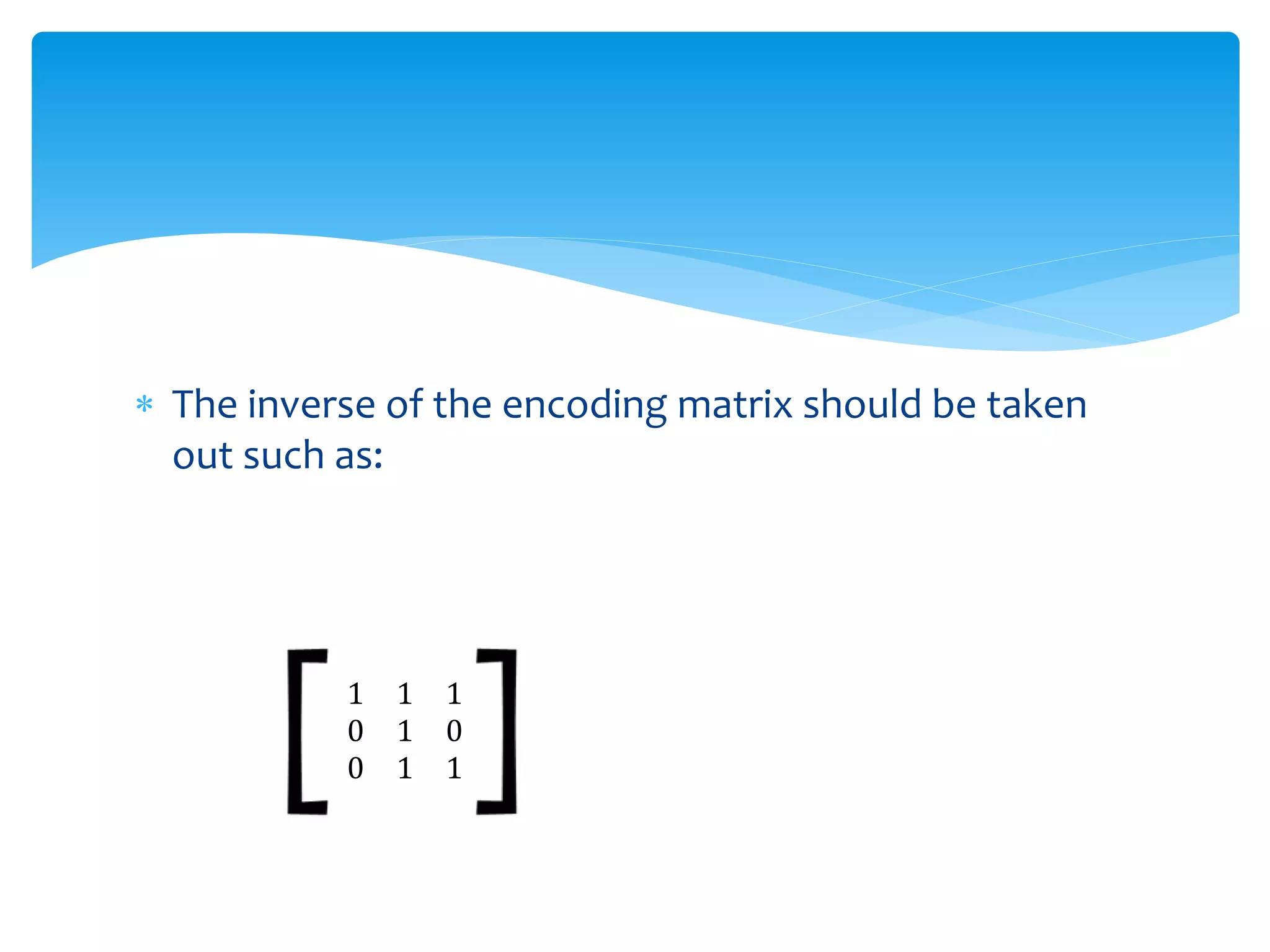
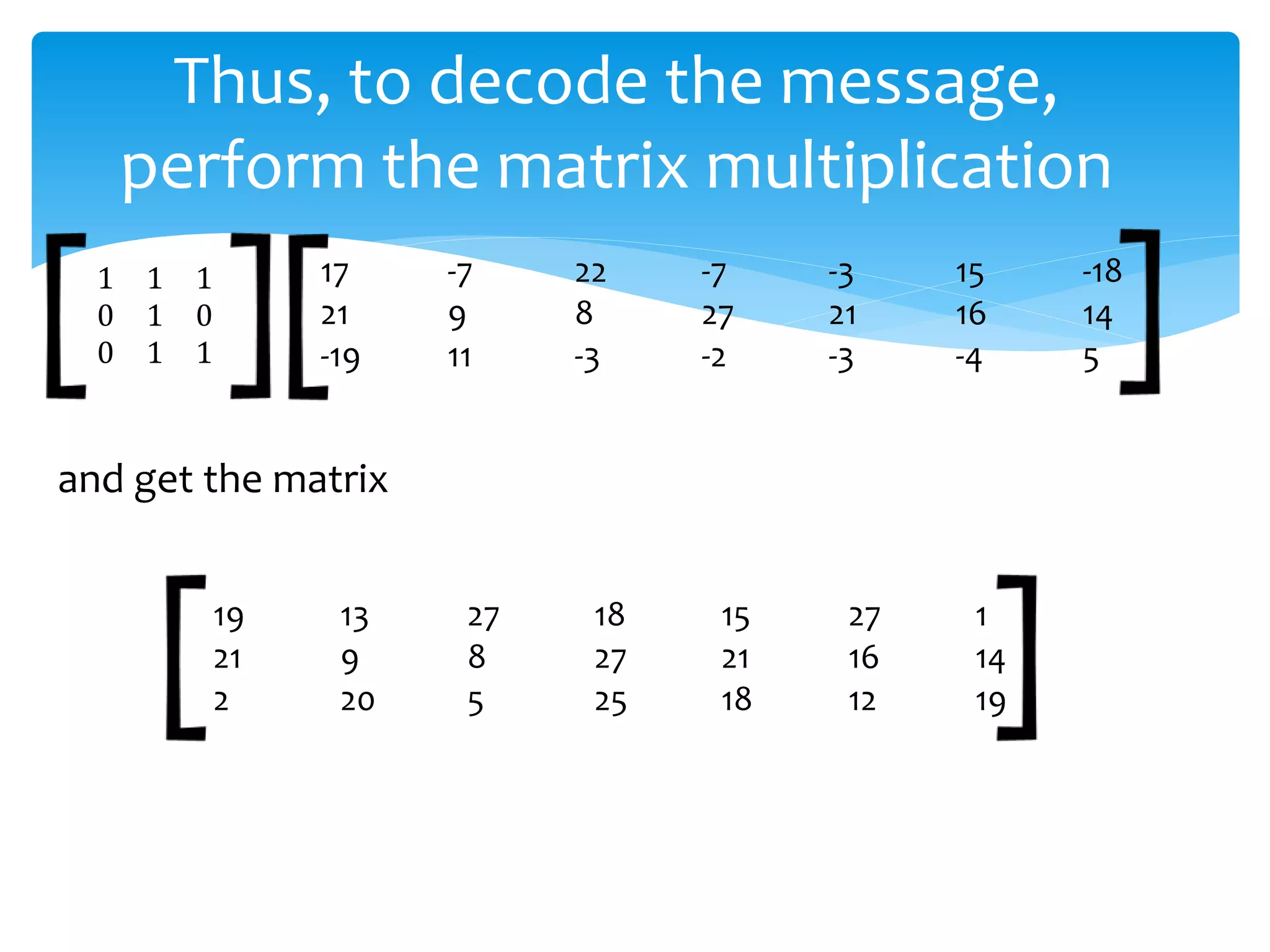
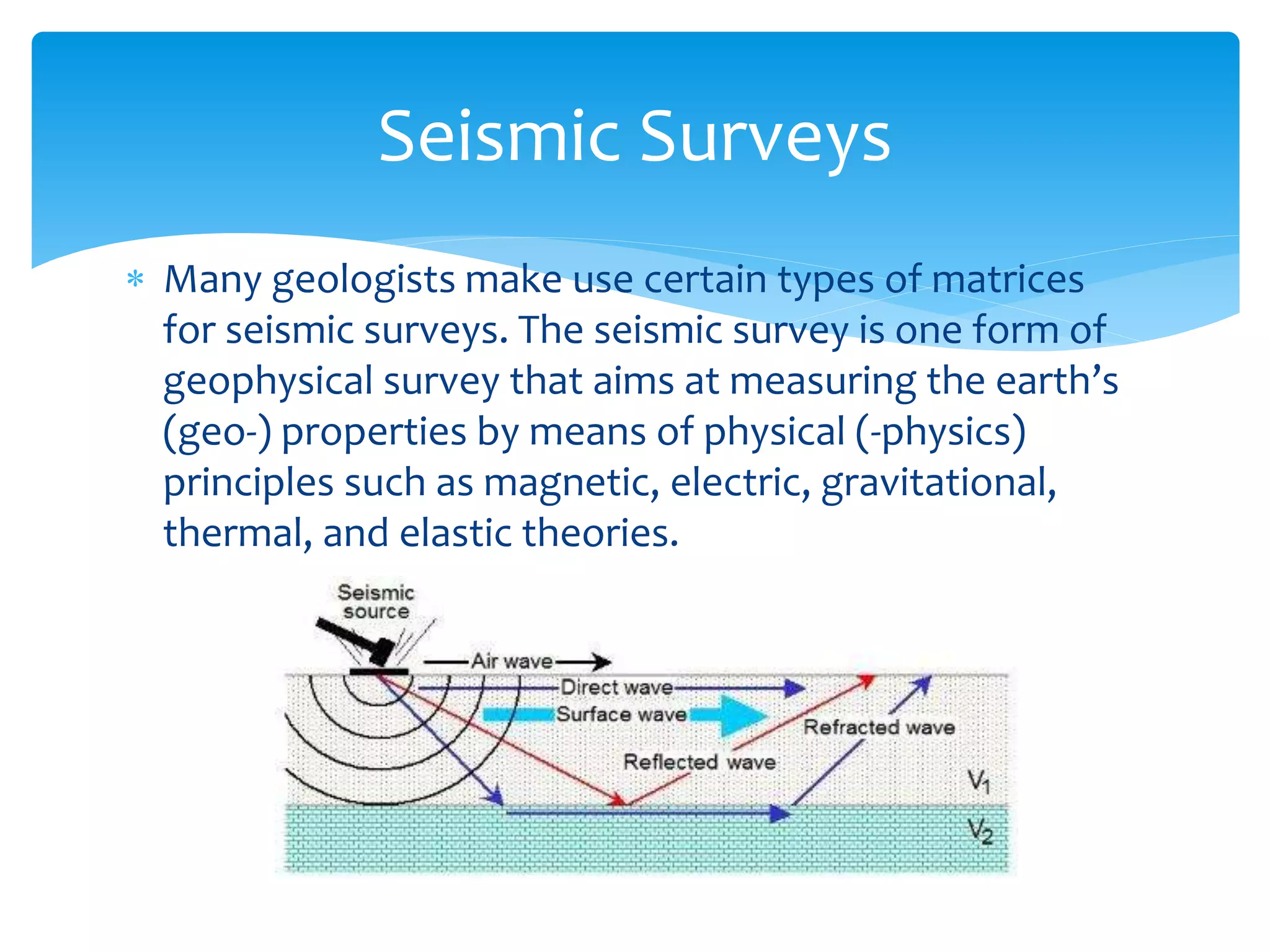
