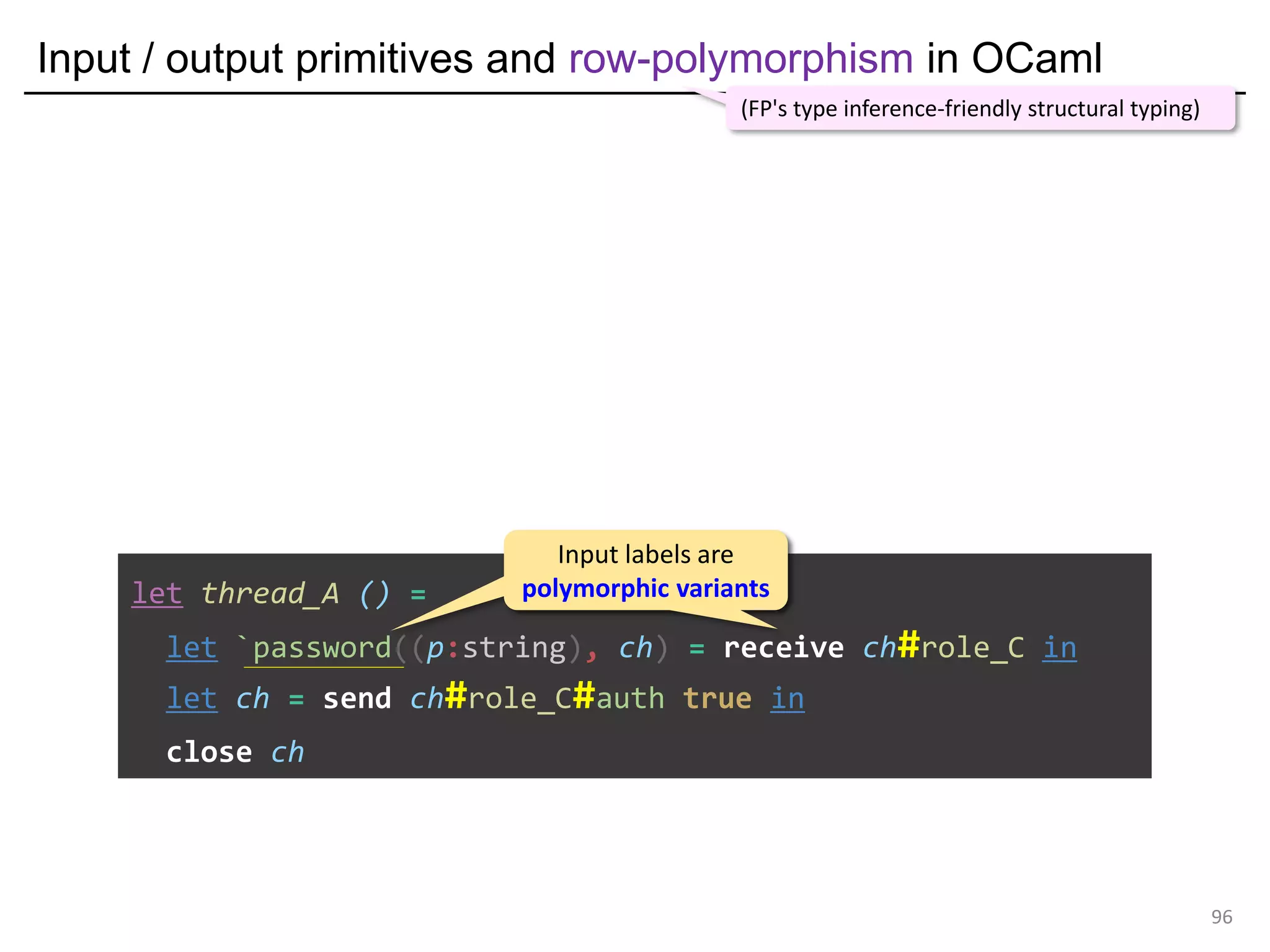
![Input / output primitives and row-polymorphism in OCaml
99
let thread_A () =
let `password((p:string), ch) = receive ch#role_C in
let ch = send ch#role_C#auth true in
close ch
OCaml's row-polymorphism simulates session-type subtyping
(FP's type inference-friendly structural typing)
Input labels are
polymorphic variants
Input labels are
polymorphic variants
Output labels are methods in
an object (fields in a polymorphic record)
Output labels are methods in
an object (fields in a polymorphic record)
val ch :
< role_C : [< `password of
string *
< role_C : < auth : (bool * close) out lin; .. >; .. >
] inp lin; .. >
-> unit](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-99-2048.jpg)
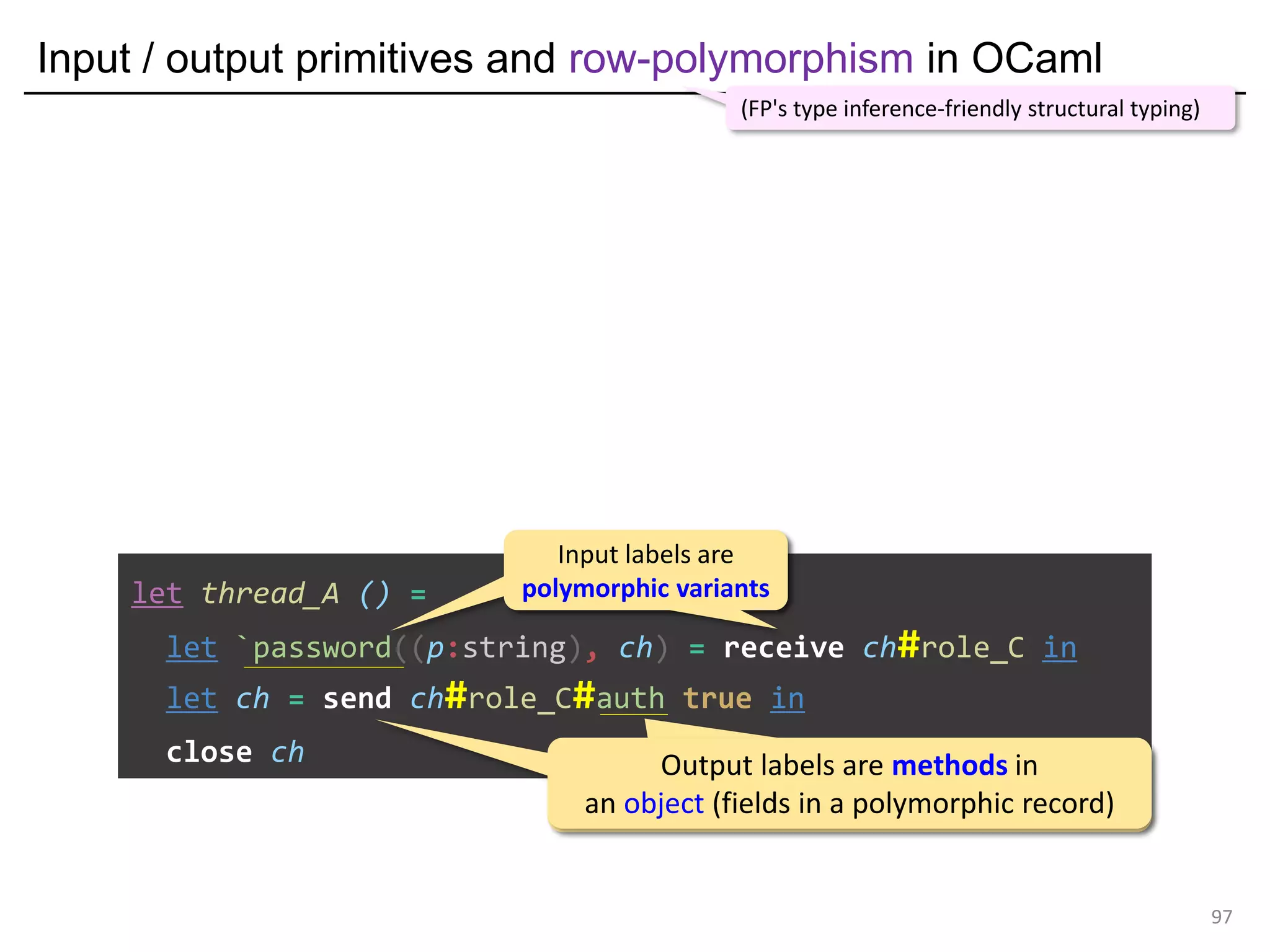
![Input / output primitives and row-polymorphism in OCaml
100
let thread_A () =
let `password((p:string), ch) = receive ch#role_C in
let ch = send ch#role_C#auth true in
close ch
