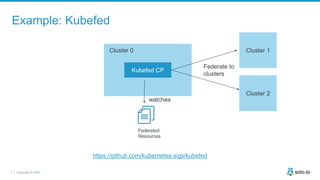
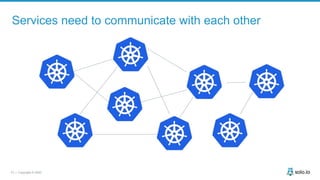
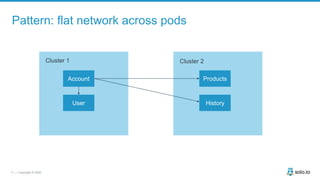
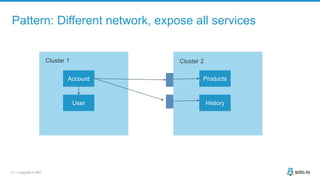
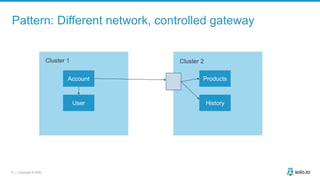
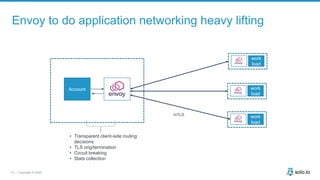
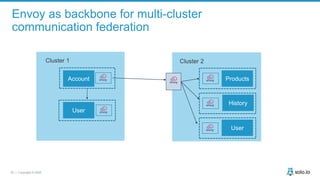
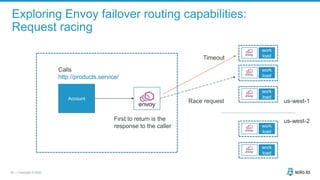
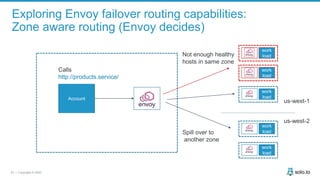
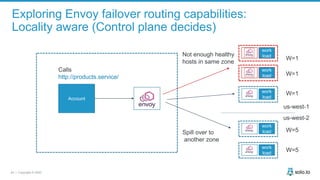
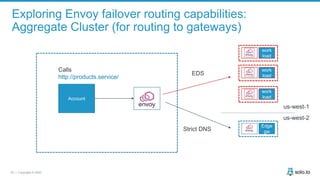
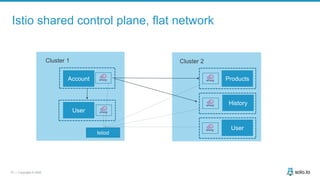
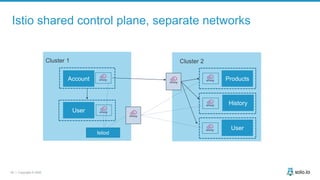
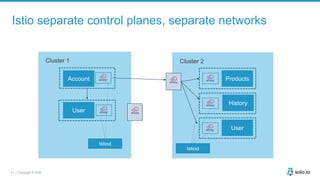
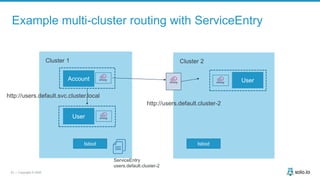
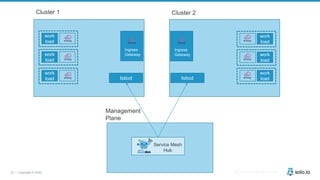
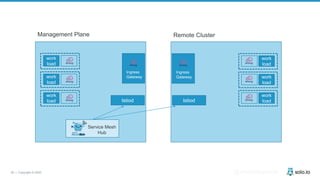
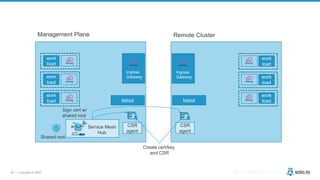
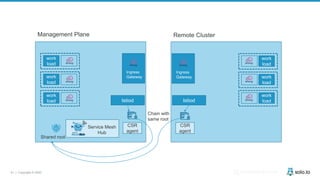
This document discusses multi-cluster Kubernetes and service mesh patterns, emphasizing challenges such as team velocity, decentralization, security, and compliance. It details the benefits of using smaller clusters, cluster federation, and the Envoy proxy for communication and traffic management. Additionally, it explores various patterns for network communication and considerations for implementing service meshes across clusters.