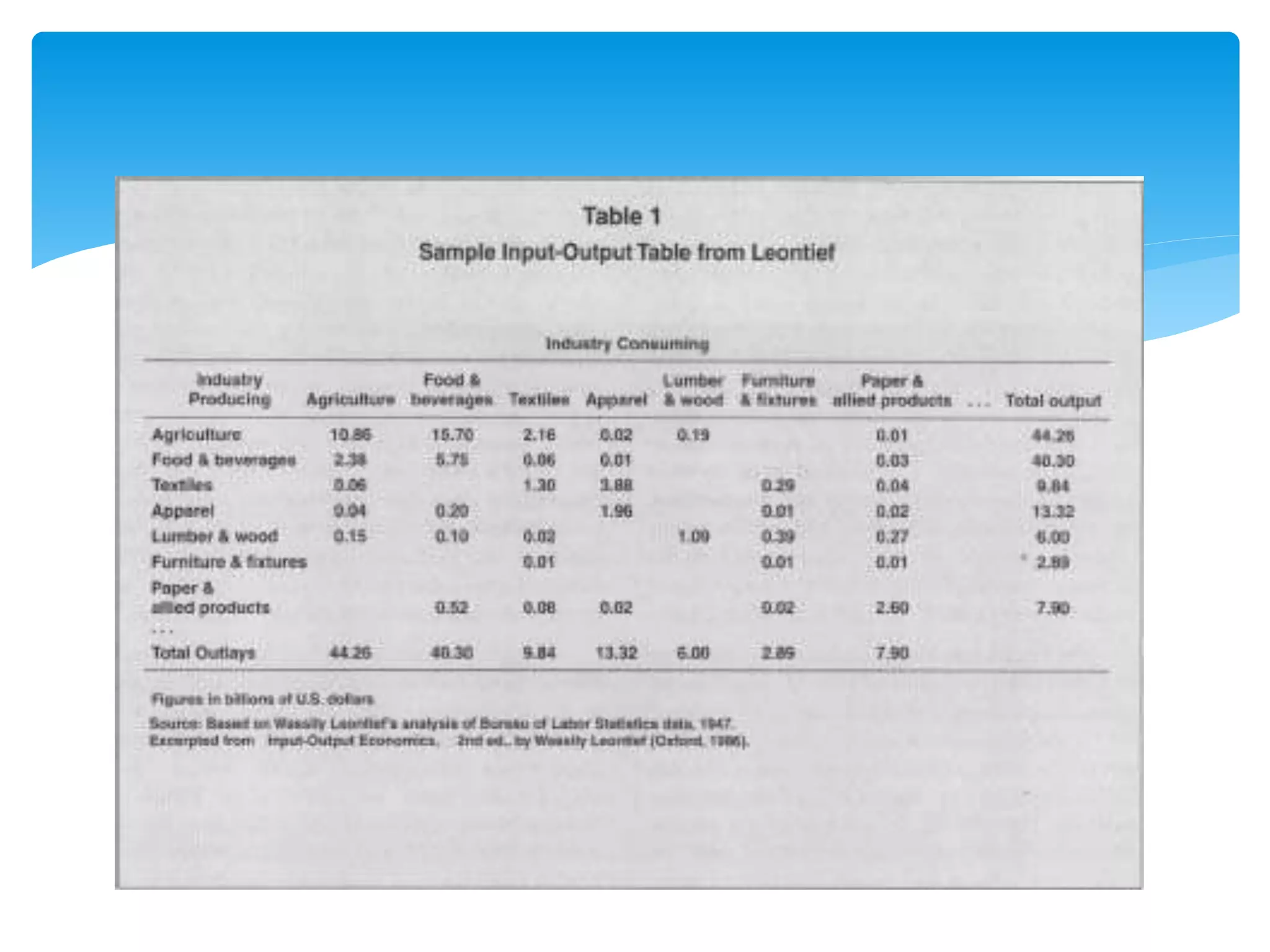
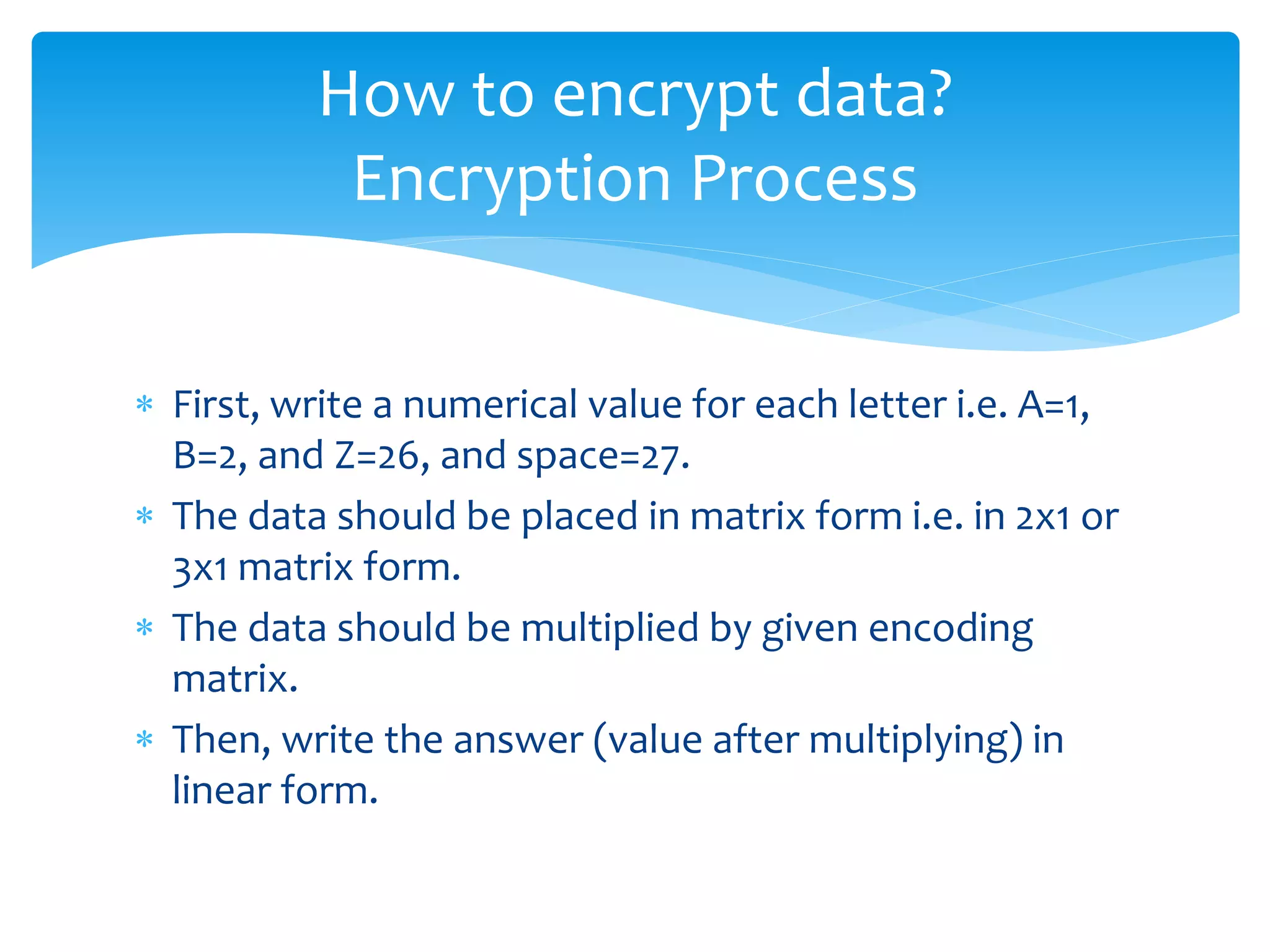
The document presents an overview of the application of matrices in cryptography, highlighting the encryption and decryption processes through numeric transformation and matrix multiplication. It also mentions the use of matrices in fields such as geology for seismic surveys, economics for production efficiency, computer graphics for animations, and data organization in various scientific and engineering contexts. Overall, it illustrates the versatility of matrices across different disciplines.



