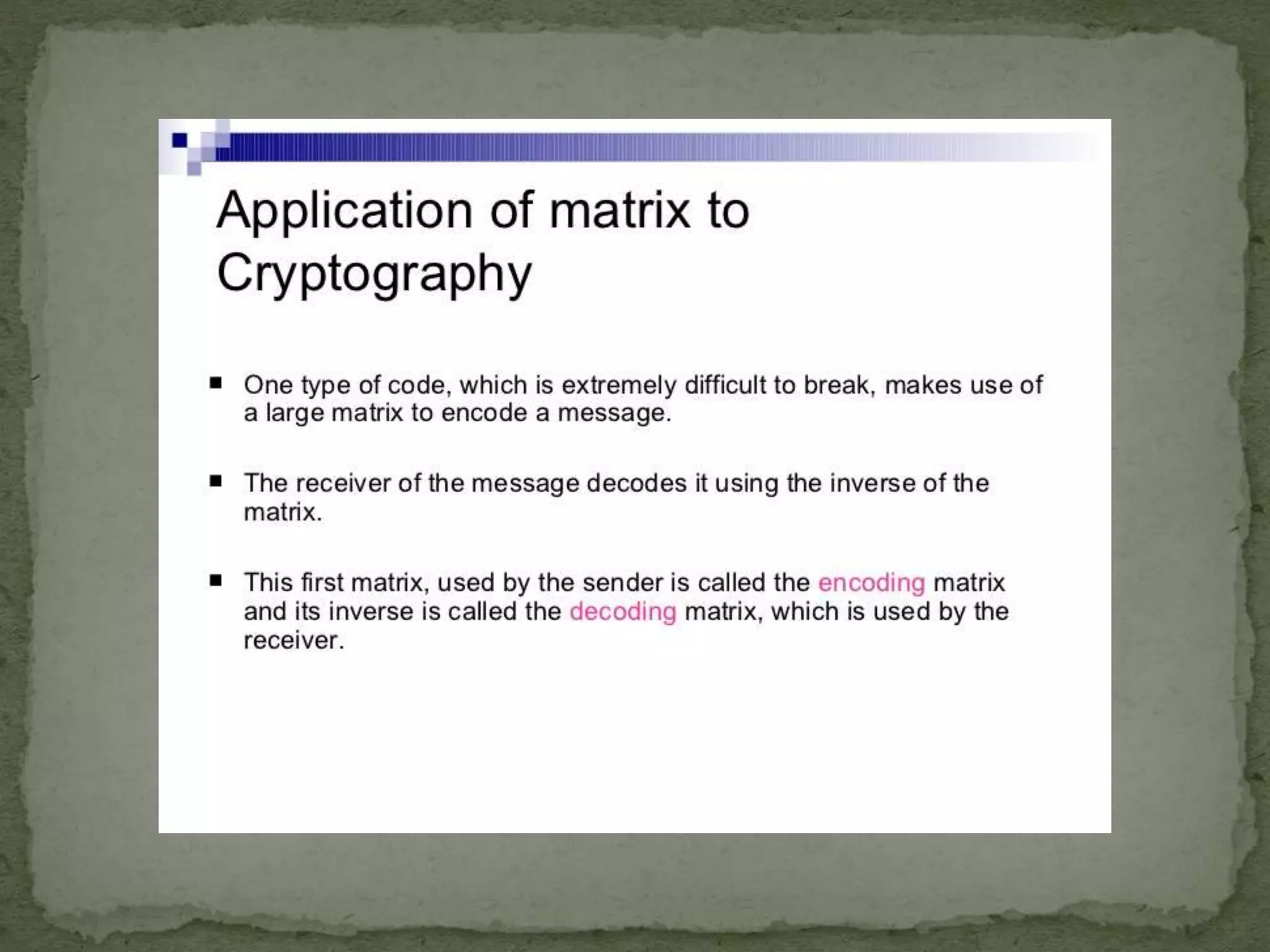
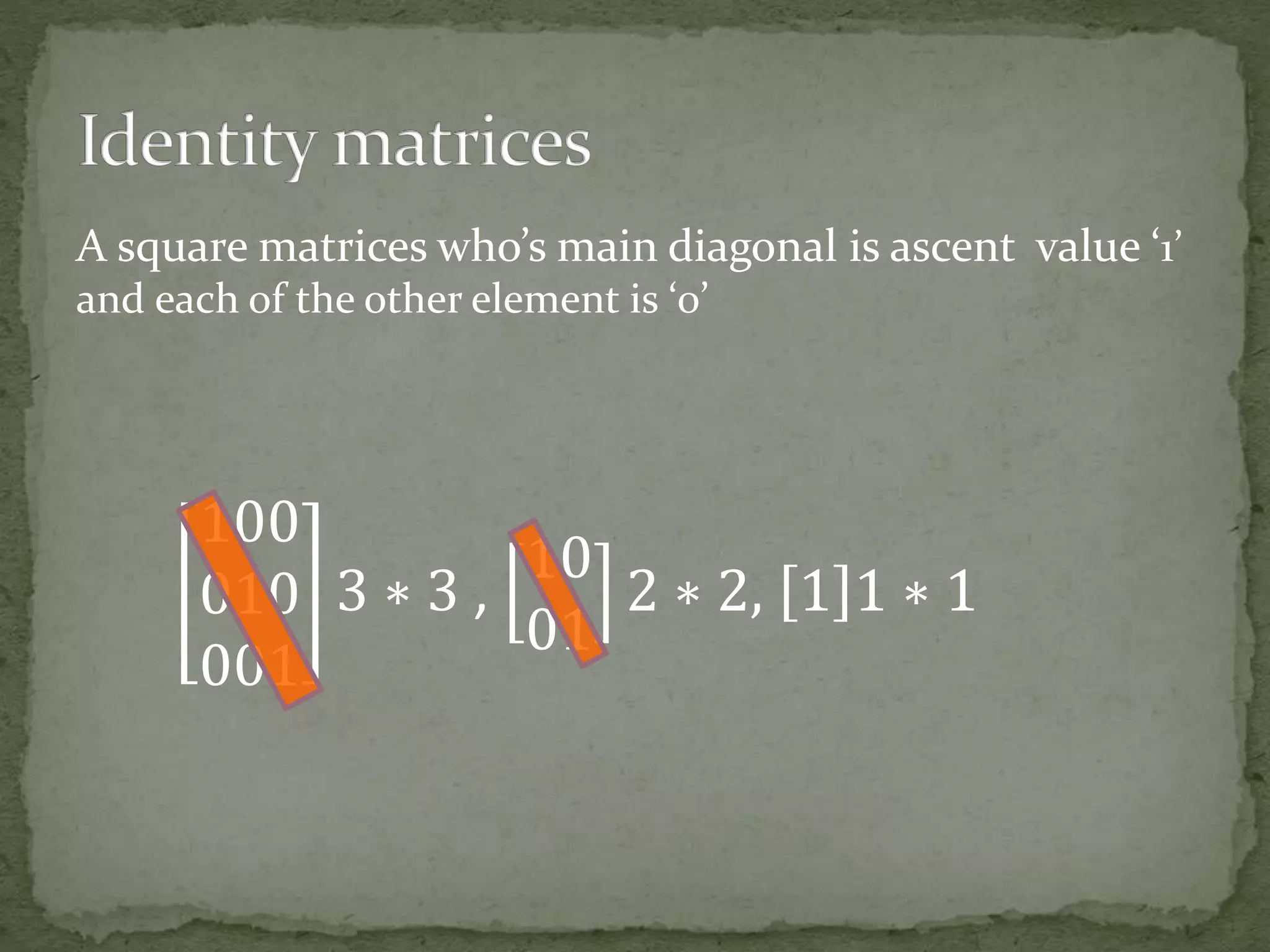This document discusses matrices and their uses. It defines what a matrix is and provides examples of different types of matrices like row matrices, column matrices, null matrices, identity matrices, diagonal matrices, triangular matrices, and transpose matrices. It then discusses some applications of matrices like in cryptography for encrypting messages, in electrical circuits, quantum mechanics, optics, robotics, automation, economics, and more. Matrices are useful for tasks like plotting graphs, scientific studies, page ranking algorithms, image projection, representing real world data, and calculating gross domestic products.