OCaml's row-polymorphism simulates session-type subtyping
(FP's type inference-friendly structural typing)
Input labels are
polymorphic variants
Input labels are
polymorphic variants
Output labels are methods in
an object (fields in a polymorphic record)
Output labels are methods in
an object (fields in a polymorphic record)
val ch :
< role_C : [< `password of
string *
< role_C : < auth : (bool * close) out lin; .. >; .. >
] inp lin; .. >
-> unit
Inferred polymorphic variant type: it can have less receiving labels
(= in this case it must have password at least since there must be one)](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-100-2048.jpg)
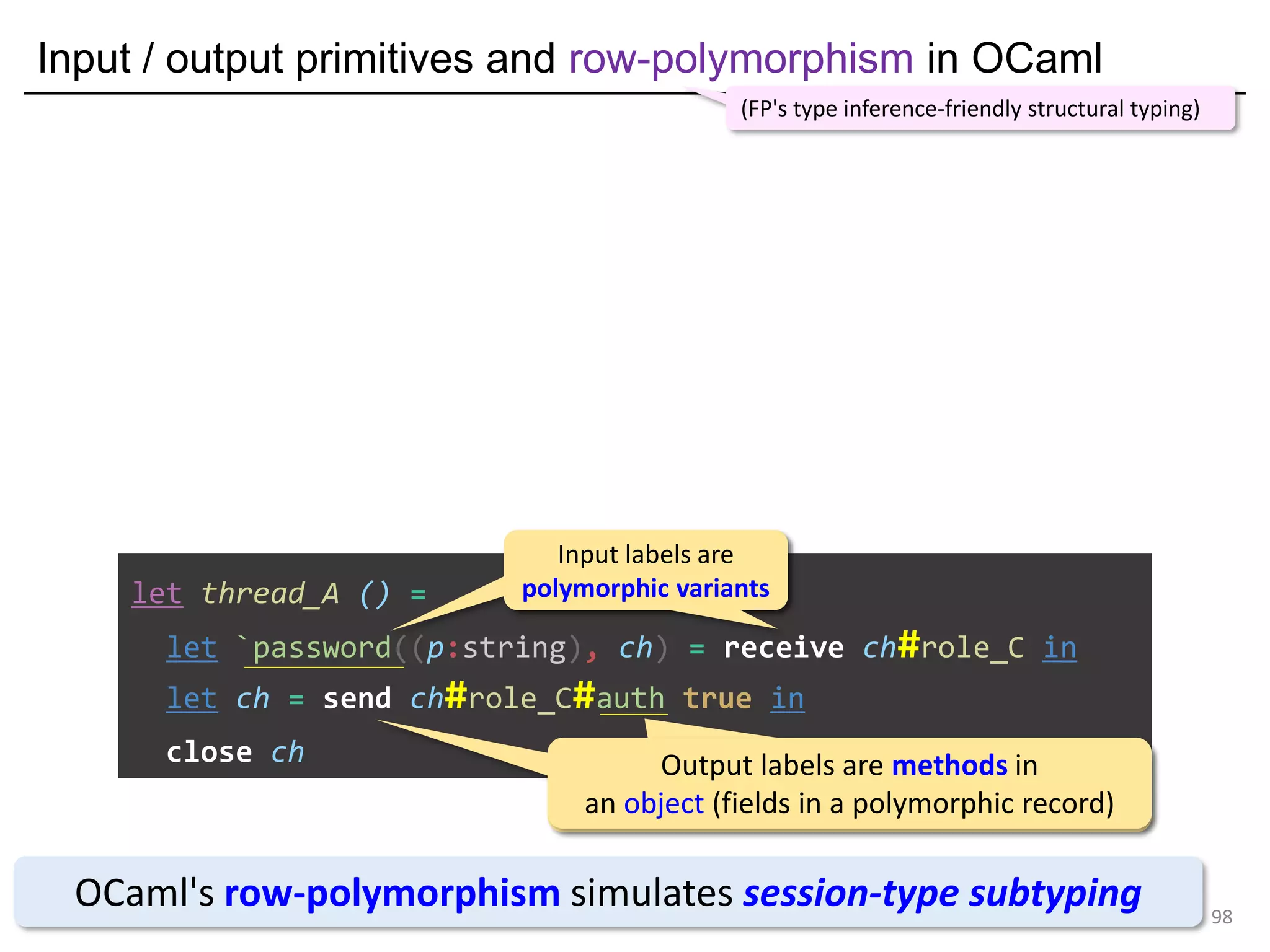
![Input / output primitives and row-polymorphism in OCaml
101
let thread_A () =
let `password((p:string), ch) = receive ch#role_C in
let ch = send ch#role_C#auth true in
close ch
OCaml's row-polymorphism simulates session-type subtyping
