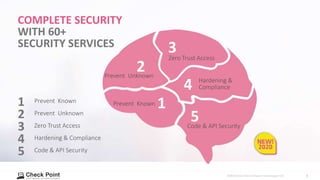
Check Point provides complete security across networks, endpoints, cloud, and mobile with over 60 security services to protect over 50 types of assets. Their security services include preventing known and unknown threats, zero trust access management, hardening and compliance, and code/API security. They offer consolidated security management and shared threat intelligence across all security domains.