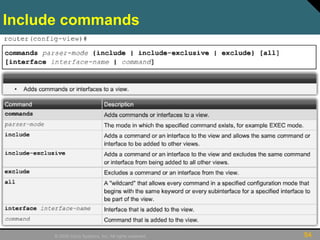
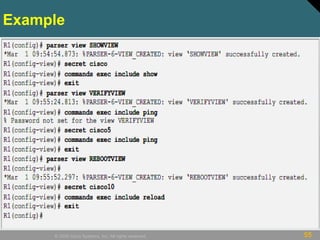
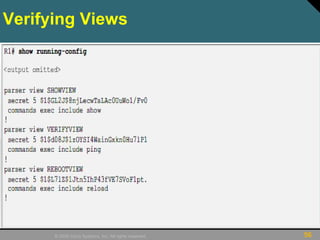
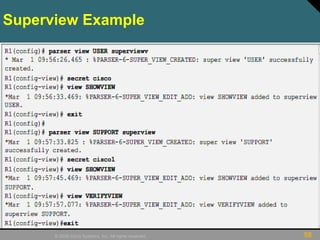
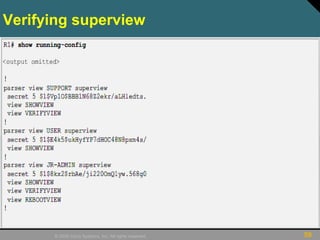
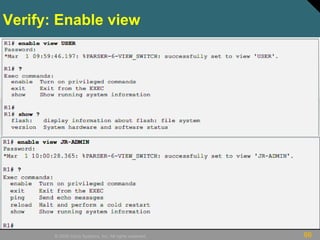
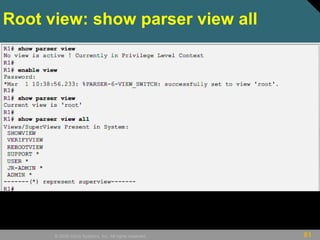
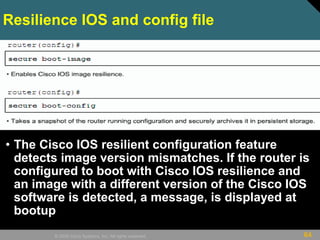
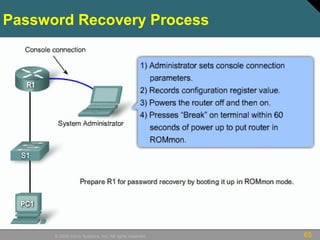
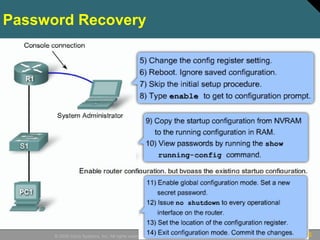
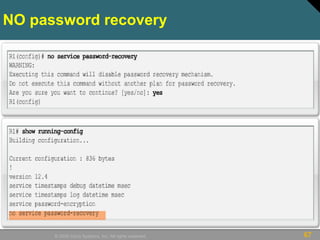
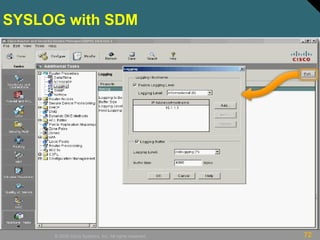
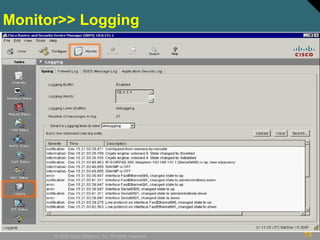
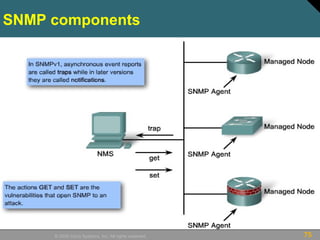
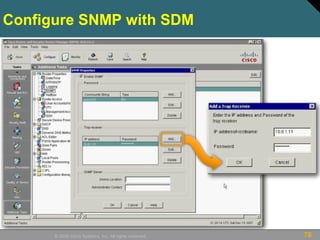
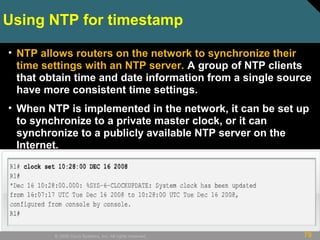
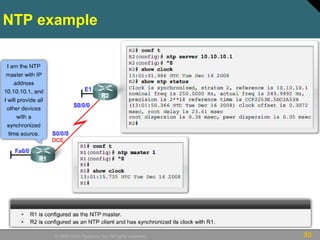
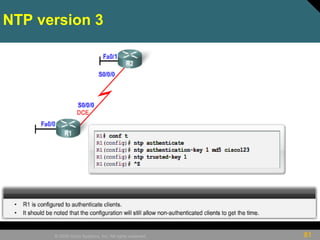
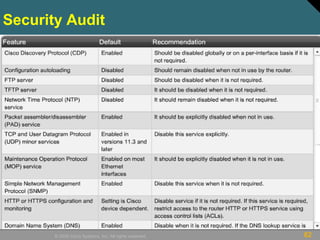
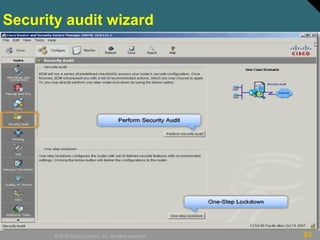
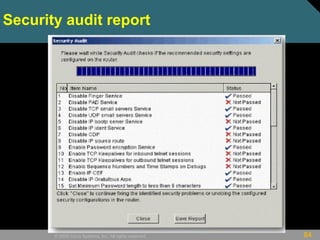
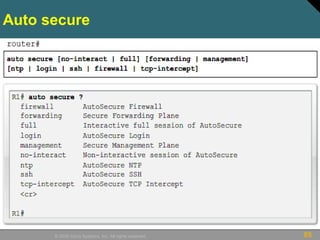
