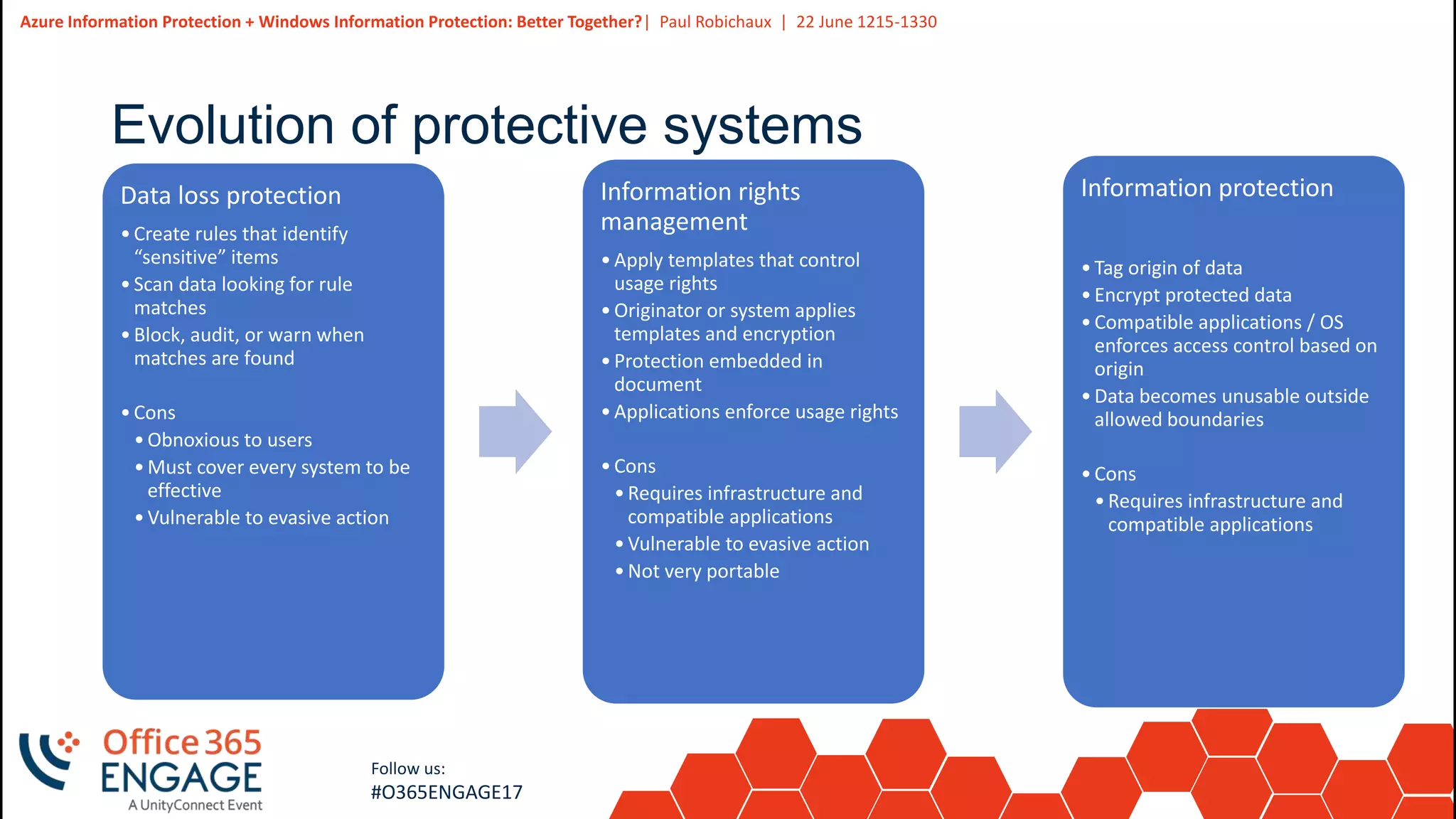
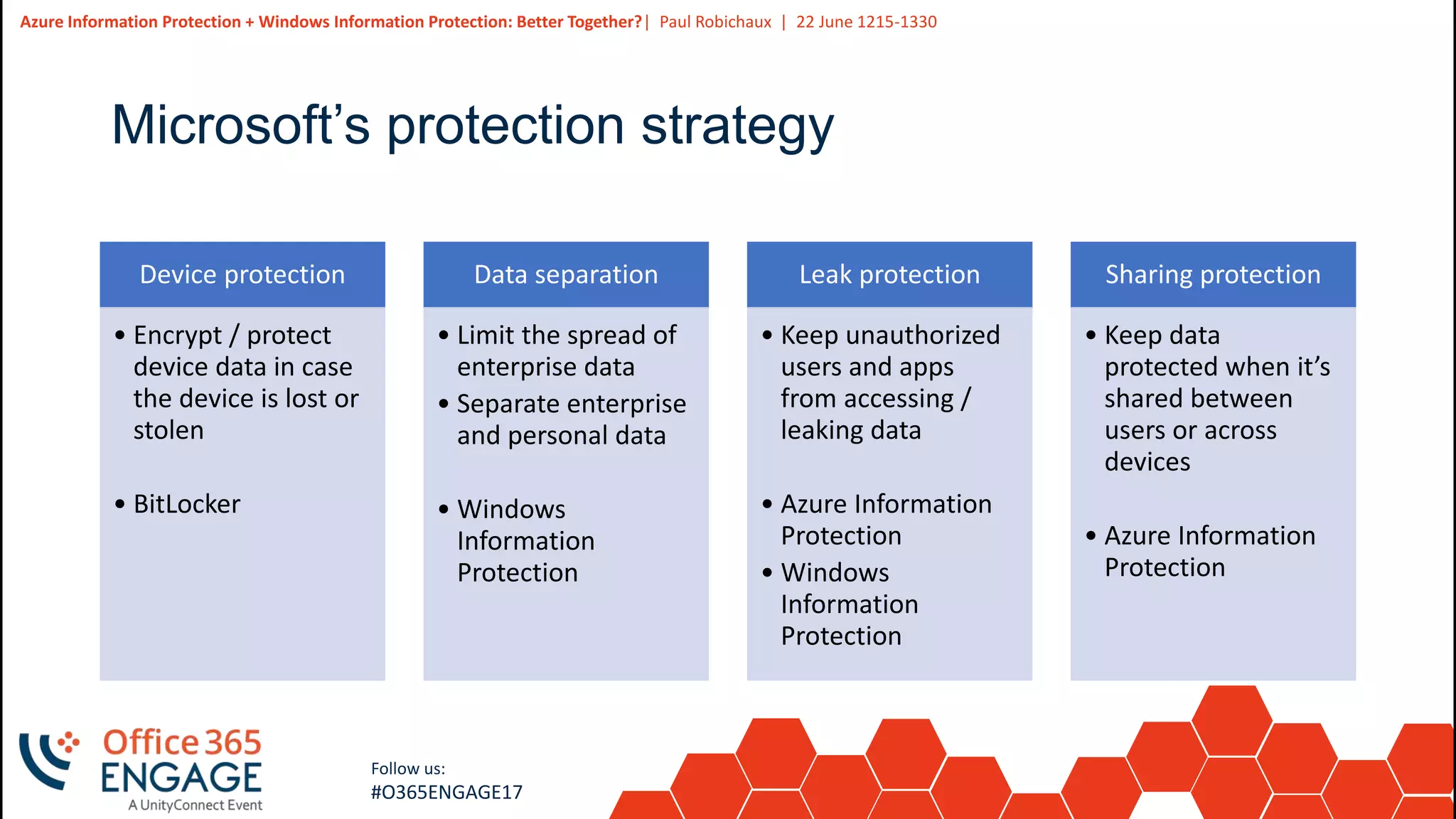
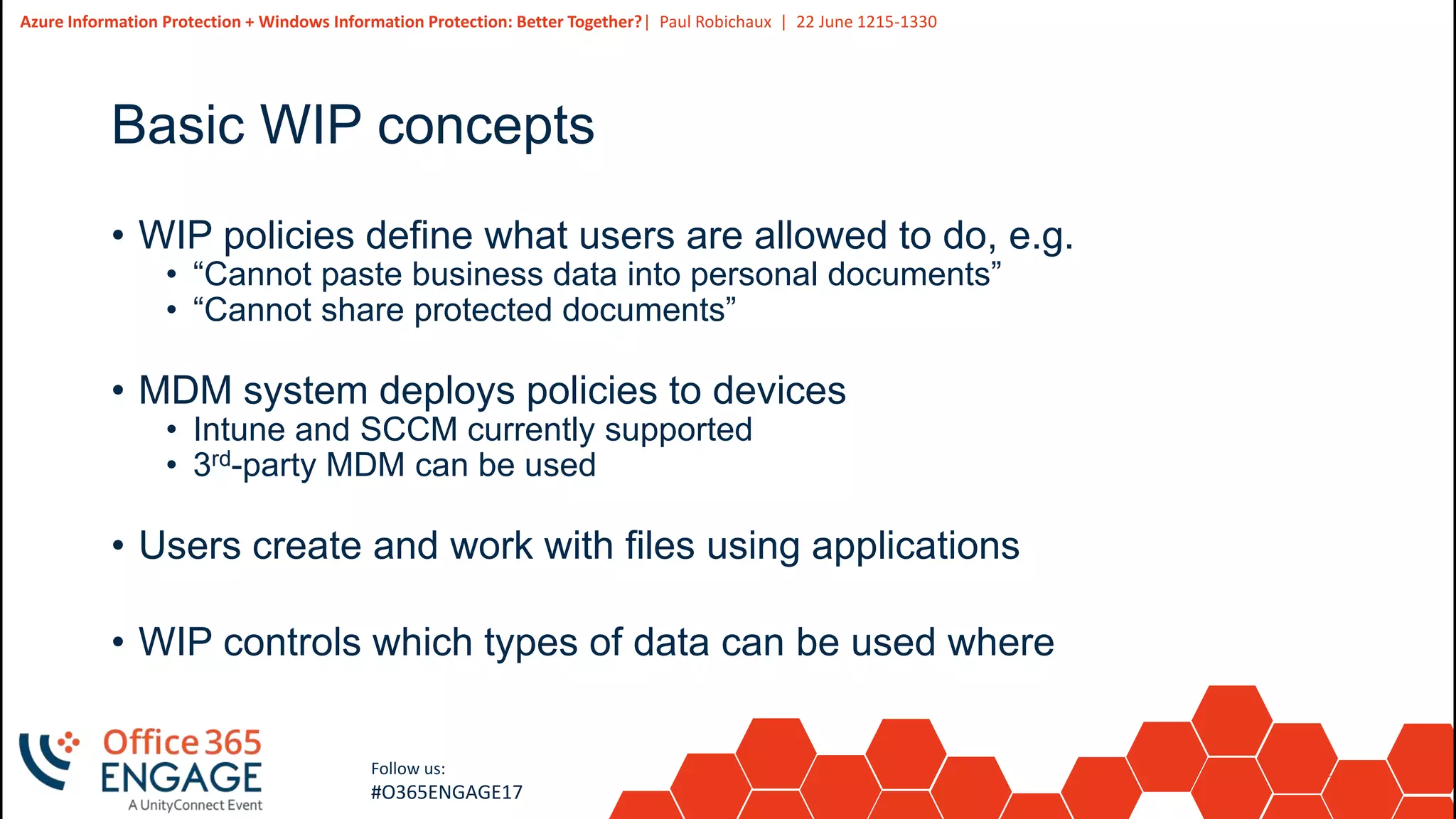
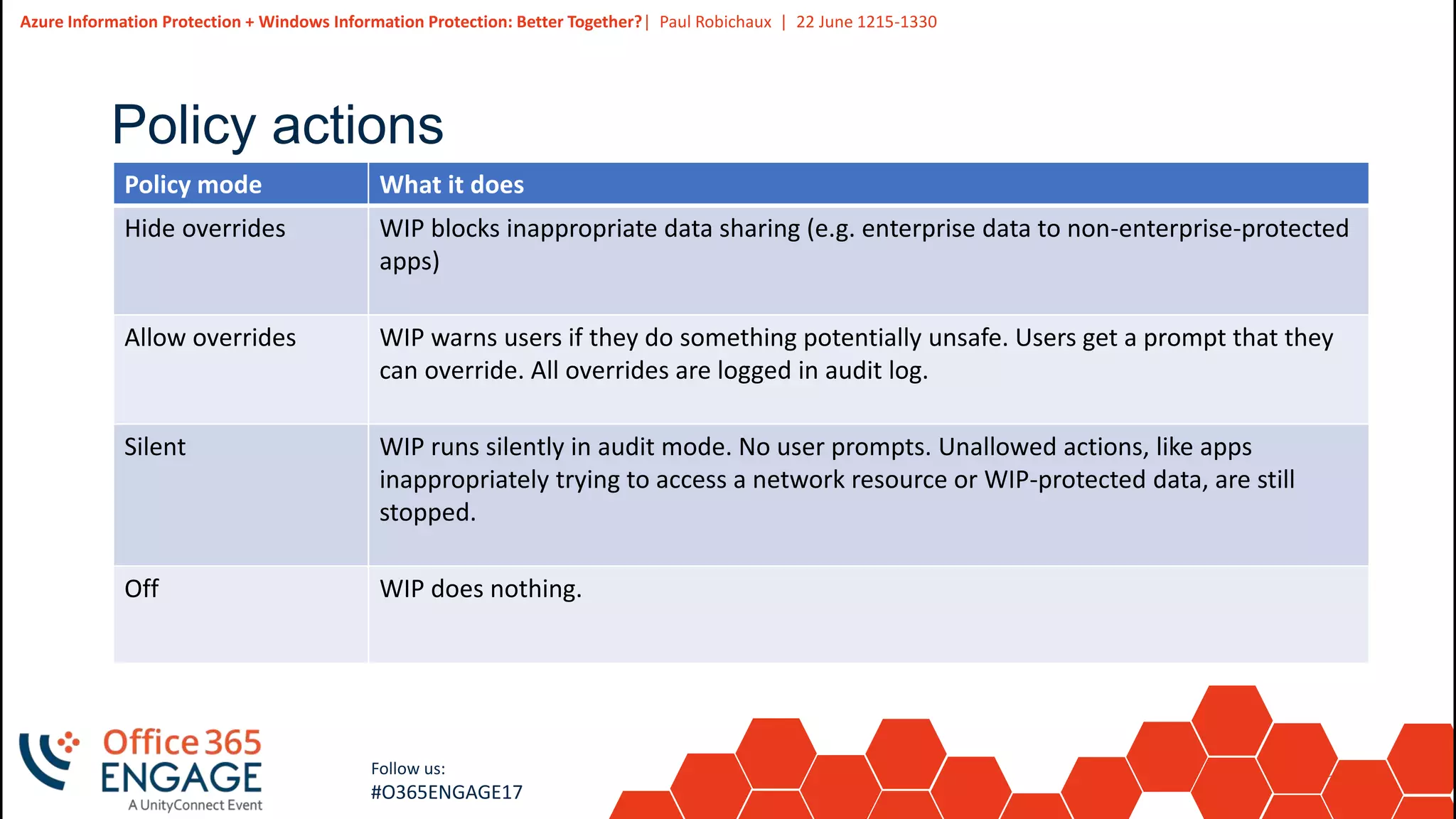
This presentation discusses how Azure Information Protection (AIP) and Windows Information Protection (WIP) work together to protect organizational data. AIP uses information rights management to encrypt and control access to documents in Office 365. WIP provides context awareness and policies on Windows devices to separate enterprise and personal data and control what apps can access each type of data. The presentation demonstrates basic AIP functionality in Outlook and explains how WIP policies define rules for user actions related to protected business data.