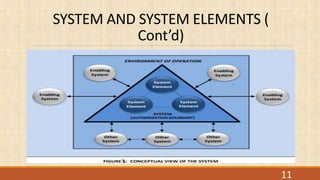
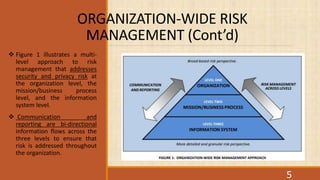
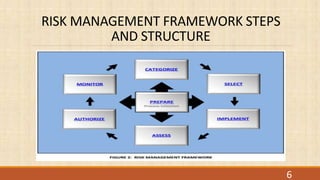
This document provides an overview of NIST Special Publication 800-37, which outlines the Risk Management Framework (RMF) for federal agencies. The RMF is a cyclical process for assessing and managing risk to systems and organizations on an ongoing basis. It includes seven steps: (1) prepare the organization; (2) categorize systems and data; (3) select controls; (4) implement controls; (5) assess controls; (6) authorize systems; and (7) monitor systems. The RMF takes a system lifecycle approach and requires coordination between information security and privacy programs to effectively manage risk.





![INFORMATION SECURITY AND PRIVACY
IN THE RMF (Cont’d)
[OMB A-130] defines a privacy control as an administrative, technical, or physical safeguard
employed within an agency to ensure compliance with applicable privacy requirements and to
manage privacy risks.
A privacy control is different from a security control, which the Circular defines as a safeguard
or countermeasure prescribed for an information system or an organization to protect the
confidentiality, integrity, and availability of the system and its information.
9](https://image.slidesharecdn.com/800-37-230425133703-3064d4e2/85/800-37-pptx-9-320.jpg)