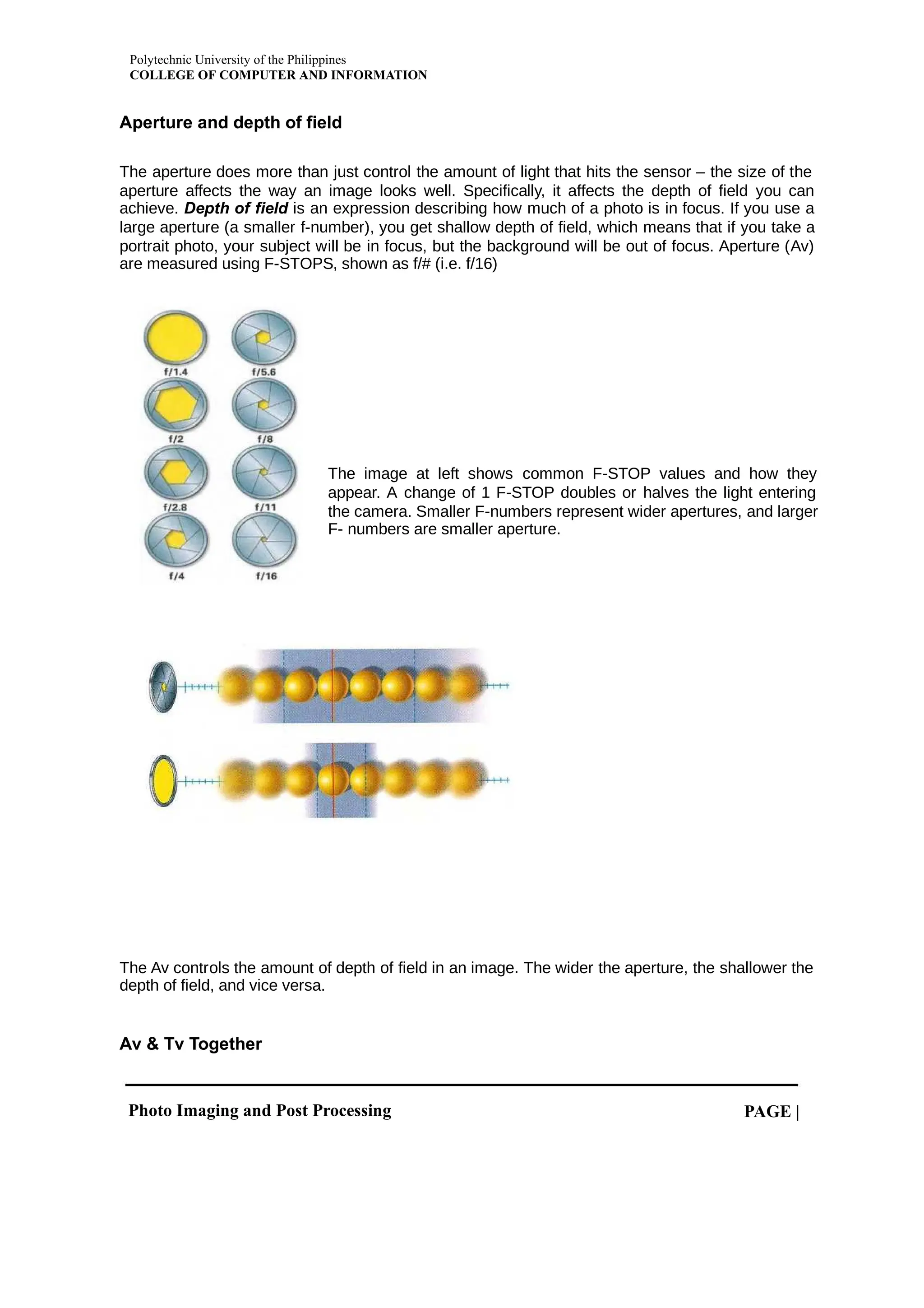
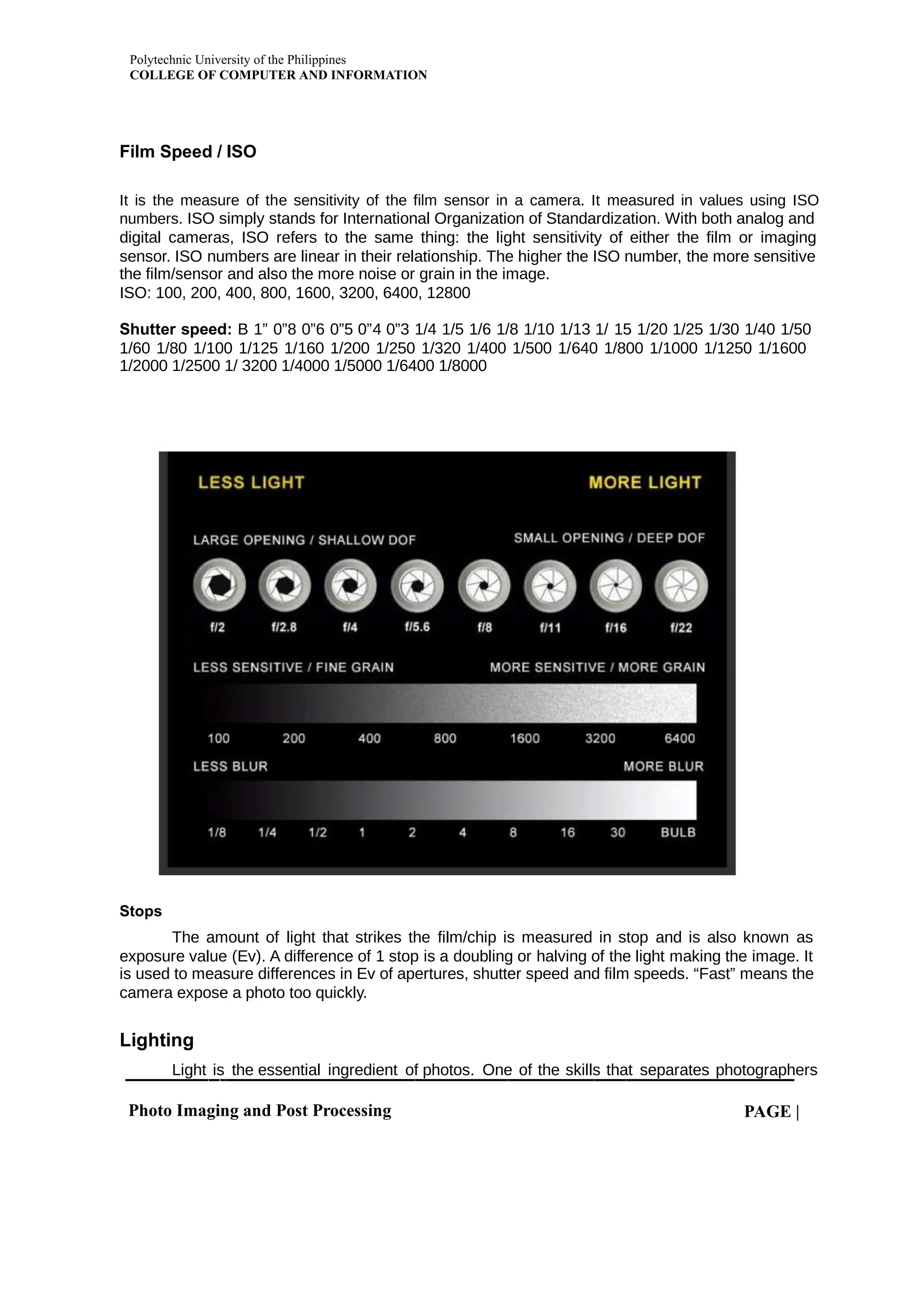
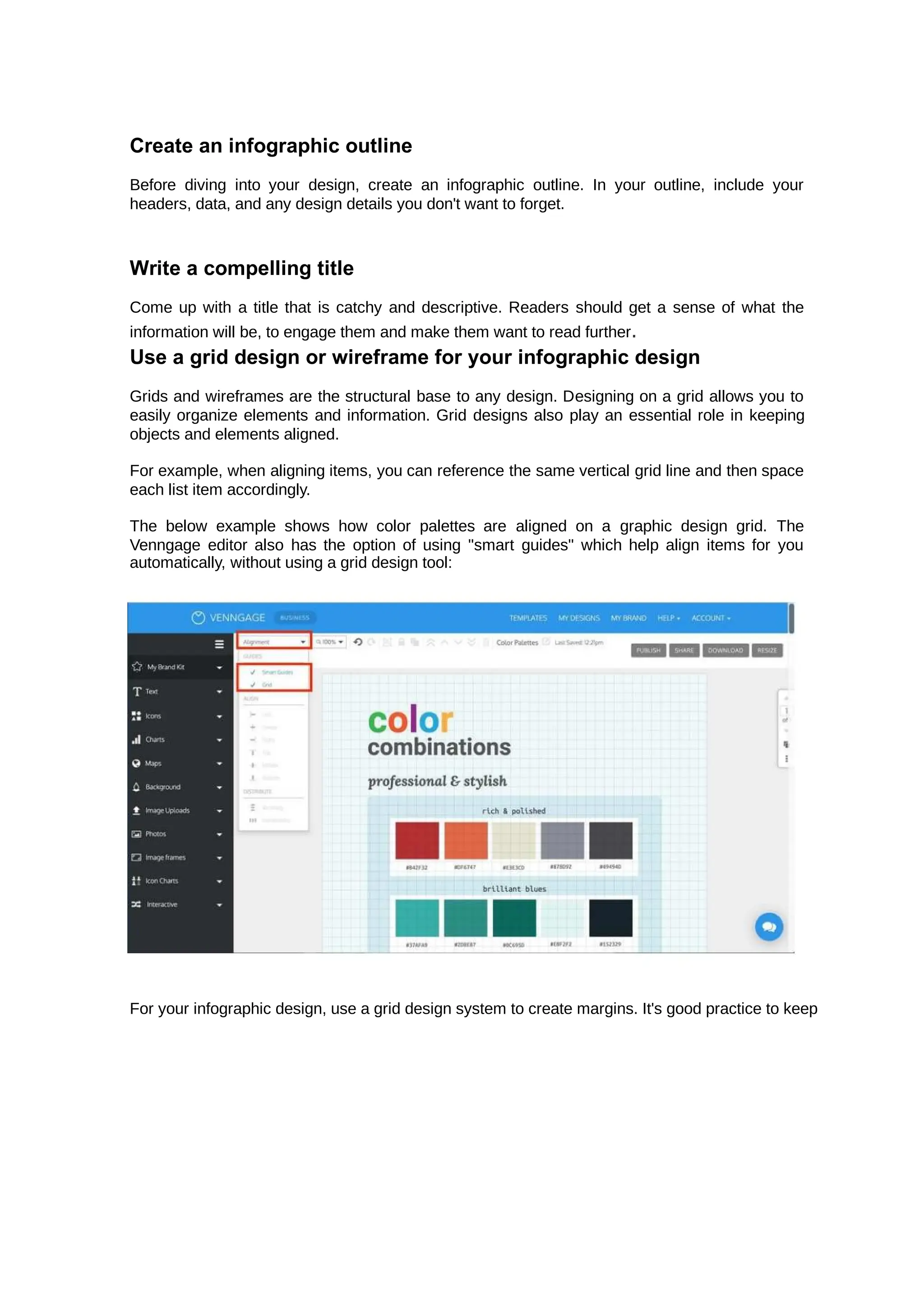
This document provides an overview of information and communication technology (ICT) including its history, uses in daily life, and impacts on society. ICT refers to technologies that allow people to communicate and access information, and includes devices, networking components, applications, and systems. The document discusses how ICT is used for communication, education, jobs/employment, and socializing. It also outlines both positive impacts like increased access to information, and negative impacts such as computer addiction and cybercrimes. The document provides context around ICT's role in modern society.























































































