Information System Sensitivity Level Impact Assessment (NIST SP 800-60v2r1)
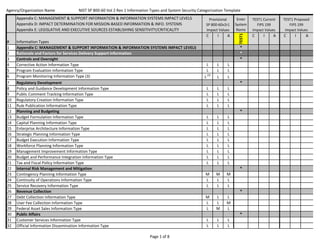
- 1. Information System Name: _________________________________ Official Use Only (When Filled) National Security (N/S) Information Out of Scope IMPACT ASSESSMENT (Determines the Sensitivity Level of an Information System/Information Type) Sensitivity Level of Information System (IS)/Information Type (Perceived impact from the loss to the three fundamental security attributes of information: confidentiality, integrity and availability. Impact Value Highest Water Mark: Current = BLANK; Proposed = BLANK Information Types Provisional View SP 800‐60v2r1 Impact Values Headers Enter System Name <‐‐‐‐‐‐‐ C I A * Appendix C: Management & Support Information & Information Systems Impact Levels I A C I A * Controls and Oversight C System Name Proposed FIPS 199 Impact Values * Rationale and Factors for Services Delivery Support Information System Name Current FIPS 199 Impact Values * Corrective Action Information Type L L L Program Evaluation Information Type L L L L (3) L L Program Monitoring Information Type (3) Regulatory Development * Policy and Guidance Development Information Type L L L Public Comment Tracking Information Type L L L Regulatory Creation Information Type L L L Rule Publication Information Type L L L Planning and Budgeting * Budget Formulation Information Type L L L Capital Planning Information Type L L L Enterprise Architecture Information Type L L L Strategic Planning Information Type L L L Budget Execution Information Type L L L Workforce Planning Information Type L L L Management Improvement Information Type L L L Budget and Performance Integration Information Type L L L Tax and Fiscal Policy Information Type L L L Internal Risk Management and Mitigation * Contingency Planning Information Type M M M Continuity of Operations Information Type M M M Service Recovery Information Type L L L Revenue Collection * Debt Collection Information Type M L L User Fee Collection Information Type L L M Federal Asset Sales Information Type L M L Public Affairs * Customer Services Information Type L L L Official Information Dissemination Information Type L L L Print Date: 2/19/2014 Page 1 of 8 Contact: James W. De Rienzo
- 2. Information System Name: _________________________________ Official Use Only (When Filled) National Security (N/S) Information Out of Scope IMPACT ASSESSMENT (Determines the Sensitivity Level of an Information System/Information Type) Sensitivity Level of Information System (IS)/Information Type (Perceived impact from the loss to the three fundamental security attributes of information: confidentiality, integrity and availability. Impact Value Highest Water Mark: Current = BLANK; Proposed = BLANK Information Types Provisional View SP 800‐60v2r1 Impact Values Headers Enter System Name <‐‐‐‐‐‐‐ C I A * Product Outreach Information Type L L L L C I A System Name Proposed FIPS 199 Impact Values C I A L Public Relations Information Type System Name Current FIPS 199 Impact Values L Legislative Relations * Legislation Tracking Information Type L L L Legislation Testimony Information Type L L L Proposal Development Information Type M L L Congressional Liaison Operations Information Type M L L General Government * Central Fiscal Operations Information Type (4) M L L Legislative Functions Information Type L L L Executive Functions Information Type (5) L L L Central Property Management Information Type L (6) L L (7) Central Personnel Management Information Type L L L Taxation Management Information Type M L L Central Records and Statistics Management Information Type M L L Income Information Information Type (8) M M M Personal Identity and Authentication Information Information Type (8) M M M Entitlement Event Information Information Type (8) M M M Representative Payee Information Information Type (8) M M M General Information Information Type (9) L L L Notification of Finding Report Information (General Information Information Type ‐ [9]) L L L Memoranda and Guidelines (General Information Information Type ‐ [9]) L L L Presidential Directives & Executive Orders (General Information Information Type ‐ [9]) L L L Other Executive Office of the President Guidance (General Information Information Type ‐ [9]) L L L Rationale and Factors for Government Resource Management Information * Administrative Management * L (6) L (7) L (7) Facilities, Fleet, and Equipment Management Information Type Help Desk Services Information Type L L L Security Management Information Type M M L Travel Information Type L L L Workplace Policy Development and Management Information Type (Intra‐Agency Only) L L L Financial Management Print Date: 2/19/2014 * Page 2 of 8 Contact: James W. De Rienzo