(FP's type inference-friendly structural typing)
Input labels are
polymorphic variants
Input labels are
polymorphic variants
Output labels are methods in
an object (fields in a polymorphic record)
Output labels are methods in
an object (fields in a polymorphic record)
val ch :
< role_C : [< `password of
string *
< role_C : < auth : (bool * close) out lin; .. >; .. >
] inp lin; .. >
-> unit
Inferred polymorphic variant type: it can have less receiving labels
(= in this case it must have password at least since there must be one)
Inferred object type: it can have more sending labels](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-101-2048.jpg)
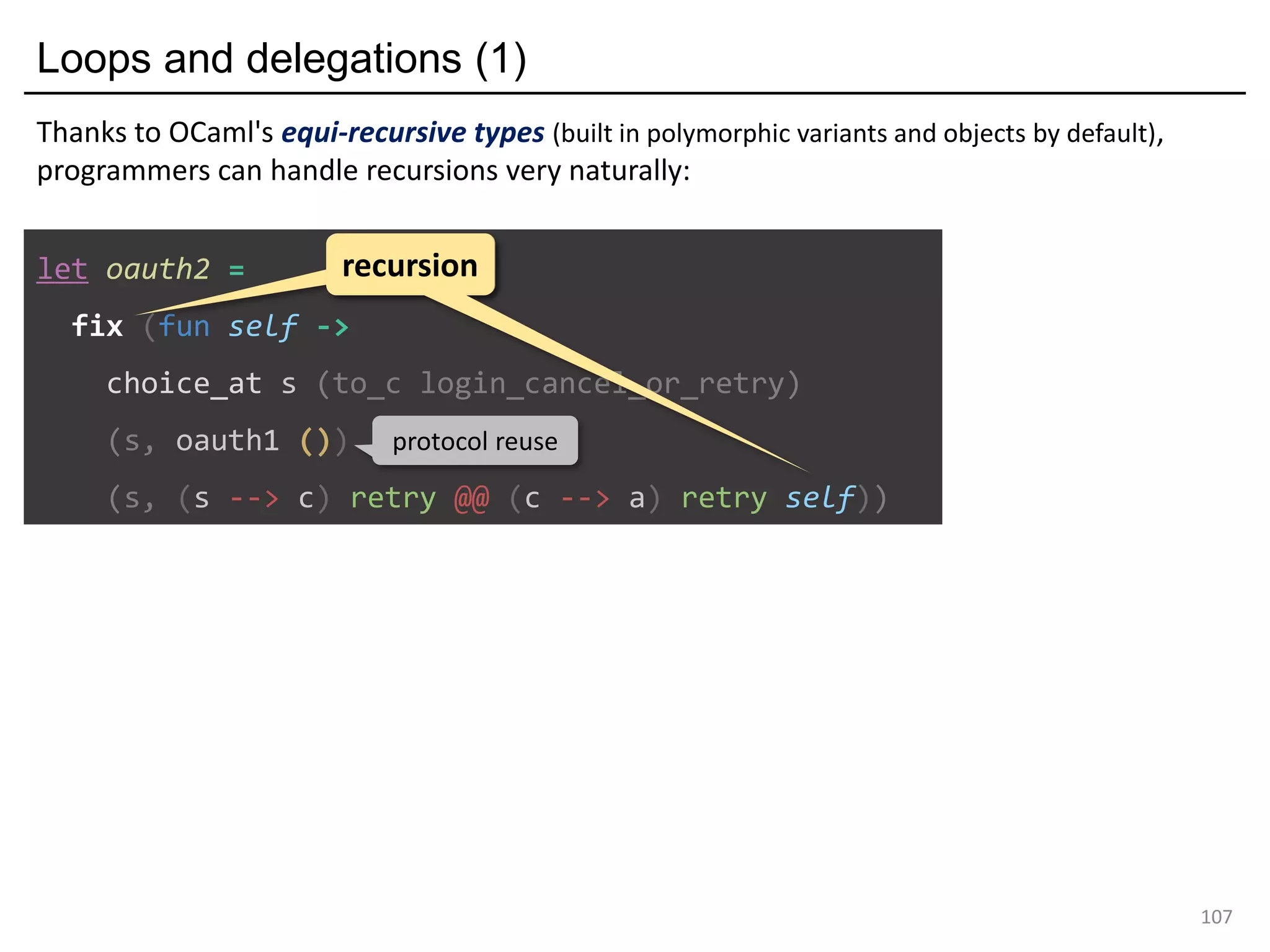
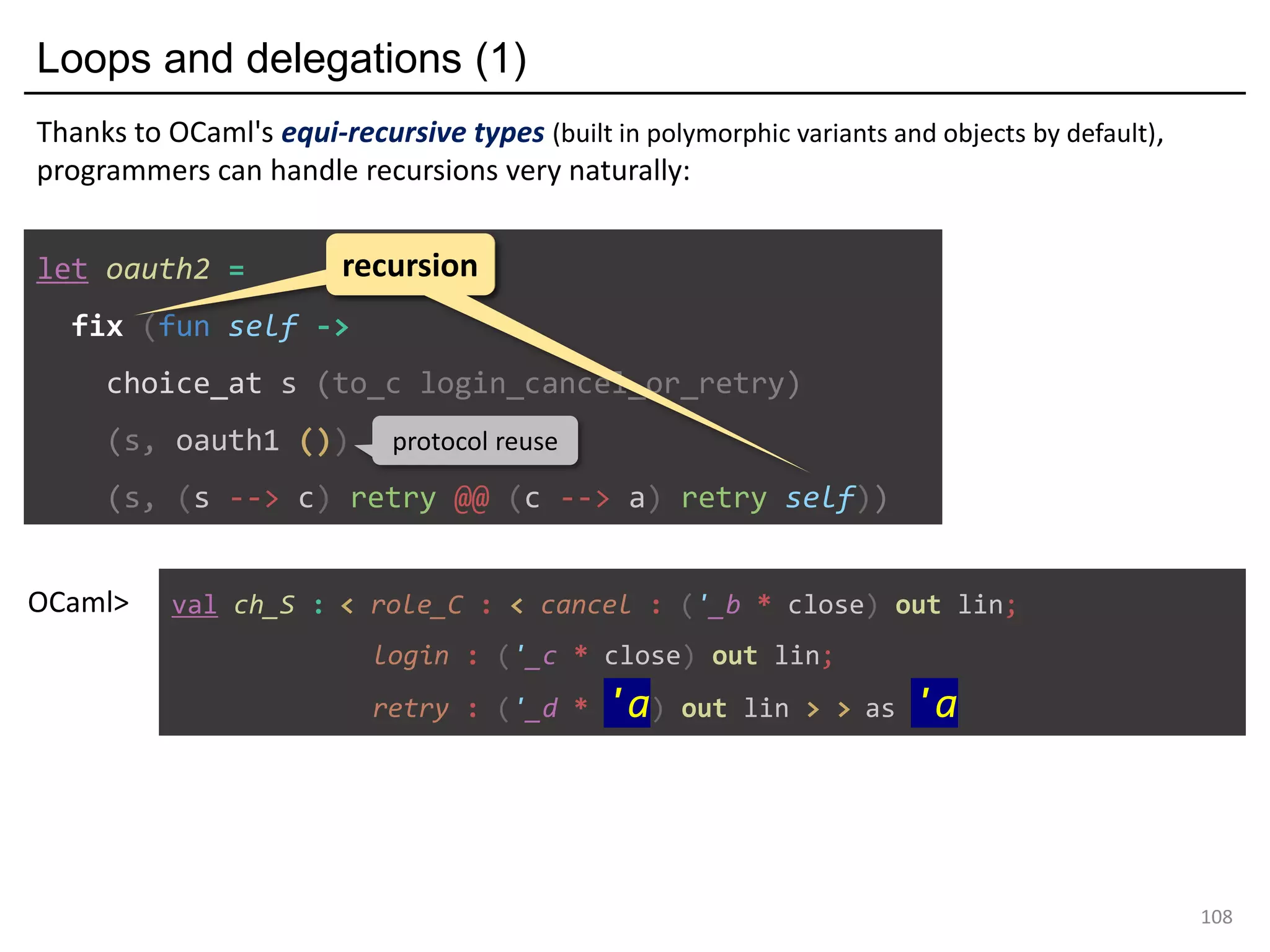
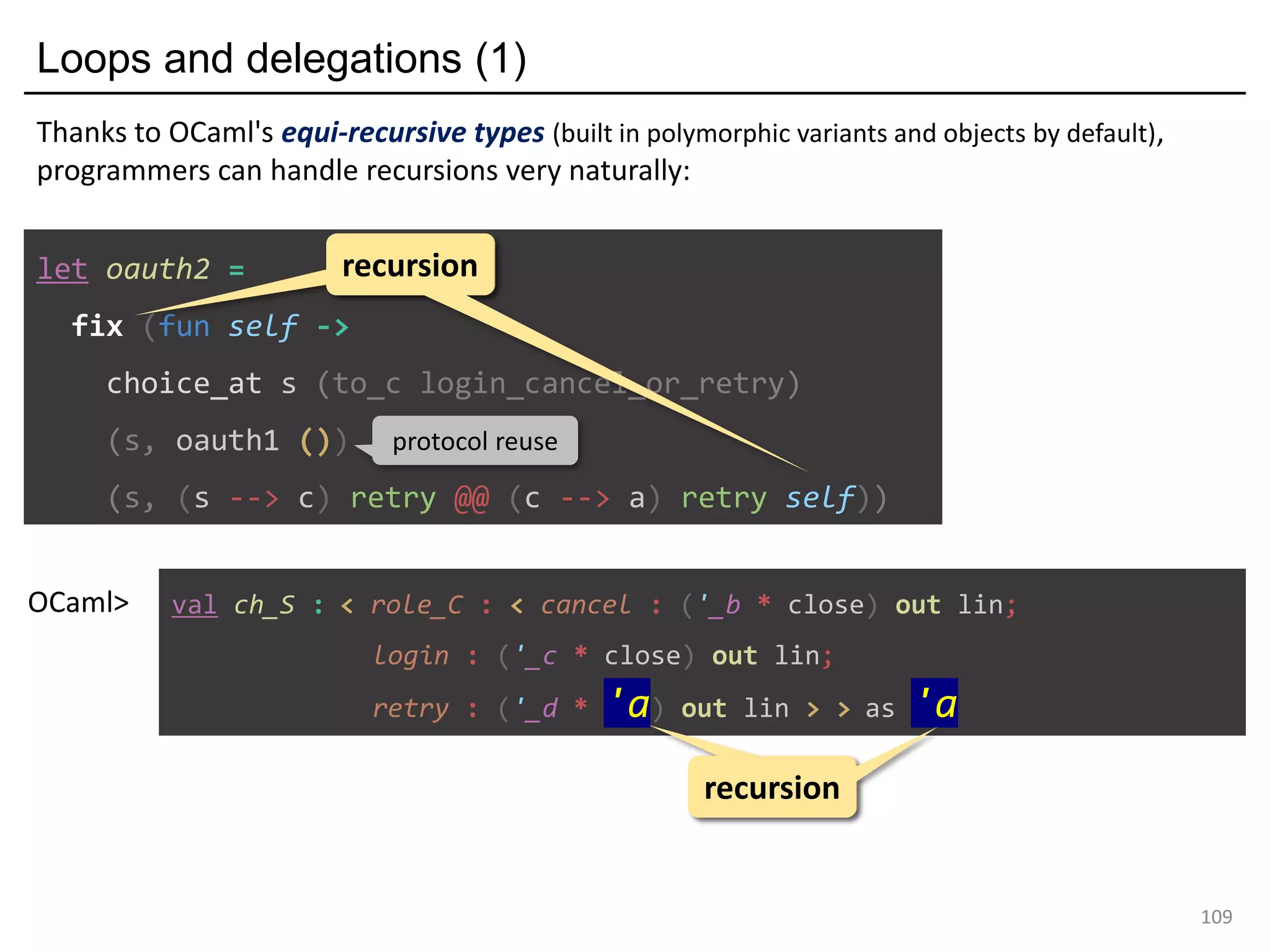
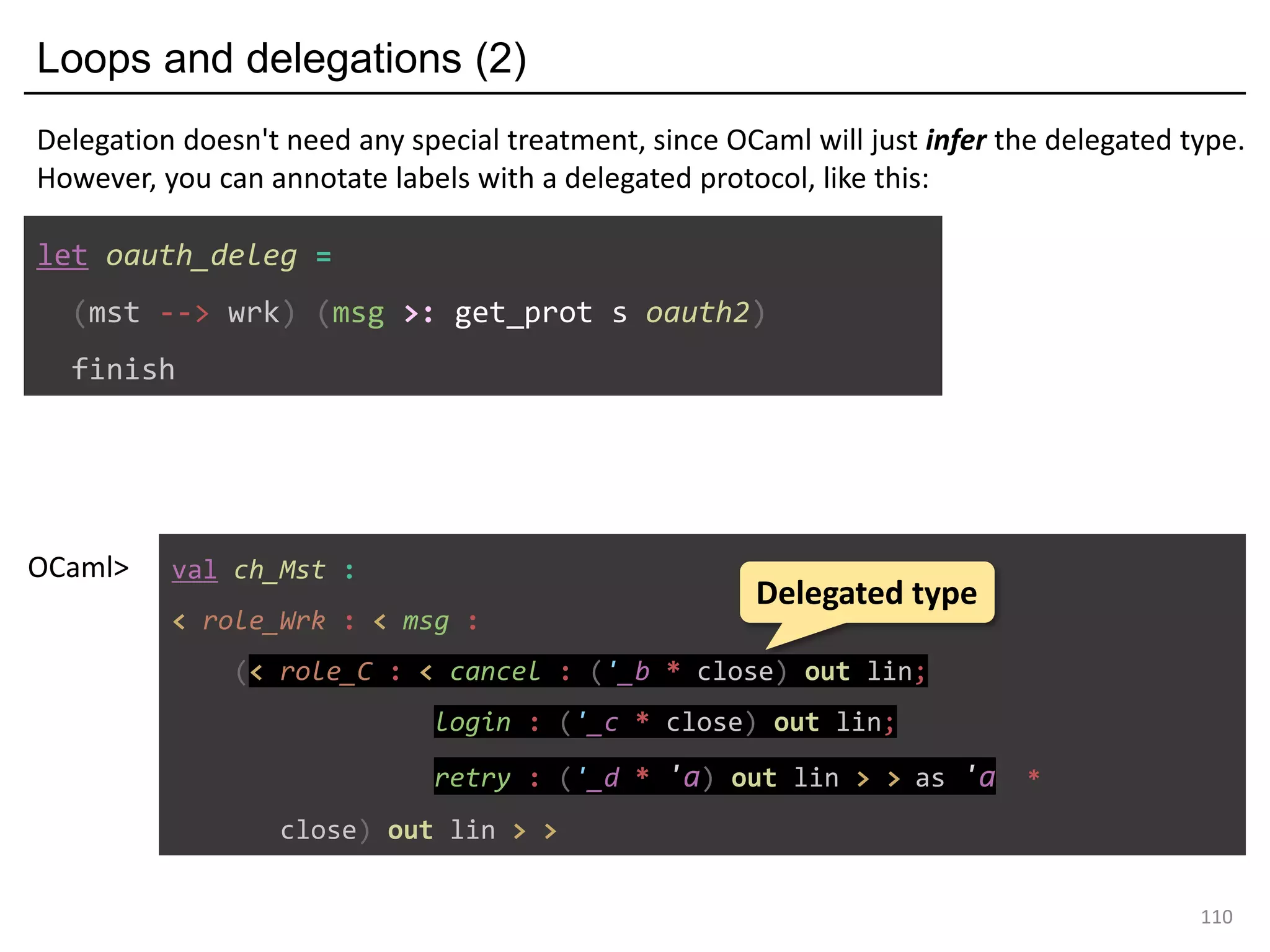
![[Formalisation] OCamlM : a Minimal calculus for global combinators
Main results:
115
A calculus with structural subtyping, equi-recursive types and
i/o-typed channels
Theorem (Subject Reduction): if ⊢ e and e→* e' then ⊢ e'
Theorem (Operational Correspondence):
(Completeness)
(Soundness)
Corollary (Deadlock Freedom): If an MPST process P is
deadlock-free, OCamlM expression e=⟦P⟧ is deadlock-free.](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-115-2048.jpg)
![• Benchmarks reflect our design decision to use
mutable long lived objects (e.g channel vectors)
❖ Our work: few mutable long lived objects, created at the start of the protocol
❖ State-of-the-art (linear-decomposition [Scala et.a]): many small channels, created on-demand
(during the protocol execution)
118](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-118-2048.jpg)
![Benchmarks
• Comparison with Linear (Binary) Decomposition [Scalas et al., 2017]
❖ Translation from MPST to Linear Types
❖ Continuation Passing Style (CPS):
It creates (and exchanges) a fresh channel at each communication step
❖ Must be slower than us??
