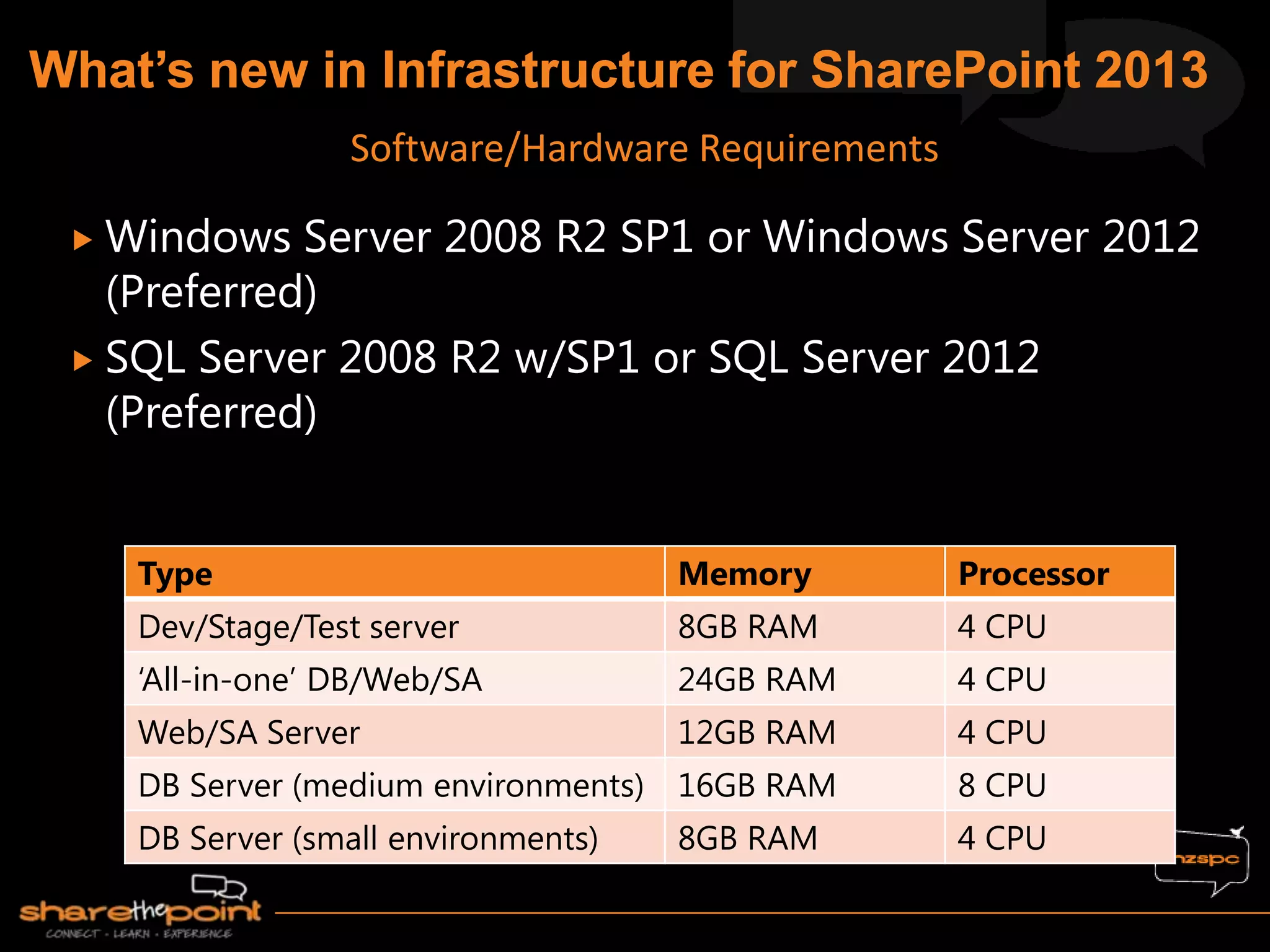
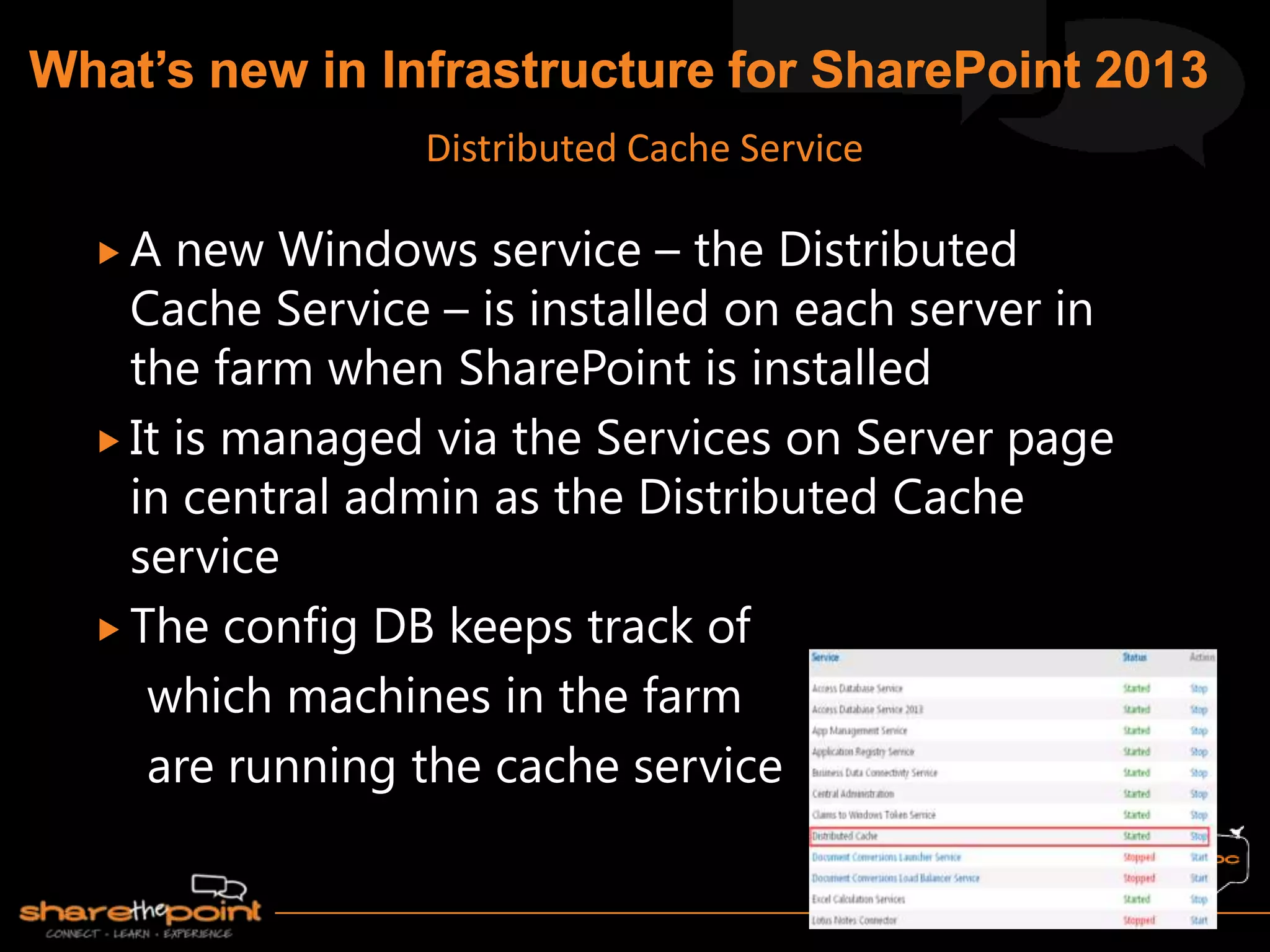
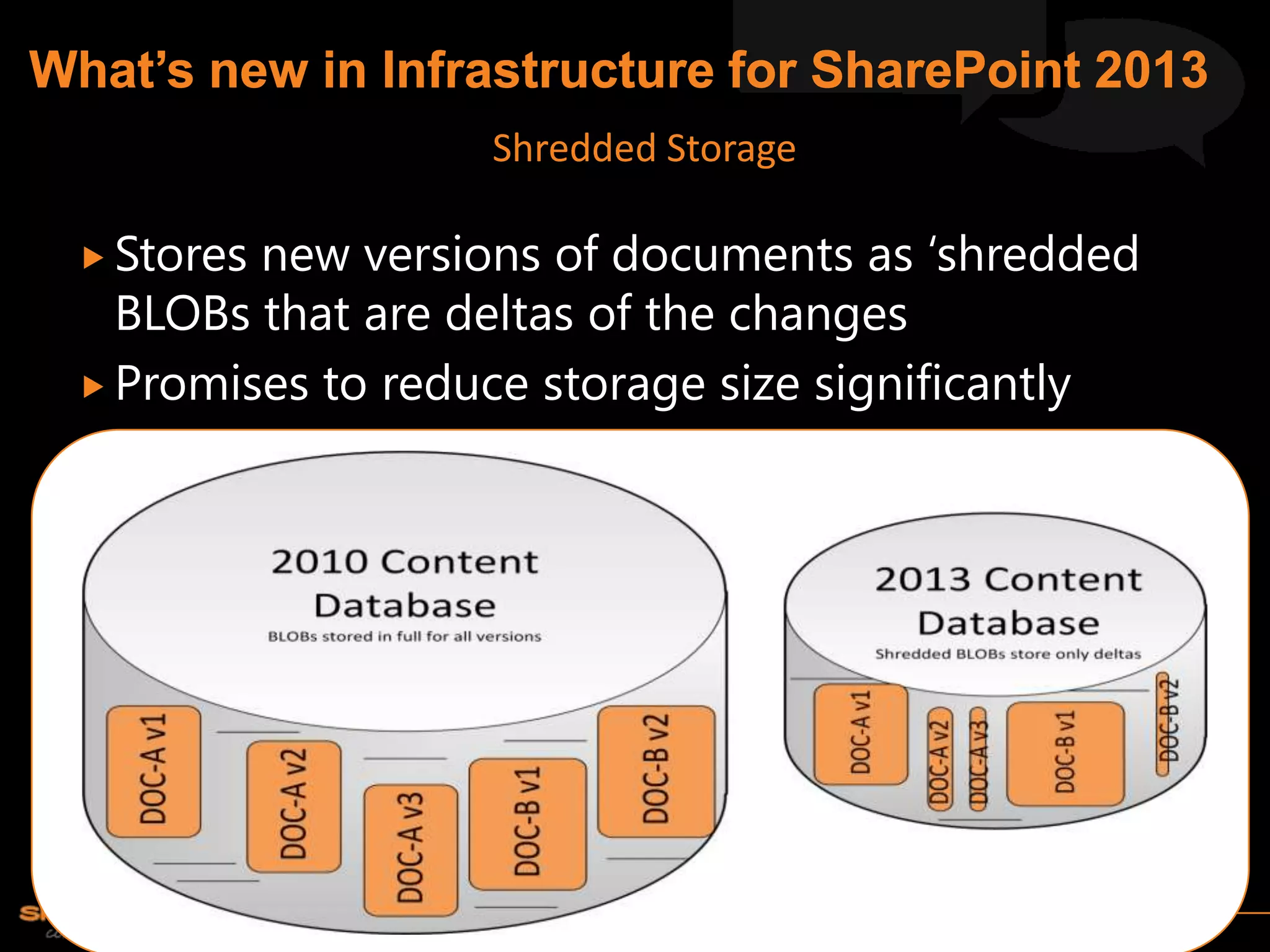
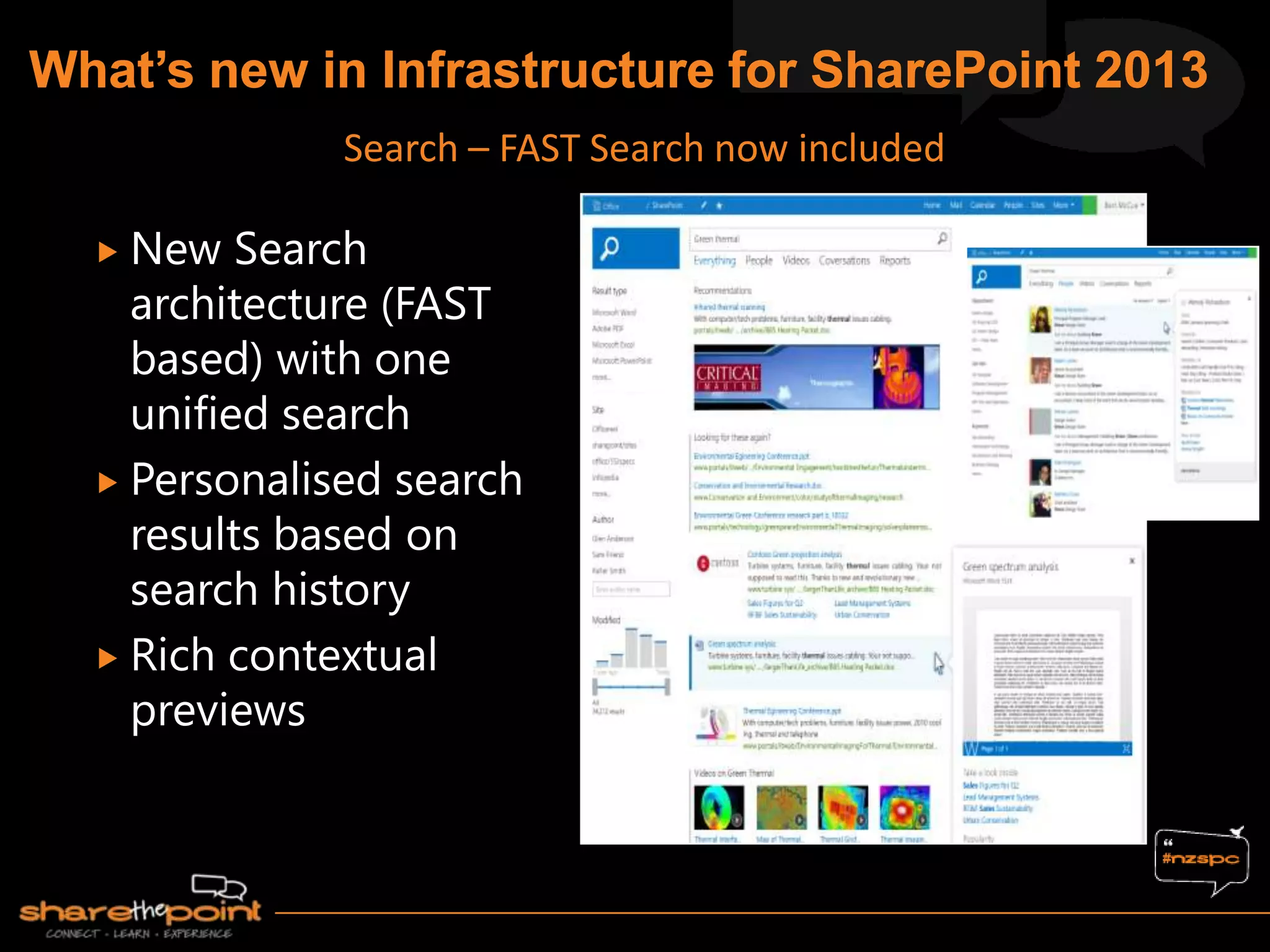
