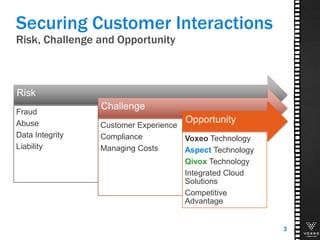
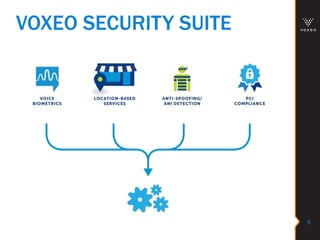
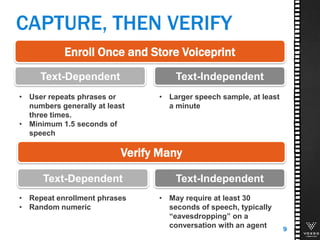
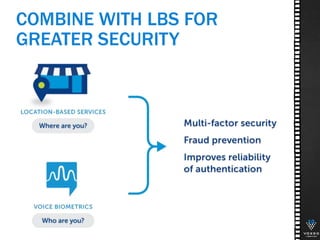
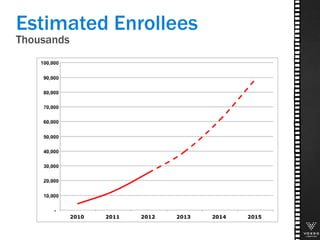
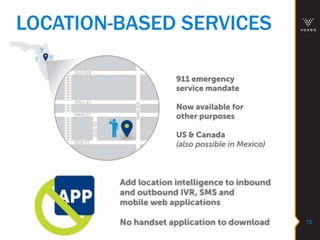
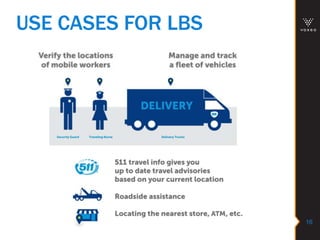
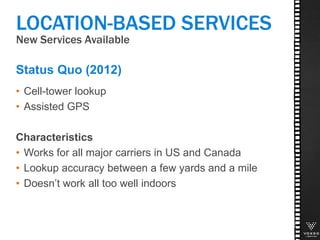
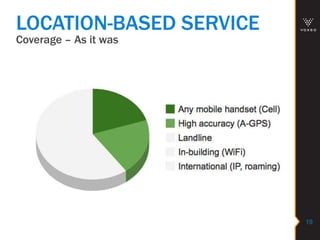
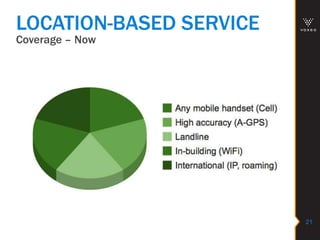
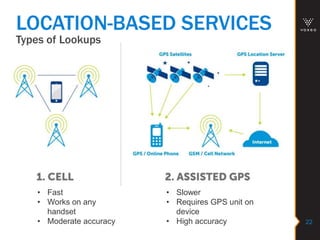
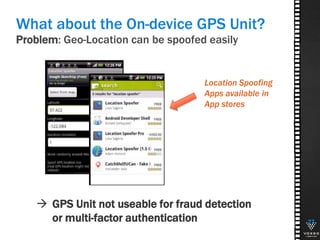
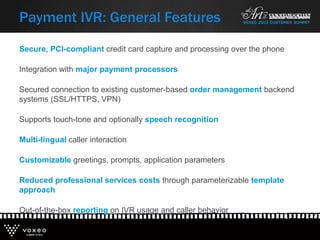
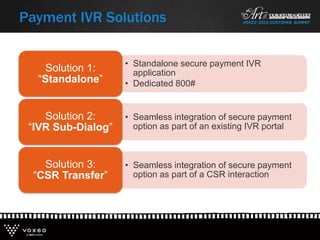
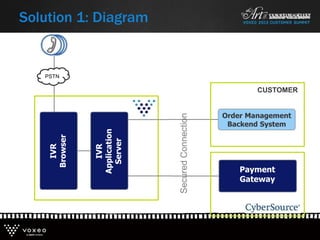
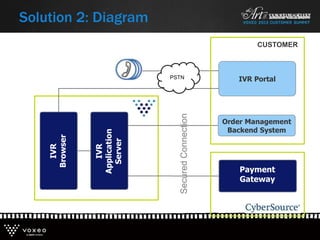
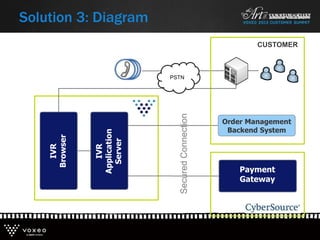
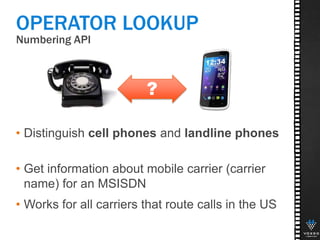
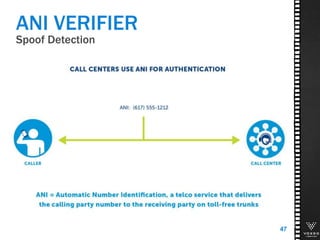
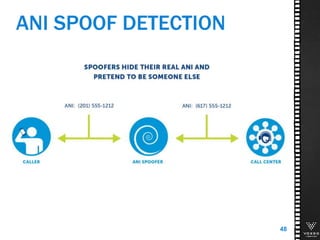
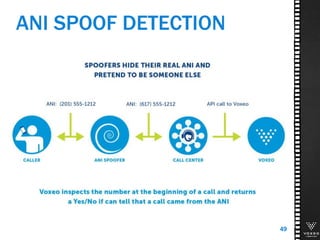
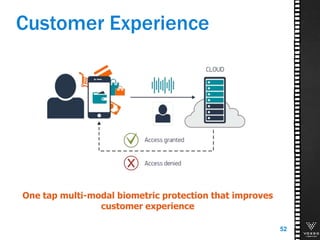
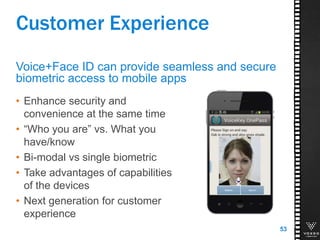
