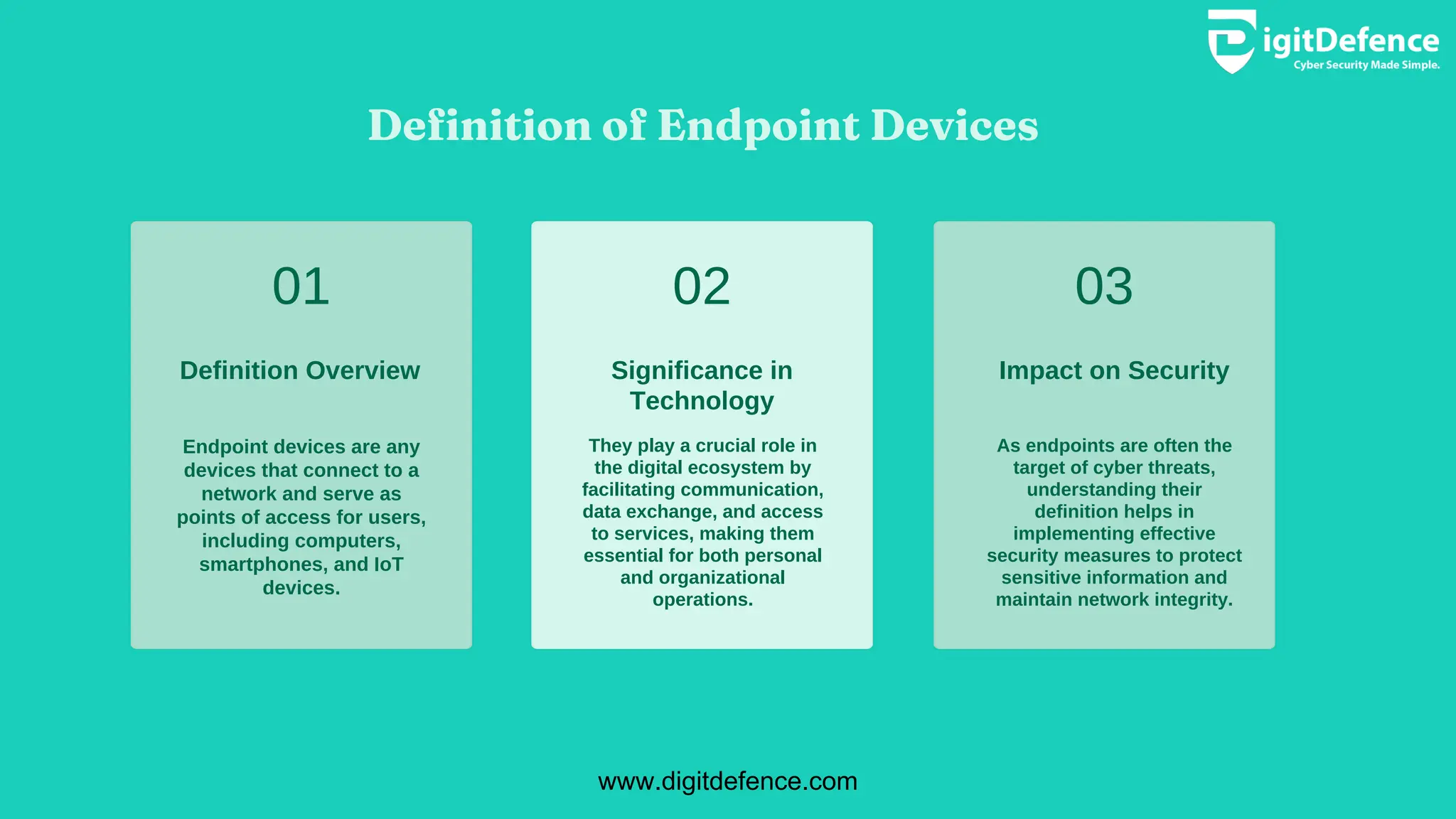
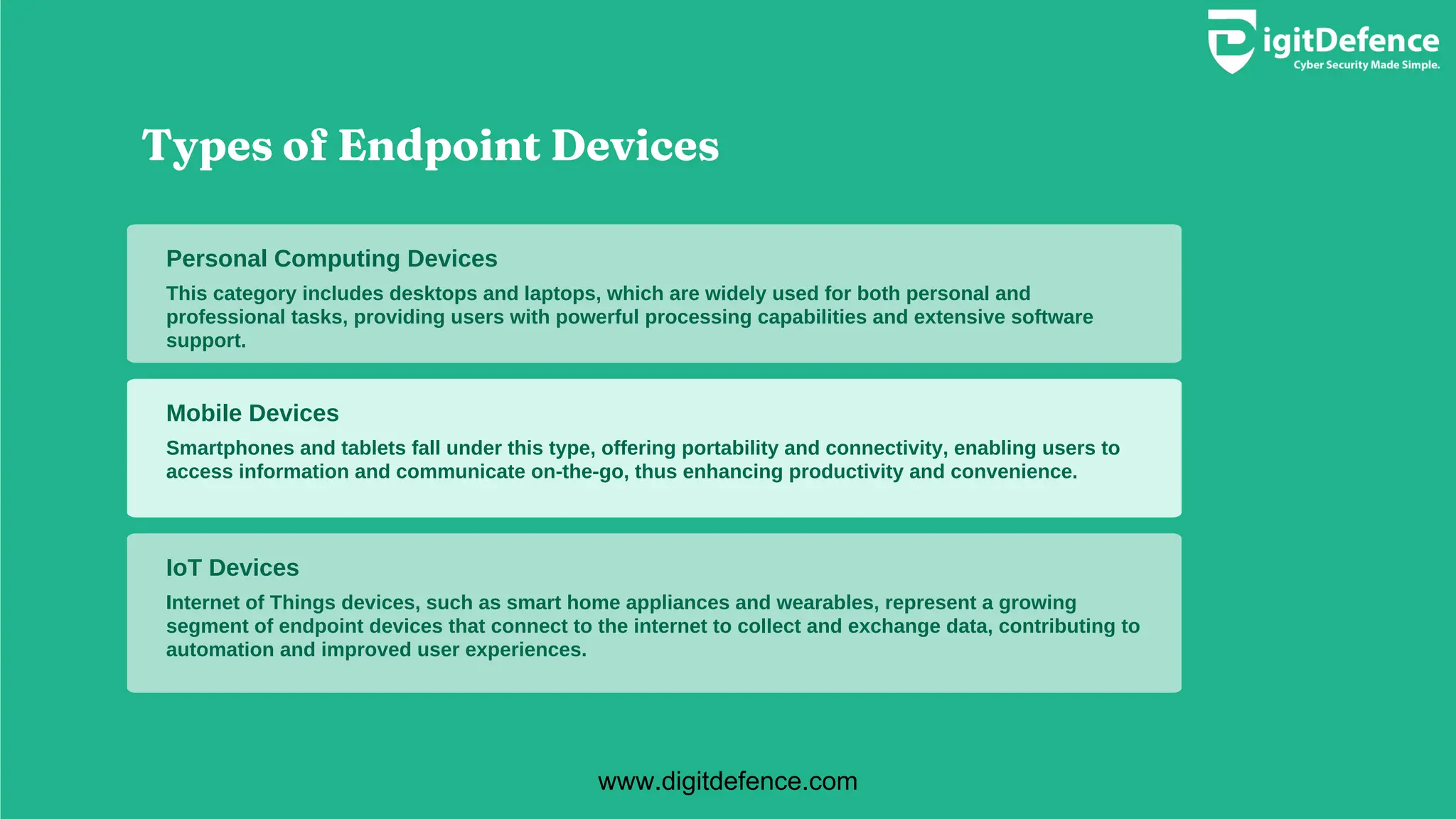
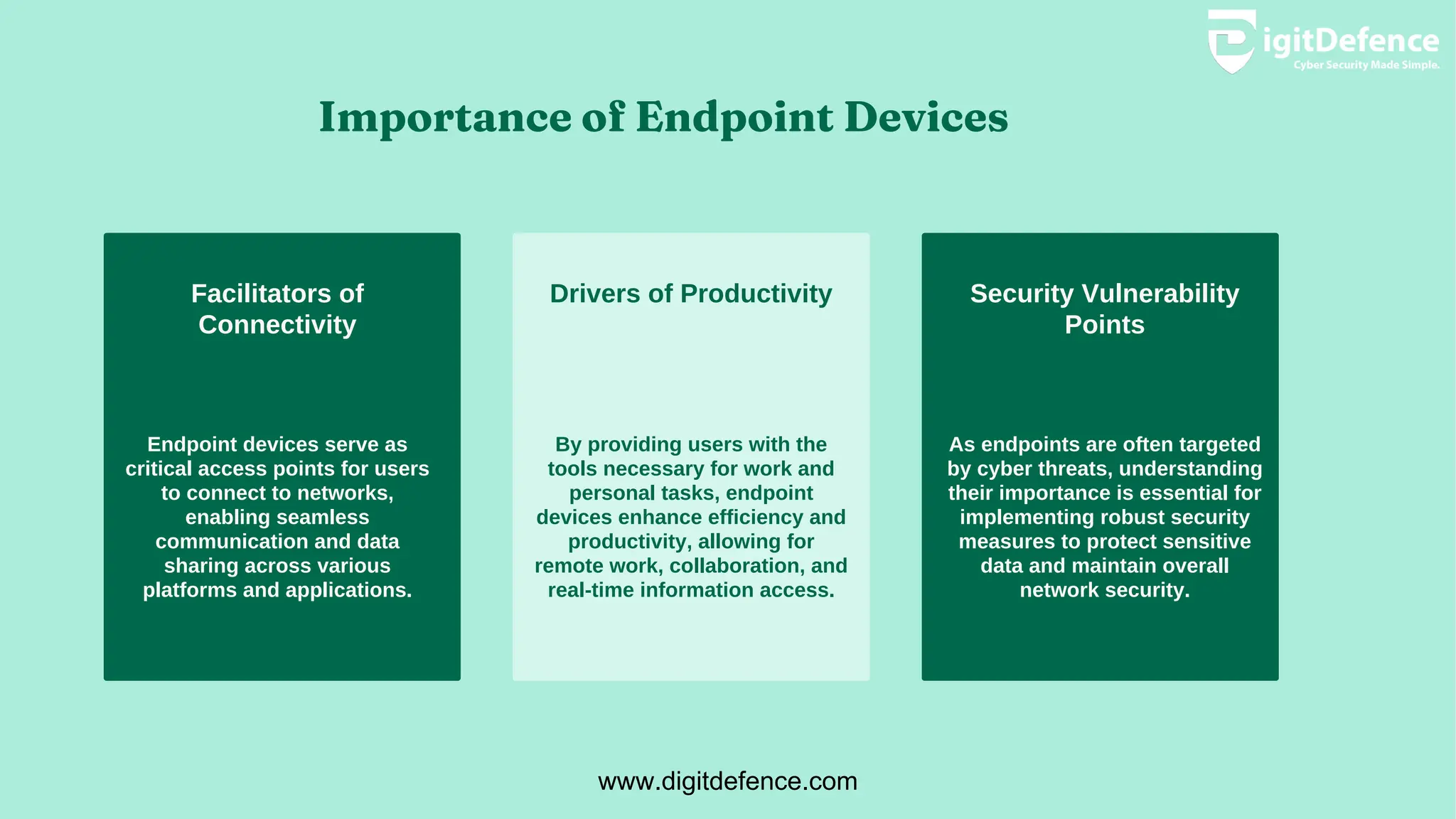
Endpoint devices are any devices connecting to a network, crucial for communication and access to services, but often targeted by cyber threats. Major types include personal computers, mobile devices, and IoT gadgets, each presenting unique security risks and vulnerabilities. Implementing strong security measures, regular updates, and multi-factor authentication is essential for protecting sensitive information across these devices.