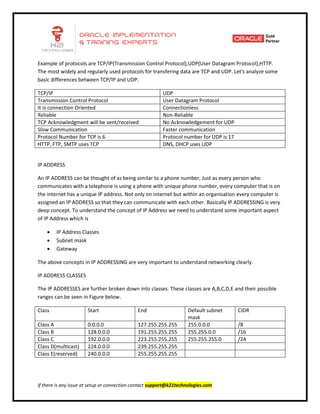
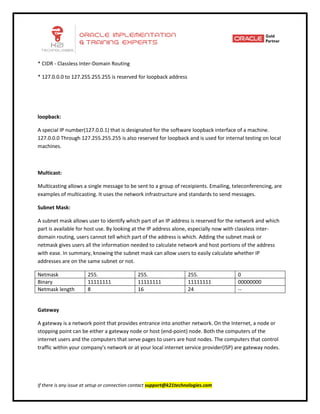
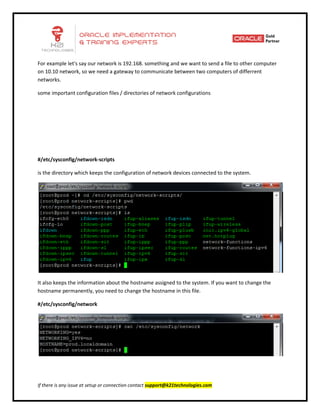
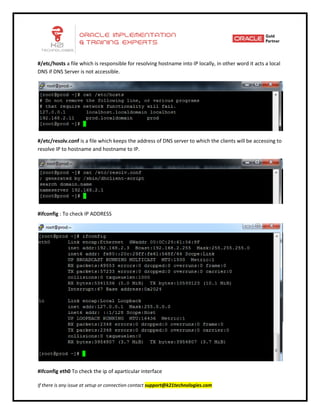
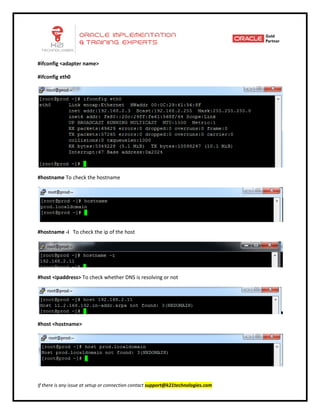
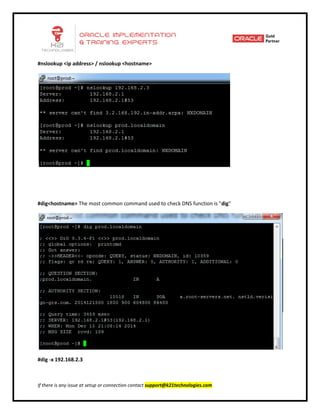
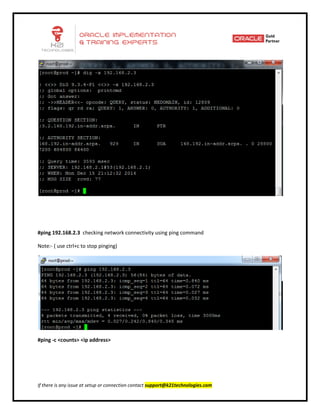
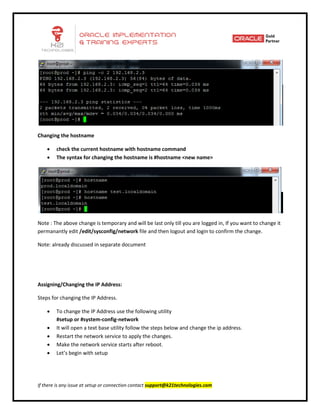
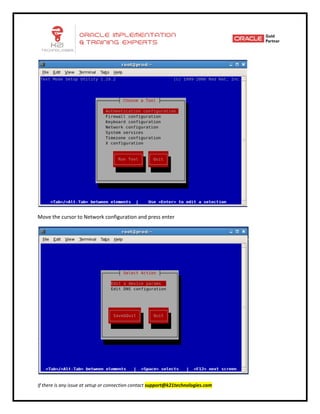
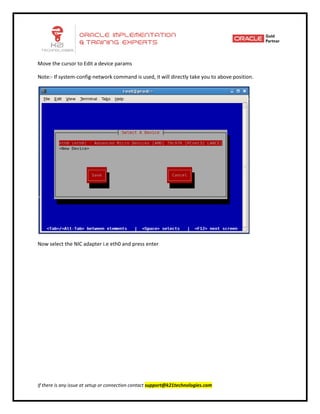
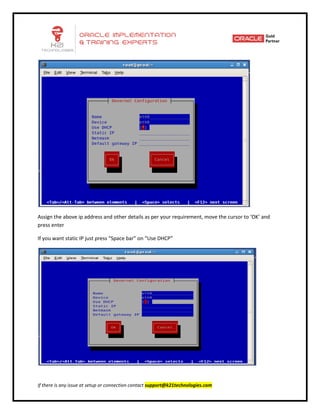
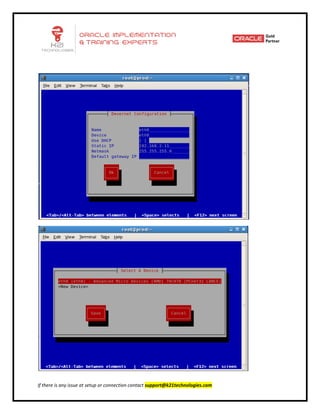
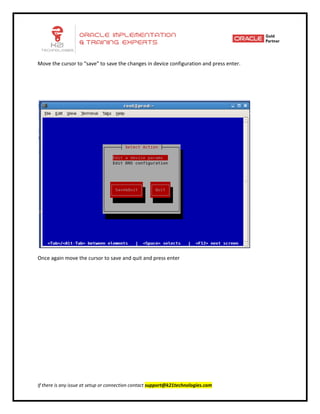
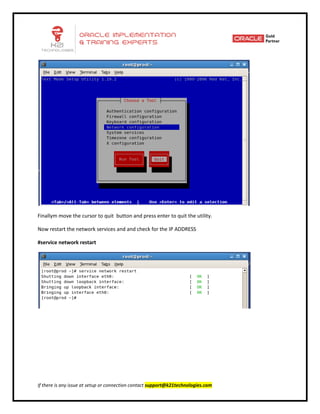
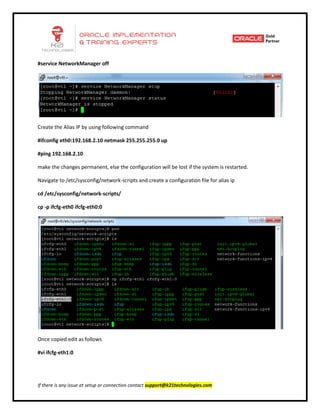
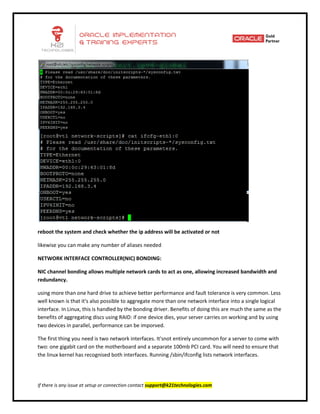
This document provides an overview of networking concepts including network interface cards, media, topologies, protocols, IP addressing, and network troubleshooting tools. It discusses the basic requirements for networking like NICs, media, topology, protocols, and IP addressing. It provides details on TCP and UDP protocols, IP address classes, subnet masks, gateways, and Linux network configuration files and commands.
![If there is any issue at setup or connection contact support@k21technologies.com
Overview of Unix
Activity Guide 5
[Edition 1]
[Last Update 130815]
For any issues/help contact : support@k21technologies.com](https://image.slidesharecdn.com/networkconfigurationinunixactivity5guide-150816110629-lva1-app6891/85/Network-configuration-in-Linux-1-320.jpg)