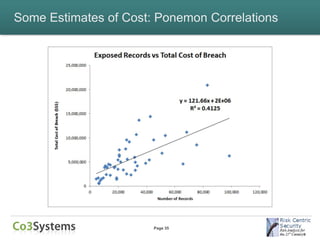
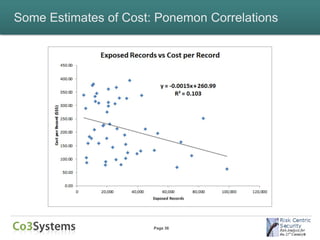
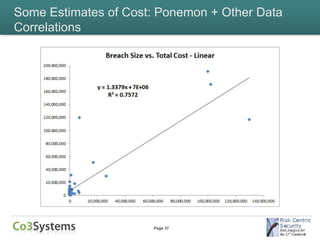
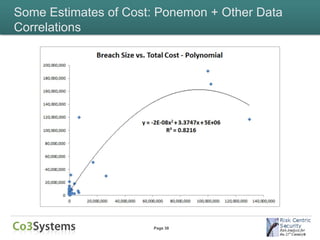
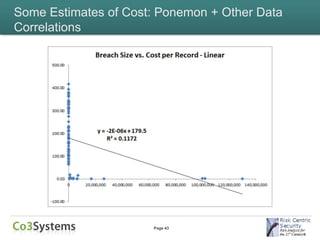
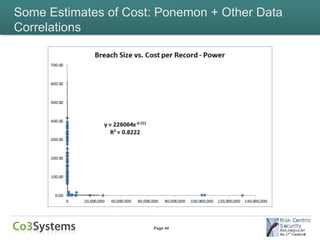
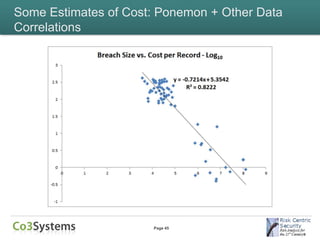
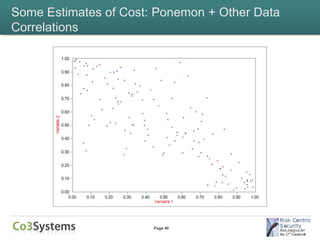
This document provides an overview of the costs associated with data breaches. It begins by introducing the speakers and the agenda. It then discusses what constitutes a data breach and the types of data that may be exposed, such as PII, PHI, intellectual property, and financial information. The document explores the various direct and indirect costs of a breach for different entities. It provides examples of cost estimates from past breaches, which range from thousands to over $170 million depending on the size and type of breach. Patterns in breach cost data are examined, though correlations are weak. Overall, the document deconstructs the complexities involved in understanding and estimating the full costs of a data breach.

























![What is PII in the European Union?
Personally Identifiable Information (PII):
• A term similar to PII, "personal data" is defined in EU directive 95/46/EC, for the
purposes of the directive:[4]
Article 2a: 'personal data' shall mean any information relating to an identified
or identifiable natural person ('data subject'); an identifiable person is one who
can be identified, directly or indirectly, in particular by reference to an
identification number or to one or more factors specific to his physical,
physiological, mental, economic, cultural or social identity;
from wikipedia.com
Page 62](https://image.slidesharecdn.com/co3rscr5-121114111613-phpapp01/85/Deconstructing-Data-Breach-Cost-62-320.jpg)