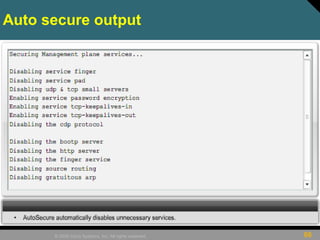
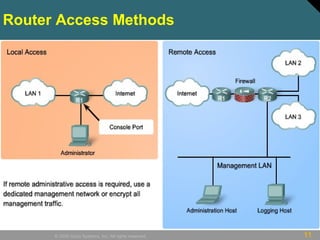
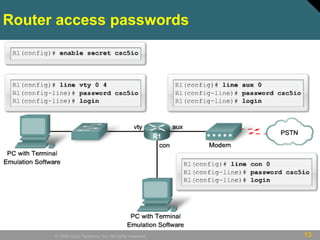
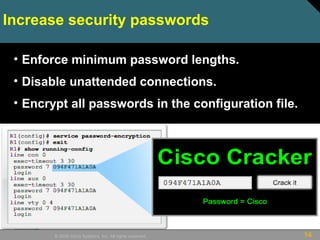
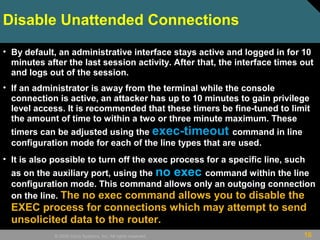
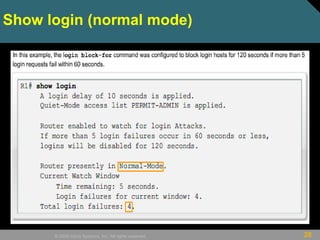
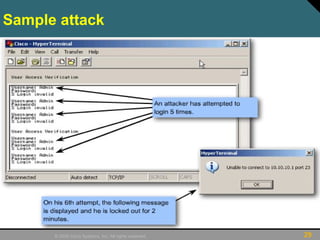
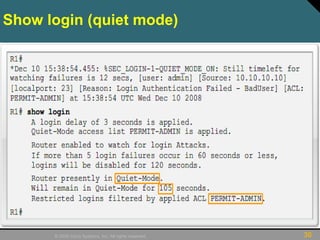
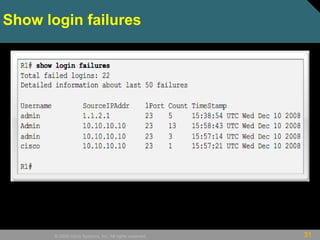
This document discusses securing Cisco routers. It covers topics like securing physical and remote access to routers, configuring administrative roles and views, and monitoring router activity. Some key points include assigning privilege levels to restrict commands, creating CLI views to control command access for different user roles, and using login features like quiet mode, block lists, and banners to restrict failed login attempts. The document provides examples of securing routers by configuring services like SSH and encrypting passwords.