![Matrices
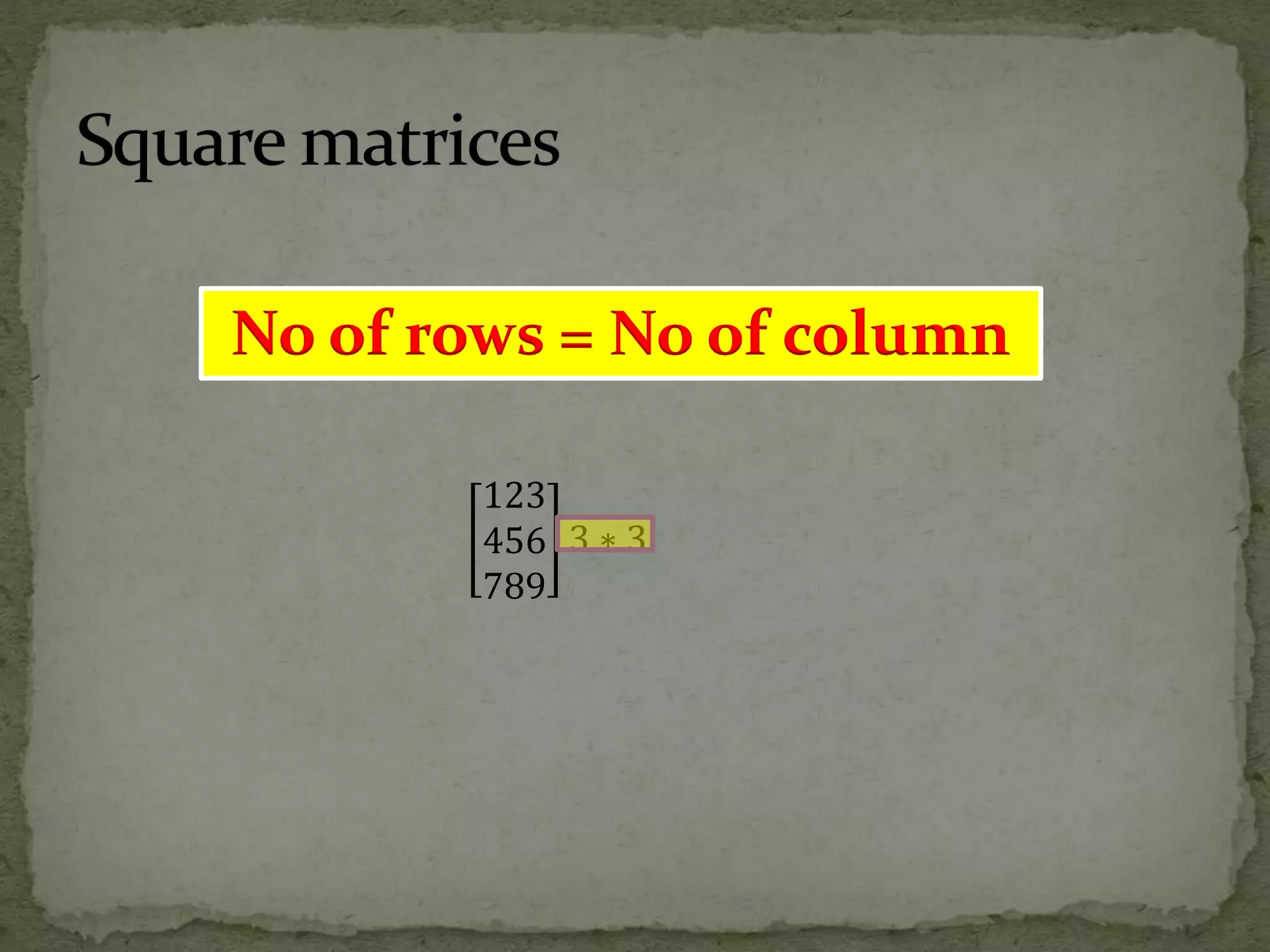
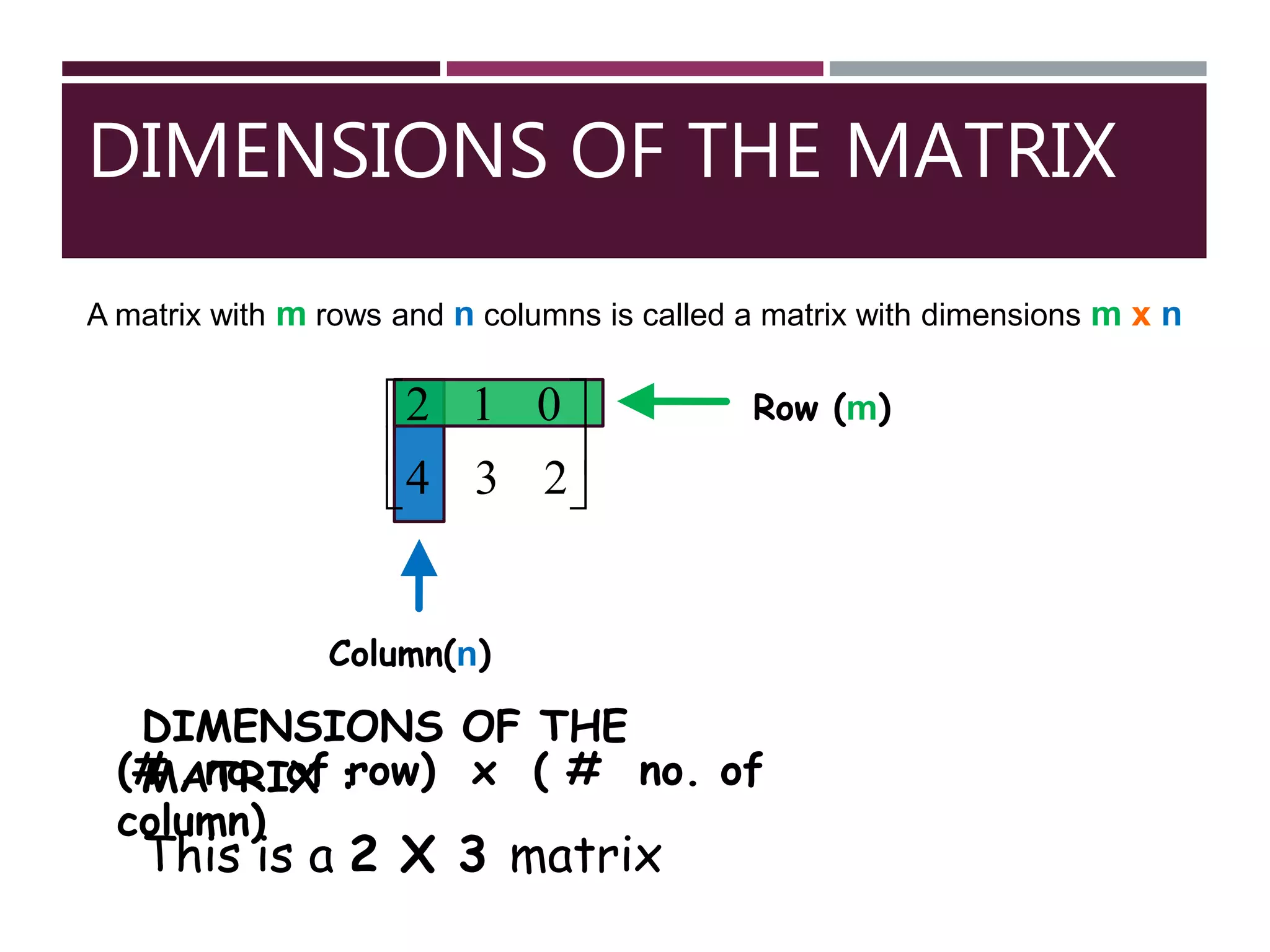
A rectangular arrangement of numbers in rows and
columns.
It is the Combination of linear equation.