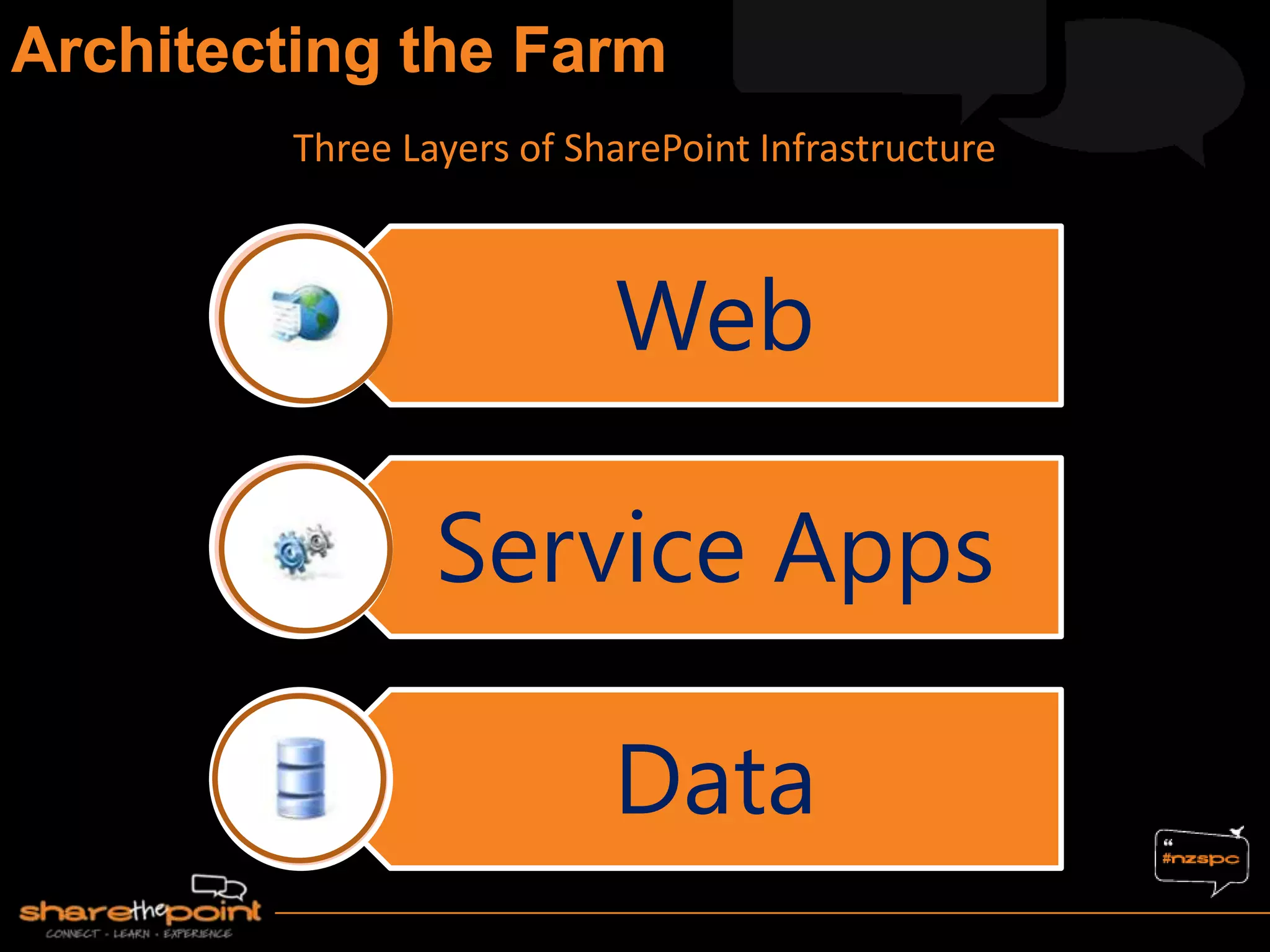
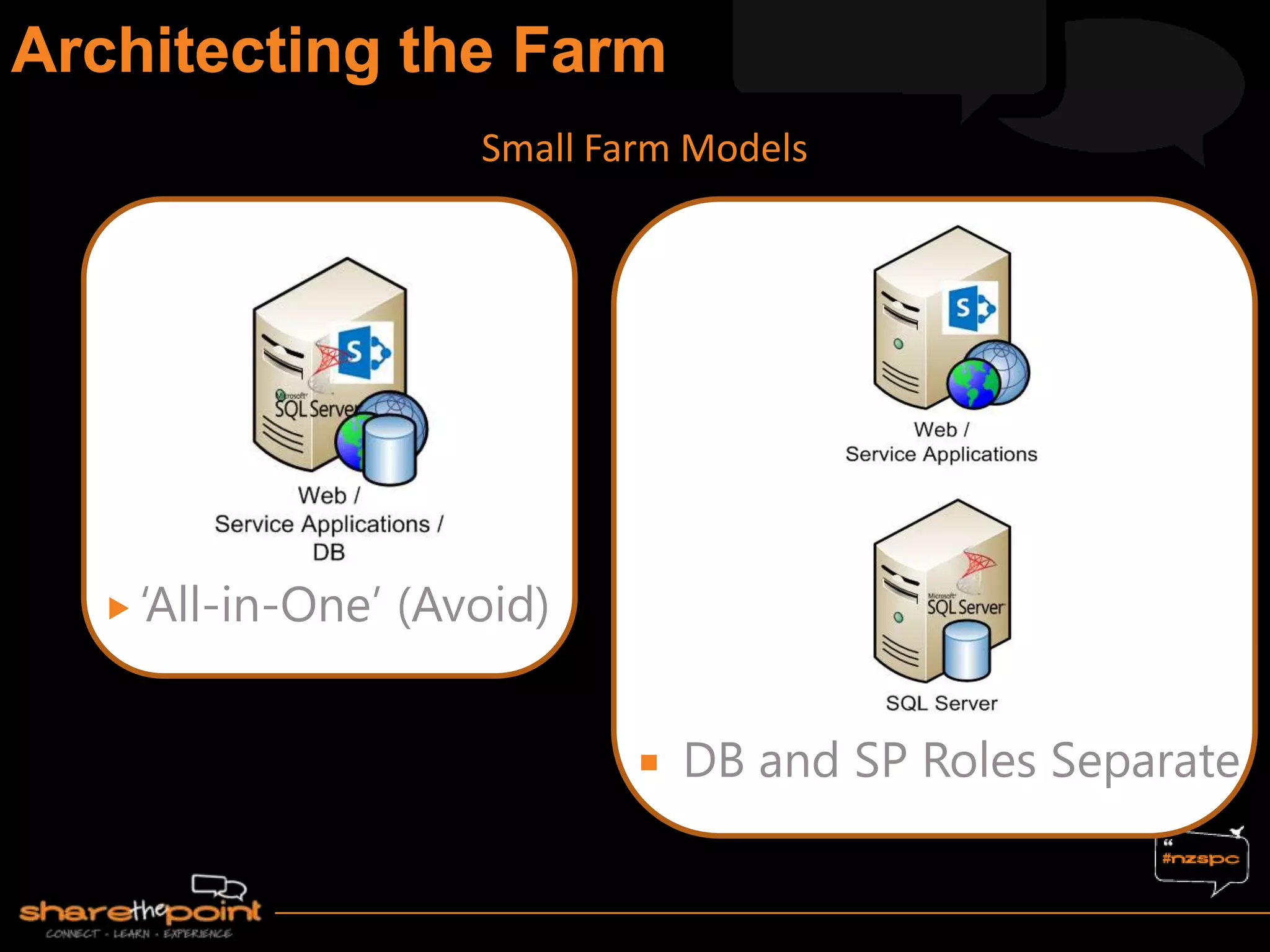
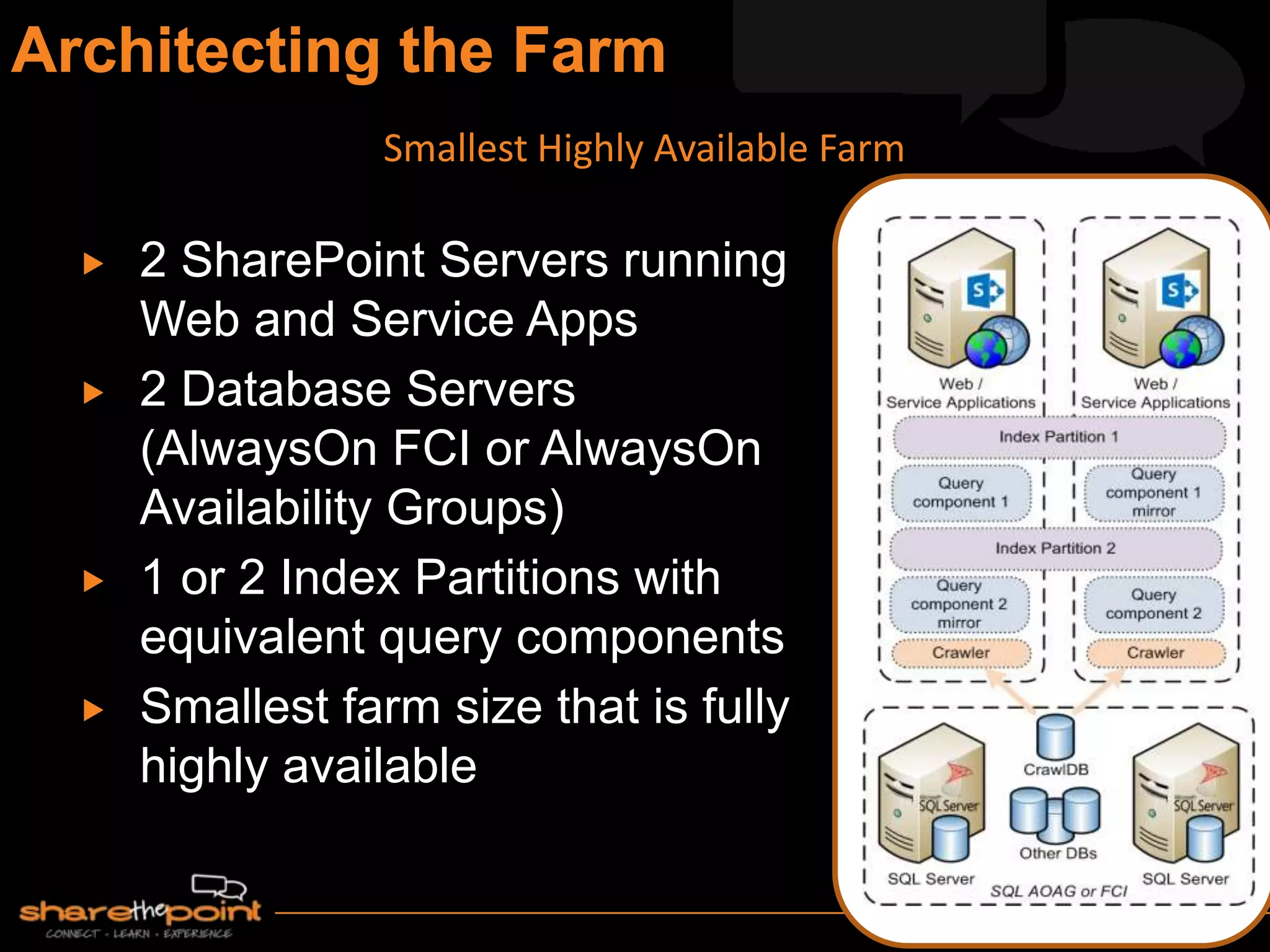
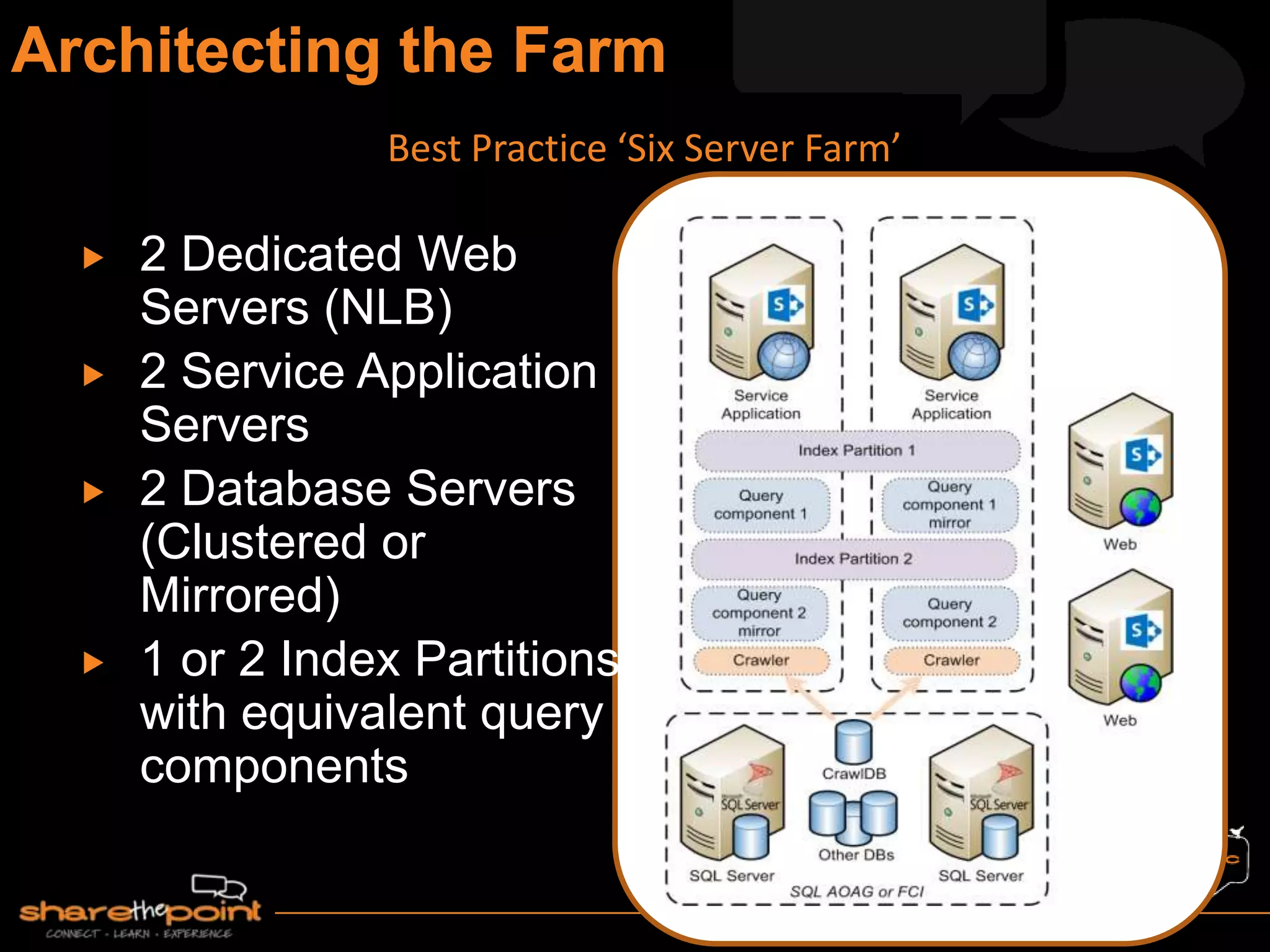
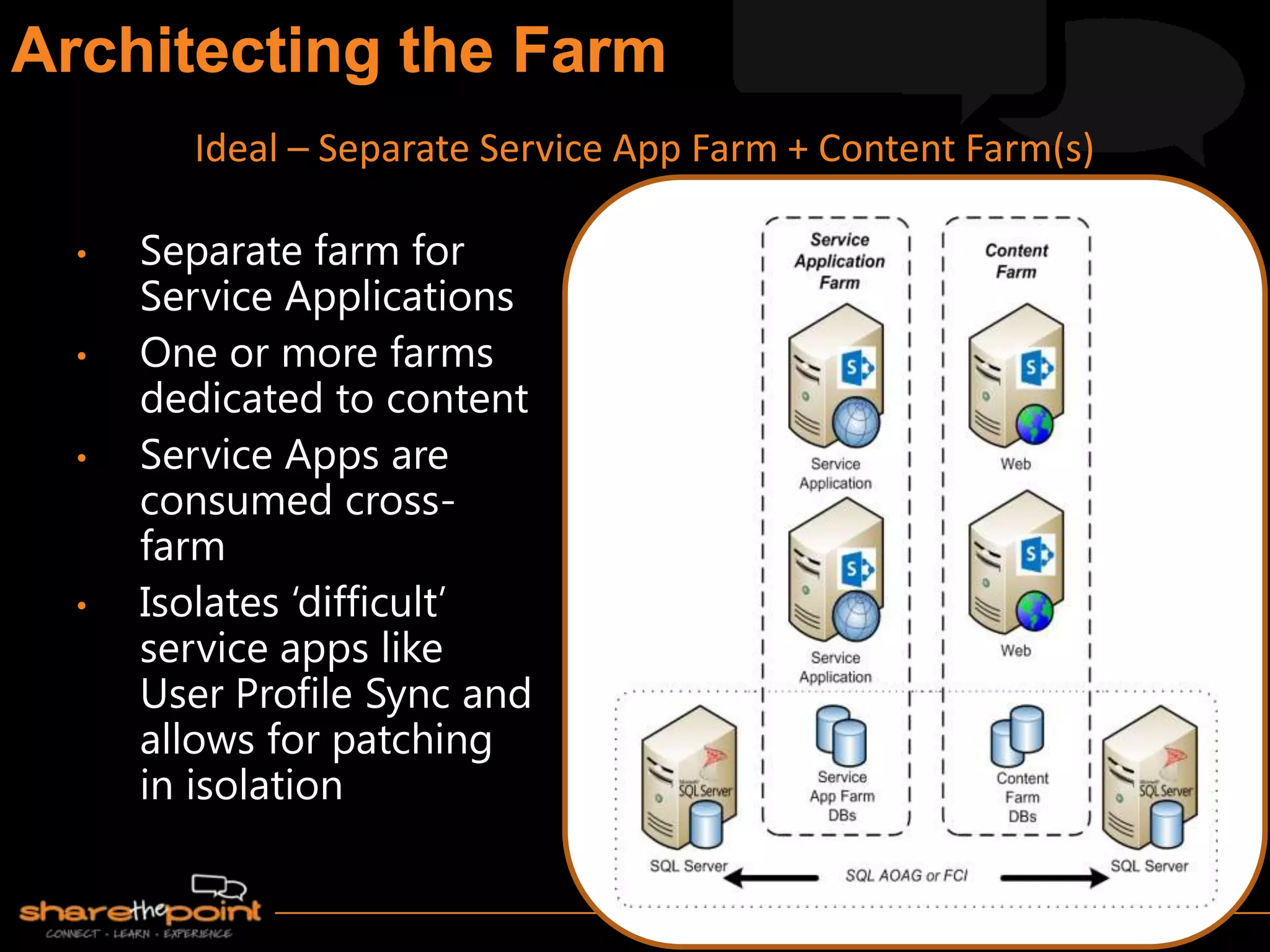
