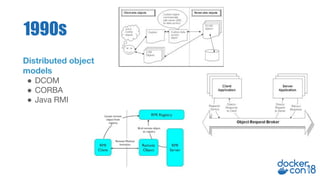
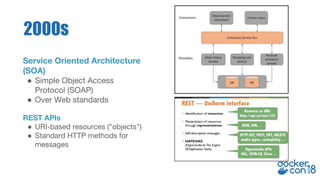
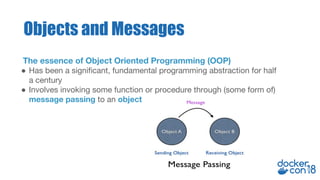
Tony Pujals, a Senior Developer Advocate at AWS, focuses on container services and microservices, highlighting the importance of object-oriented programming and message passing in programming architecture. He discusses the rise of microservices and container technology, emphasizing its role in managing distributed systems and the necessity for a service mesh to handle complexity in communication. Additionally, he promotes Istio as a leading service mesh solution, acknowledging ongoing developments and the need for stability and education in the field.
![● Developer Advocate @AWS
○ Container Services [ ECS | EKS | Fargate ]
● Docker Captain & Certified Docker Associate
○ Organizer/presenter for Docker Mountain View meetup
○ Currently authoring a Docker course for UC Davis /
Coursera
● Go and Node.js programmer
○ Generally fanatical about containers, microservices,
cloud computing
● Live in Mountain View, California
About me
@tonypujals](https://image.slidesharecdn.com/dockermicroservicesandtheservicemesh-180621000553/85/Docker-microservices-and-the-service-mesh-2-320.jpg)