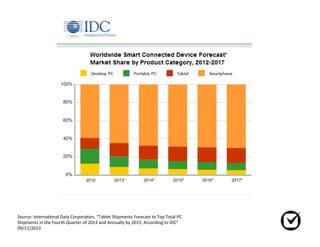
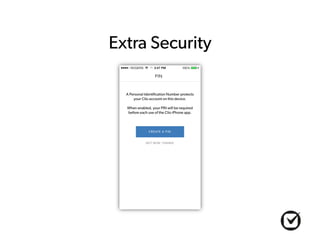
The document discusses mobile computing in law firms. It notes that mobile devices now account for the majority of computing device sales, and that most lawyers now use smartphones for work. However, it also outlines several risks of mobile computing like device loss, theft, or confiscation. It discusses recent court cases around mobile privacy and searches. The document recommends best practices for mobile security like password protecting devices, backing up data regularly, using location services, and storing client data in cloud services.