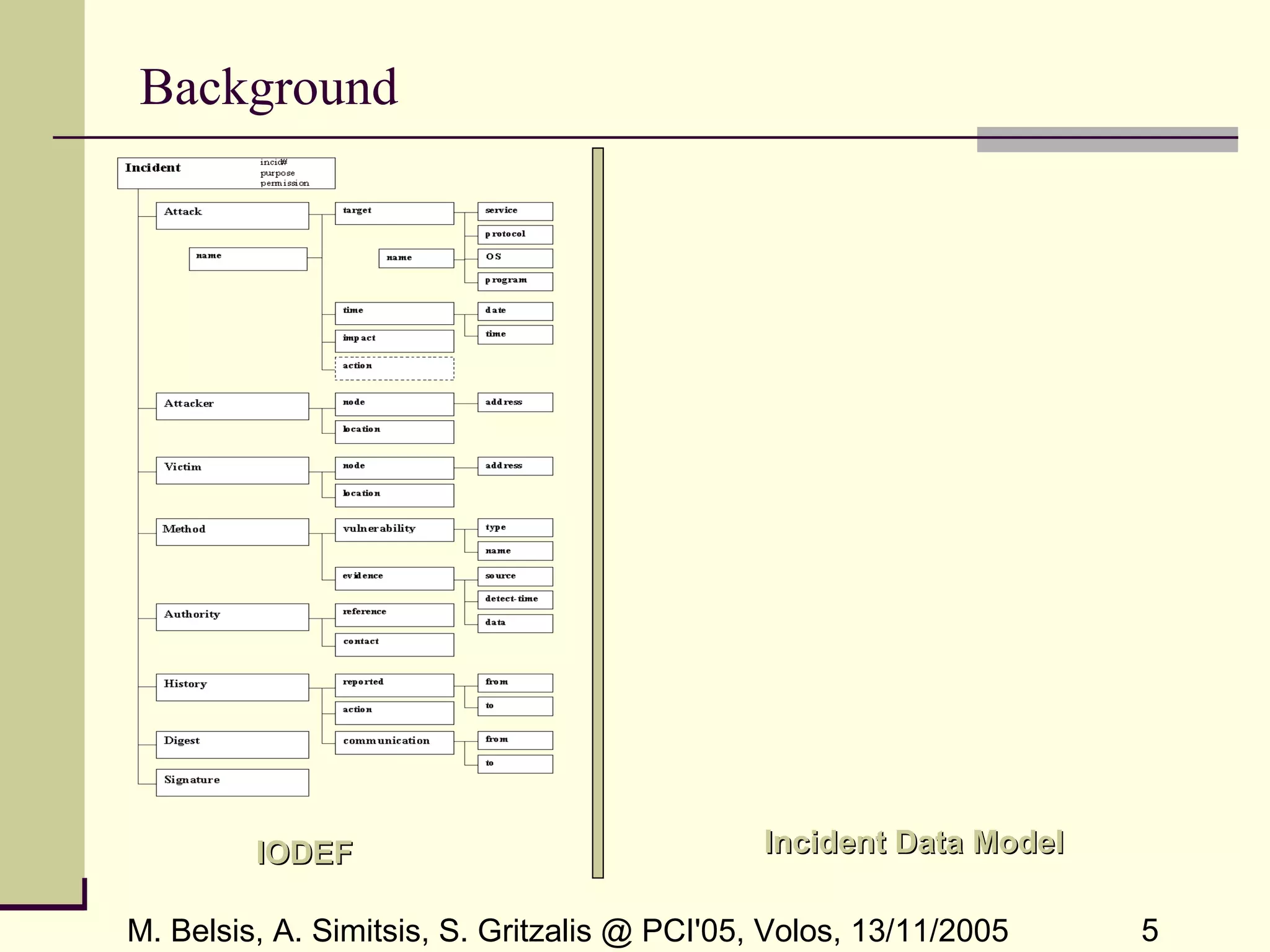
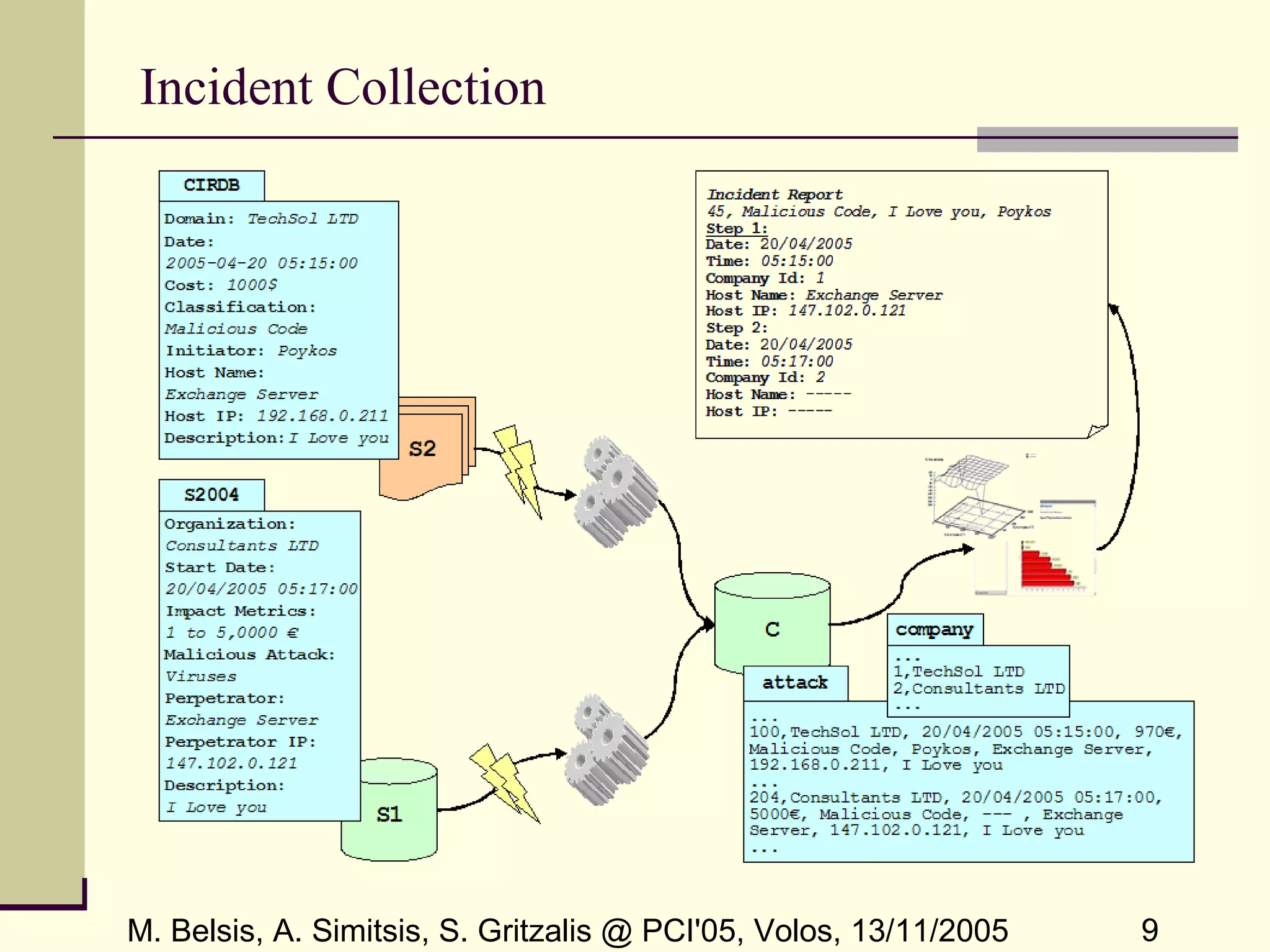
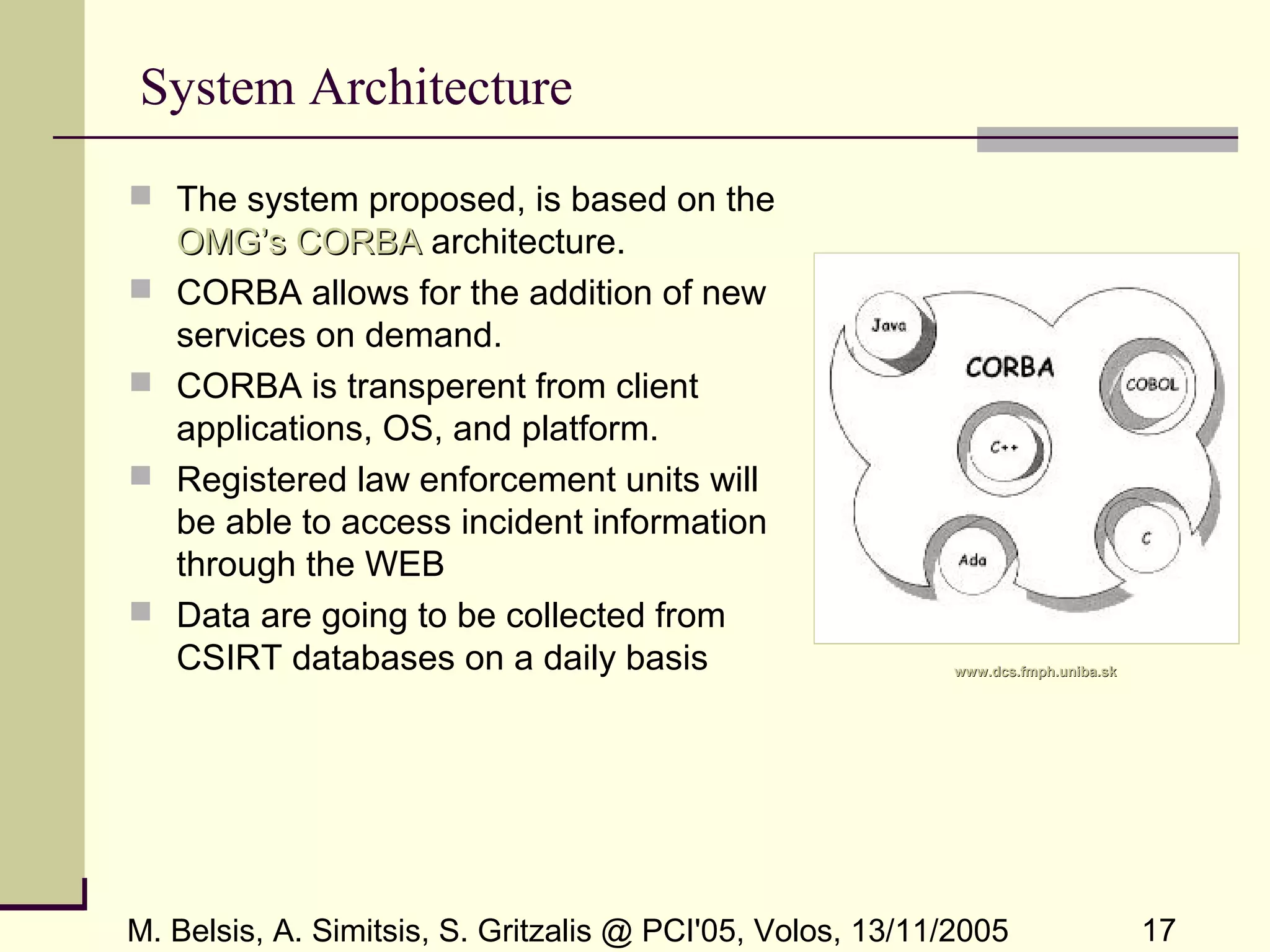
The document presents a framework for workflow-based security incident management, emphasizing the challenges of integrating data from various incident databases. It proposes a centralized incident database management system (DBMS) that utilizes ETL workflows for efficient collection, transformation, and loading of incident data. The goal is to facilitate incident correlation and improve law enforcement's ability to respond to security incidents by minimizing the time window for information dissemination.