It is Represented by these symbols:
[], ||,()](https://image.slidesharecdn.com/matrix-161109151358/75/Matrix-and-it-s-Application-2-2048.jpg)
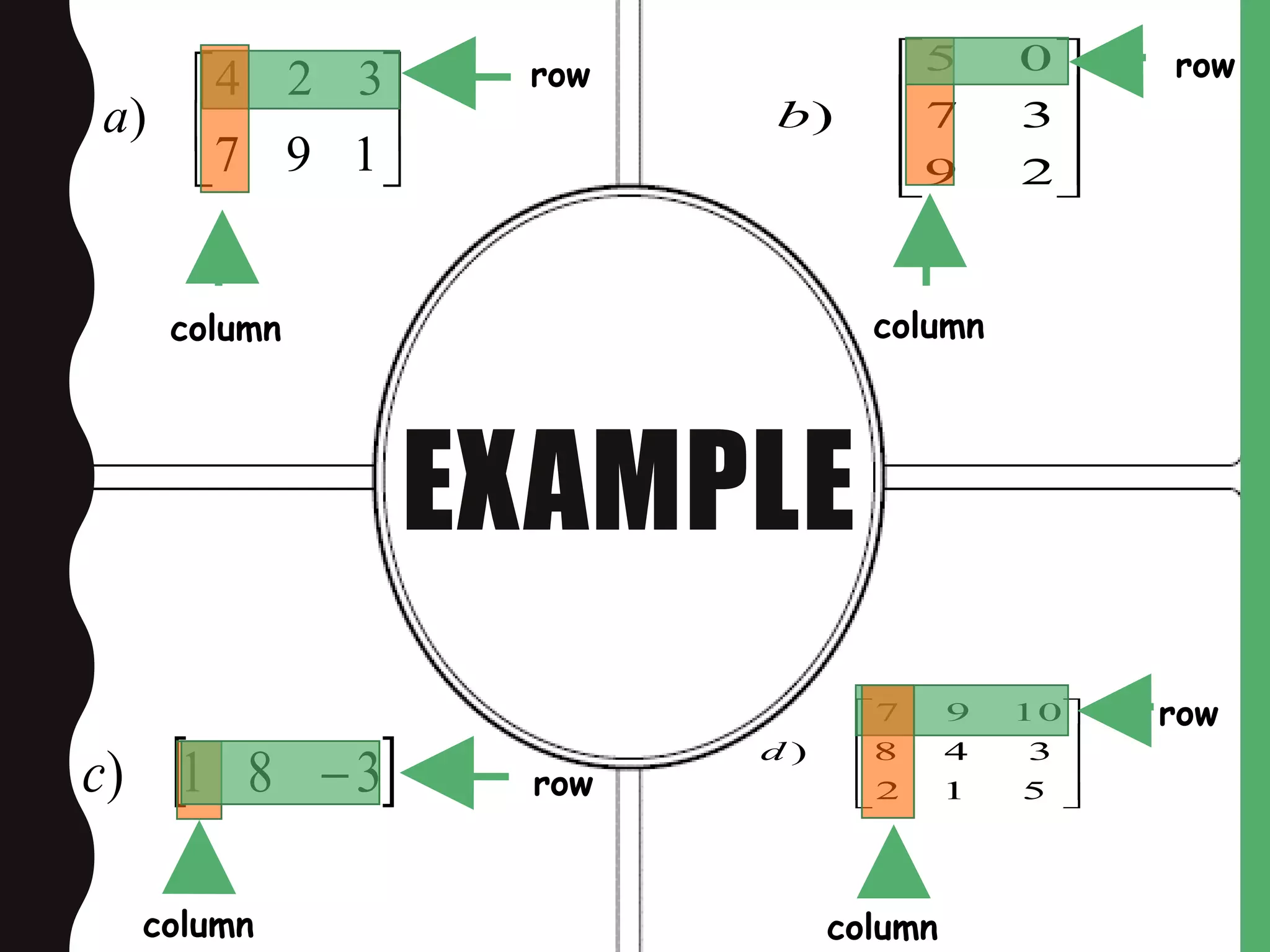
![Types of Matrices
1. Row matrices – A matrices which has only one row
called row matrices e.g.-
[123]1*3
2. Column matrices – A matrices which has only one column
is called column matrices e.g. –](https://image.slidesharecdn.com/matrix-161109151358/75/Matrix-and-it-s-Application-5-2048.jpg)