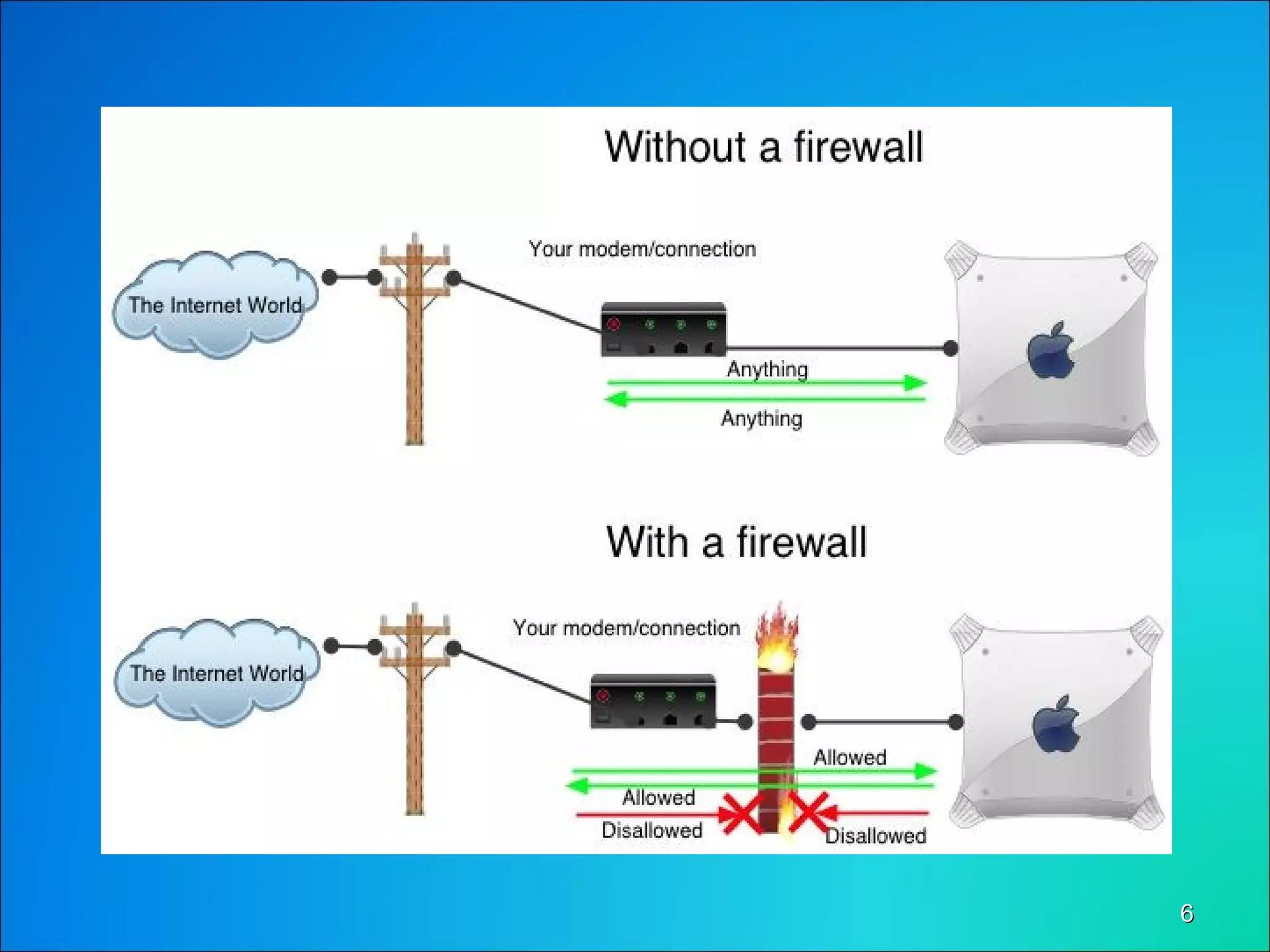
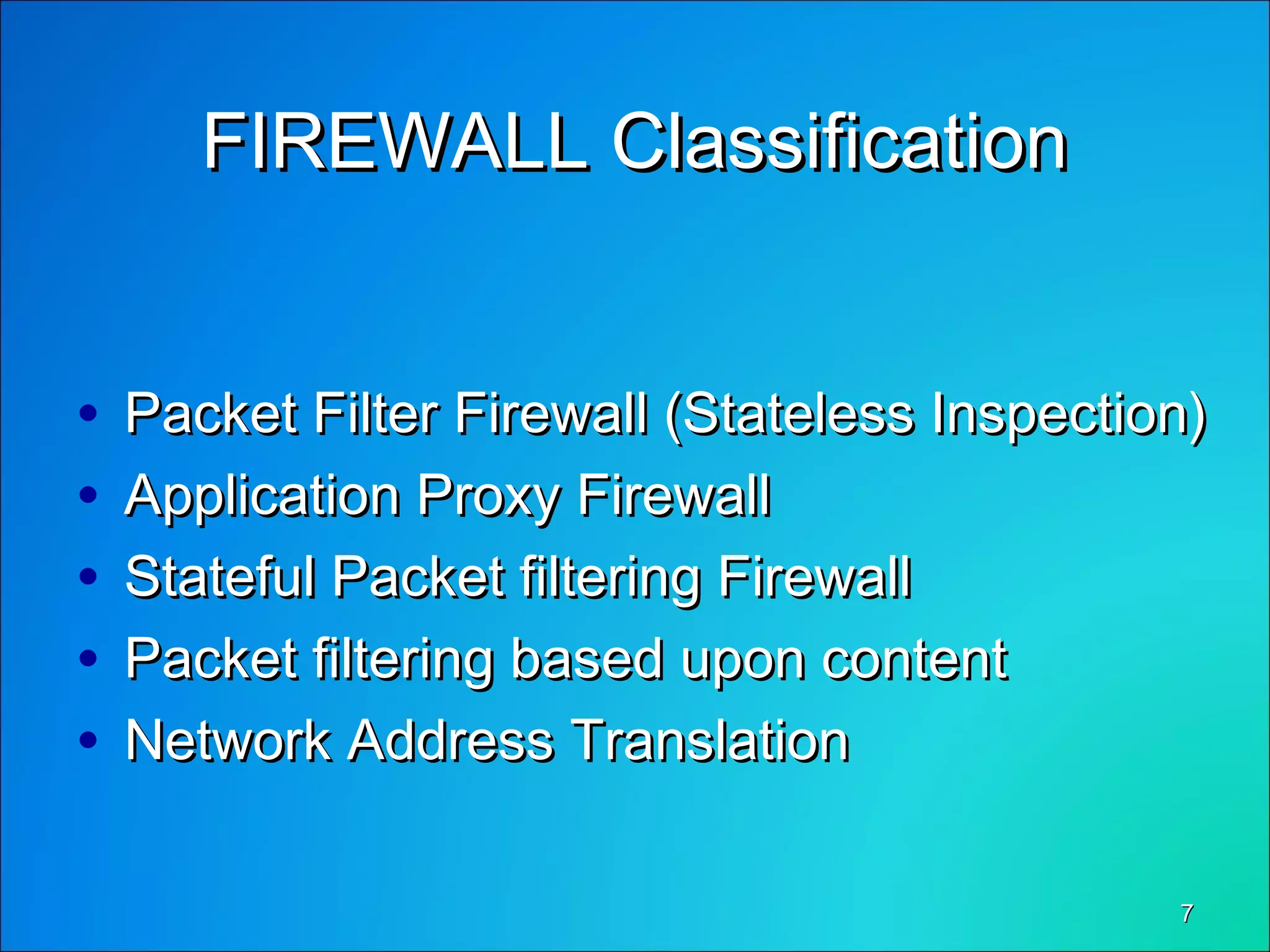
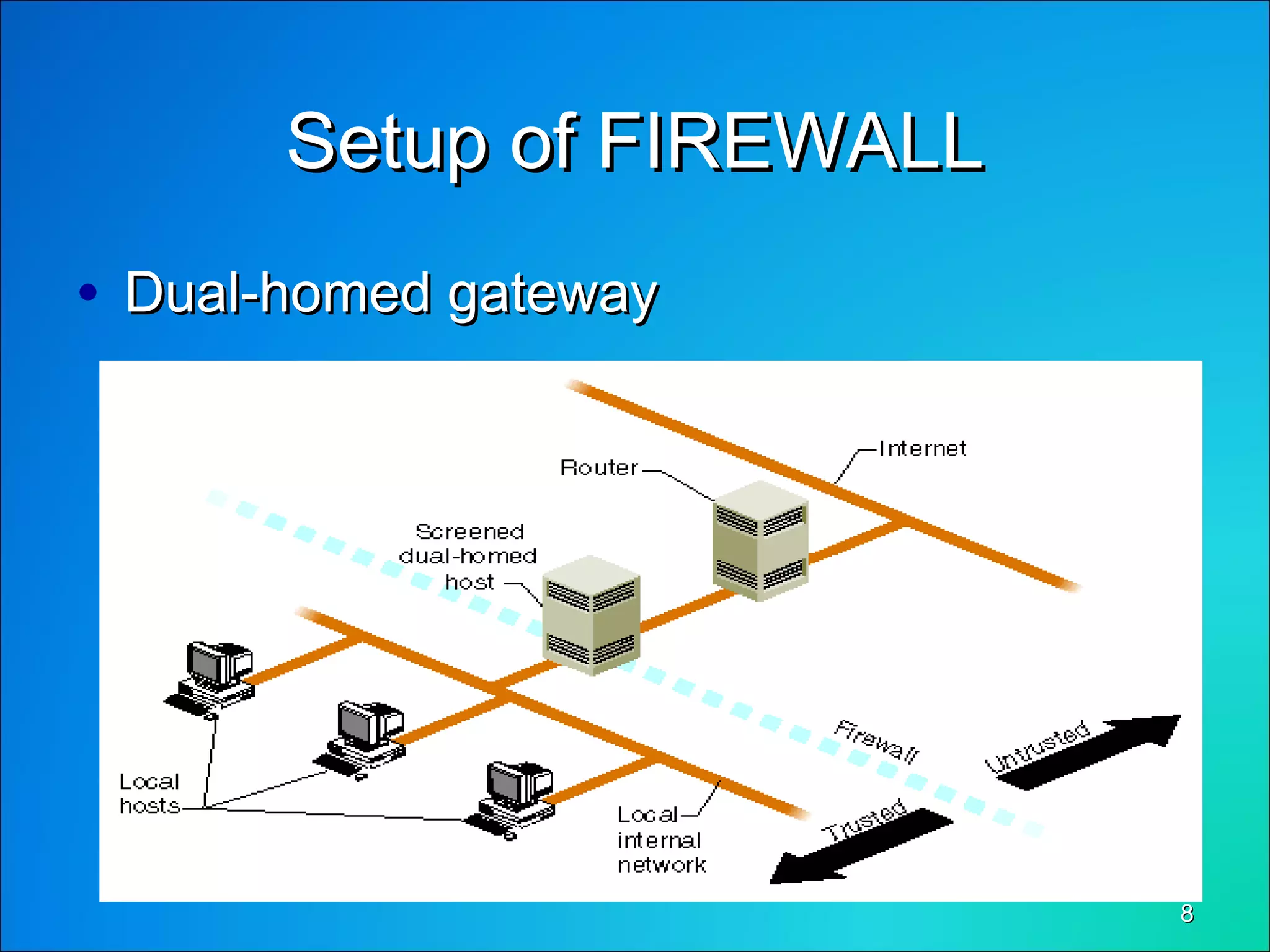
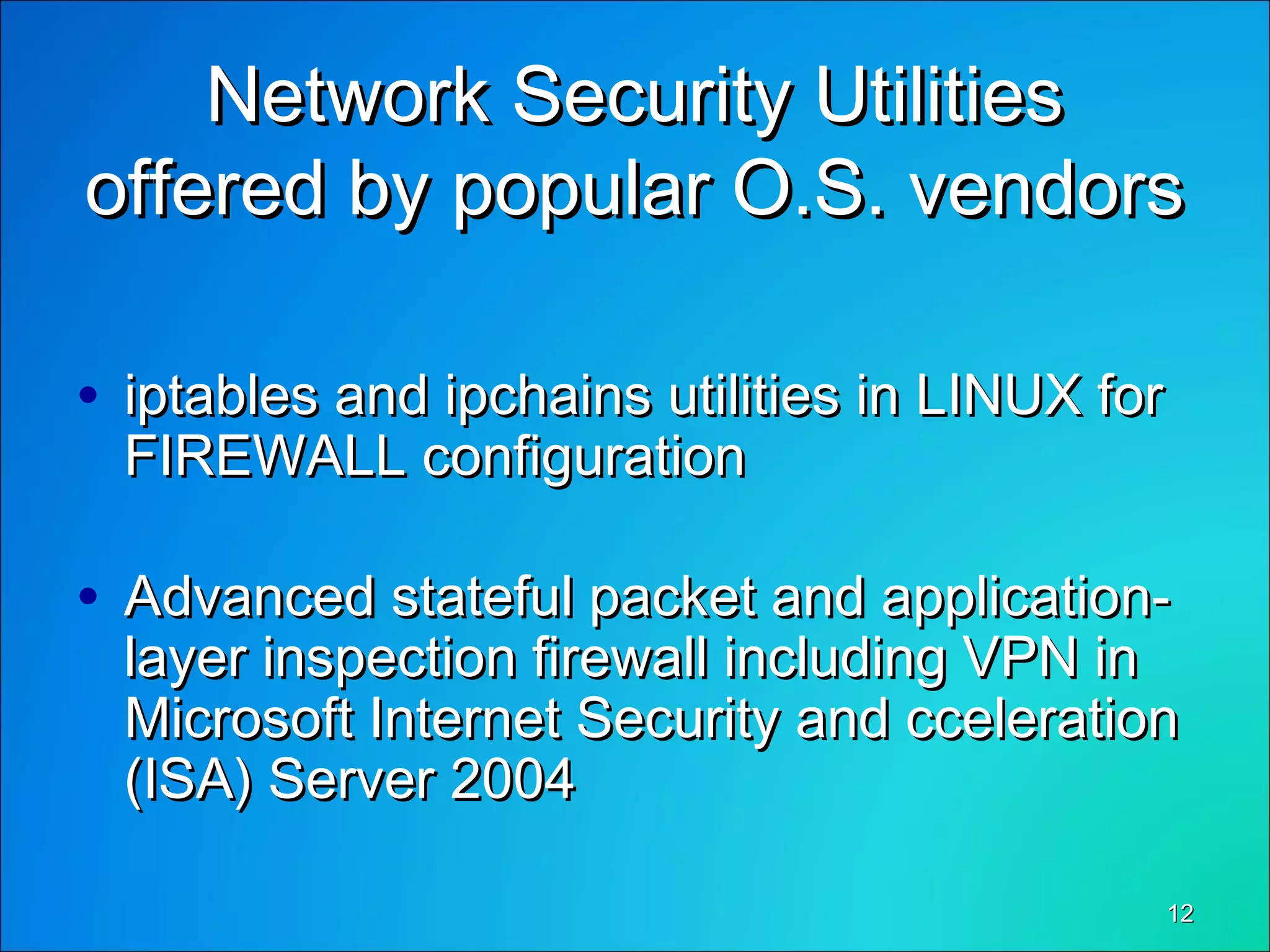
This document discusses network security through firewalls. It begins by outlining desirable network features such as high bandwidth, security, and low client costs. It then describes different levels of security from the BIOS to the application level. Common security issues like packet sniffing and password attacks are examined. The document defines a firewall as software that controls and analyzes data passing between networks, placed at the connection point between two networks. It classifies firewalls and discusses how dual-homed gateways can be set up. The document explores how firewalls provide protection against threats like remote logins, backdoors, session hijacking, and denial of service attacks. It concludes by stating that firewalls are a solution to common network security problems