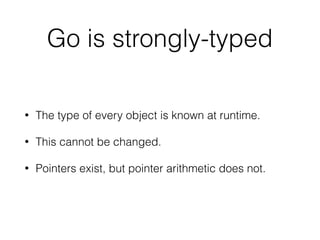
The document presents a discussion on Go (Golang), emphasizing its efficiency and security features for building web applications and server management. It outlines essential tips for using Go securely, including memory management, type safety, code formatting, and protecting against common vulnerabilities like cross-site request forgery and SQL injection. Additionally, it highlights various tools and libraries, such as the Gorilla toolkit and security middleware, that enhance the development experience and security of Go applications.














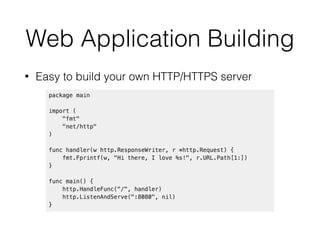
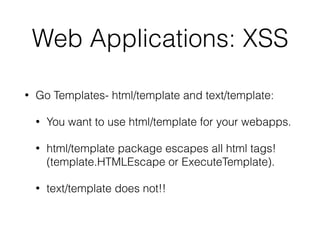



![Example:
secureMiddleware := secure.New(secure.Options{
AllowedHosts: []string{"example.com", "ssl.example.com"},
SSLRedirect: true,
SSLHost: "ssl.example.com",
SSLProxyHeaders: map[string]string{"X-Forwarded-Proto": "https"},
STSSeconds: 315360000,
STSIncludeSubdomains: true,
STSPreload: true,
FrameDeny: true,
ContentTypeNosniff: true,
BrowserXssFilter: true,
ContentSecurityPolicy: "default-src 'self'",
PublicKey: `pin-sha256="base64+primary=="; pin-
sha256="base64+backup=="; max-age=5184000; includeSubdomains; report-
uri="https://www.example.com/hpkp-report"`,
})](https://image.slidesharecdn.com/lascon2015-golangtips-151023002928-lva1-app6891/85/13-practical-tips-for-writing-secure-golang-applications-25-320.jpg)

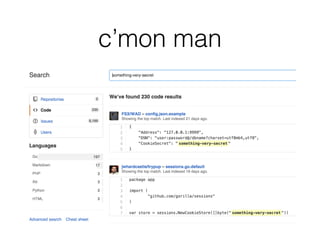
![nosurf example
var templateString = `
<!doctype html>
<html><body>
{{ if .name }}
<p>Your name: {{ .name }}</p>
{{ end }}
<form action="/" method="POST">
<input type="text" name="name">
<!-- Try removing this or changing its value
and see what happens -->
<input type="hidden" name="csrf_token" value="{{ .token }}">
<input type="submit" value="Send">
</form></body></html>
`
var templ = template.Must(template.New("t1").Parse(templateString))
func myFunc(w http.ResponseWriter, r *http.Request) {
context := make(map[string]string)
context["token"] = nosurf.Token(r)
if r.Method == "POST" {
context["name"] = r.FormValue("name")
}
templ.Execute(w, context)
}
func main() {
myHandler := http.HandlerFunc(myFunc)
fmt.Println("Listening on http://127.0.0.1:8000/")
http.ListenAndServe(":8000", nosurf.New(myHandler))
}](https://image.slidesharecdn.com/lascon2015-golangtips-151023002928-lva1-app6891/85/13-practical-tips-for-writing-secure-golang-applications-27-320.jpg)