• Compete with ours in some cases (!), but CPS is slower in general
❖ OCaml's major GC is doing nice work
• Monad (static linearity checking with overhead) VS. Direct style (dynamic)
119](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-119-2048.jpg)
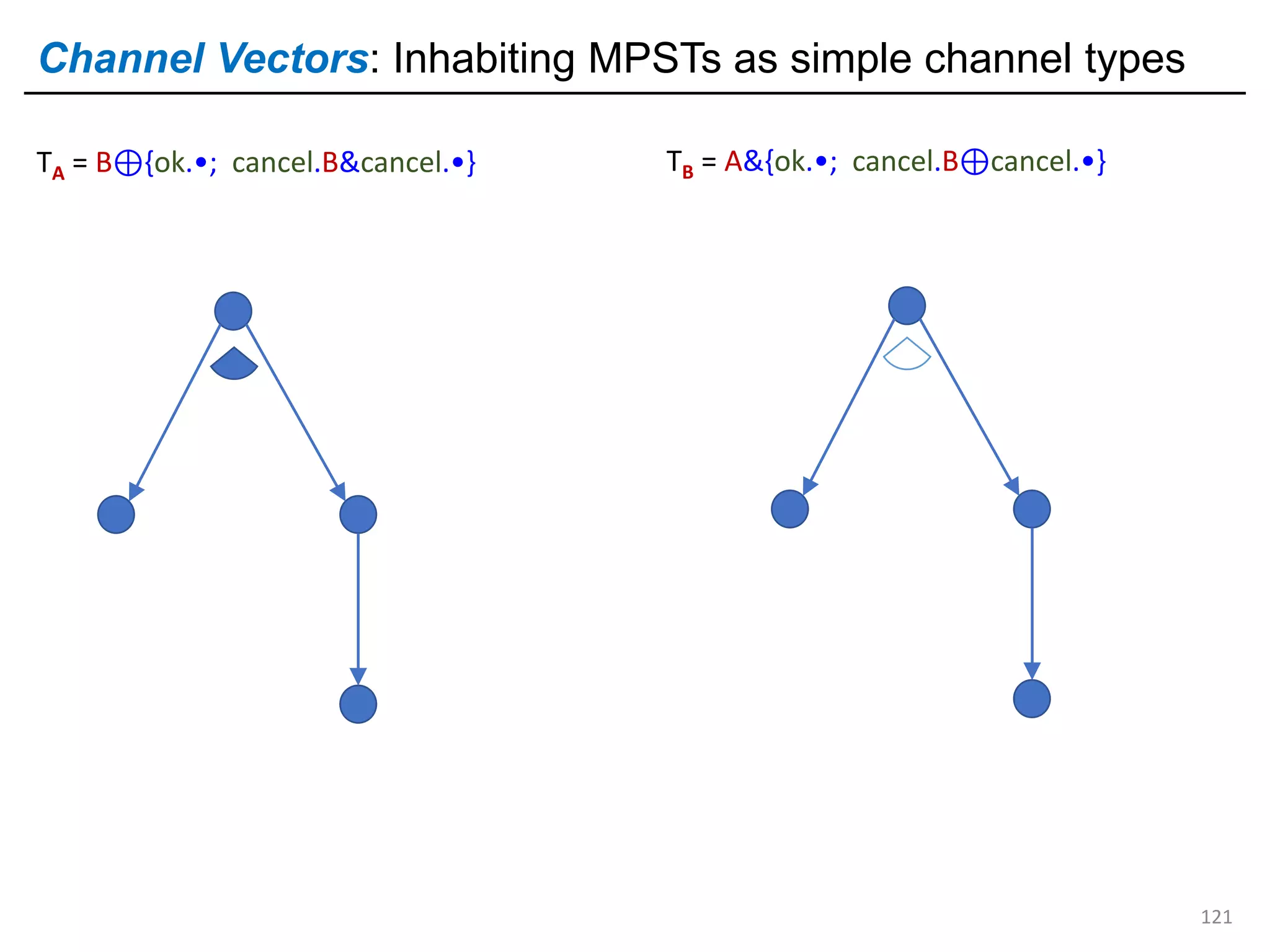
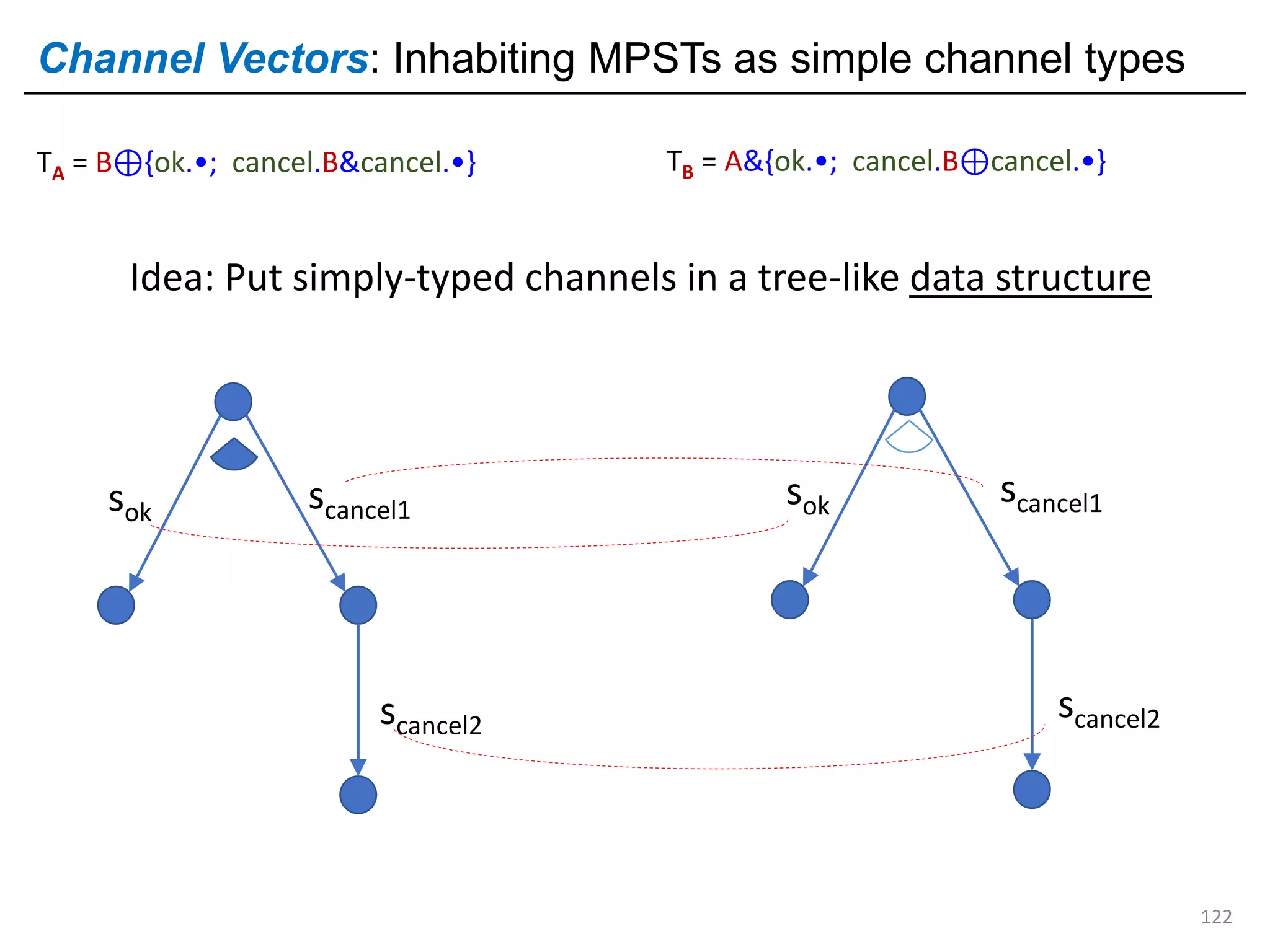
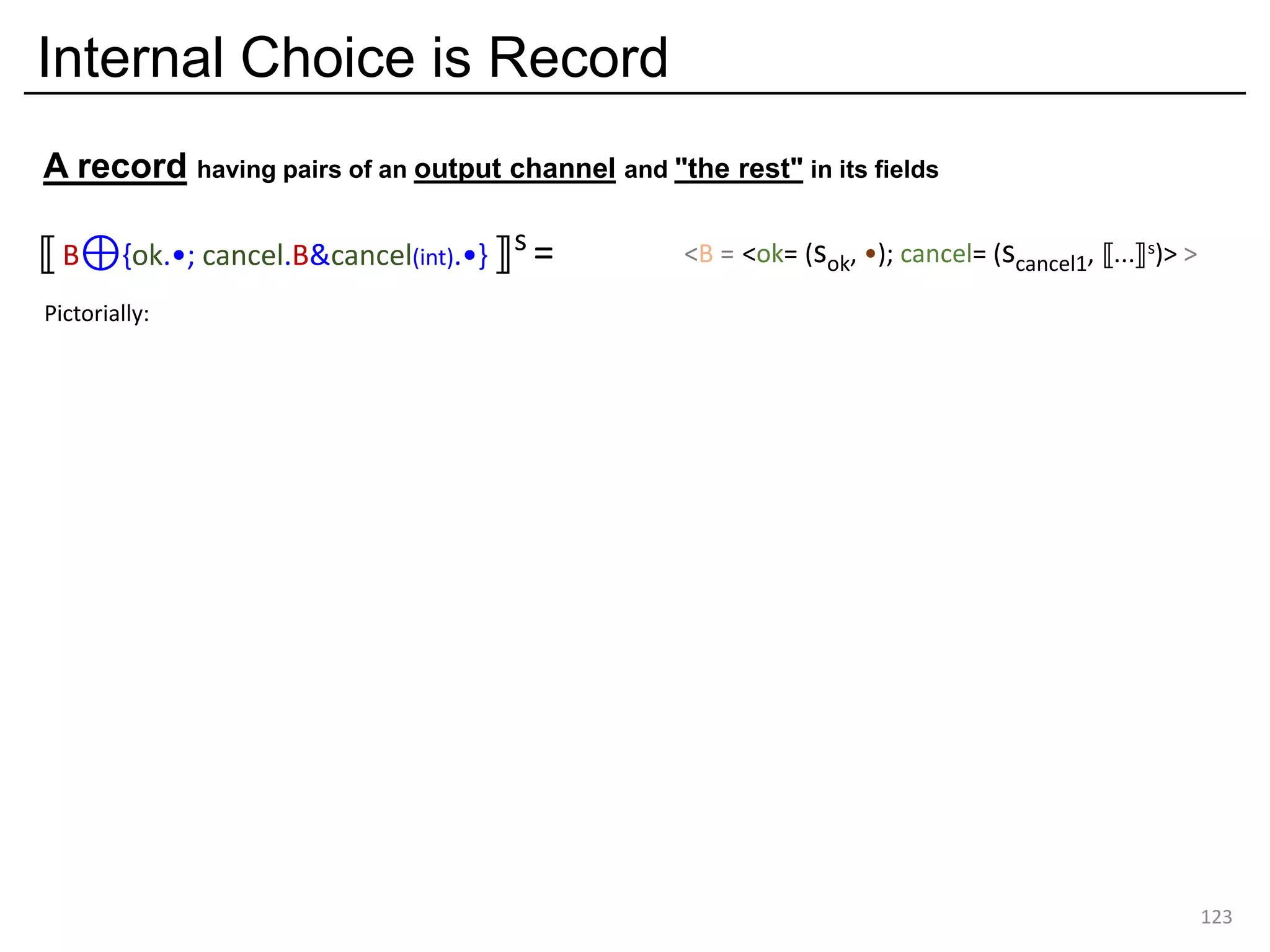
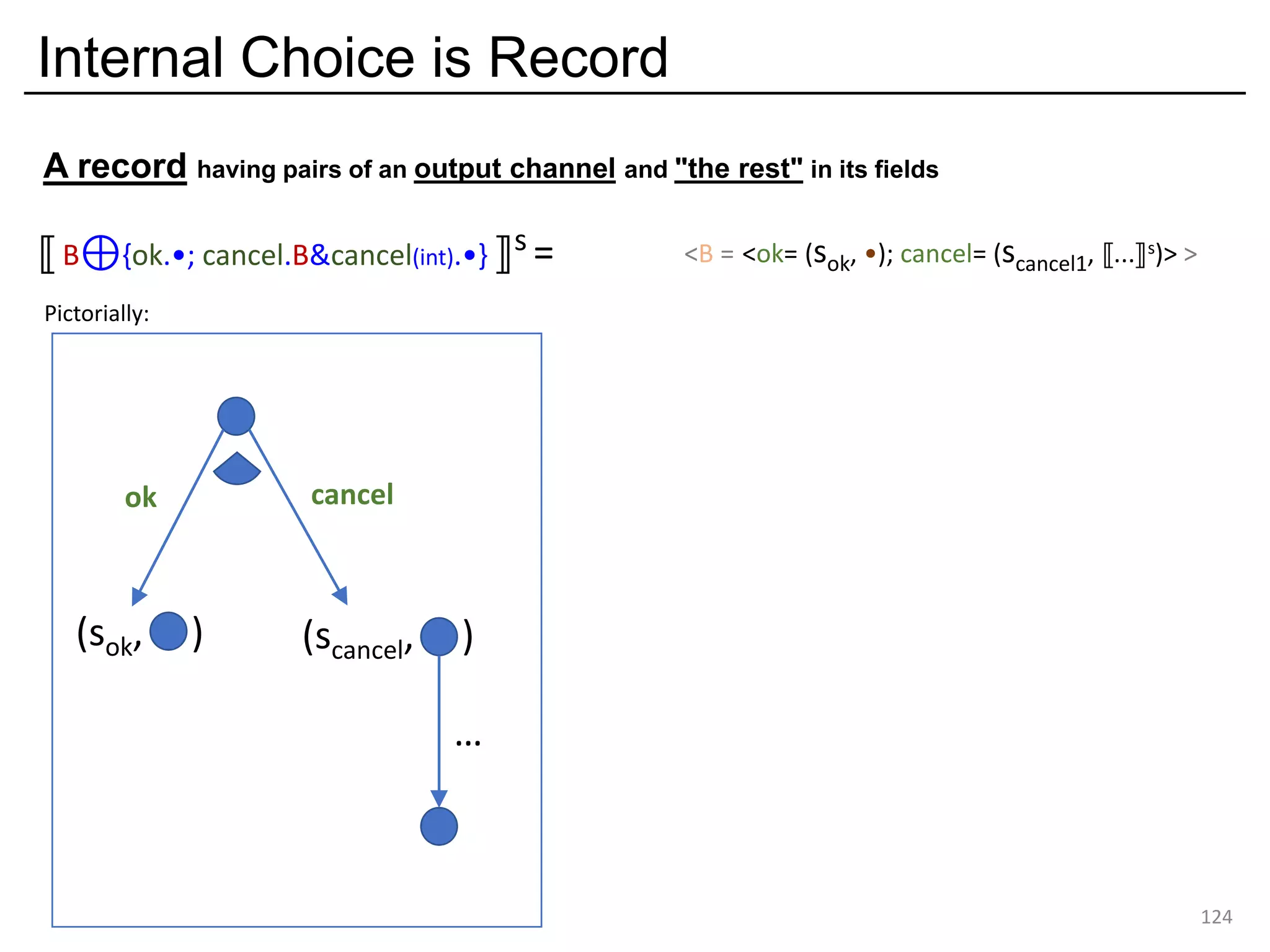
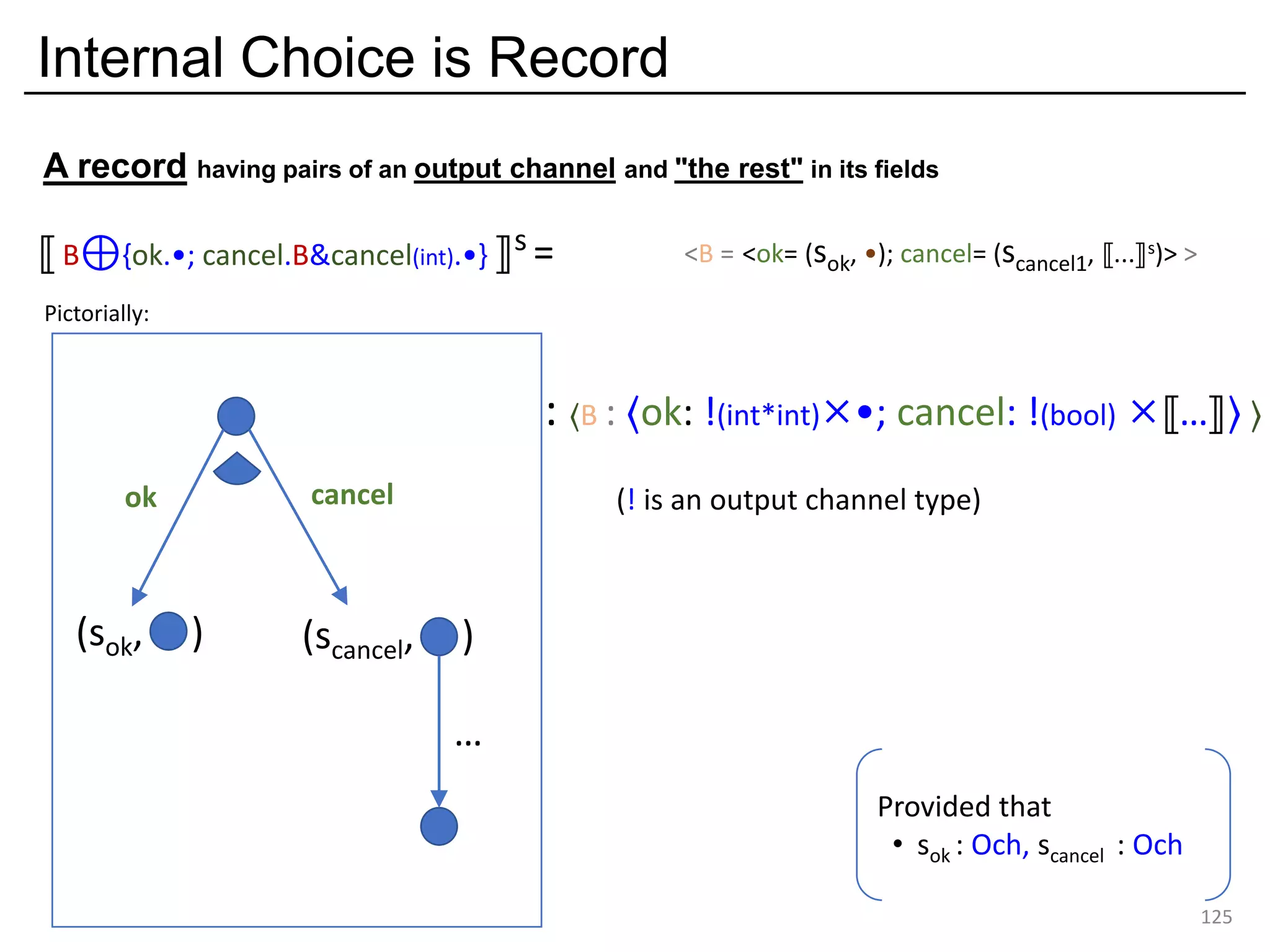
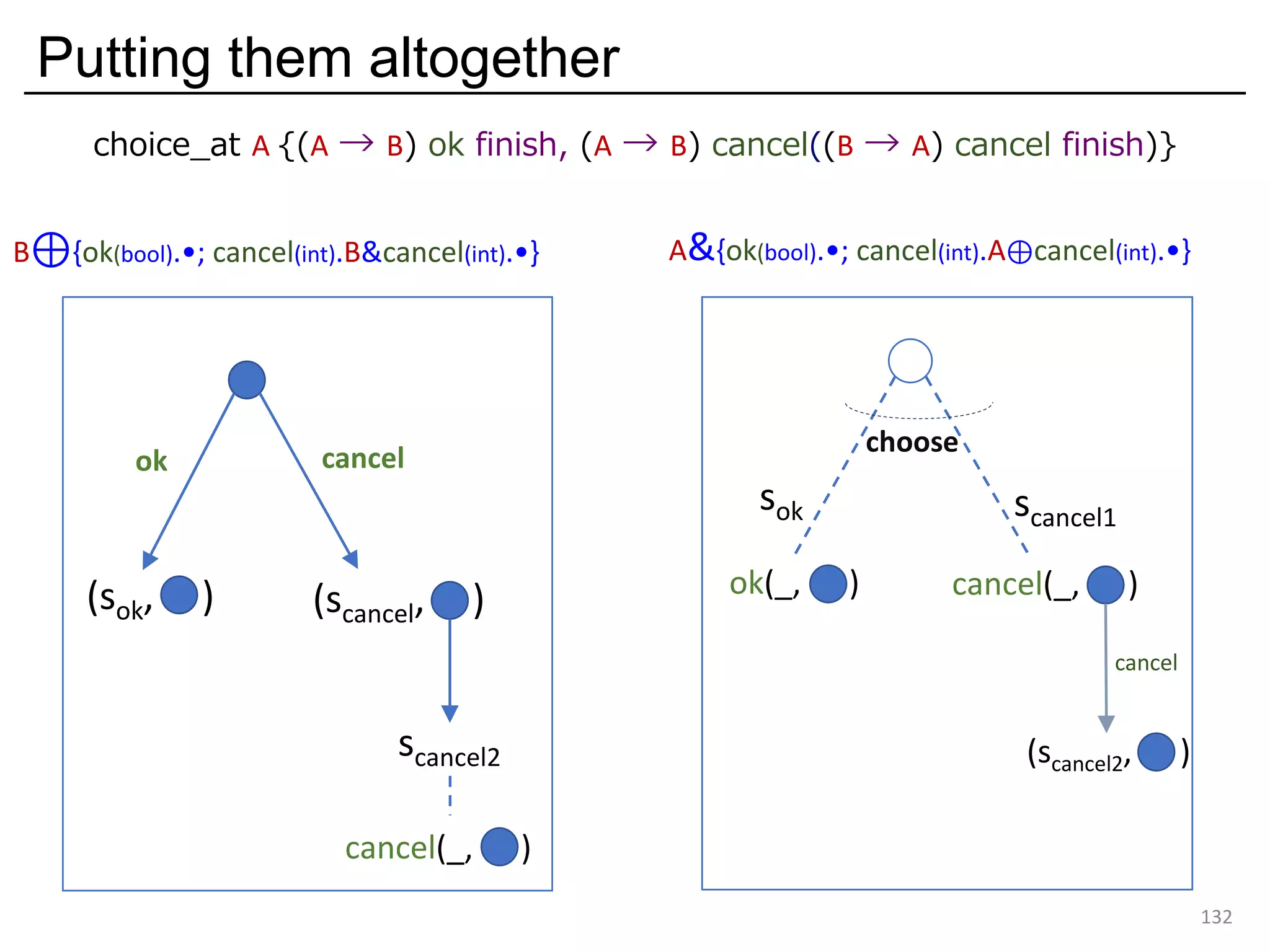
![External choice is variant input
126
Variant input type: ?[ok_(boolו); cancel_(int× …)]
Variant type: [ok_(boolו); cancel_(int× …)]
("Either ok (with boolו) or cancel (with intׅ)")
("Receives either ok (with boolו) or cancel (with intׅ)")
cancel(_, )ok(_, )
scancel1sok
cancel
external choice
Pictorially: But how?](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-126-2048.jpg)
