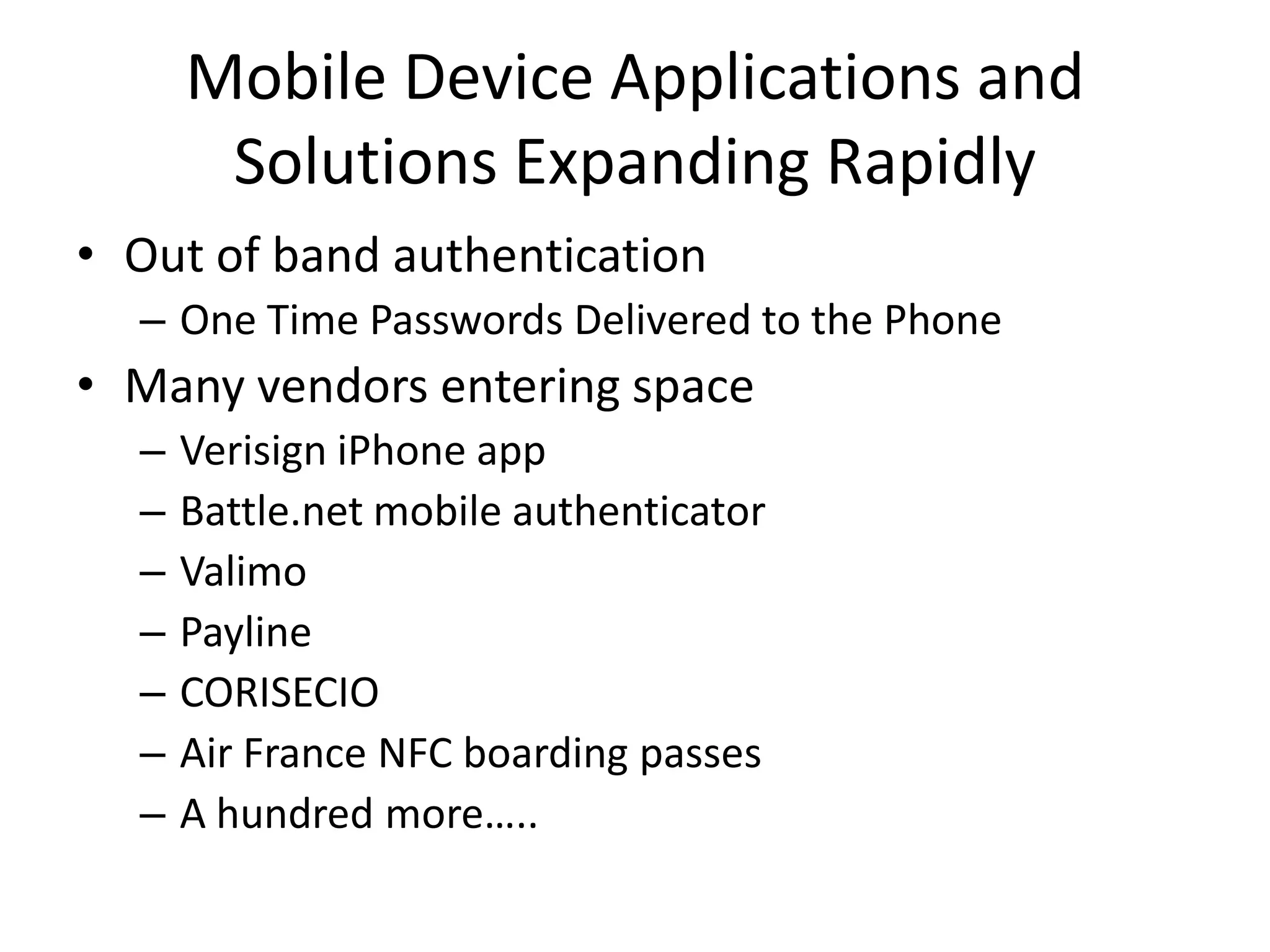
This document discusses securing mobile devices and the edge of networks. It defines what mobile devices include, such as cell phones, laptops, and more. It outlines various attack vectors for mobile devices, including emails, MMS, SMS, and removable storage. The document also discusses using device certificates and FIPS 201 to help authenticate and manage devices. It notes challenges in managing both device and user security and behavior. Finally, it recommends enabling security features like passwords, data encryption, and remote wiping to help secure mobile devices.