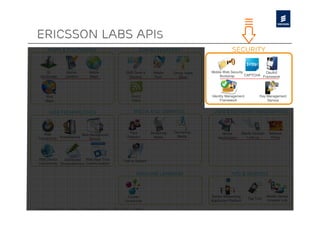
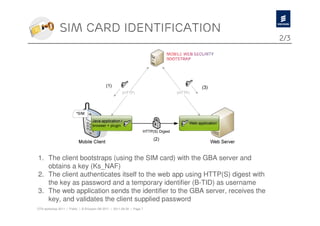
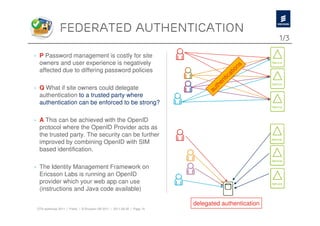
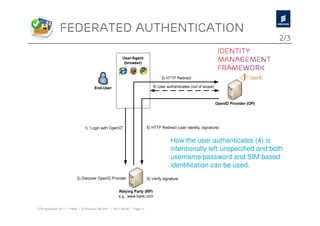
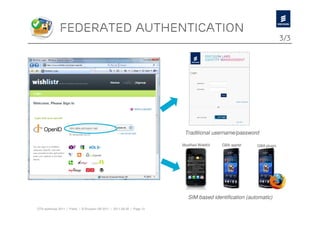
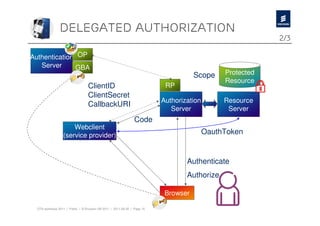
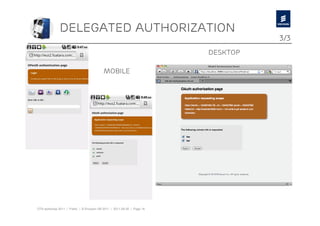
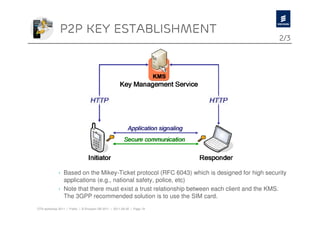
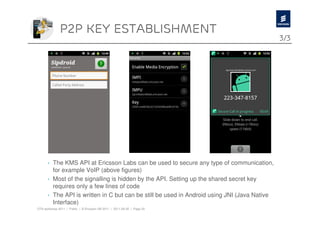
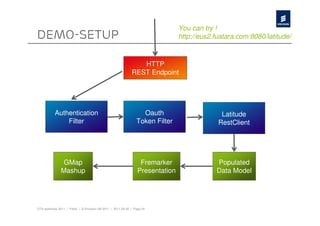
The document discusses Ericsson's advancements in security technologies, specifically focusing on their labs' offerings such as sim card identification, federated authentication using OpenID, and delegated authorization through OAuth. It highlights the need for improved authentication methods beyond traditional username/password systems, showcasing the use of SIM-based identification for enhanced security. Additionally, it presents peer-to-peer key establishment methodologies for secure communication, leveraging Ericsson's key management server capabilities.