1. The document discusses enhancing default MongoDB security by implementing access control, authentication, network hardening, encryption, and auditing.
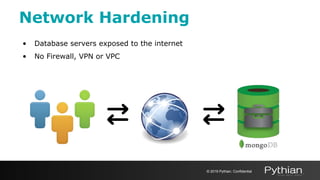
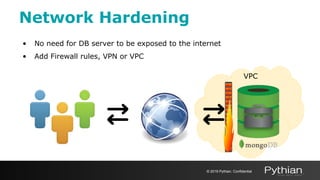
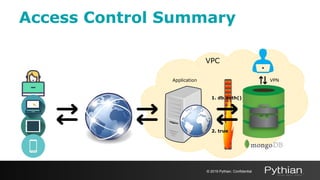
2. It describes enabling authentication and authorization to control access, limiting network exposure through firewalls and VPNs, and using TLS/SSL encryption to protect data in transit.
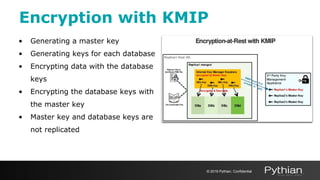
3. Storage engine encryption and auditing are also covered to protect data at rest and track system activity.

![{"name": "Igor Donchovski",
"live_in": "Skopje",
"email": "donchovski@pythian.com",
"current_role": "Lead database consultant",
"education": [{"type": "College", "name": "FEIT", "graduated": "2008", "university": "UKIM"},
{"type": "Master", "name": "FINKI", "graduated": "2013", "university": "UKIM"}],
"work": [{"role": "Web developer", "start": "2007", "end": "2012", "company": "Gord Systems"},
{"role": "DBA", "start": "2012", "end": "2014", "company": "NOVP"},
{"role": "Database consultant", "start": "2014", "end": "2016", "company": "Pythian"},
{"role": "Lead database consultant", "start": "2016", "company": "Pythian"}],
"certificates": [{"name": "C100DBA", "year": "2016", "description": "MongoDB certified DBA"}],
"social": [{"network": "LinkedIn", "url": "https://mk.linkedin.com/in/igorle"},
{"network": "Twitter", "url": "https://twitter.com/igorle"}],
"interests": ["Hiking", "Biking", "Traveling"],
"hobbies": ["Painting", "Photography", "Cooking"],
"proud_of": ["Volunteering", "Helping the Community"]}
About Me
© 2019 Pythian. Confidential](https://image.slidesharecdn.com/enhancingthedefaultmongodbsecurity-190617102734/85/Enhancing-the-default-MongoDB-Security-2-320.jpg)





![• security:authorization: enabled
use admin
db.createUser(
{
user: "UserAdmin",
pwd: "123456",
roles: [ { role: "userAdminAnyDatabase", db: "admin" }, "readWriteAnyDatabase" ]
}
)
Access Control
© 2019 Pythian. Confidential
2. Who are you?
1. db.foo.findOne()](https://image.slidesharecdn.com/enhancingthedefaultmongodbsecurity-190617102734/85/Enhancing-the-default-MongoDB-Security-12-320.jpg)
![mongo --port 27017 -u "UserAdmin" --authenticationDatabase "admin" -p
db.createUser(
{
user: "tester",
pwd: "qwerty",
roles: [ { role: "readWrite", db: "test" },
{ role: "read", db: "reporting" } ]
}
)
Access Control
© 2019 Pythian. Confidential
2. true
1. db.auth()](https://image.slidesharecdn.com/enhancingthedefaultmongodbsecurity-190617102734/85/Enhancing-the-default-MongoDB-Security-13-320.jpg)







![Auditing
Track System Activity
● schema (DDL)
● replica set and sharded cluster
● authentication and authorization
● CRUD operations
auditLog:
destination: <syslog>, <console>, <file>
format: <JSON>, <BSON>
path: data/db/auditLog.<json>,<bson>
filter: '{ atype: { $in: ["dropCollection"]}}'
* Available in MongoDB Enterprise only
© 2019 Pythian. Confidential
> bsondump auditLog.bson
{"atype":"authenticate","ts":{"$date":"2019-02-14T14:11:29.97
5+0100"},"local":{"ip":"127.0.1.1","port":27017},"remote":{"i
p":"127.0.0.1","port":42634},"users":[],"roles":[],"param":{"
user":"root","db":"admin","mechanism":"SCRAM-SHA-1"},"result"
:18}
{"atype":"authCheck","ts":{"$date":"2019-02-14T14:15:49.161+0
100"},"local":{"ip":"127.0.1.1","port":27017},"remote":{"ip":
"127.0.0.1","port":42636},"users":[{"user":"test","db":"admin
"}],"roles":[{"role":"read","db":"admin"}],"param":{"command"
:"insert","ns":"test.orders","args":{"insert":"orders","docum
ents":[{"_id":{"$oid":"58a3030507bd5e3486b1220d"},"id":1.0,"i
tem":"paper clips"}],"ordered":true}},"result":13}](https://image.slidesharecdn.com/enhancingthedefaultmongodbsecurity-190617102734/85/Enhancing-the-default-MongoDB-Security-41-320.jpg)