![22© 2009 Cisco Systems, Inc. All rights reserved.
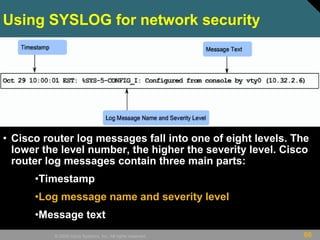
Cisco Enhanced login features
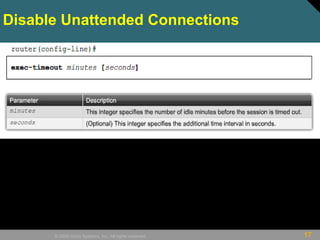
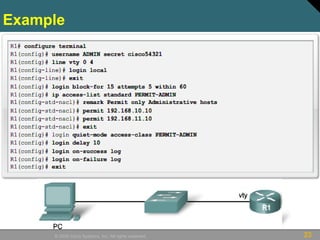
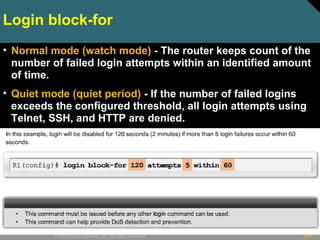
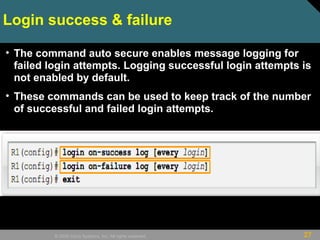
• Router(config)# login block-for seconds
attempts tries within seconds
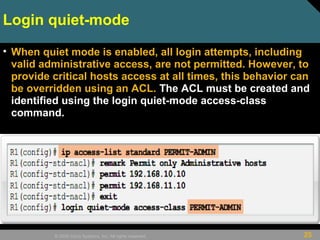
• Router(config)# login quiet-mode access-
class {acl-name | acl-number}
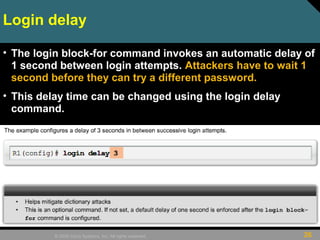
• Router(config)# login delay seconds
• Router(config)# login on-failure log [every
login]
• Router(config)# login on-success log
[every login]](https://image.slidesharecdn.com/ccnasecch02-securingdevicesnetwork-101109072926-phpapp01/85/network-security-22-320.jpg)













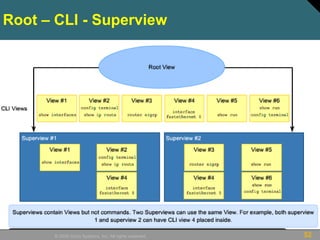
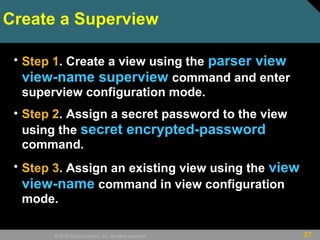
![53© 2009 Cisco Systems, Inc. All rights reserved.
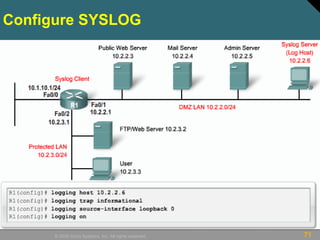
Create a view
• Step 1. Enable AAA with the aaa new-model global
configuration command. Exit and enter the root view with
the enable view command.
• Step 2. Create a view using the parser view view-name
command. This enables the view configuration mode. There
is a maximum limit of 15 views in total.
• Step 3. Assign a secret password to the view using the
secret encrypted-password command.
• Step 4. Assign commands to the selected view using the
commands parser-mode {include | include-exclusive |
exclude} [all] [interface interface-name | command]
command in view configuration mode.](https://image.slidesharecdn.com/ccnasecch02-securingdevicesnetwork-101109072926-phpapp01/85/network-security-53-320.jpg)