![Shape
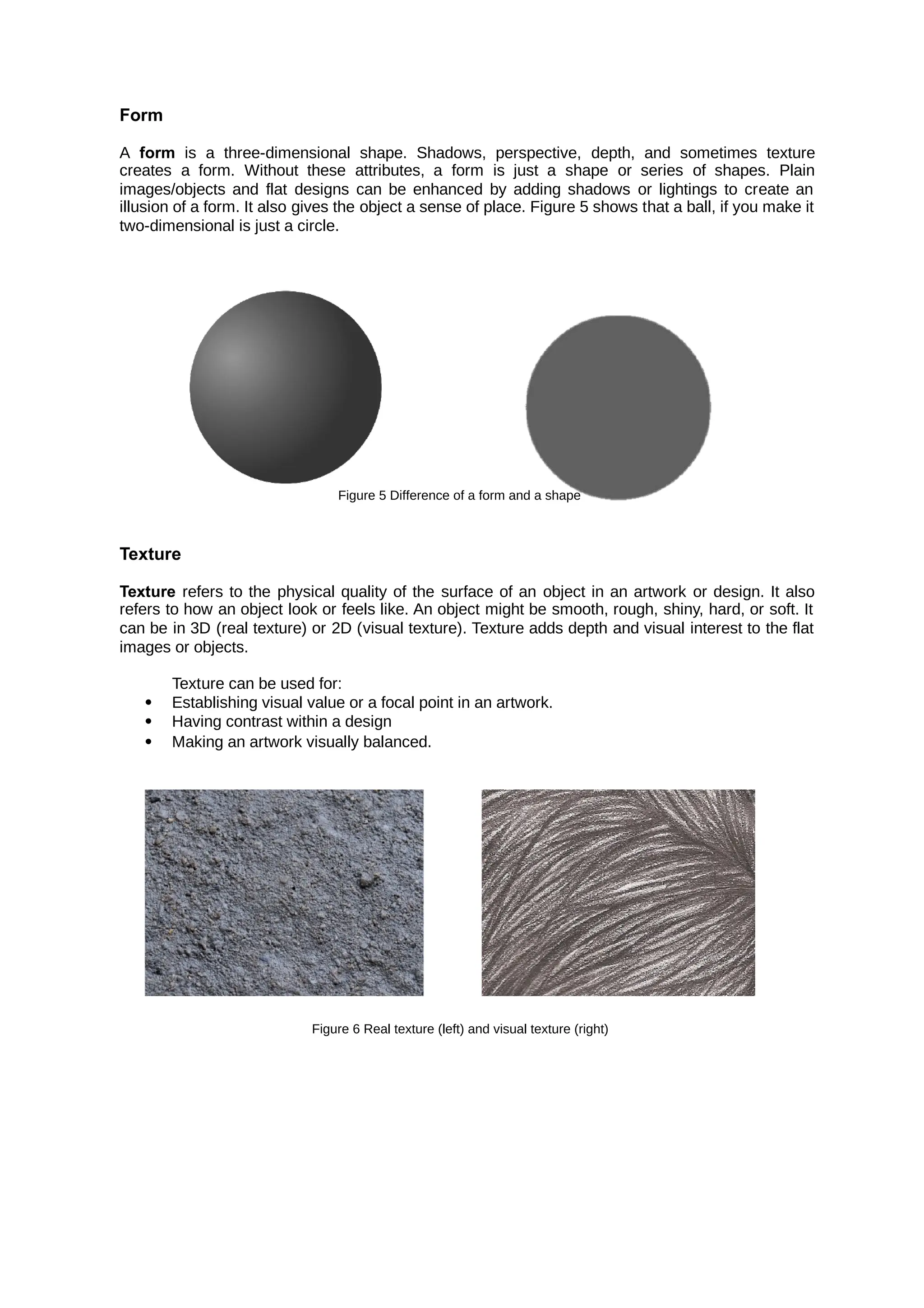
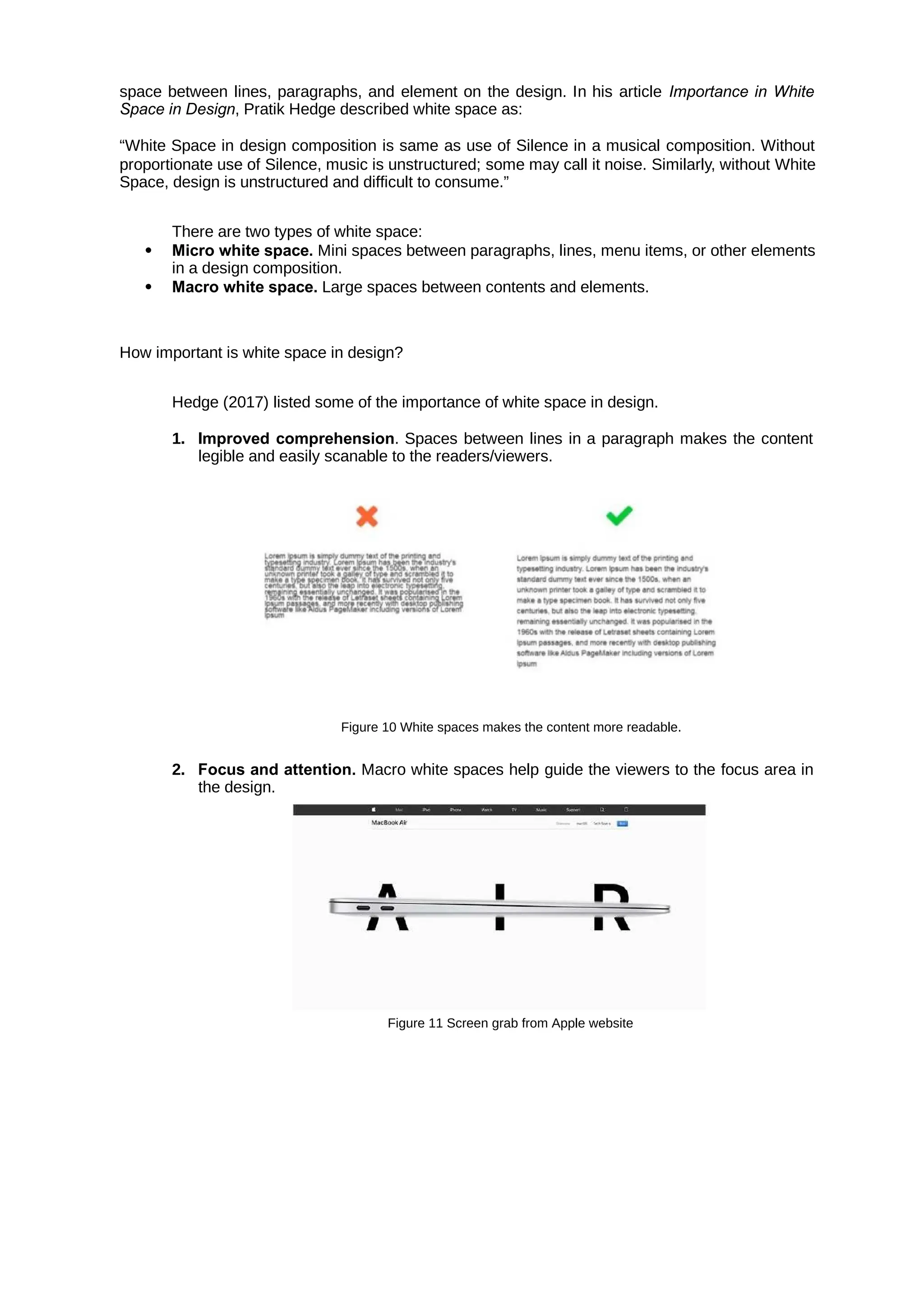