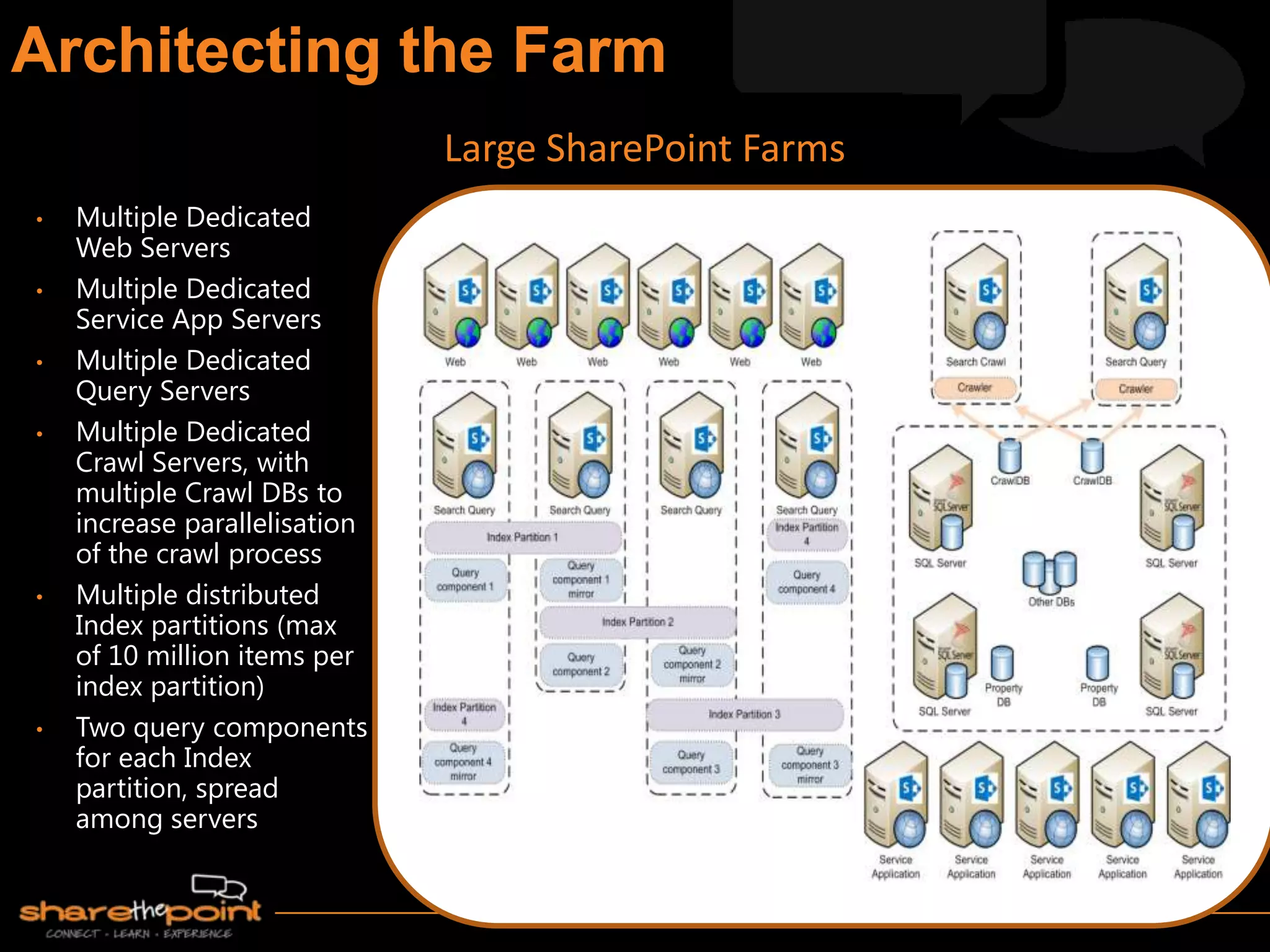
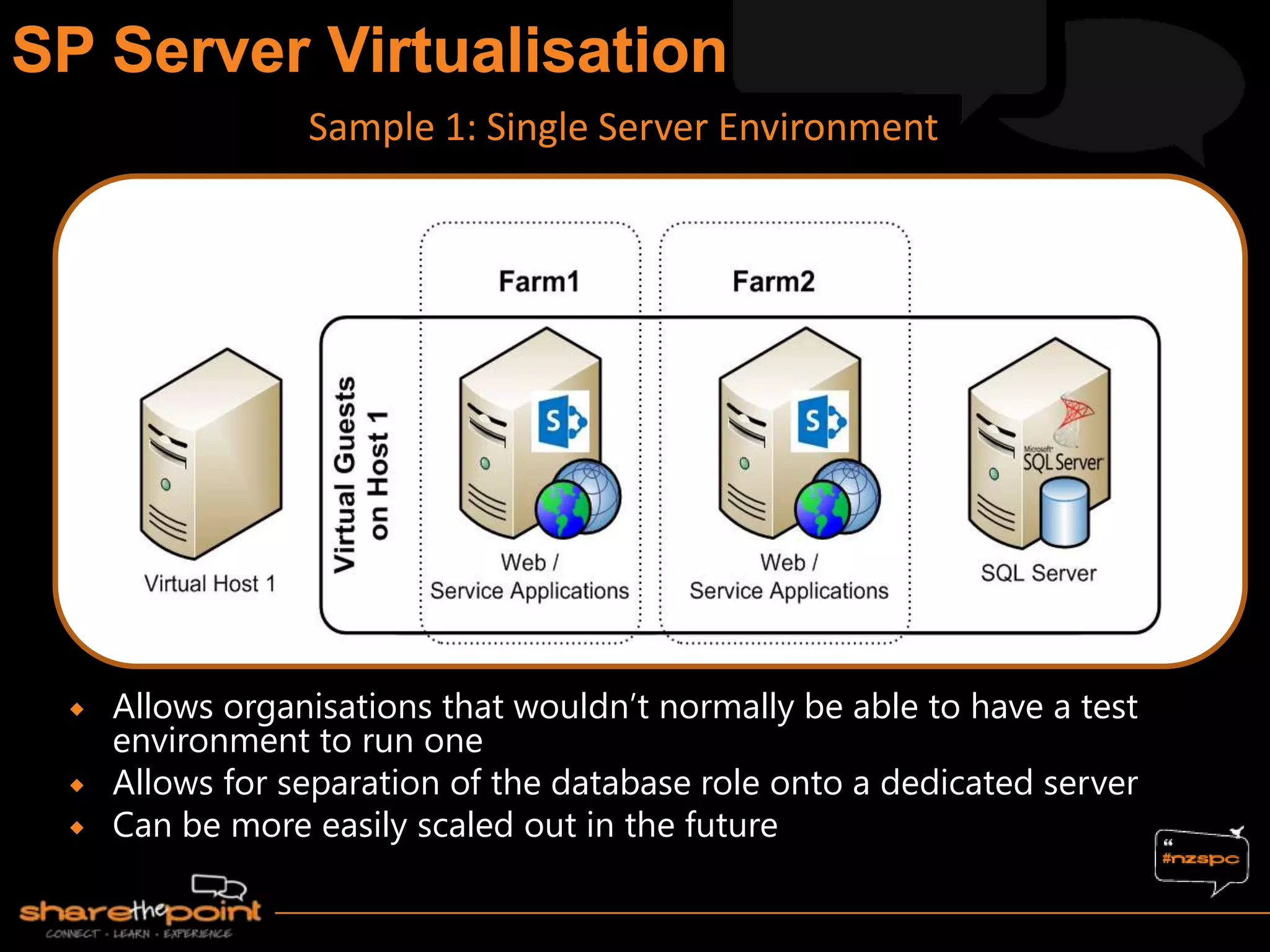
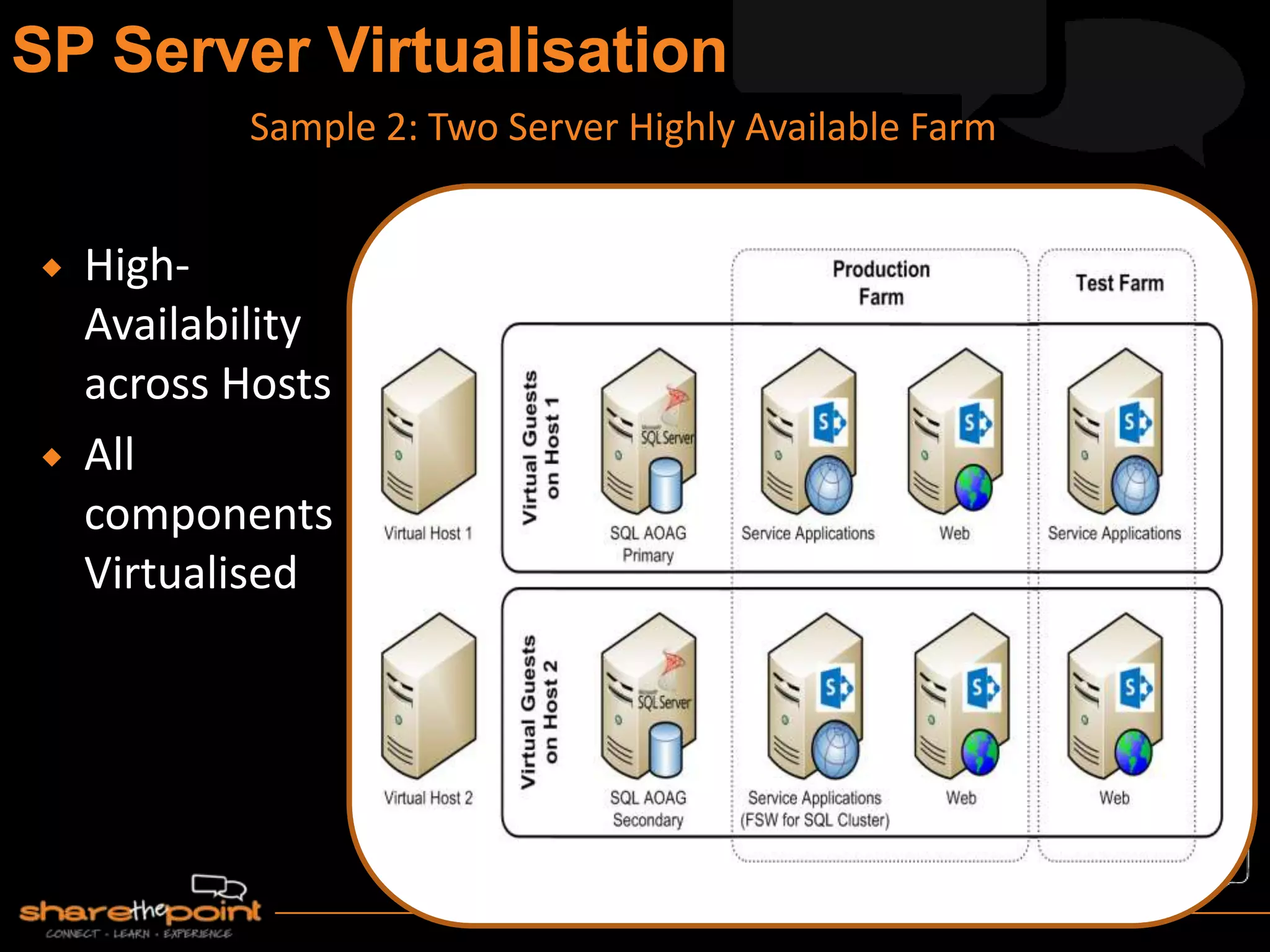
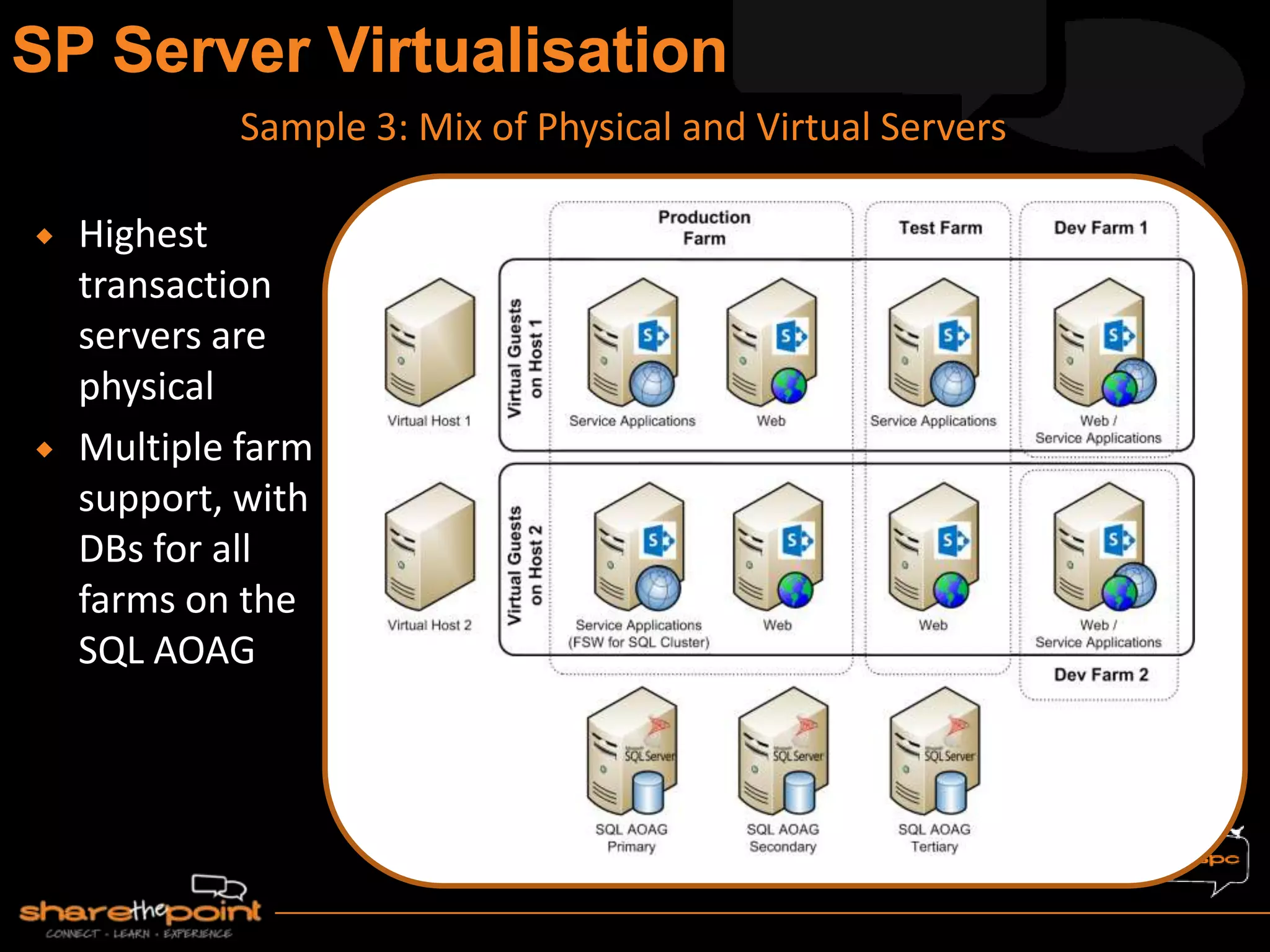