- 3. Information System Name: _________________________________ Official Use Only (When Filled) National Security (N/S) Information Out of Scope IMPACT ASSESSMENT (Determines the Sensitivity Level of an Information System/Information Type) Sensitivity Level of Information System (IS)/Information Type (Perceived impact from the loss to the three fundamental security attributes of information: confidentiality, integrity and availability. Impact Value Highest Water Mark: Current = BLANK; Proposed = BLANK Information Types Provisional View SP 800‐60v2r1 Impact Values Headers Enter System Name <‐‐‐‐‐‐‐ C I A * Assets and Liability Management Information Type L L L M M M L M L M L M L M A L Cost Accounting/ Performance Measurement Information Type I L Collections and Receivables Information Type C L Payments Information Type A L Accounting Information Type I L Funds Control Information Type C System Name Proposed FIPS 199 Impact Values L Reporting and Information Information Type System Name Current FIPS 199 Impact Values L Human Resource Management * HR Strategy Information Type L L L Staff Acquisition Information Type L L L Organization & Position Management Information Type L L L Compensation Management Information Type L L L Benefits Management Information Type L L L Employee Performance Management Information Type L L L Employee Relations Information Type L L L Labor Relations Information Type L L L Separation Management Information Type L L L Human Resources Development Information Type L L L Supply Chain Management * Goods Acquisition Information Type L L L Inventory Control Information Type L L L Logistics Management Information Type L L L Services Acquisition Information Type L L L Information and Technology Management * System Development Information Type L M L Lifecycle/Change Management Information Type L M L System Maintenance Information Type L M L IT Infrastructure Maintenance Information Type (10) L L L Information Security Information Type L M L Record Retention Information Type L L L Information Management Information Type (11) L M L System and Network Monitoring Information Type M M L Print Date: 2/19/2014 Page 3 of 8 Contact: James W. De Rienzo
- 4. Information System Name: _________________________________ Official Use Only (When Filled) National Security (N/S) Information Out of Scope IMPACT ASSESSMENT (Determines the Sensitivity Level of an Information System/Information Type) Sensitivity Level of Information System (IS)/Information Type (Perceived impact from the loss to the three fundamental security attributes of information: confidentiality, integrity and availability. Impact Value Highest Water Mark: Current = BLANK; Proposed = BLANK Information Types Provisional View SP 800‐60v2r1 Impact Values Headers Enter System Name <‐‐‐‐‐‐‐ C Information Sharing Information Type I A * System Name Current FIPS 199 Impact Values C I A System Name Proposed FIPS 199 Impact Values C I A N/A N/A N/A Appendix D: Impact Determination for Mission‐Based Information & Infomation Systems * Defense and National Security * N/S N/S N/S Homeland Security * Border and Transportation Security Information Type M M M Key Asset and Critical Infrastructure Protection Information Type H H H Catastrophic Defense Information Type H H H Executive Functions of the Executive Office of the President (EOP) Information Type (23) H M H Intelligence Operations (24) N/S N/S N/S Disaster Management * * Disaster Monitoring and Prediction Information Type L H H Disaster Preparedness and Planning Information Type L L L Disaster Repair and Restoration Information Type L L L Emergency Response Information Type L H H International Affairs and Commerce * Foreign Affairs Information Type H H M International Development and Humanitarian Aid Information Type M L L Global Trade Information Type H H H Natural Resources * Water Resource Management Information Type L L L Conservation, Marine and Land Management Information Type L L L Recreational Resource Management and Tourism Information Type L L L Agricultural Innovation and Services Information Type L L L Energy * L(25) M(26) M(26) Energy Supply Information Type Energy Conservation and Preparedness Information Type L L L Energy Resource Management Information Type M L L Energy Production Information Type L L L Environmental Management * Environmental Monitoring and Forecasting Information Type L M L Environmental Remediation Information Type M L L Pollution Prevention and Control Information Type L L L Print Date: 2/19/2014 Page 4 of 8 Contact: James W. De Rienzo