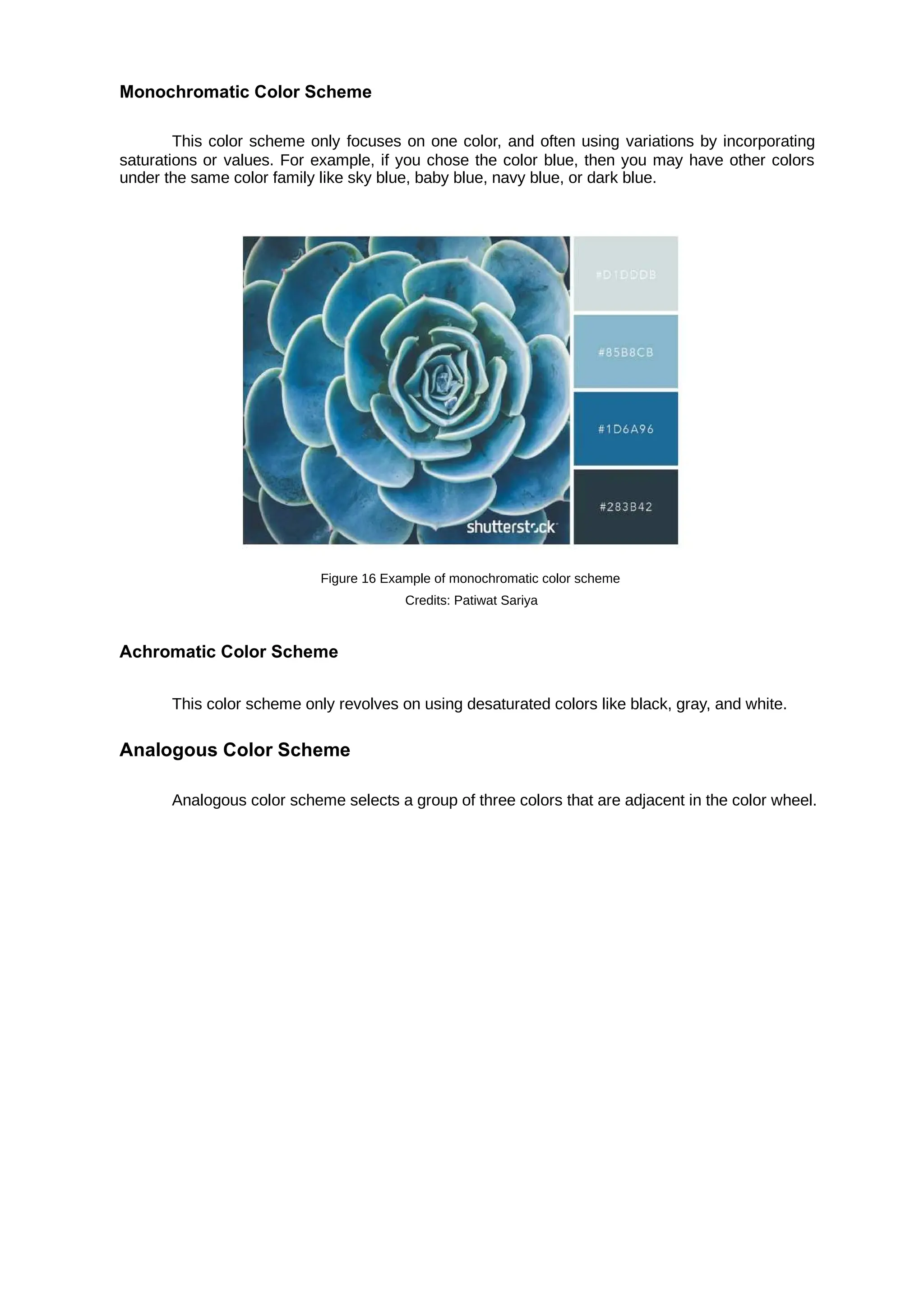
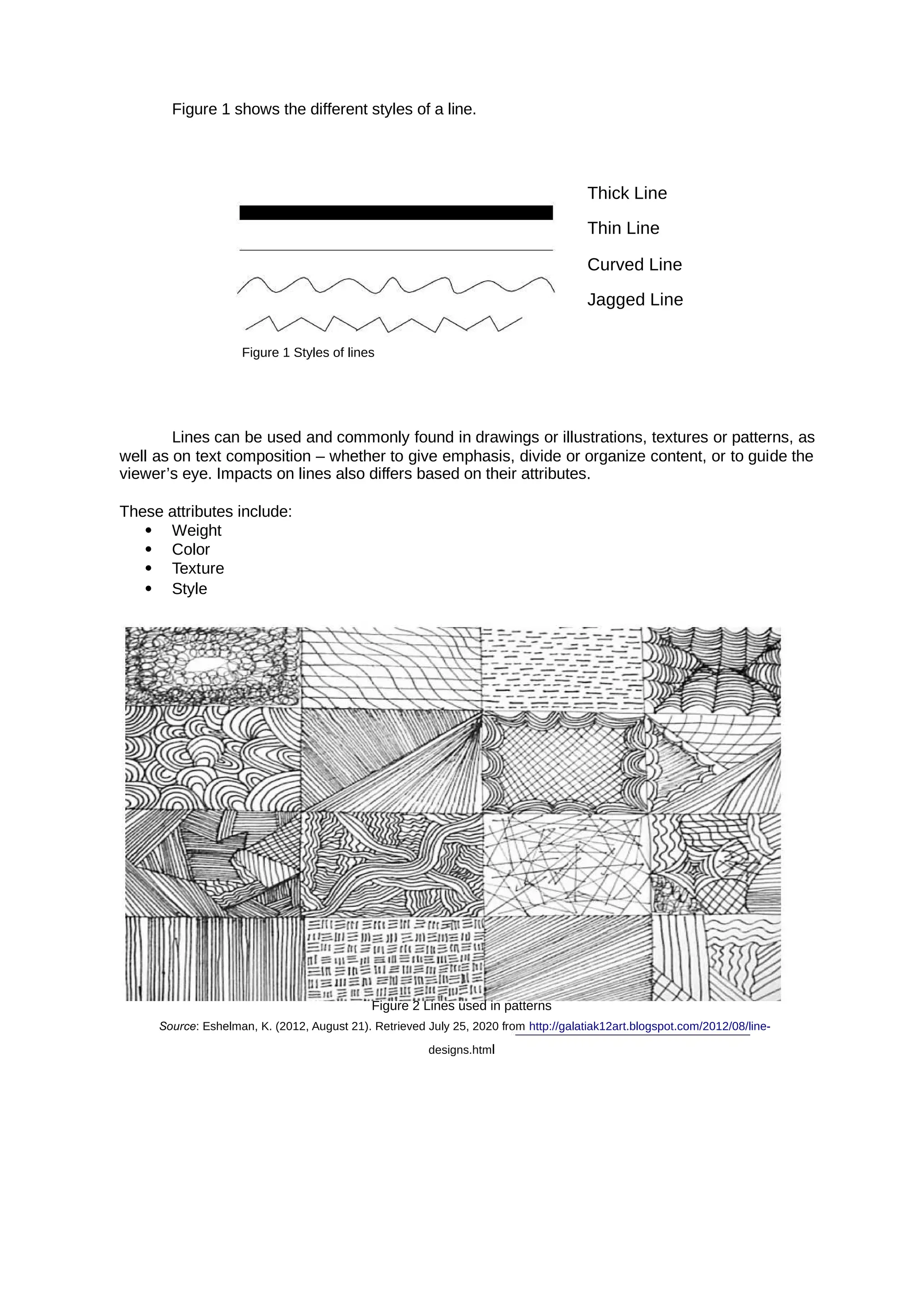
A is a two-dimensional external boundary of an object. Any object outline that has
shape
height and width can be considered as a shape. Together with lines, they form the foundation of
your design.
There are two (2) major categories of shapes in design:
Geometric – these are regular and mathematical shapes.
Organic – these are freeform shapes.
Figure 3 shows the different examples of geometric and organic shapes.