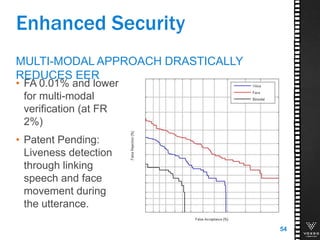
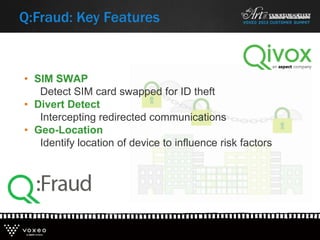
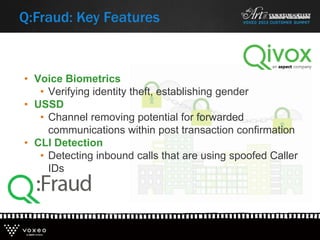
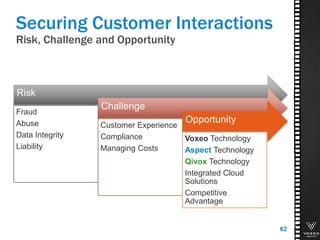
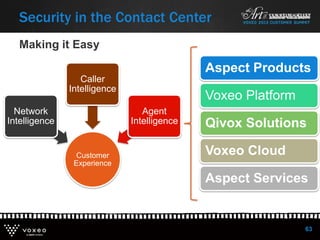
This document discusses various technologies for securing customer interactions, including voice biometrics, location-based services, payment processing, and operator lookup. It notes that fraud costs over $200 billion annually and contact centers spend over $12 billion on security. Voice biometrics can identify customers by their voiceprint and location-based services provide additional authentication through mobile device location. Payment processing allows secure credit card transactions via IVR or with agents. Operator lookup verifies phone numbers to reduce spoofing. When combined with Aspect and Qivox technologies, these solutions provide comprehensive security across the contact center.