- 5. Information System Name: _________________________________ Official Use Only (When Filled) National Security (N/S) Information Out of Scope IMPACT ASSESSMENT (Determines the Sensitivity Level of an Information System/Information Type) Sensitivity Level of Information System (IS)/Information Type (Perceived impact from the loss to the three fundamental security attributes of information: confidentiality, integrity and availability. Impact Value Highest Water Mark: Current = BLANK; Proposed = BLANK Information Types Provisional View SP 800‐60v2r1 Impact Values Headers Enter System Name <‐‐‐‐‐‐‐ C I A * Economic Development System Name Current FIPS 199 Impact Values C I A System Name Proposed FIPS 199 Impact Values C I A * Business and Industry Development Information Type L L L Intellectual Property Protection Information Type L L L Financial Sector Oversight Information Type M L L Industry Sector Income Stabilization Information Type M L L Community and Social Services * Homeownership Promotion Information Type L L L Community and Regional Development Information Type L L L Social Services Information Type L L L Postal Services Information Type L M M Transportation * Ground Transportation Information Type L L L Water Transportation Information Type L L L Air Transportation Information Type L L L Space Operations Information Type L H H Education * Elementary, Secondary, and Vocational Education Information Type L L L Higher Education Information Type L L L Cultural and Historic Preservation Information Type L L L Cultural and Historic Exhibition Information Type L L L Workforce Management * Training and Employment Information Type L L L Labor Rights Management Information Type L L L Worker Safety Information Type L L L Health * Access to Care Information Type L M L Population Health Management and Consumer Safety Information Type L M L Health Care Administration Information Type L M L Health Care Delivery Services Information Type L H L Health Care Research and Practitioner Education Information Type L M L Income Security * General Retirement and Disability Information Type Print Date: 2/19/2014 M Page 5 of 8 M M Contact: James W. De Rienzo
- 6. Information System Name: _________________________________ Official Use Only (When Filled) National Security (N/S) Information Out of Scope IMPACT ASSESSMENT (Determines the Sensitivity Level of an Information System/Information Type) Sensitivity Level of Information System (IS)/Information Type (Perceived impact from the loss to the three fundamental security attributes of information: confidentiality, integrity and availability. Impact Value Highest Water Mark: Current = BLANK; Proposed = BLANK Information Types Provisional View SP 800‐60v2r1 Impact Values Headers Enter System Name <‐‐‐‐‐‐‐ C I A * Unemployment Compensation Information Type L L L L L L L L A C I A L Survivor Compensation Information Type I L Food and Nutrition Assistance Information Type C System Name Proposed FIPS 199 Impact Values L Housing Assistance Information Type System Name Current FIPS 199 Impact Values L Law Enforcement * Criminal Apprehension Information Type L L M Criminal Investigation and Surveillance Information Type M M M Citizen Protection Information Type M M M Leadership Protection Information Type M L L Property Protection Information Type L L L Substance Control Information Type M M M Crime Prevention Information Type L L L Trade Law Enforcement Information Type (27) M M M Litigation and Judicial Activities * Judicial Hearings Information Type M L L Legal Defense Information Type M H L Legal Investigation Information Type M M M Legal Prosecution and Litigation Information Type L M L Resolution Facilitation Information Type M L L Federal Correctional Activities * Criminal Incarceration Information Type L M L Criminal Rehabilitation Information Type L L L General Sciences and Innovation * Scientific and Technological Research and Innovation Information Type L M L Space Exploration and Innovation Information Type L M L Knowledge Creation and Management * Research and Development Information Type L M L General Purpose Data and Statistics Information Type L L L Advising and Consulting Information Type L L L Knowledge Dissemination Information Type L L L Regulatory Compliance and Enforcement * Inspections and Auditing Information Type Print Date: 2/19/2014 M Page 6 of 8 M L Contact: James W. De Rienzo
- 7. Information System Name: _________________________________ Official Use Only (When Filled) National Security (N/S) Information Out of Scope IMPACT ASSESSMENT (Determines the Sensitivity Level of an Information System/Information Type) Sensitivity Level of Information System (IS)/Information Type (Perceived impact from the loss to the three fundamental security attributes of information: confidentiality, integrity and availability. Impact Value Highest Water Mark: Current = BLANK; Proposed = BLANK Information Types Provisional View SP 800‐60v2r1 Impact Values Headers Enter System Name <‐‐‐‐‐‐‐ C I A * Standards Setting/Reporting Guideline Development Information Type L L L L C I A System Name Proposed FIPS 199 Impact Values C I A L Permits and Licensing Information Type System Name Current FIPS 199 Impact Values L Public Goods Creation and Management * Manufacturing Information Type L L L Construction Information Type L L L Public Resources, Facility and Infrastructure Management Information Type L L L Information Infrastructure Management