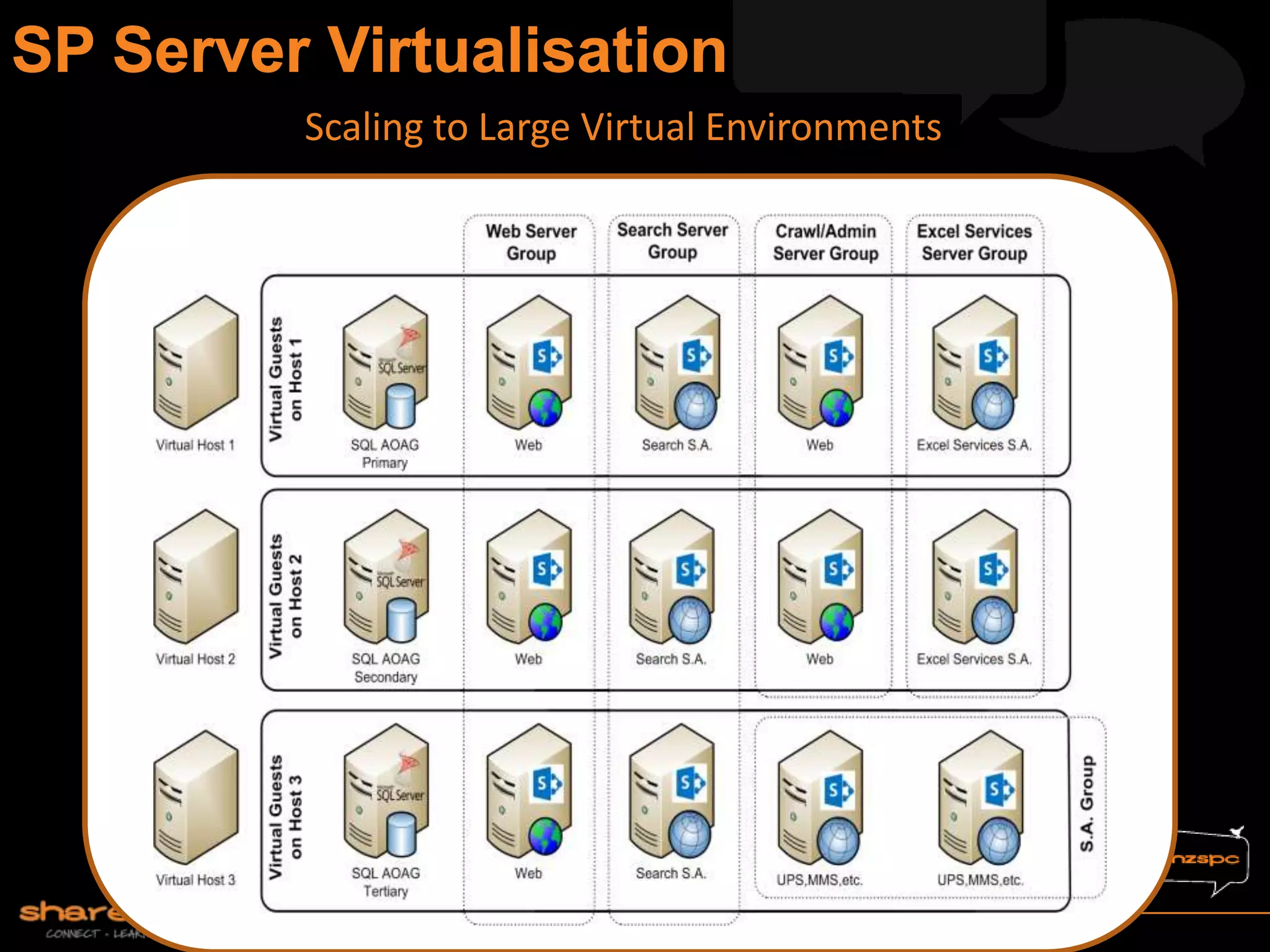
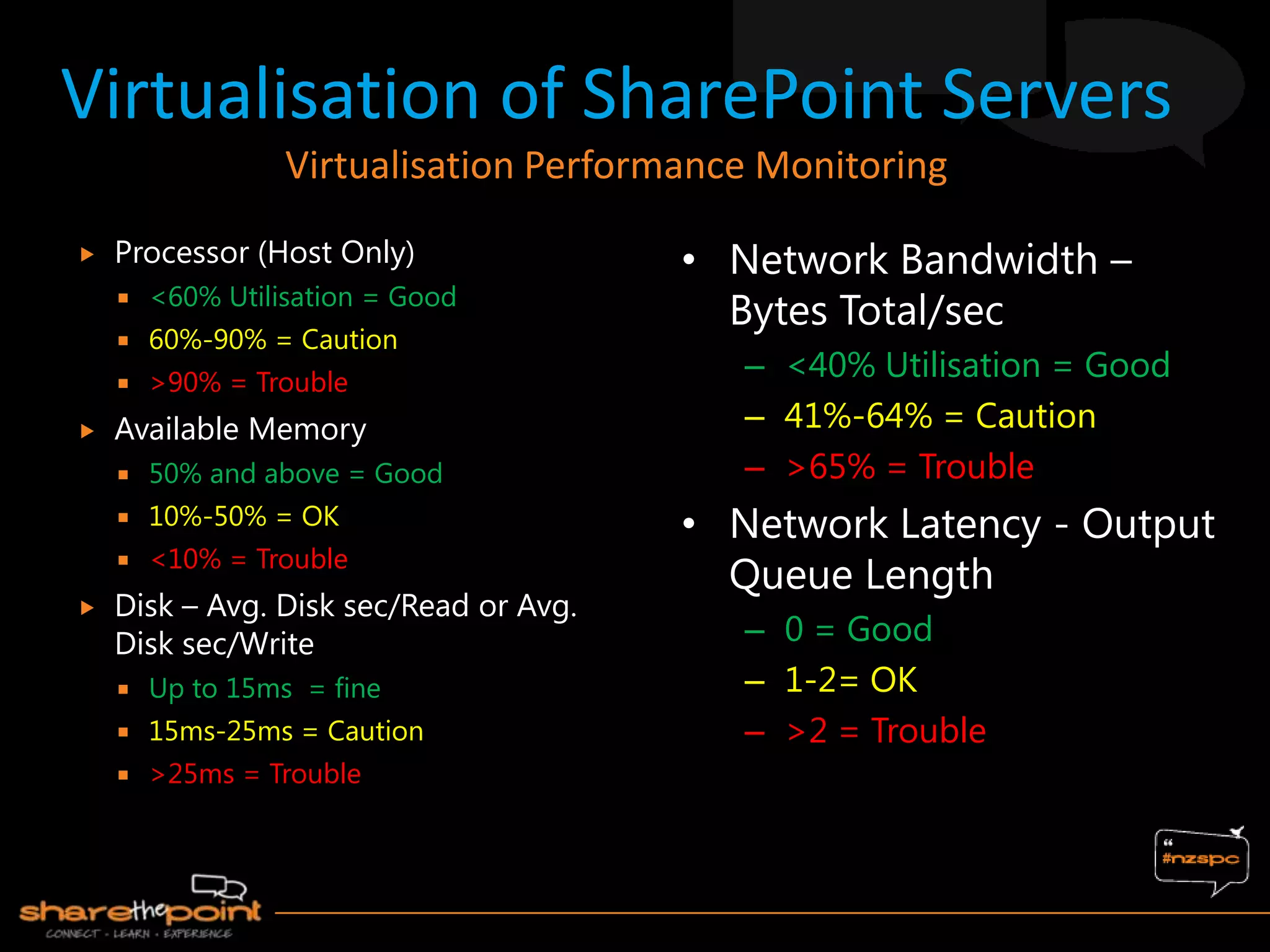
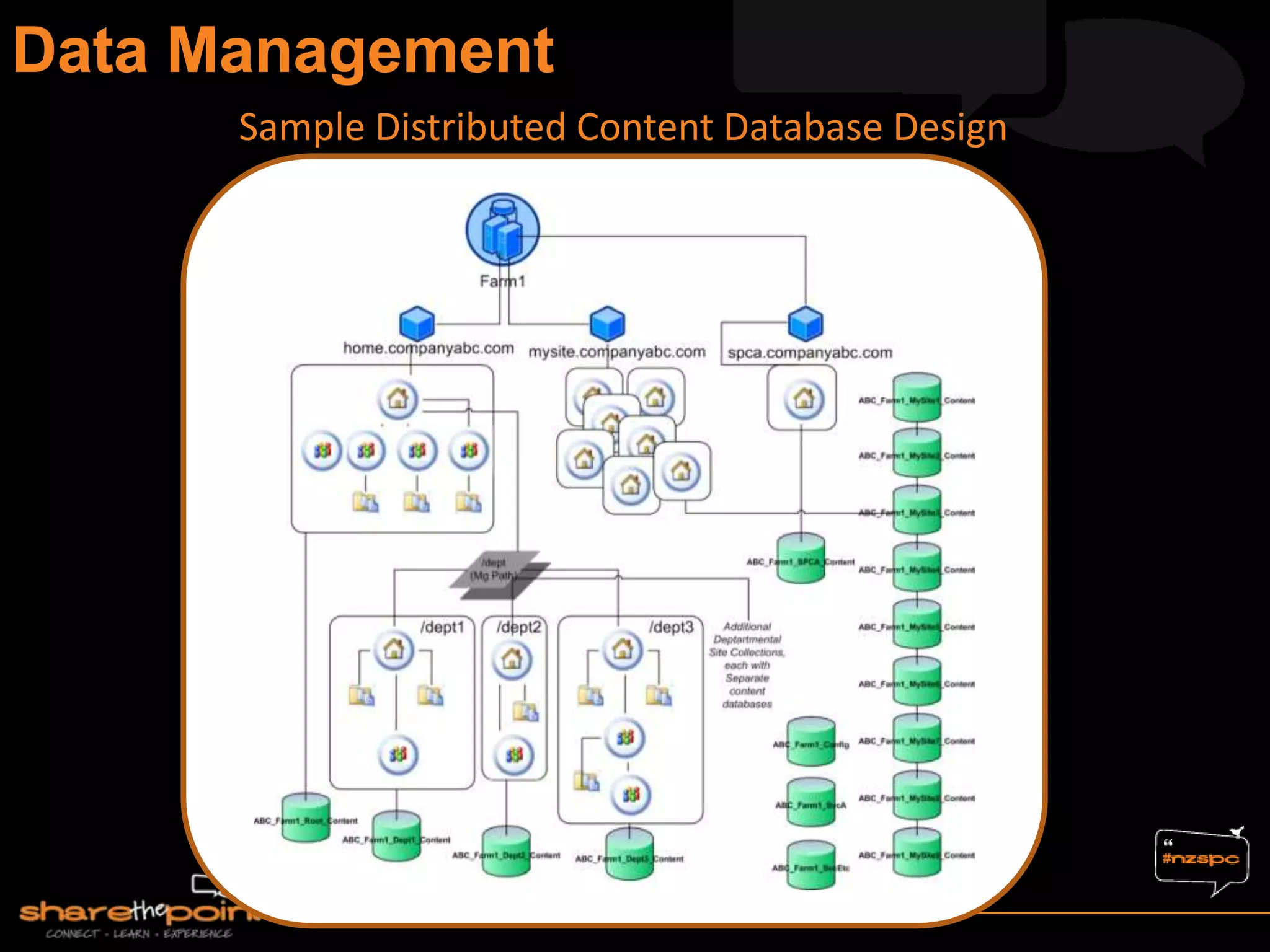
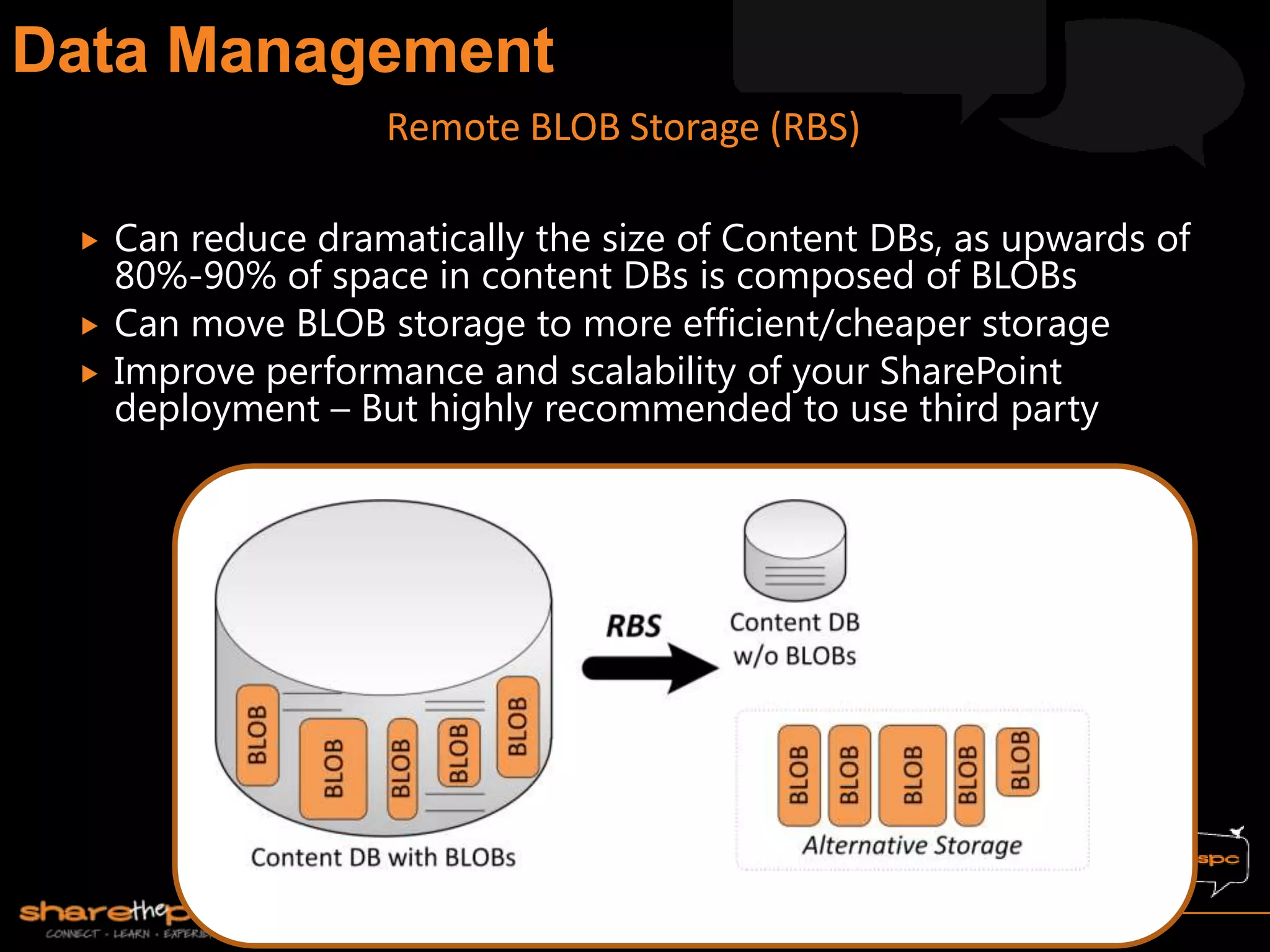