Figure 3 Example of geometric and freeform shapes
Source: Lewman, L. (2018, February 18). [Digital Image]. Retrieved July 25, 2020,
from https://www.slideshare.net/LeahLewman/elements-of-art-shape-88242623
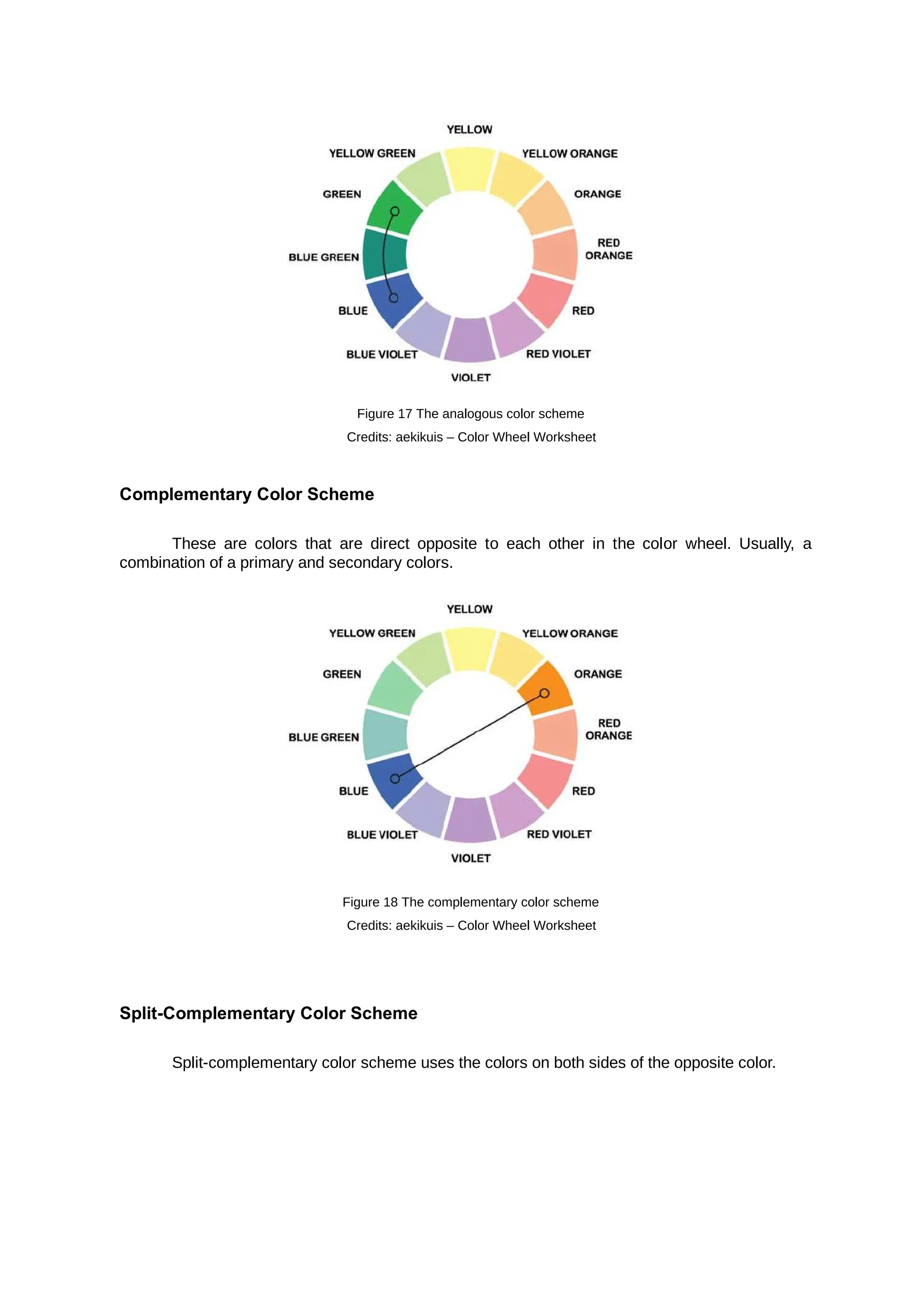
Shapes can be used in organizing or dividing contents, create illustrations, and in adding interest to
one’s work/design.
Figure 4 Using shapes in a poster design](https://image.slidesharecdn.com/module-living-in-the-it-eracompress-231110153753-b83c03bf/75/module-living-in-the-it-era_compress-pdf-93-2048.jpg)