![A Solution from Concurrent ML (Reppy, 1993)
127
… has a set of (event) primitives we need!
choose : List[?T] -> ?T
makes a (multiplexed) channel (external choice)
wrap : (α -> β) -> ?α -> ?β
makes a wrapped channel
sok : ?bool, scancel : ?int
: ?[ok_(boolו); cancel_(int× …)] (← wanted)](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-127-2048.jpg)
![A Solution from Concurrent ML (Reppy, 1993)
128
… has a set of (event) primitives we need!
choose : List[?T] -> ?T
makes a (multiplexed) channel (external choice)
wrap : (α -> β) -> ?α -> ?β
makes a wrapped channel
sok : ?bool, scancel : ?int
wrap (λx.[ok=(x,•)]) sok
: ?[ok_(boolו)]
wrap (λx.[cancel=(x,…)]) scancel
: ?[cancel_(int×…)]
: ?[ok_(boolו); cancel_(int× …)] (← wanted)](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-128-2048.jpg)
![A Solution from Concurrent ML (Reppy, 1993)
129
… has a set of (event) primitives we need!
choose : List[?T] -> ?T
makes a (multiplexed) channel (external choice)
wrap : (α -> β) -> ?α -> ?β
makes a wrapped channel
sok : ?bool, scancel : ?int
wrap (λx.[ok=(x,•)]) sok
: ?[ok_(boolו)]
wrap (λx.[cancel=(x,…)]) scancel
: ?[cancel_(int×…)]
List(wrap (λx.[ok=(x,•)]) sok; wrap (λx.[cancel=(x,…)]) scancel)
: List[ ?[ok_(boolו), cancel_(intׅ)] ]
: ?[ok_(boolו); cancel_(int× …)] (← wanted)](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-129-2048.jpg)
![A Solution from Concurrent ML (Reppy, 1993)
130
… has a set of (event) primitives we need!
choose : List[?T] -> ?T
makes a (multiplexed) channel (external choice)
wrap : (α -> β) -> ?α -> ?β
makes a wrapped channel
sok : ?bool, scancel : ?int
wrap (λx.[ok=(x,•)]) sok
: ?[ok_(boolו)]
wrap (λx.[cancel=(x,…)]) scancel
: ?[cancel_(int×…)]
List(wrap (λx.[ok=(x,•)]) sok; wrap (λx.[cancel=(x,…)]) scancel)
: List[ ?[ok_(boolו), cancel_(intׅ)] ]