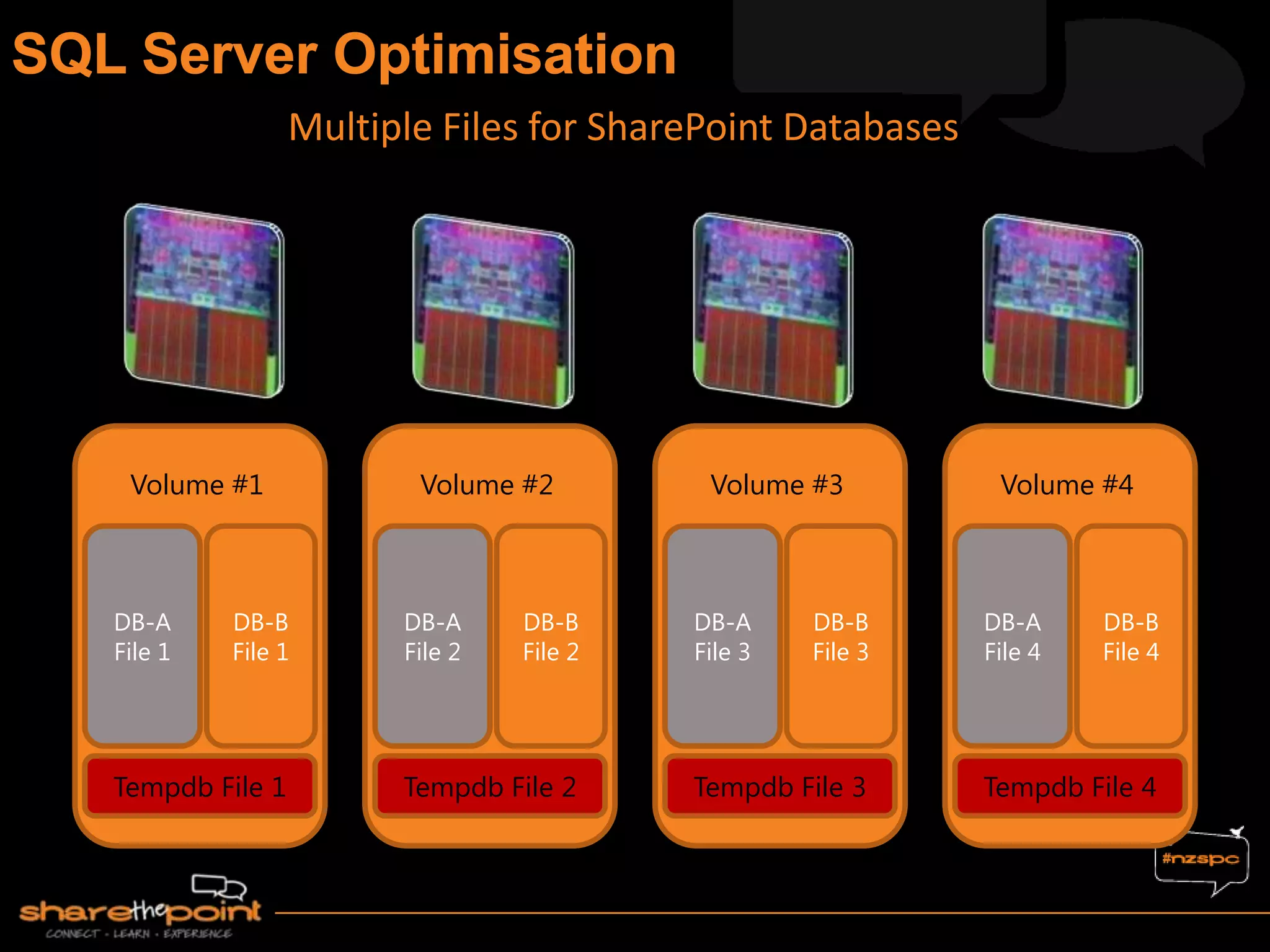
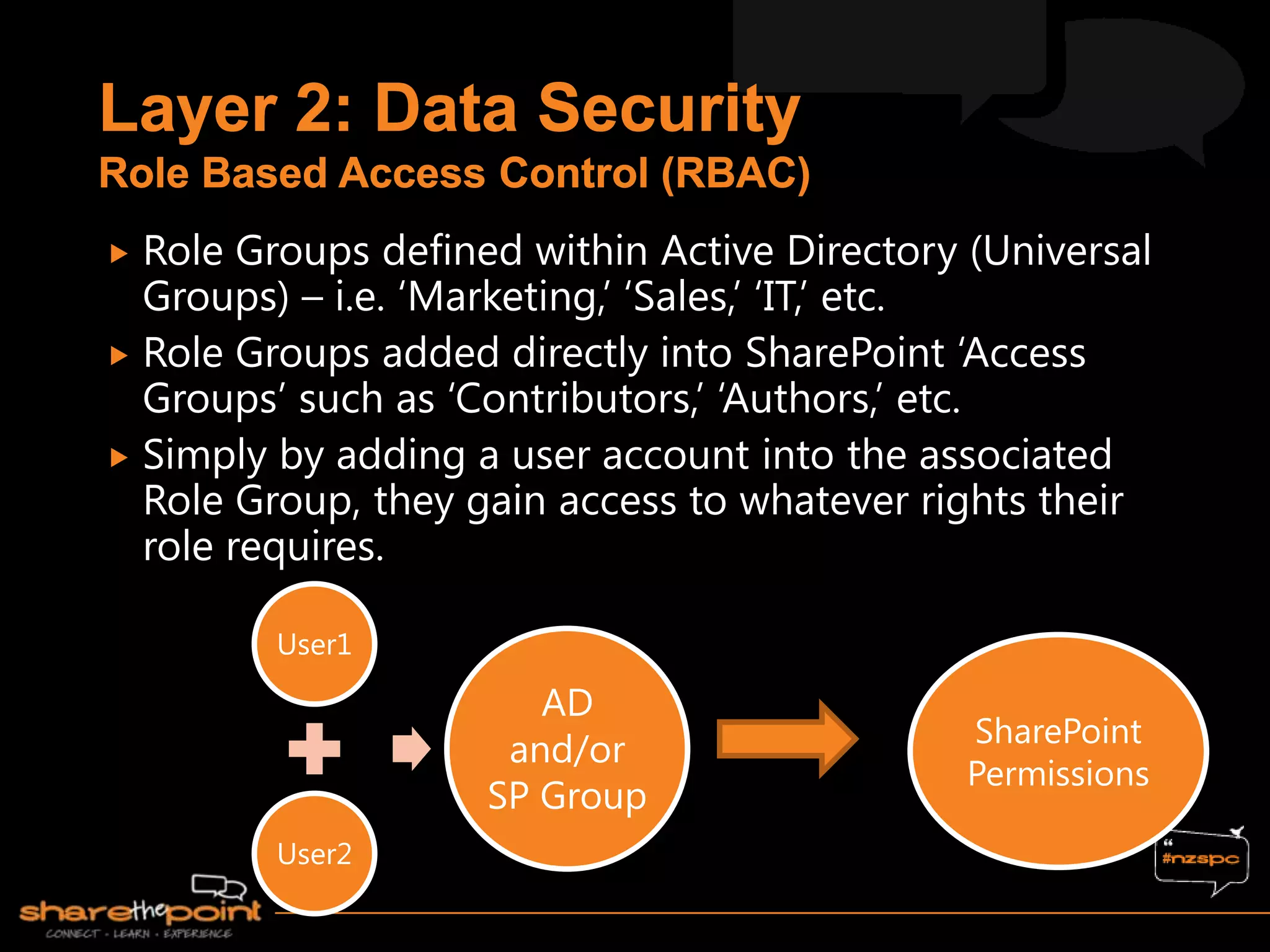
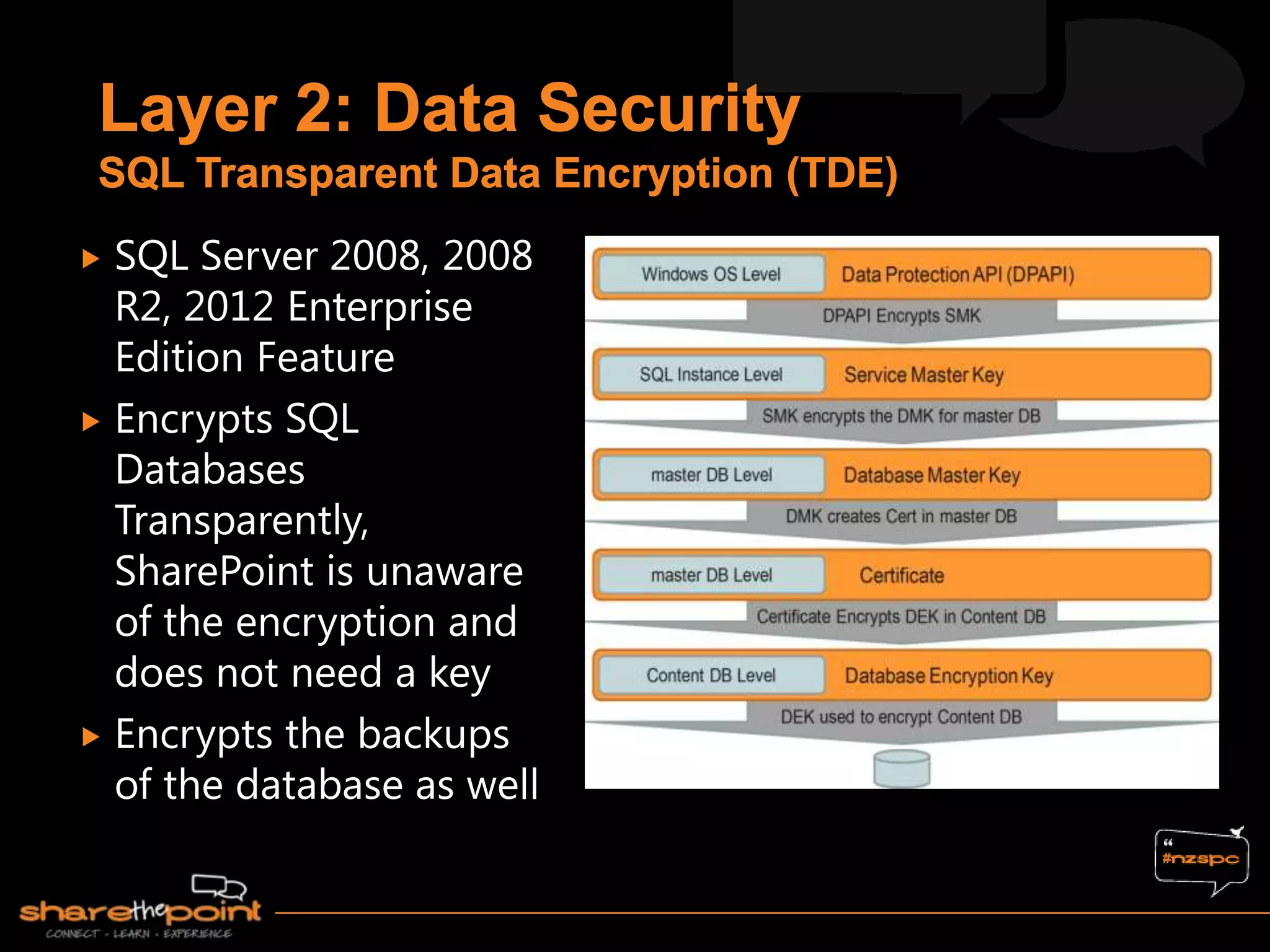
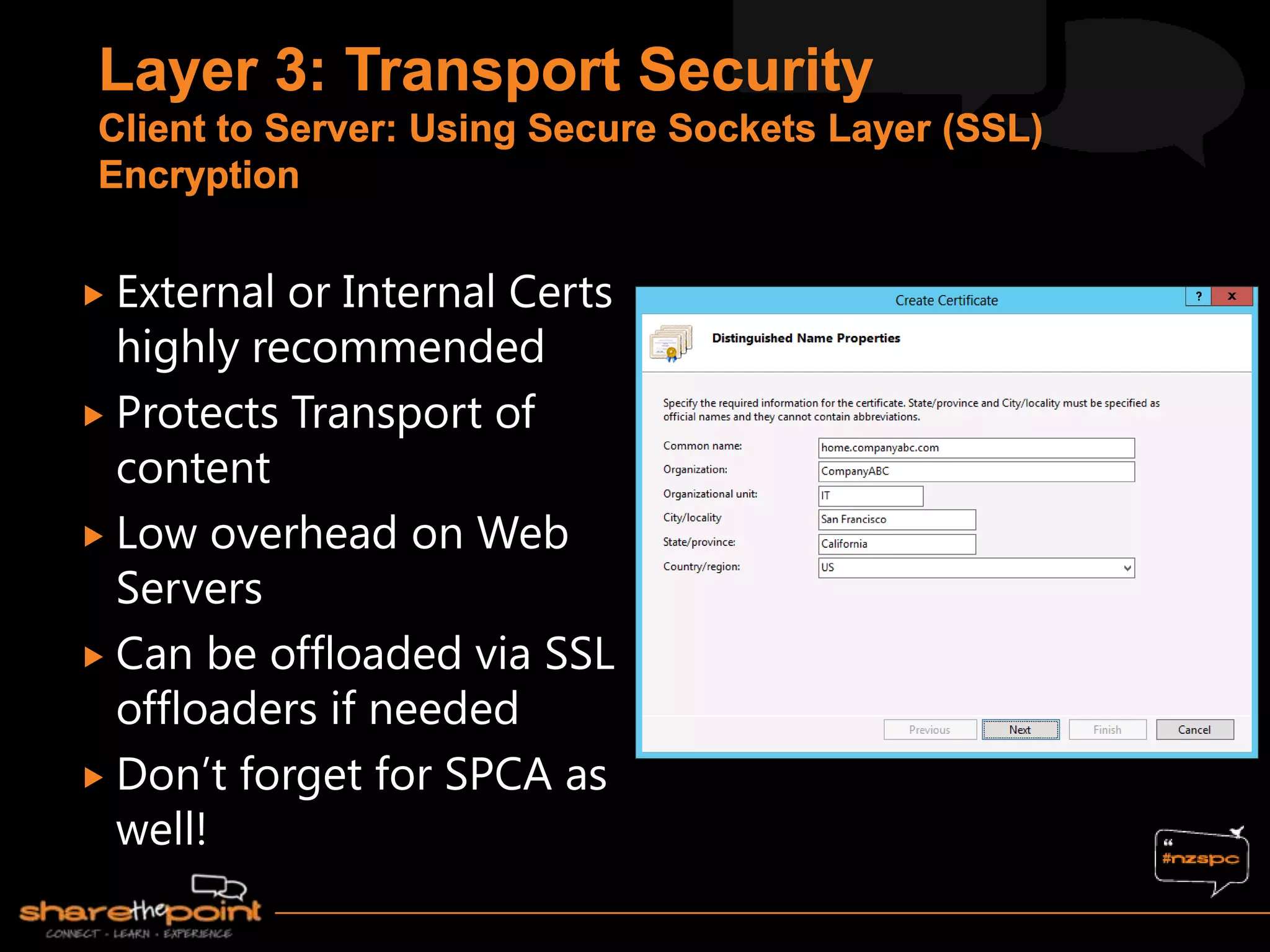
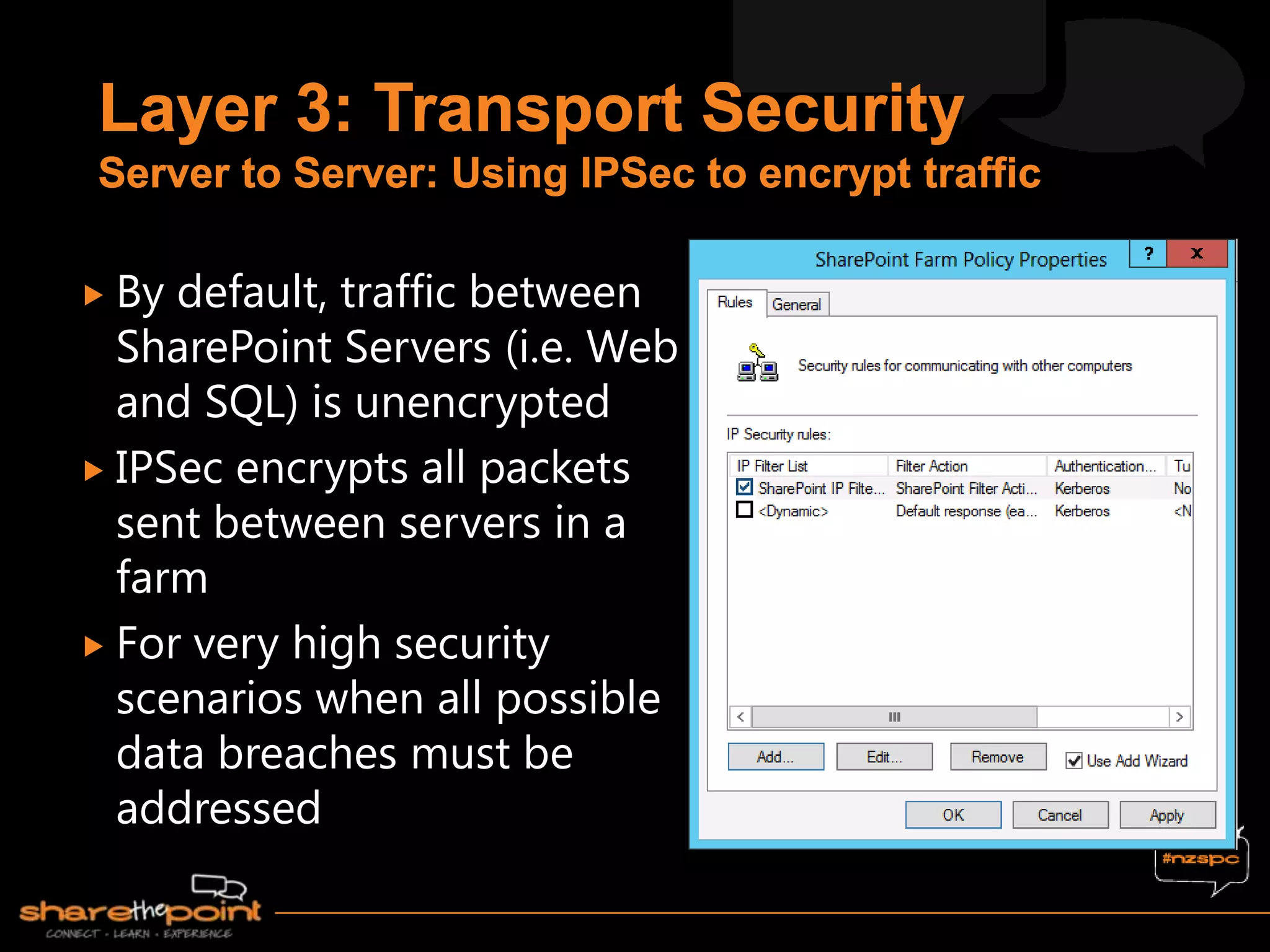
Michael Noel is the author of 19 technical books on Microsoft technologies that have sold over 300,000 copies. He is a partner at Convergent Computing, an infrastructure and security consulting firm. The document provides hardware and software requirements for SharePoint 2013 environments, including recommended memory, processors, and editions of Windows Server and SQL Server. It also summarizes new features in SharePoint 2013 like the distributed cache service, request management, and claims-based authentication.