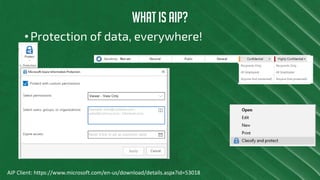
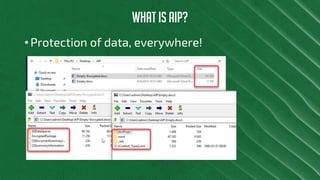
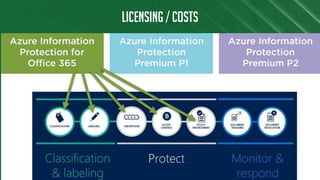
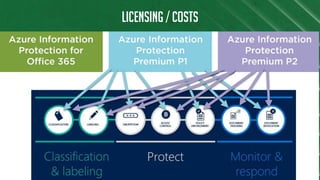
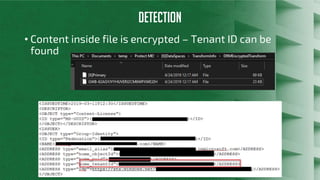
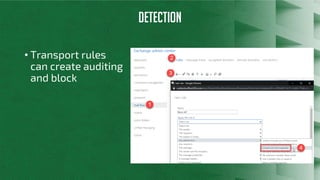
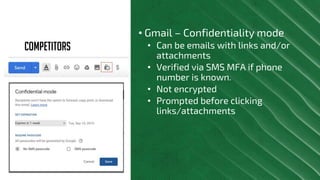
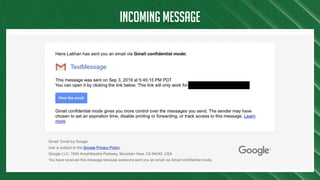
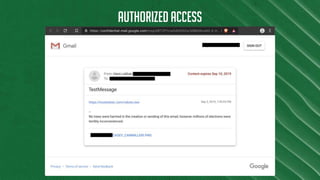
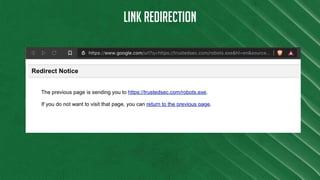
The document discusses Azure Information Protection (AIP), detailing its features, licensing costs, and user experience for phishing protection. Key aspects include data encryption, tracking email usage, and the ability to protect various file formats. It also compares AIP with competitor services like Gmail's confidentiality mode.