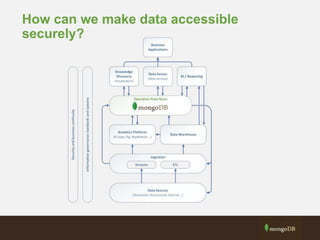
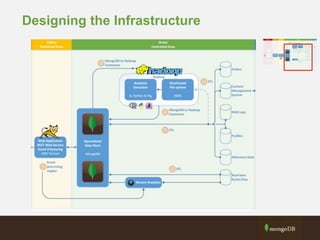
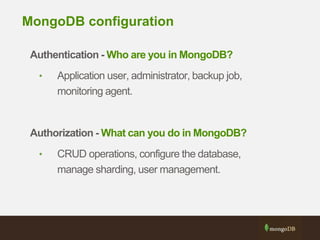
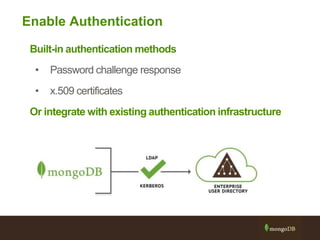
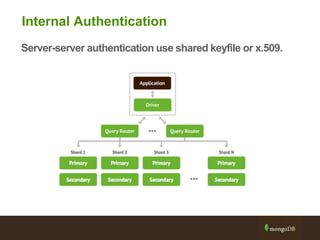
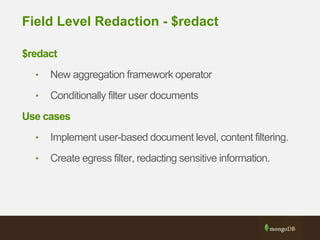
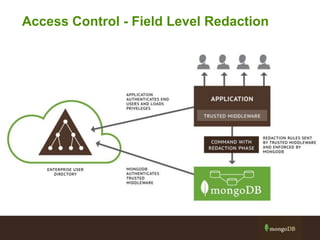
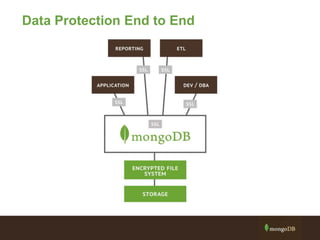
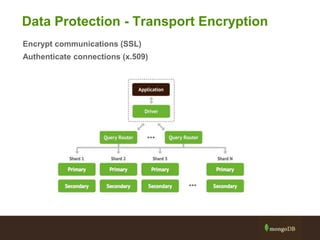
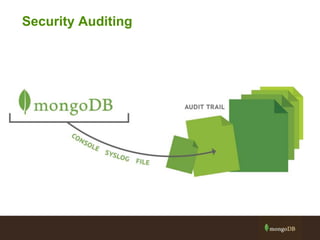
The document outlines best practices for securing MongoDB applications, focusing on database access control, data protection, and auditing. Key points include designing security from the beginning, implementing role-based access control, and ensuring encrypted data transmission and storage. Additional recommendations emphasize not exposing database servers to the internet and regularly consulting MongoDB security documentation.