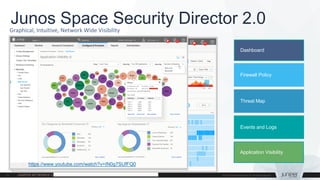
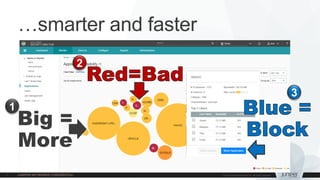
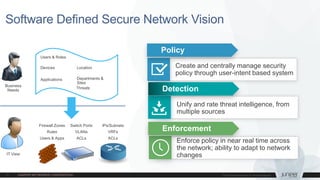
The document provides information on Juniper SRX platform updates, including:
1) vSRX updates - The virtual firewall platform now supports up to 80G FW throughput on a single server and 100G vSRX was announced. Support for VMware 5.5+SRIOV and features parity with physical SRX firewalls.
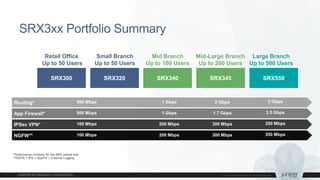
2) Physical SRX updates - New SRX3xx and SRX550 series for branches up to 500 users. The SRX1500 provides high performance networking and security for enterprise edge and data center edge. The SRX5400 supports advanced software security services.
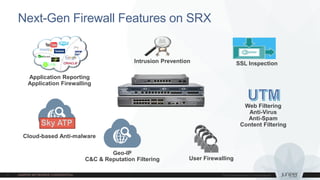
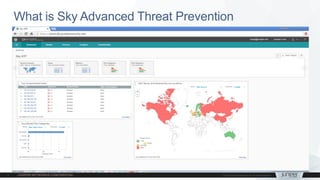
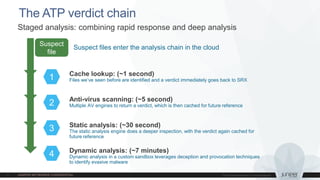
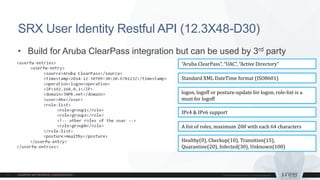
3) Software updates - Sky ATP cloud-based malware analysis and SRX User Identity REST API.











![SSL Forward Proxy and UTM
• 12.3X48-D25 and 15.1X49-D40 support UTM with SSL Proxy
• No configuration changes on UTM side. A ssl-proxy profile must be
applied
[…]policy trust-to-untrust match source-address any
[…]policy trust-to-untrust match destination-address any
[…]policy trust-to-untrust match application junos-any
[…]policy trust-to-untrust then permit application-services ssl-proxy profile-name ssl-inspection-p
[…]policy trust-to-untrust then permit application-services utm-policy junos-av-policy
[…]policy trust-to-untrust then permit application-services application-firewall rule-set block-app
[…]policy trust-to-untrust then log session-close](https://image.slidesharecdn.com/3junipersecurityreloadedhendrych-160601154025/85/Next-Generation-Security-Solution-17-320.jpg)