choose (List(wrap (λx.[ok=(x,•)]) sok; wrap (λx.[cancel=(x,…)]) scancel))
: ?[ok_(boolו); cancel_(int× …)] (← wanted)](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-130-2048.jpg)
![A Solution from Concurrent ML (Reppy, 1993)
131
… has a set of (event) primitives we need!
choose : List[?T] -> ?T
makes a (multiplexed) channel (external choice)
wrap : (α -> β) -> ?α -> ?β
makes a wrapped channel
sok : ?bool, scancel : ?int
wrap (λx.[ok=(x,•)]) sok
: ?[ok_(boolו)]
wrap (λx.[cancel=(x,…)]) scancel
: ?[cancel_(int×…)]
List(wrap (λx.[ok=(x,•)]) sok; wrap (λx.[cancel=(x,…)]) scancel)
: List[ ?[ok_(boolו), cancel_(intׅ)] ]
choose (List(wrap (λx.[ok=(x,•)]) sok; wrap (λx.[cancel=(x,…)]) scancel))
cancel(_, )ok(_, )
scancel1
sok
(scancel2, )
cancel
choose
: ?[ok_(boolו); cancel_(int× …)] (← wanted)](https://image.slidesharecdn.com/ocaml-mpst-kent-anim-190924105910/75/OCaml-MPST-Global-Protocol-Combinators-131-2048.jpg)