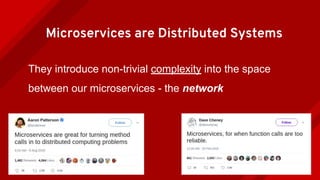
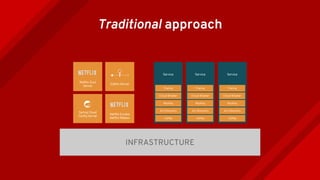
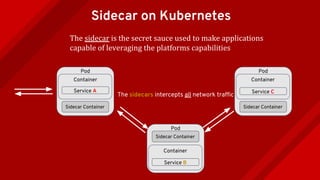
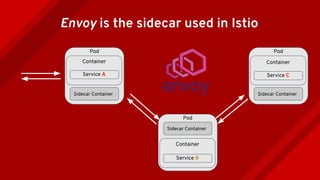
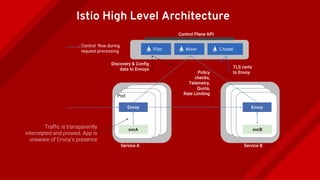
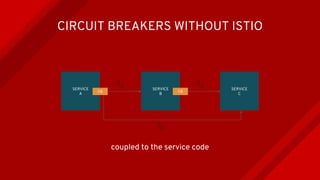
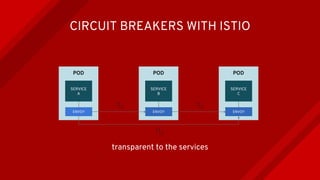
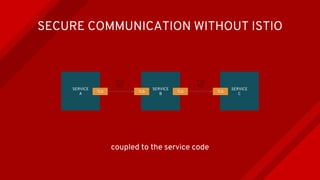
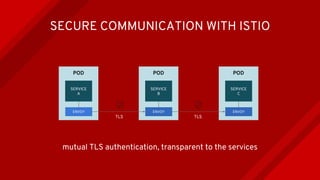
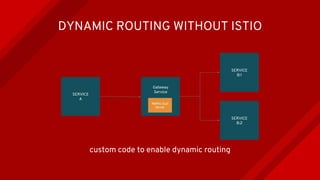
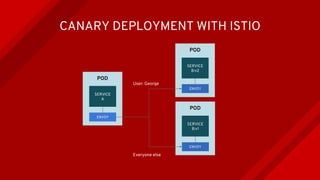
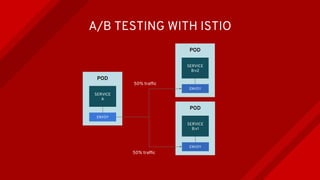
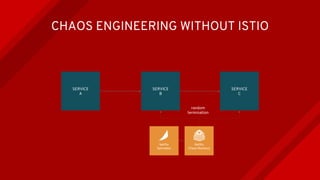
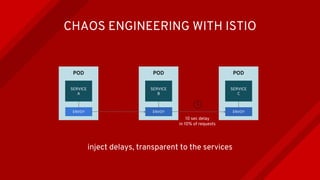
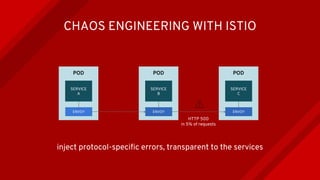
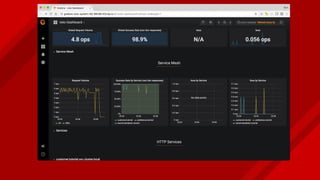
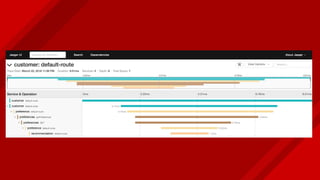
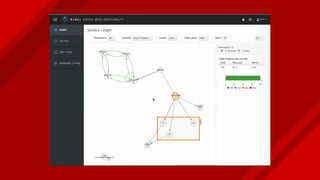
The document introduces Istio as a solution for managing the complexity of microservices by providing a service mesh that enhances resilience, security, observability, and routing. It discusses drawbacks of traditional approaches and emphasizes moving common concerns to the platform level to improve microservices operations. Istio utilizes sidecar containers (Envoy) to intercept traffic and offer capabilities like dynamic routing, circuit breaking, and chaos engineering, all while remaining transparent to the services themselves.