The document provides an overview of external authentication options for Percona Server for MongoDB and MongoDB Enterprise, highlighting configurations for LDAP, SASL, and Kerberos. It includes detailed setup instructions, security configurations, and examples of how to authenticate users within these systems. Additionally, it emphasizes operational management through tools like Ops Manager and offers career opportunities at ObjectRocket.





![Authentication
www.objectrocket.com
10
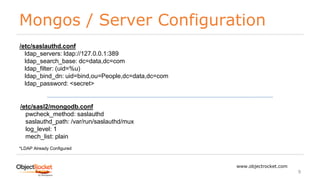
db.getSiblingDB("$external").createUser({user : 'jason', roles: [ {role : "readWrite", db: 'prod'} ] });
db.getSiblingDB("$external").auth({mechanism: "PLAIN", "user": "jason", "pwd": ”secret", "digestPassword": false });
HelloWorld.py
from pymongo import MongoClient
# MongoDB Connection URI and Establish Connection
uri = "mongodb://jason:terpko@localhost:27018/prod?authMechanism=PLAIN&authSource=$external”
client = MongoClient(uri)
…](https://image.slidesharecdn.com/mongodb-externalauthentication-180421132926/85/MongoDB-External-Authentication-10-320.jpg)





![Mongod Configuration (security.)
www.objectrocket.com
17
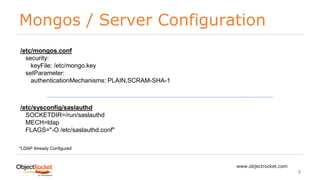
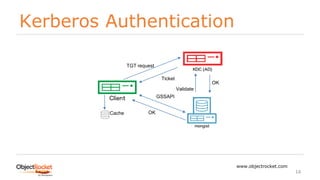
security:
authorization: enabled
keyFile: /etc/mongo.key
ldap:
authz:
queryTemplate: DC=DATA,DC=COM??sub?(&(objectClass=group)(member:1.2.840.113556.1.4.1941:={USER}))
bind:
method: simple
queryPassword: <secret>
queryUser: bind@data.com
servers: ldap.data.com:636
transportSecurity: tls
userToDNMapping: '[{match : "(.+)",ldapQuery:"DC=DATA,DC=COM??sub?(userPrincipalName={0})"}]'
setParameter:
authenticationMechanisms: GSSAPI
/etc/mongod.conf](https://image.slidesharecdn.com/mongodb-externalauthentication-180421132926/85/MongoDB-External-Authentication-17-320.jpg)
![Mongod Configuration (security.)
www.objectrocket.com
18
security:
authorization: enabled
keyFile: /etc/mongo.key
ldap:
authz:
queryTemplate: DC=DATA,DC=COM??sub?(&(objectClass=group)(member:1.2.840.113556.1.4.1941:={USER}))
bind:
method: simple
queryPassword: <secret>
queryUser: bind@data.com
servers: ldap.data.com:636
transportSecurity: tls
userToDNMapping: '[{match : "(.+)",ldapQuery:"DC=DATA,DC=COM??sub?(userPrincipalName={0})"}]'
setParameter:
authenticationMechanisms: GSSAPI
/etc/mongod.conf](https://image.slidesharecdn.com/mongodb-externalauthentication-180421132926/85/MongoDB-External-Authentication-18-320.jpg)
![Mongod Configuration (security.)
www.objectrocket.com
19
security:
authorization: enabled
keyFile: /etc/mongo.key
ldap:
authz:
queryTemplate: DC=DATA,DC=COM??sub?(&(objectClass=group)(member:1.2.840.113556.1.4.1941:={USER}))
bind:
method: simple
queryPassword: <secret>
queryUser: bind@data.com
servers: ldap.data.com:636
transportSecurity: tls
userToDNMapping: '[{match : "(.+)",ldapQuery:"DC=DATA,DC=COM??sub?(userPrincipalName={0})"}]'
setParameter:
authenticationMechanisms: GSSAPI
/etc/mongod.conf](https://image.slidesharecdn.com/mongodb-externalauthentication-180421132926/85/MongoDB-External-Authentication-19-320.jpg)
![Client Authentication
www.objectrocket.com
21
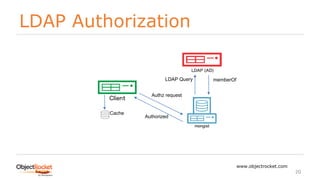
db.getSiblingDB("admin").createRole( { role: "CN=dba,DC=data,DC=com", privileges: [], roles: [
"userAdminAnyDatabase", "readWriteAnyDatabase", "dbAdminAnyDatabase", "clusterAdmin" ] });
db.getSiblingDB("$external").auth({mechanism: "GSSAPI", "user": "jason@DATA.COM" });
HelloWorld.py
from pymongo import MongoClient
# MongoDB Connection URI and Establish Connection
uri="mongodb://jason%40DATA.COM@server1.data.com:27017,.../?replicaSet=rs1&authMechanism=GSSAPI&ssl=true”
client=MongoClient(uri)
…](https://image.slidesharecdn.com/mongodb-externalauthentication-180421132926/85/MongoDB-External-Authentication-21-320.jpg)