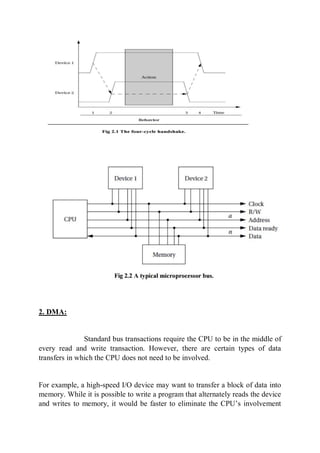
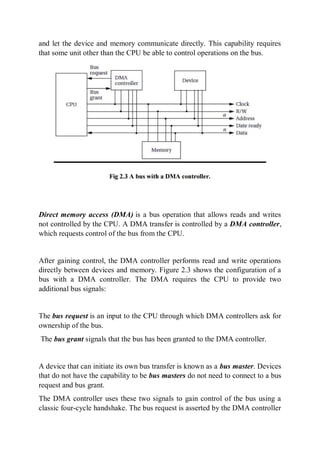
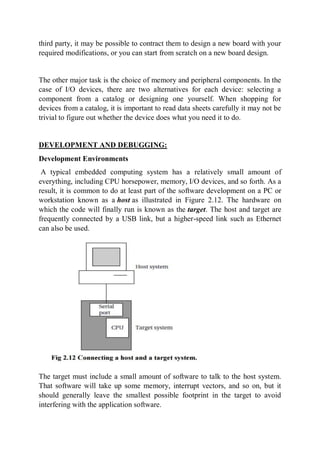
The document discusses computer buses and how they allow the CPU to communicate with memory and I/O devices. It describes the basic handshake protocol used by most bus protocols and how microprocessor buses build on this. It also discusses direct memory access (DMA) which allows direct communication between devices and memory without CPU involvement. The document then covers interfacing memory and I/O devices to the bus and considerations for embedded system architecture, hardware design, development environments, and debugging techniques.