Information Type L L L Federal Financial Assistance * Federal Grants (Non‐State) Information Type L L L Direct Transfers to Individuals Information Type L L L Subsidies Information Type L L L Tax Credits Information Type M L L Credit and Insurance * Direct Loans Information Type L L L Loan Guarantees Information Type L L L General Insurance Information Type L L L Transfers to State/Local Governments * Formula Grants Information Type L L L Project/Competitive Grants Information Type L L L Earmarked Grants Information Type L L L State Loans Information Type L L L Direct Services for Citizens * Military Operations Information Type (28) N/A N/A N/A Civilian Operations Information Type (28) N/A N/A N/A APPENDIX E: Legislative & Executive & Executive Sources Establishing Sensitivity/Criticality * Legislative Mandates * Executive Mandates * Office of Management and Budget Memoranda and Guidelines * Presidential Directives and Executive Orders * Other EOP Guidance * OMB and Case Law Interpretations * Print Date: 2/19/2014 Page 7 of 8 Contact: James W. De Rienzo
- 8. Information System Name: _________________________________ Official Use Only (When Filled) National Security (N/S) Information Out of Scope IMPACT ASSESSMENT (Determines the Sensitivity Level of an Information System/Information Type) Sensitivity Level of Information System (IS)/Information Type (Perceived impact from the loss to the three fundamental security attributes of information: confidentiality, integrity and availability. Impact Value Highest Water Mark: Current = BLANK; Proposed = BLANK Information Types Provisional View SP 800‐60v2r1 Impact Values Headers Enter System Name <‐‐‐‐‐‐‐ C I A * System Name Current FIPS 199 Impact Values C I A System Name Proposed FIPS 199 Impact Values C I A 3 The confidentiality impact assigned to the Program Monitoring Information Type may necessitate the highest confidentiality impact of the information types processed by the system. 4 Tax‐related functions are associated with the Taxation Management information type. 5 The OMB Business Reference Model “Executive Function has been expanded to include general agency executive functions as well as Executive Office of the President (EOP) functions. Strictly EOP executive functions are treated in Appendix D, Examples of Impact Determination for Mission‐Based Information and Information Systems. 6 High where safety of major critical infrastructure components or key national assets is at stake. 7 Moderate or High in emergency situations where time‐critical processes affecting human safety or major assets are involved. 8 The identified information types are not a derivative of OMB’s Business Reference Model and were added to address privacy information. 9 The OMB Business Reference Model does not include a General Information information type. This information type was added as a catch‐all information type. As such, agencies may use this to identify additional information types not defined in the BRM and assign impact levels. 10 The confidentiality impact assigned to the IT Infrastructure Maintenance Information Type may necessitate the highest confidentiality impact of the information types processed by the system. 11 The confidentiality impact assigned to the Information Management Information Type may necessitate the highest confidentiality impact of the information types processed by the system. 20 Impact level is usually moderate to high in emergency situations where time‐critical processes affecting human safety or major assets are involved. 21 A loss of confidentiality that causes a significant degradation in mission capability, places the agency at a significant disadvantage, or results in major damage to assets, requiring extensive corrective actions or repairs. 23 The identified information types are not a derivative of OMB’s Business Reference Model and were added to address functions of the Executive Office of the President (EOP). 24 Where foreign intelligence information is involved, the information and information systems are categorized as national security information or systems and are outside the scope of this guideline. 25 High where safety of radioactive materials, highly flammable fuels, or transmission channels or control processes at risk. 26 Usually Moderate or High where mission‐critical procedures are involved. 27 The identified information types are not a derivative of OMB’s Business Reference Model and were added to address trade law enforcement. 28 As mode of delivery of mission‐based services, the security categorization of Direct Services to Citizens sub‐functions Military Operations and Civilian Operation is dependent on the mission services delivered to the citizens [e.g., Health Care; Emergency Response, Environmental Remediation] should be categorized in accordance with the mission‐based information type. Print Date: 2/19/2014 Page 8 of 8 Contact: James W. De Rienzo
