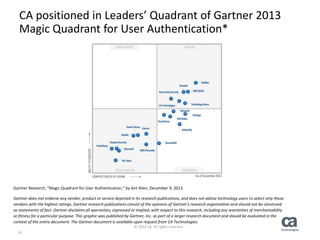
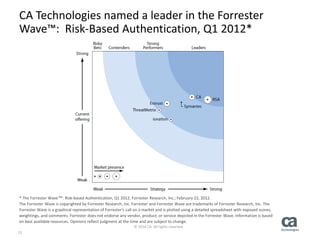
The document discusses the importance of strong and risk-based authentication in protecting user identities from increased online attacks and data breaches. It outlines various challenges with traditional authentication methods and introduces multi-factor and risk-based authentication as more secure alternatives. Additionally, CA Technologies offers a combined solution that enhances security and complies with industry regulations.