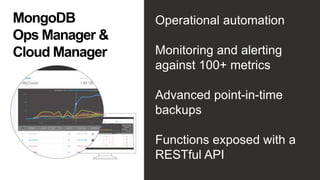
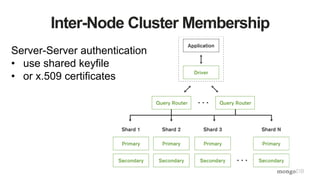
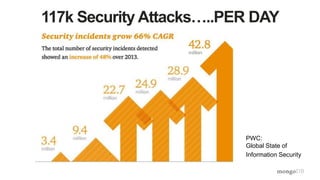
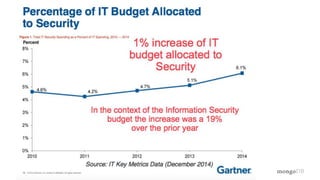
The document discusses the importance of securing MongoDB deployments in response to increasing security threats and regulatory requirements. It outlines best practices for database security, including data access controls, authentication, authorization, and encryption measures. Resources for further learning and compliance guidelines are also provided.








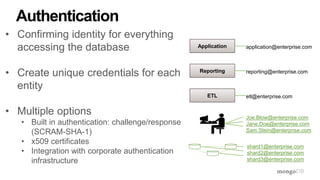
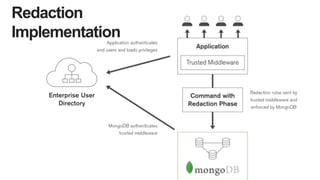
![Authorization: MongoDB Field Level Redaction
User 1
- Confidentia
l
- Secret
{ _id: ‘xyz’,
field1: {
level: [ “Confidential” ],
data: 123
},
field2: {
level: [ “Top Secret” ],
data: 456
},
field3: {
level: [ “Unclassified” ],
data: 789
}
}
User 2
- Top Secret
- Secret
- Confidentia
l
User 3
- Unclassified
FieldLevelAccessControl
• Enables a single document to store data with multiple
security levels](https://image.slidesharecdn.com/mongodbsecuritydaysv2-151026161916-lva1-app6892/85/MongoDB-Days-UK-Securing-Your-Deployment-with-MongoDB-Enterprise-19-320.jpg)
![Redaction in Action
User 1
- Confidentia
l
- Secret
{ _id: ‘xyz’,
field1: {
level: [ “Confidential” ],
data: 123
},
field2: {
level: [ “Top Secret” ],
data: 456
},
field3: {
level: [ “Unclassified” ],
data: 789
}
}
User 2
- Top Secret
- Secret
- Confidentia
l
User 3
- Unclassified
FieldLevelAccessControl](https://image.slidesharecdn.com/mongodbsecuritydaysv2-151026161916-lva1-app6892/85/MongoDB-Days-UK-Securing-Your-Deployment-with-MongoDB-Enterprise-20-320.jpg)
![Redaction in Action
User 1
- Confidentia
l
- Secret
{ _id: ‘xyz’,
field1: {
level: [ “Confidential” ],
data: 123
},
field2: {
level: [ “Top Secret” ],
data: 456
},
field3: {
level: [ “Unclassified” ],
data: 789
}
}
User 2
- Top Secret
- Secret
- Confidentia
l
User 3
- Unclassified
FieldLevelAccessControl](https://image.slidesharecdn.com/mongodbsecuritydaysv2-151026161916-lva1-app6892/85/MongoDB-Days-UK-Securing-Your-Deployment-with-MongoDB-Enterprise-21-320.jpg)
![Redaction in Action
User 1
- Confidentia
l
- Secret
{ _id: ‘xyz’,
field1: {
level: [ “Confidential” ],
data: 123
},
field2: {
level: [ “Top Secret” ],
data: 456
},
field3: {
level: [ “Unclassified” ],
data: 789
}
}
User 2
- Top Secret
- Secret
- Confidentia
l
User 3
- Unclassified
FieldLevelAccessControl](https://image.slidesharecdn.com/mongodbsecuritydaysv2-151026161916-lva1-app6892/85/MongoDB-Days-UK-Securing-Your-Deployment-with-MongoDB-Enterprise-22-320.jpg)