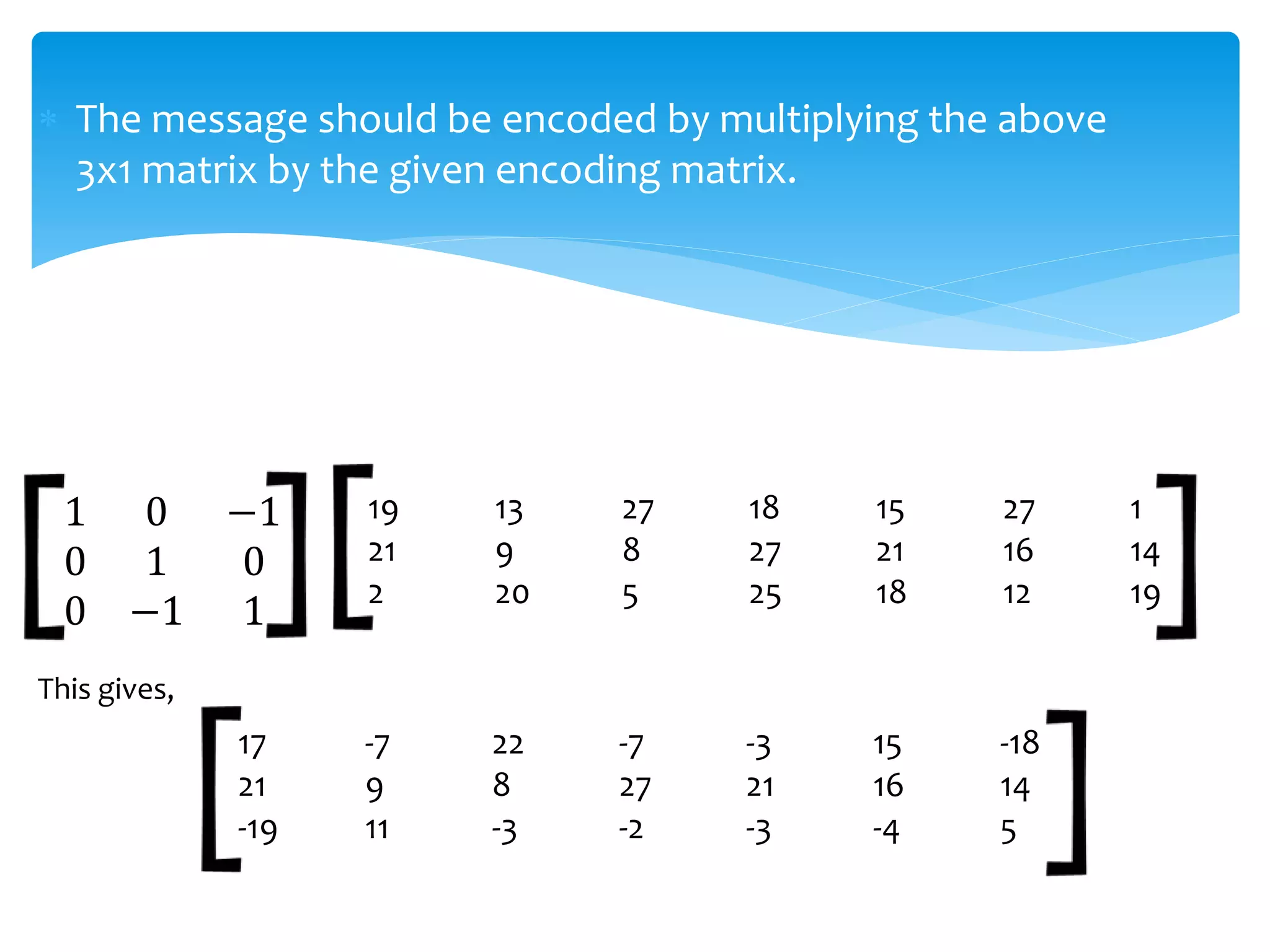
![ Since we are using a 3 by 3 matrix, we break the
enumerated message above into a sequence of 3 by 1
vectors:
[ ] [ ] [ ] [ ] [ ] [ ] [ ]19
21
2
13
9
20
18
27
25
27
8
5
15
21
18
1
14
19
27
16
12](https://image.slidesharecdn.com/presentationonapplicationofmatrix-140704224856-phpapp01/75/Presentation-on-application-of-matrix-5-2048.jpg)